New Markers of Cyber Risk Management Maturity: Know, Understand, Communicate Risk
Gain confidence in reporting to the board and senior leadership
“Maturity” – it’s a timeworn concept in cyber risk management, and a necessary one – but not sufficient to keep cybersecurity up to speed with the needs of the business.
To explain…NIST CSF, ISO 27005 and the like are highly useful as compliance standards (or lists of best practices) for cyber risk assessment and indicators of a certain level of maturity for security organizations.
But they can’t answer on the basics that any CISO would like to know such as “How much risk do we have?” and “If we invest in security controls, how much less risk will we have?”
Those questions can only be answered by a methodology to quantify cyber risk in financial terms and support return-on-investment calculations. ISO and NIST, etc. stay in a technical lane; ”cyber risk management maturity” might be “We can raise our compliance score from 3 to 3.5 if we spend X amount of dollars on new controls but we can’t really say that will buy us X dollars in risk reduction.”
FAIR (Factor Analysis of Information Risk) is the standard for cyber risk quantification in financial terms, recognized by the National Institute of Standards and Technology (NIST). FAIR, in effect, opens the conversation between security and the business.
But cyber risk quantification, even with FAIR (Factor Analysis of Information Risk), still doesn’t go beyond the technical mindset if cyber risk managers don’t start aligning their thinking with their business partners.
In that spirit, here are three new, business-friendly goals to gauge maturity in cyber risk: Know, Understand, Communicate.

Know and understand your business structure and respective risks and communicate that cross-functionally.
Note that these goals are compatible with the common cybersecurity standards – we’re focussing on ISO 27005 here – and are facilitated by FAIR.
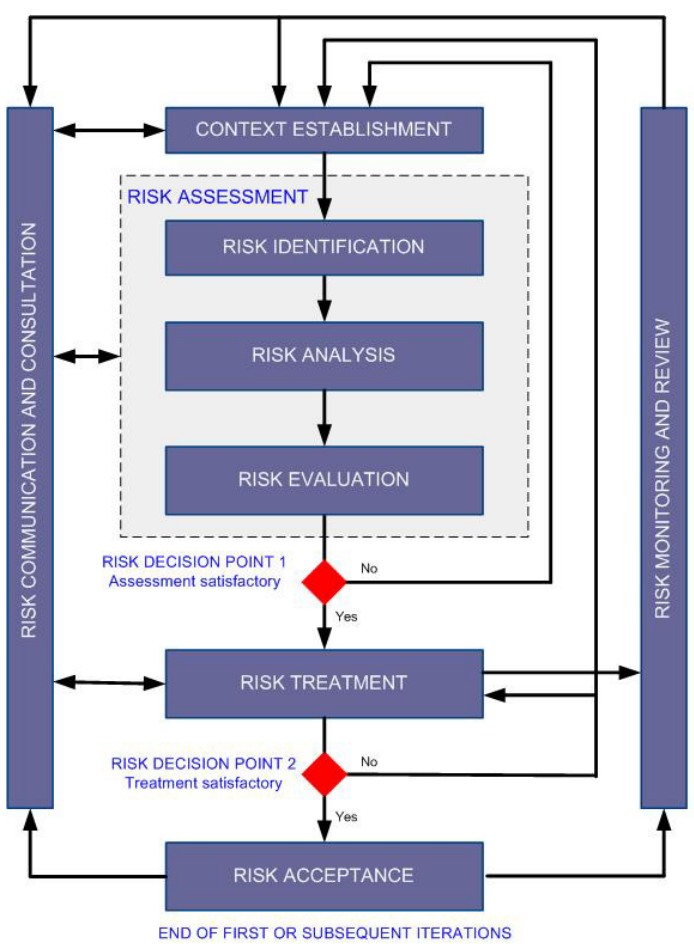
Image: Risk Assessment with ISO 27005
KNOW
- Know the business
- Scope business segments and structure
- Know the risks and consequences for each
- Know the business owners
Account for the activities and revenue sources of the business to start but more importantly segment the business in the way that your stakeholders want to see the risk, that is depending on where they see the value generated by the business.
For example, a major corporation could have many different lines of business, each with subsidiary business units and each running multiple applications. Stakeholders may want to see risk at the business unit level or applications level or some mix.
Aligning with ISO 27005
The standard recommends starting by establishing the context of the risk, defining stakeholders and parameters for risk-based decisions. Next, establish acceptable risk levels and impacts. Then identify the assets, threats and vulnerabilities for business segments.
How FAIR Helps
The FAIR Materiality Assessment Model (FAIR-MAM) is a great starting point for a quantitative risk management program. It’s a highly detailed methodology for collecting loss data specific to the structure of the business that, in effect, leads you to “know your business” by segment and value chain.
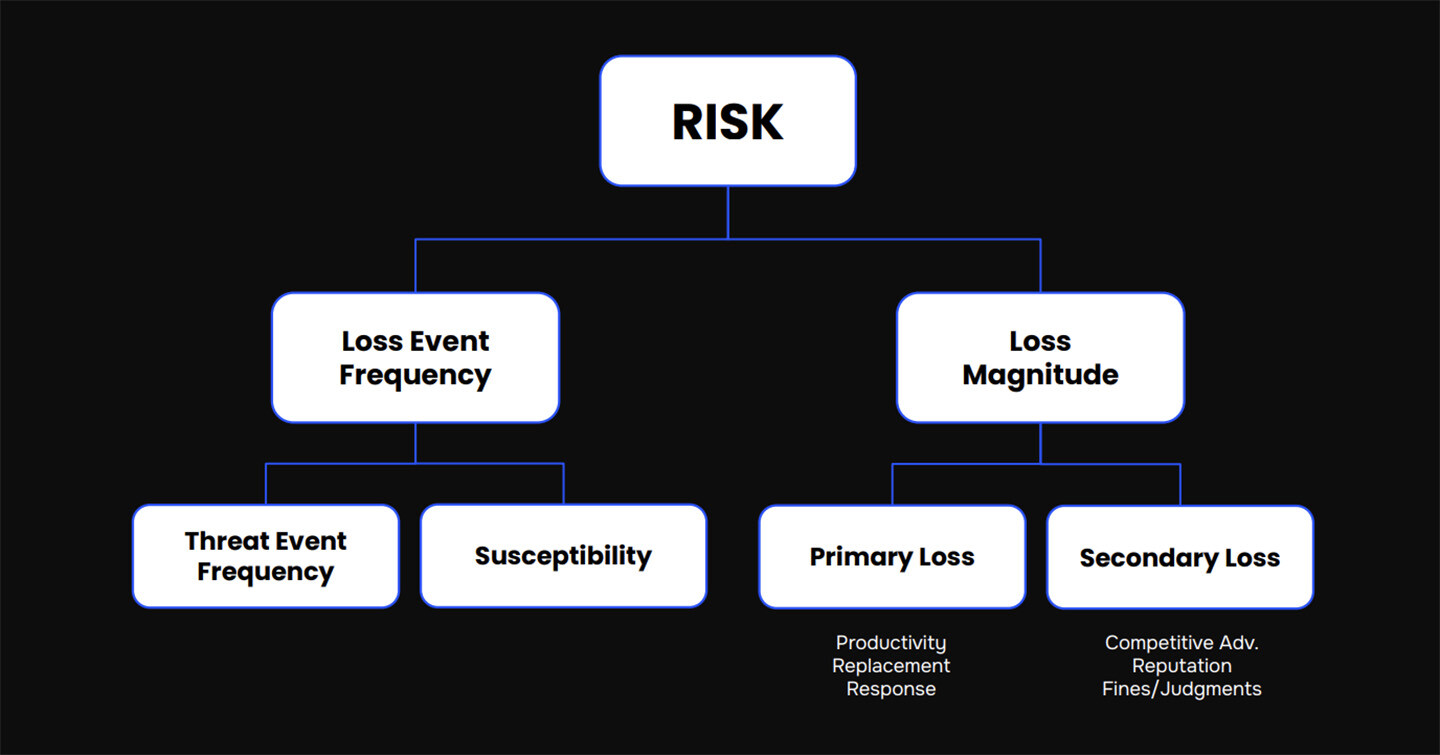
Image: Representation of FAIR Model
UNDERSTAND
- Understand the risk assessment methodology
- Understand the relevant risk scenarios
- Understand the likelihood and probable loss from those scenarios
Place the organization’s methodology on a spectrum from assessing risk qualitatively (say a vote by committee of risk managers) to a rigorous, software-assisted quantitative solution based on FAIR. Understand the confidence you can have in the organization’s risk data; ideally it comes from up-to-the-minute reporting from telemetry on threats plus carefully curated loss data for impact.
Define the risk scenarios, an exercise itself in cyber risk management maturity to identify the probable threat actors, assets at risk, controls in place and outcomes, all in a manner that most follows the way the business operates, for instance, by business unit or application.
The acid test: Can the business make reliable, defensible, risk-informed decisions?
Aligning with ISO 27005
The standard describes the steps here in FAIR-friendly terms, suggesting assessment of likelihood and impact and assigning a risk level. That’s followed by prioritizing risks then avoiding, mitigating, transferring or accepting each risk. Note that the standard does not prescribe a specific approach to analyzing risk and leaves it to risk practitioners to select their preferred analytics model.
How FAIR Helps
FAIR provides the process and structure to identify the key elements of cyber risk scenarios and more importantly quantifies the risk factors to produce scenarios in a range of probable outcomes. The FAIR Controls Analytics Model (FAIR-CAM) adds an extra layer of sophistication, assessing tools for their effectiveness in real time for the most accurate read on the likelihood of any scenario to cause a loss.
COMMUNICATE
- Reports and dashboards for internal and external stakeholders
- Continual risk visibility
- Real-time automated risk monitoring
Here we are really talking about tools to pull together Know and Understand and present cyber risk data to stakeholders in a non-technical, business-friendly, ROI-led mode that’s completely aligned with how everyone understands the business.
A real-time, continuous view of the organization’s risk posture sets this approach apart from the traditional risk assessments completed to satisfy ISO and other compliance authorities that capture risk at a point-in-time and are immediately outdated.
Aligning with ISO 27005
The standard is completely in sync here with best practices on communication, recommending regular risk assessments based on controls measurements and updates to treatment plans or risk registers.
How FAIR Helps
FAIR enables reporting to business stakeholders that answers their bottom-line questions: How likely are we to get hit with a particular cyber loss event? What is our loss exposure from an event or aggregated by business segment, application or other key concerns of management. With continuous updating from 1) the attack surface on the threat landscape and 2) the status of controls, a CISO can report at any time with confidence and in FAIR terms to stakeholders or the Board.
Reaching Cyber Risk Management Nirvana
While no CISO can hope for blissful peace of mind in today’s cybersecurity threat landscape, updating risk management practices along these Know-Understand-Communicate guidelines can serve up these benefits:
- Enterprise-wide visibility of risks based on existing controls and findings and external threat intel
- Confidence in communicating overall cyber risk to the Board, Executive Team and the business
- Alignment of risks and risk tolerance of the Board and Executive Team
- Benchmark risks in comparison to peers
- Easily meet regulatory reporting requirements
The SAFE risk management platform provides a complete set of FAIR-based use cases to guide your organization along the path of the Know/Understand/ Communicate maturity milestones. Contact Us for a Demo!



