Time to make the shift from compliance-driven, reactive approaches to continuous cyber risk management.
Third-party cyber breaches aren’t just a looming threat—they’re happening right now, and they’re costing businesses big. According to the SAFE 2025 Risk Radar report, a single cyberattack can slash up to 4.1% of quarterly revenue, while broader research suggests companies lose anywhere from 1-5% due to third-party vulnerabilities.
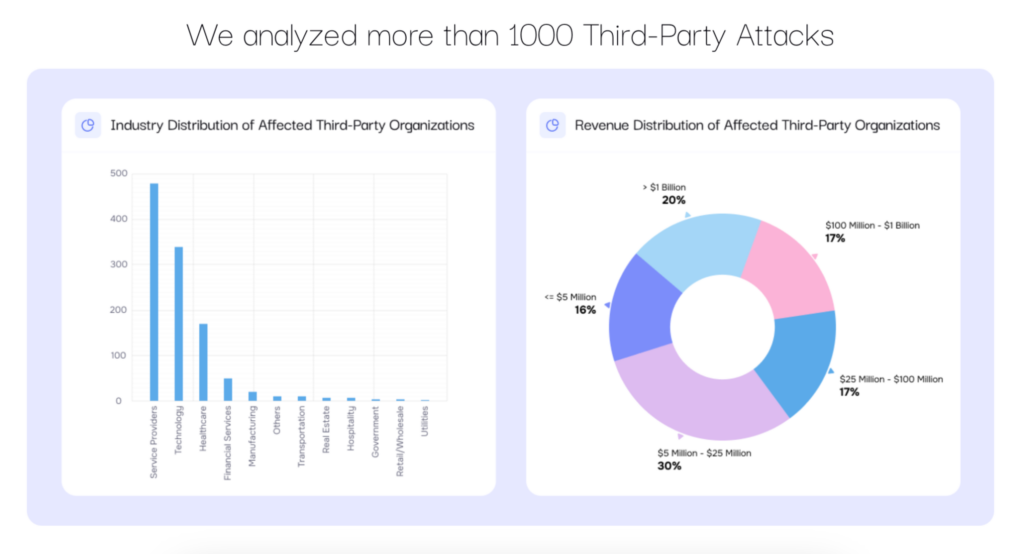
The SAFE Risk Radar Report, 2025
Despite the urgency, the current system is failing. Third-Party Risk Management (TPRM) is often reduced to a mere compliance checkbox exercise, with vendors getting approved long before security assessments are even completed. At the front lines of managing third-party cyber risks are practitioners dealing with vendors – their cybersecurity posture, managing their risk exposure, juggling compliance guidelines from across the globe, and more.
Risk practitioners run a gantlet of challenges, each more pressing than the last. In this post, we’ll uncover the top five obstacles in Third-Party Risk Management—and how you can tackle them head-on.
What Are the Top 5 Challenges in TPRM for a Practitioner?
1. Inefficient, Manual Assessments that Don’t Scale
With organizations relying on an average of 370 SaaS applications—and individual departments juggling 87 tools—the complexity of third-party risk assessments is skyrocketing. Yet, 69% of enterprises still manage their TPRM programs manually, forcing risk teams to spend countless hours tracking, analyzing, and updating vendor responses.
Instead of real-time insights, third-party risk practitioners are stuck sifting through static questionnaires, periodic scans, and compliance checklists. These outdated methods can’t match the speed or scale of modern vendor ecosystems, leaving organizations vulnerable and struggling to keep up with evolving risks.
2. Flawed Prioritization of Third Parties
Organizations often assess third-party cyber risk based on factors like geography, revenue size, and data access. However, in today’s fast-paced, SaaS-driven environment, this approach can miss the mark.
Large vendors typically have strong security programs, yet small-to-mid-sized vendors—who often lack the resources to invest in cybersecurity—account for 60% of data breaches (Verizon DBIR 2024). By prioritizing the wrong factors, businesses risk overlooking high-risk, low-visibility third parties, leaving critical gaps in their security posture.
3. Over-Reliance on Compliance
For many organizations, third-party risk assessments have become just another compliance exercise, dictated by regulatory requirements rather than real security concerns. The issue? Compliance doesn’t equal security.
Third-party risk practitioners and analysts agree – most compliance-driven assessments rely on generic Yes/No responses and fail to capture the true risk of exposure. Worse, as regulations become more stringent, businesses often treat TPRM as a bureaucratic hurdle rather than an opportunity to strengthen security postures. This mindset leaves organizations vulnerable—checking the right boxes but missing the real threats.
4. Too Many Findings, Not Enough Direction
As businesses expand their vendor networks, cybersecurity tools generate an overwhelming number of findings. Every security platform flags its own “critical risks”, creating a flood of alerts with little guidance on which issues matter most.
Risk practitioners are often left navigating an ocean of vulnerabilities, struggling to prioritize the most pressing threats. This challenge is only getting worse as attack surfaces grow—making it increasingly difficult to separate signal from noise and focus on the risks that truly impact business resilience.
5. Inefficient Vendor Collaboration that Slows Progress
Third-party risk management isn’t just about assessing and reporting risks—it requires ongoing collaboration to help vendors improve their security posture. But with hundreds of vendors to engage, risk teams face an overwhelming challenge: providing continuous, meaningful feedback at scale.
Meanwhile, vendors juggle risk requirements from multiple enterprises, often receiving scattered and conflicting instructions. Without a more efficient way to collaborate, risk practitioners struggle to track real-time changes in vendor risk posture and guide vendors toward the most impactful security improvements—rather than drowning them in low-priority tasks with minimal risk reduction.
SAFE Re-Imagines Third-Party Risk Management
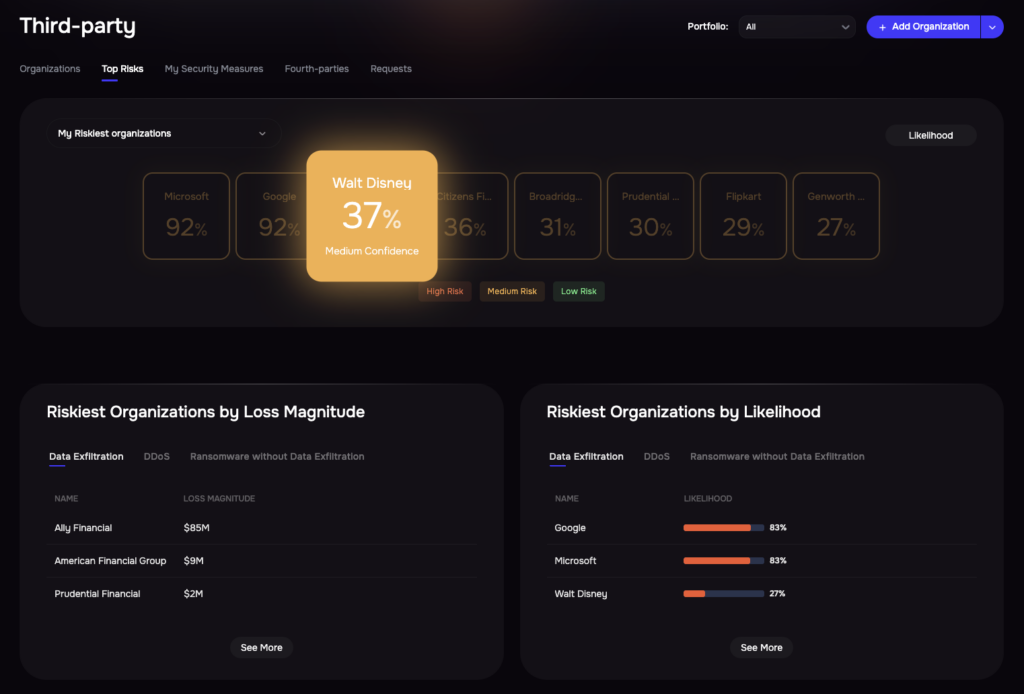
The challenges of third-party risk management demand a shift from compliance-driven, reactive approaches towards a continuous cyber risk management. That’s where SAFE’s Third-Party Risk Management (TPRM) solution comes in.
Instead of relying on outdated assessments, the SAFE One platform delivers an AI-driven, scalable, and continuous approach to vendor risk management. With automation, dynamic risk monitoring, and deep intelligence, SAFE enables businesses to identify, quantify, and mitigate third-party cyber risks before they escalate into costly breaches.
SAFE TPRM features:
✅ AI-Driven Cyber Risk Management – Eliminate redundancies, reduce operational overhead by up to 90% with SAFE’s AI agents, automating repetitive tasks so your team can focus on what truly matters—reducing cyber risk.
✅ Risk-Based Prioritization – Instantly identify and prioritize high-risk third parties, enabling faster risk mitigation and smarter resource allocation.
✅ Automated Compliance & Reporting – Stay compliant with minimal effort as AI handles questionnaire ingestion, analysis, and vendor feedback—reducing manual workload.
✅ Continuous Monitoring – AI-driven automation continuously detects, assesses, and mitigates third-party risks in real time.
✅ Seamless Third-Party Enablement – Empower your vendors with AI-driven recommendations, helping them prioritize actions and strengthen security.
SAFE completely automates third-party onboarding, due diligence and continuous monitoring, transforming vendor interaction workflows, helping businesses move at the speed of growth. Re-imagine your Cyber TPRM approach with Safe. Schedule your demo with one of our cyber experts today.



