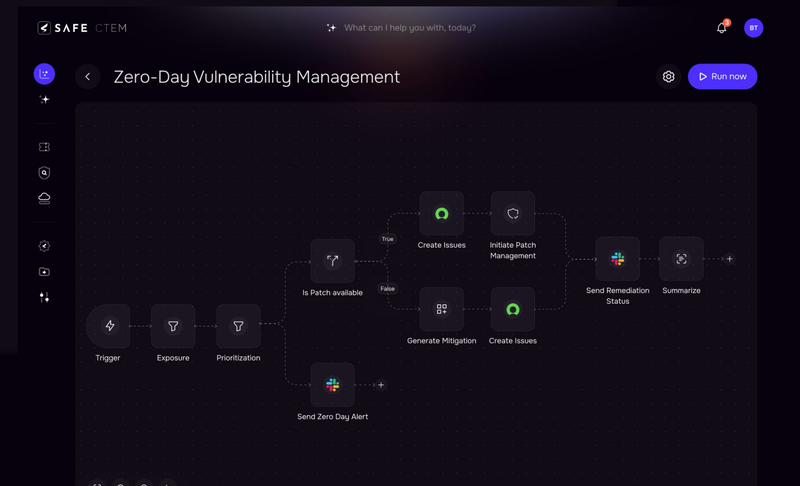
With more data, comes greater Decision Support
In today’s rapidly evolving digital landscape, comprehensive cybersecurity measures are crucial. SAFE’s customers are visionaries and changemakers who trust us to lead them into a new era of cybersecurity risk management with quantified, defensible information. They continually push us to innovate, enhancing clarity and effectiveness in cyber risk management.
When I joined SAFE, I asked, “Where should customers start their Cyber Risk Management journey?” The answer, though cliché, was illuminating: to prevent a burglary, do you secure your neighborhood first or your own home? This insight clarified why SAFE initially focused on enterprise cyber risk management. Recently, our customers urged us to develop a solution for third party cyber risk management (TPRM), addressing the fastest-growing attack surface for many enterprises.
Now, they’re pointing us to solve a broader problem. Just as we unified TPRM by consolidating disparate point solutions, the next challenge is to address the fragmented view of cyber risk that frustrates CISOs. Many large enterprises struggle to manage hundreds of siloed solutions, each generating conflicting data.
Our solution: The Cyber Singularity Platform.
What is Cyber Singularity?
In theoretical physics, “singularity” refers to a point where a function takes an infinite value. In our context, it symbolizes a pivotal breakthrough in perceiving and managing cyber risk.
If there’s one consistent message we hear from CISOs, it’s this: We are done with silos. Our critical concern isn’t where a risk originates—whether from an internal data center or a third-party service provider. We need a solution that:
- Consolidates all telemetry from first and third parties, internal siloed cybersecurity solutions, external threat intelligence, and more into one central place.
- Provides a comprehensive tool to make all our risks visible and quantifiably managed from a single platform.
- Contextualizes data specific to our business or industry.
- Applies open standards to ensure reliable and defensible insights into our risk profile. We use Factor Analysis of Information Risk (FAIR), the equivalent in cybersecurity to GAAP in accounting, along with MITRE ATT&CK and other standards.
We are on a mission to provide every organization with that single source of truth to drive better risk informed decisions and lead to positive business outcomes.
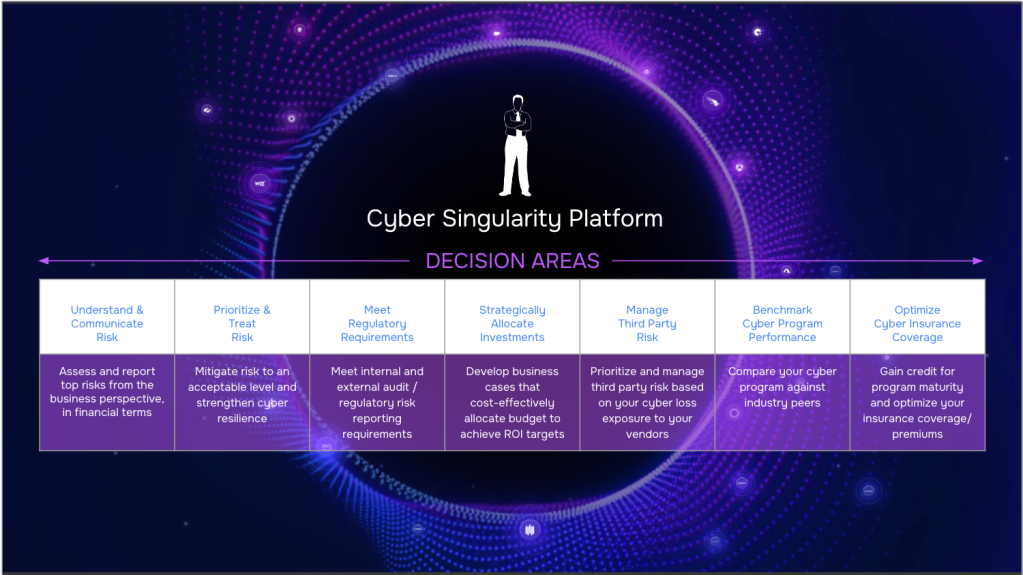
Cyber Singularity Platform Decision Areas That Will Accelerate Your Business
1. Understand and Communicate Risk
In real-time, assess, quantify, and translate risk into a business context, expressed as scenarios that address your urgent business needs and can be readily communicated across the organization. This capability transforms technical risk data into a language that executives and board members can understand, fostering informed decision-making and enhancing organizational alignment.
2. Prioritize and Treat Risk
Mitigate risk to lower financial impact and strengthen cyber resilience. Cyber risk quantification in financial terms enables data-driven prioritization among risks and clarifies which controls or security initiatives are most cost-effective for driving down risk. This strategic approach ensures that resources are allocated to address the most critical threats, optimizing both security and budget.
3. Fulfill Regulatory Requirements
Address internal and external audit and regulatory disclosure and compliance with a defensible standard for risk assessment and communication. Objective, real-time data gathering enables 10-K or other reporting in required time frames. By aligning with industry standards such as FAIR, the platform ensures that your organization meets regulatory demands with confidence.
4. Strategically Allocate Investments
Develop risk-informed business cases to strategically allocate cyber budget and achieve ROI objectives. Run ‘what-if’ scenarios to model the effect on risk reduction of alternate strategies. This forward-thinking approach allows organizations to maximize the impact of their cybersecurity investments, ensuring that every dollar spent contributes to overall risk reduction.
5. Manage Third-Party Risk
Conduct end-to-end scenario modeling of third-party impact on first-party business operations and vice versa. Prioritize third parties based on risk to your business and focus on the most critical third-party controls. This comprehensive view of third party cyber risk management ensures that your supply chain is secure, mitigating potential vulnerabilities from external sources.
6. Benchmarking Cyber Program Performance
Compare your cyber program against industry peers and demonstrate value back to the business. We offer a comprehensive set of industry loss data and external threat feeds contextual to your business based on your geography, industry, and size. Benchmarking against peers provides valuable insights, highlighting areas for improvement and showcasing your program’s strengths.
7. Maximize Cyber Insurance Benefits
Gain credit for cyber program maturity and determine the right levels of safeguard required for your organization. Multiple brokers and carriers have accepted and validated our platform and offer discounts to our users. By demonstrating the maturity and effectiveness of your cybersecurity program, you can negotiate better terms and lower premiums, optimizing your cyber insurance coverage.
Conclusion: Take a Transformative Leap
The Cyber Risk Singularity represents a transformative leap in how organizations manage and perceive cyber risk. By consolidating all cybersecurity data into a unified platform, businesses can enhance their decision-making capabilities across seven key areas: understanding and communicating risk, prioritizing and treating risk, fulfilling regulatory requirements, strategically allocating investments, managing third-party risk, benchmarking program performance, and maximizing cyber insurance benefits.
Embrace the future of cyber risk management with SAFE’s Cyber Singularity Platform. See SAFE in Action: here or Contact us for a demo and discover how our innovative approach can enforce your cyber risk management strategy.