Most Likely and Damaging Cyber Threats and Vulnerabilities in 2025
From AI to Zero Trust – Find your best mix of risk models, threat intel, real-time controls monitoring and risk posture
By Vidit Baxi
Headlines from the future…
“Misconfigured Software Update Leaves Electric Cars Unable to Start”
“Pharma Company Faces Ruin after Drug Formulas Leaked by Large Language Model”
“City Government in Fiscal Crisis as Ransomware Freezes Tax Collection”

Those risk scenarios hardly have the power to surprise anymore. In fact, by the time you’re reading this, they may already be in the news. It’s an easy prediction that…
- Rapidly evolving capabilities of threat actors and
- Rising interconnectivity and data flows among enterprises and third-party partners,
- All accelerated at full speed ahead by the application of artificial intelligence by both cyber attackers and defenders
…will make 2025 pretty much shields-up for 12 months.
Let’s take a look at how to prepare to meet the five top threats and vulnerabilities anticipated for 2025, and how we can assemble the best mix of risk assessment models, threat intelligence, real time monitoring of controls and risk posture to best inform mitigation and response strategies.
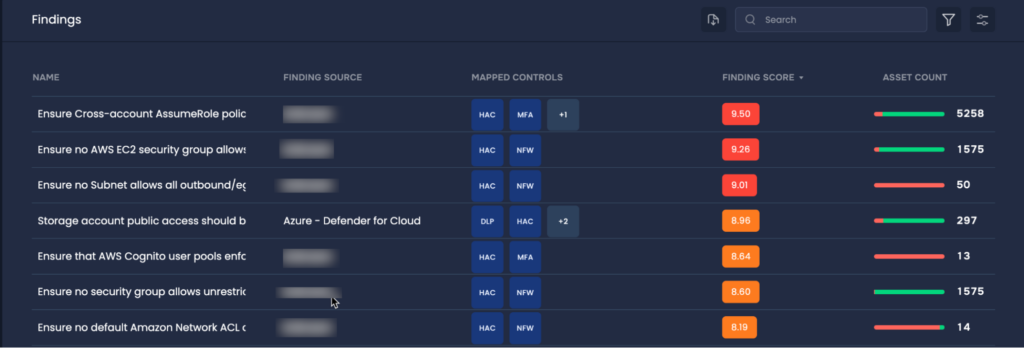
Real-time tracking of findings on the SAFE One Platform
1. Zero-Day Vulnerabilities and Exploits
Anticipated Landscape in 2025
Zero-day exploits—attacks that target previously unknown vulnerabilities—will likely continue to generate serious disruptions In 2025, the attack surface will expand further as organizations rely even more on interconnected devices, cloud infrastructure, and third-party applications. Generative AI (GenAI) has robust search capabilities that attackers will use to surface new zero days, as well as unpatched CVEs.
Threat Actors
Nation-states, hacktivists, and advanced persistent threat (APT) groups will continue to be power users of zero-days, for their own attacks or selling exploits on the black market. AI-powered zero-day hunting tools could “democratize” exploits for less sophisticated attackers, raising the threat level.
Recent Risk Scenarios
- A malicious WordPress plugin, PhishWP, turning legitimate websites into phishing traps
- New Mirai botnet leveraging zero-day vulnerabilities in industrial routers and smart home devices
- Phishing campaign exploiting legitimate PayPal address to hijack user accounts (January 2025)
Recommendations
Employ robust, real-time monitoring of threat actor activity and their TTPs through integrations with security tools. Generate probable risk scenarios with FAIR quantitative analysis. Prioritize risk scenarios based on severity of the vulnerability, age, exploitability and business impact – plan remediation accordingly.
Learn more in a SAFE whitepaper: Mastering Vulnerability Management
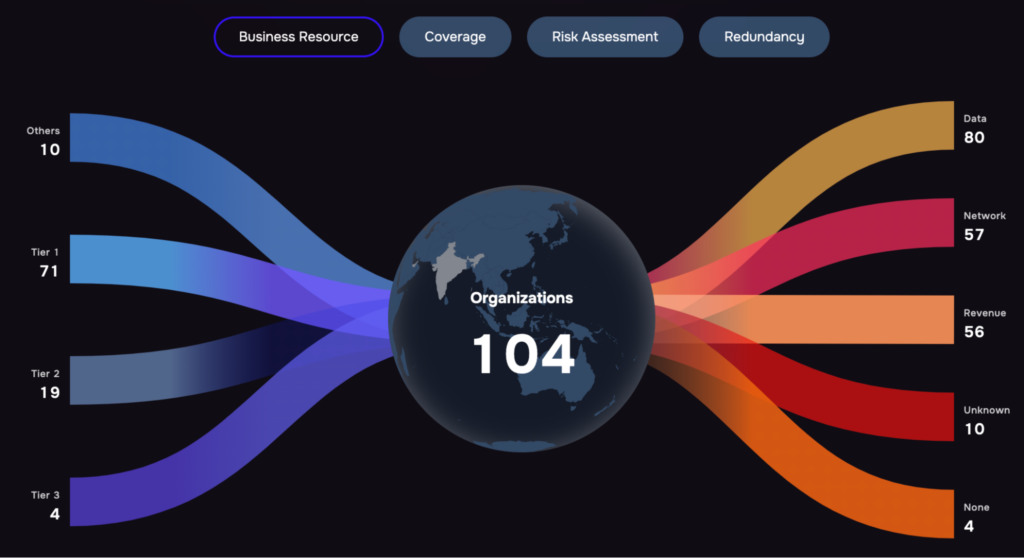
Third party risk management on the SAFE One platform
2. Supply Chain Vulnerabilities
Anticipated Landscape in 2025
Supply chain or third-party risk is on an upward trajectory in 2025, as attackers have figured out that vendors are typically easier to compromise than the large enterprises they serve – and it’s an open secret in the cybersecurity community that third party cyber risk management (TPRM) is broken. The standard tools – questionnaires filled out by the third party or outside-in scans of discoverable security tooling – fall far behind a fast-moving threat community. In 2025, the hyperconnectivity between businesses, suppliers, and service providers will amplify the threat environment
Threat Actors
Well-funded groups, including state-sponsored actors, are likely to prioritize supply chain attacks due to their high-impact potential and stealthiness. The SolarWinds breach served as the blueprint for similar advanced attacks. However, software flaws such as the CrowdStrike endpoint outage of 2024 showed how much damage a non-malicious, third party loss event can also cause.
Recent Risk Scenarios
- North Korean Pungsan group targeting developers via supply chain attack on npm ecosystem
- Salt Typhoon, a China-linked threat group, penetrating a wide range of US telcos apparently with the goal of accessing text and voice communication.
Recommendations
Consolidate data from outside-in scans, questionnaires, inside-out assessments and direct evidence such as phishing reports to create a unified view of risk posture for both the third party and the enterprise – then focus on a prioritized set of controls for maximum impact, leveraging FAIR analysis to discover best ROI.
Learn more in a SAFE whitepaper: TPRM Program Blueprint
3. Cloud Security Risks
Anticipated Landscape in 2025
Cloud adoption makes good business sense and will continue to be a popular solution for data and applications hosting in 2025. The risks of cloud deployment are well-known – and yet, obvious vulnerabilities get exploited year after year: bucket misconfigurations, identity access management failures, and insecure APIs.
Threat Actors
Criminal groups and opportunistic hackers are out there scanning for weak points.
Recent Risk Scenario:
- Reportedly, a hacker extorted $2.7 million in 2024 from customers of cloud services vendor Snowflake using unencrypted credentials harvested via infostealer malware, compounded by lack of MFA on Snowflake accounts.
Recommendations
Organizations should adopt “zero trust” principles, continuously authenticating access to cloud systems and providing real-time visibility into the enterprise’s internal resiliency controls for third parties.
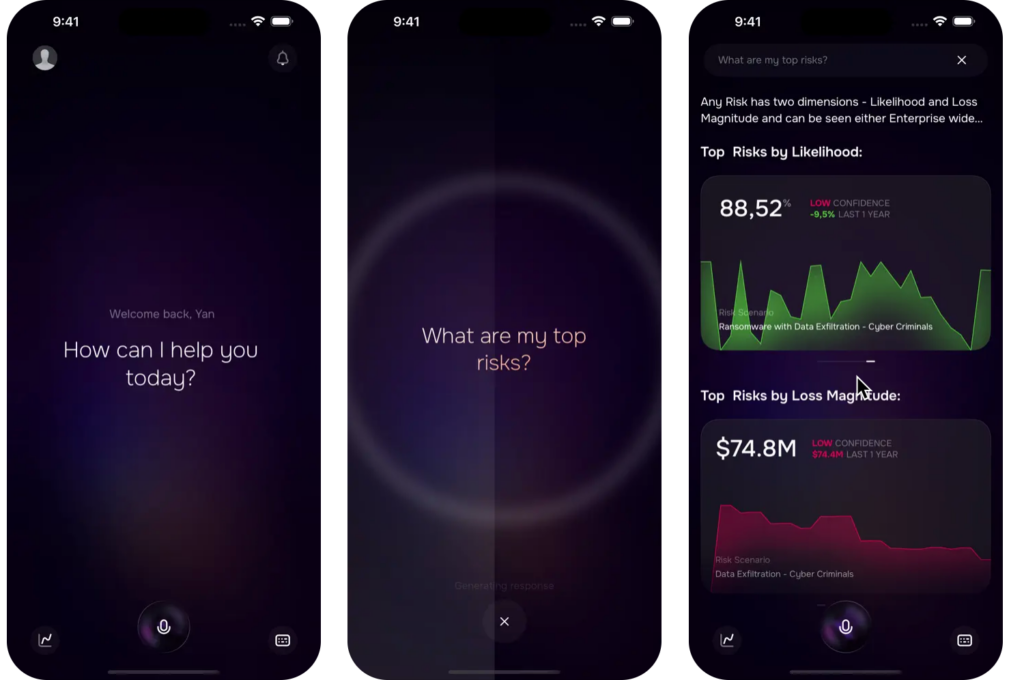
AI agent on SAFE X mobile app
4. AI in Cybersecurity Cuts Two Ways
Anticipated Landscape in 2025
AI on Offense
AI’s growing capabilities will empower threat actors to automate complex attack vectors, hunt for vulnerabilities at scale, and dynamically adapt messaging during cyber attacks. Equally challenging: Non-malicious but destructive use of AI by employees within the enterprise.
The FAIR Institute’s AI Approach Playbook details five vectors of risk originating in Generative AI:
1. Shadow GenAI,
2. Foundational Large Language Models (LLMs),
3. Hosting on LLMs,
4. Managed LLMs,
5. Active cyber attack.
Some sample risk scenarios from the AI Playbook:
Leaking company-sensitive information via an open-source LLM Models such as ChatGPT
LLM provider has weak security and attackers gain access to sensitive data via prompt injection.
Attacker uses AI to generate highly personal phishing emails
Attacker uses polymorphic malware engineered with AI to evolve and evade detection.
AI on Defense
On the positive side, organizations can harness AI to revolutionize cybersecurity defenses. Machine learning (ML) algorithms can process vast amounts of data in real time, detecting irregularities that might signal an attack. AI agents can automate routine cybersecurity tasks, such as onboarding third parties or patch management.
Recommendations
Design your AI systems with a security-first approach, specifically by assessing most probable risk scenarios to focus your efforts; FAIR-based analysis produces assessment in business-friendly, financial terms. The MIT Risk Repository, with over 1,000 scenarios categorized, is a good starting point. Assess your risk posture vs AI with the NIST AI-RMF framework to identify potential vulnerabilities and minimize compliance risk.
5. Ransomware
Anticipated Landscape in 2025
Ransomware will remain a top threat due to its profitability and low barriers of entry for amateur attackers. In 2025, expect to see attackers integrate AI to identify high-value targets, discover vulnerabilities, and even negotiate ransom payments with greater sophistication.
Threat Actors
Organized cybercrime groups, nation-state actors and ransomware-as-a-service (RaaS) operators will dominate the ransomware landscape. New affiliate models may emerge, incentivizing amateur hackers to launch ransomware campaigns.
Risk Scenarios:
Ransomware is complicated – typically, a risk scenario plays out in many steps. Most commonly it begins with phishing to induce a user to click on malware but could also begin with exploiting unpatched software or stolen credentials. It helps the attackers if – as in the case of the massive Change Healthcare hack of 2024 – the victim company operates without multi-factor authentication (MFA). Next, the intruder must run lateral movement through the network, perhaps using insecure remote desktop protocol (RDP) connections…find and encrypt high-value files…and contact the victims and negotiate a ransom. Increasingly common: double extortion, encrypting data then threatening public disclosure to up the ante on the payout.
Recommendations
Invest in robust incident response plans that outline steps for identifying, isolating, and remediating ransomware attacks. Here too, zero trust can be an indispensable practice. Regular backups and employee training also play a critical role in mitigating ransomware risks. Using FAIR for a quantitative understanding of potential ransomware attack costs helps guide insurance purchases and response planning.
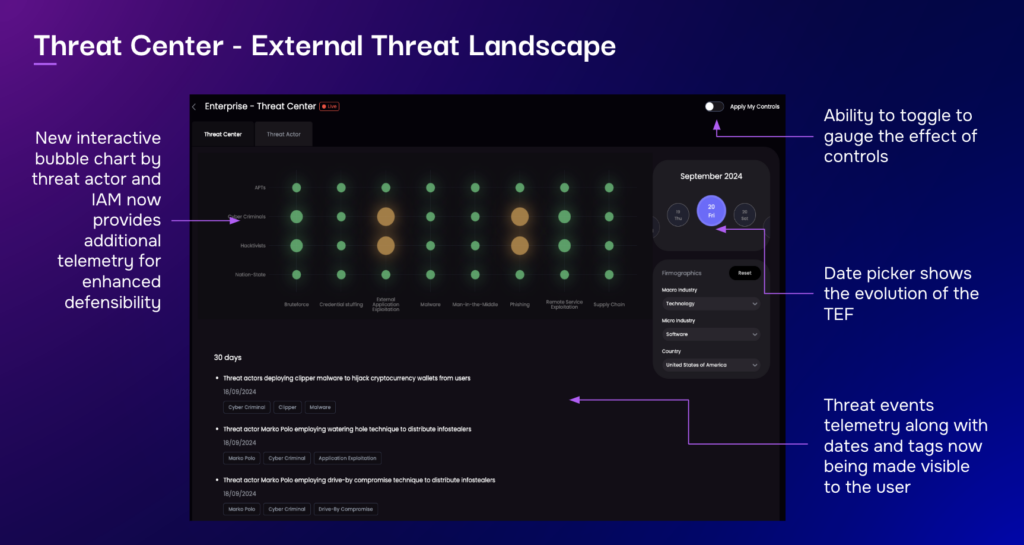
Introducing the SAFE Threat Center, Your Centralized Solution to Today’s Threat Environment
Faced with this this harsh landscape, cyber defenders operate with some critical liabilities:
- Scattered Threat Data: Security teams often rely on multiple tools, leading to fragmented threat information and inefficiencies.
- Delayed Response: Without centralized visibility, responding to critical threats can be slow, increasing the risk of breaches.
- Lack of Insights: It’s difficult to determine which threats are most critical, leading to wasted time on low-priority issues.
Organizations today need a centralized solution to monitor and act on threats effectively.
Introducing the SAFE Threat Center, a central hub that brings together all threat intelligence in one place with real-time insights into your risk.
How Threat Center Works
- Constant Threat Monitoring, scanning the landscape for malware, APTs and other threat as they develop
- Real-time Threat Updates, assessing the likelihood of a cyber event happening based on your specific business environment
- Tracking Hackers, monitoring known threat actor groups that target your organization
- Automated Risk Insights, generates automated insights into risk scenarios based on your vulnerabilities
See how the SAFE One Platform’s Threat Center protects your business from evolving cyber threats.
Schedule your 1:1 demo with a SAFE cyber risk expert today.



