NIS2 Directive: How to Use SAFE to Be Compliant on Cybersecurity Risk Program Requirements
Effectively manage risk, ensure business continuity, and fulfill reporting obligations with this detailed guide.
By Jacqueline Lebo and Akash Jain
Executive Summary
The NIS2 Directive introduces stringent cybersecurity risk management requirements for essential and important entities within the EU. This document outlines how the SAFE platform can assist organizations in achieving and maintaining compliance with these regulations. By leveraging SAFE’s capabilities, organizations can effectively implement the necessary technical, operational, and organizational measures to manage cybersecurity risks, ensure business continuity, and fulfill reporting obligations. This paper provides a detailed mapping of NIS2 requirements to SAFE’s functionalities, enabling a structured and data-driven approach to compliance.
Learn more in a webinar on demand:
Regulatory Wake Up Call: How to Strategically Meet NIS2 and DORA Requirements
Chapter 1
The NIS2 Requirements on Cybersecurity Risk Programs
What Is the NIS2 Directive?
The NIS2 Directive mandates a comprehensive approach to cybersecurity risk management, emphasizing proactive measures and continuous monitoring. Key articles within NIS2 define the requirements for governance, risk management, and reporting.
Article 20: Governance
- 20.1: Requires management bodies to approve, oversee, and be liable for cybersecurity risk-management measures.
- 20.2: Mandates regular cybersecurity training for management and encourages employee training.
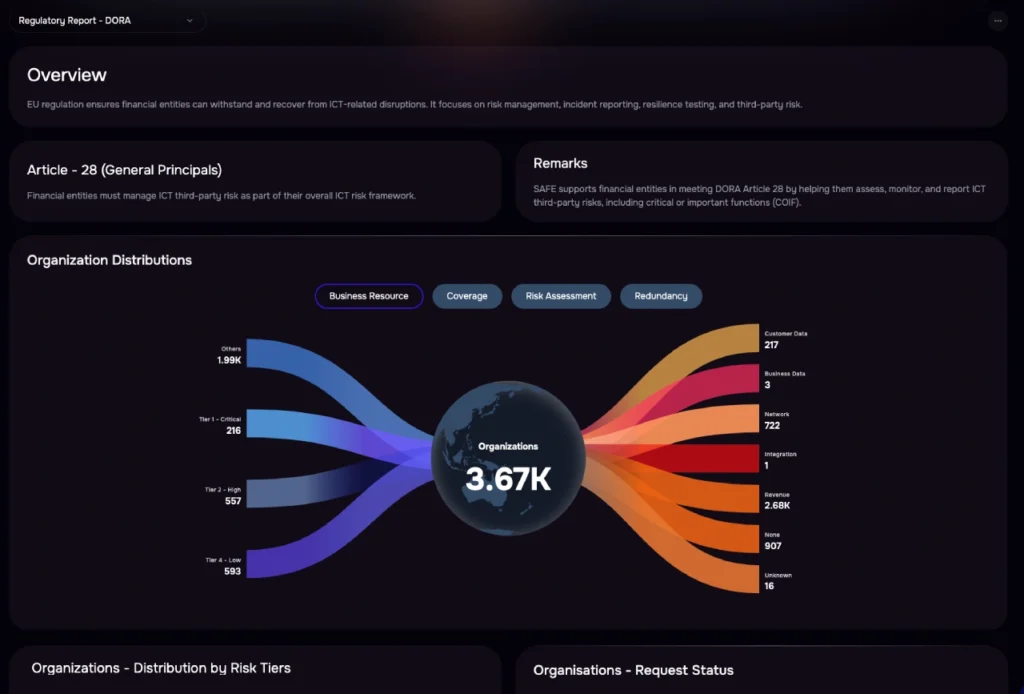
Third-party risk management with the SAFE platform. Learn more about TPRM.
Article 21: Cybersecurity Risk Management Measures
- 21.1: Organizations must implement appropriate and proportionate technical, operational, and organizational measures to manage risks.
- 21.2: Measures must be based on an all-hazards approach, including:
- (a) Risk analysis and information system security policies.
- (b) Incident handling.
- (c) Business continuity and crisis management.
- (d) Supply chain security.
- (e) Security in network and information systems acquisition, development, and maintenance.
- (f) Effectiveness assessment of cybersecurity measures.
- (g) Basic cyber hygiene and cybersecurity training.
- (h) Cryptography and encryption policies.
- (i) Human resources security, access control, and asset management.
- (j) Multi-factor authentication or continuous authentication solutions.
- 21.3: Requires consideration of supplier vulnerabilities and overall cybersecurity practices.
- 21.4: Mandates prompt corrective measures for non-compliance.
- 21.5: Commission to adopt implementing acts for specific sectors.
Article 22: Union-Level Coordinated Security Risk Assessment of Critical Supply Chain
- 22.1: Cooperation Group may conduct coordinated security risk assessments.
- 22.2: Commission identifies critical ICT services, systems, and products for assessment.
Article 23: Incident Reporting
- 23.1-23.11: Details incident reporting requirements, timelines, and communication protocols.
Article 24: Use of European Cybersecurity Certification Schemes
24.1-24.3: Encourages and mandates the use of certified ICT products and services.
Article 25: Standardization
- 25.1-25.2: Encourages the use of European and international standards
Chapter 2
Compliance with NIS2 Requirements
The SAFE platform facilitates NIS2 compliance by providing:
- Financial quantification of cybersecurity risks for informed decision-making.
- Structured risk assessment, mitigation, and reporting capabilities.
- Continuous monitoring and real-time visibility into risk posture through agentic AI.
How SAFE Can Support Achieving Compliance with the NIS2 Directive
| Article | How SAFE Helps |
| Article 20, Governance – 1 Member States shall ensure that the management bodies of essential and important entities approve the cybersecurity risk-management measures taken by those entities in order to comply with Article 21, oversee its implementation, and can be held liable for infringements by the entities of that Article.The application of this paragraph shall be without prejudice to national law as regards the liability rules applicable to public institutions, as well as the liability of public servants and elected or appointed officials. | Advisory Support SAFE offers dashboards and risk insights to help management oversee key cybersecurity risks |
| Article 20, Governance – 2 Member States shall ensure that the members of the management bodies of essential and important entities are required to follow training, and shall encourage essential and important entities to offer similar training to their employees on a regular basis, in order that they gain sufficient knowledge and skills to enable them to identify risks and assess cybersecurity risk-management practices and their impact on the services provided by the entity. | Implements SAFE supports tracking of awareness levels and helps identify gaps for further training focus. |
| Article 21, Cybersecurity risk-management measures – 1 Member States shall ensure that essential and important entities take appropriate and proportionate technical, operational and organisational measures to manage the risks posed to the security of network and information systems which those entities use for their operations or for the provision of their services, and to prevent or minimise the impact of incidents on recipients of their services and on other services. Taking into account the state-of-the-art and, where applicable, relevant European and international standards, as well as the cost of implementation, the measures referred to in the first subparagraph shall ensure a level of security of network and information systems appropriate to the risks posed. When assessing the proportionality of those measures, due account shall be taken of the degree of the entity’s exposure to risks, the entity’s size and the likelihood of occurrence of incidents and their severity, including their societal and economic impact. | Implements SAFE enables a structured risk-based approach using threat management, vulnerability insights, and posture-based quantification of exposure across assets and environments. |
| Article 21, Cybersecurity risk-management measures – 2 The measures referred to in paragraph 1 shall be based on an all-hazards approach that aims to protect network and information systems and the physical environment of those systems from incidents, and shall include at least the following:(a) policies on risk analysis and information system security; (b) incident handling; (c) business continuity, such as backup management and disaster recovery, and crisis management; (d) supply chain security, including security-related aspects concerning the relationships between each entity and its direct suppliers or service providers; (e) security in network and information systems acquisition, development, and maintenance, including vulnerability handling and disclosure; (f) policies and procedures to assess the effectiveness of cybersecurity risk-management measures; (g) basic cyber hygiene practices and cybersecurity training; (h) policies and procedures regarding the use of cryptography and, where appropriate, encryption; (i) human resources security, access control policies, and asset management; (j) the use of multi-factor authentication or continuous authentication solutions, secured voice, video,o and text communications, and secured emergency communication systems within the entity, where appropriate. | Informs SAFE supports holistic risk mitigation via capabilities such as CAM controls. |
| Article 21, Cybersecurity risk-management measures – 3 Member States shall ensure that, when considering which measures referred to in paragraph 2, point (d), of this Article are appropriate, entities take into account the vulnerabilities specific to each direct supplier and service provider and the overall quality of products and cybersecurity practices of their suppliers and service providers, including their secure development procedures. Member States shall also ensure that, when considering which measures referred to in that point are appropriate, entities are required to take into account the results of the coordinated security risk assessments of critical supply chains carried out in accordance with Article 22(1). | Implements. SAFE assesses supplier security posture using its Third party Risk Management module and enables tracking of third-party risks through ecosystem mapping and dependency analysis. |
| Article 21, Cybersecurity risk-management measures – 4 Member States shall ensure that an entity that finds that it does not comply with the measures provided for in paragraph 2 takes, without undue delay, all necessary, appropriate and proportionate corrective measures. | Implements SAFE assists in prioritizing remediation based on quantified risk impact, helping organizations meet compliance expectations |
| Article 21, Cybersecurity risk-management measures – 5 By 17 October 2024, the Commission shall adopt implementing acts laying down the technical and the methodological requirements of the measures referred to in paragraph 2 with regard to DNS service providers, TLD name registries, cloud computing service providers, data centre service providers, content delivery network providers, managed service providers, managed security service providers, providers of online market places, of online search engines and of social networking services platforms, and trust service providers. The Commission may adopt implementing acts laying down the technical and the methodological requirements, as well as sectoral requirements, as necessary, of the measures referred to in paragraph 2 with regard to essential and important entities other than those referred to in the first subparagraph of this paragraph.When preparing the implementing acts referred to in the first and second subparagraphs of this paragraph, the Commission shall, to the extent possible, follow European and international standards, as well as relevant technical specifications. The Commission shall exchange advice and cooperate with the Cooperation Group and ENISA on the draft implementing acts in accordance with Article 14(4), point (e).Those implementing acts shall be adopted in accordance with the examination procedure referred to in Article 39(2). | Informs SAFE provides visibility into what a significant incident would look like for an organization in order to better prepare for this type of reporting. It also provides a space for organizations to understand their risks |
| Article 22, Union level coordinated security risk assessments of critical supply chains – 1 The Cooperation Group, in cooperation with the Commission and ENISA, may carry out coordinated security risk assessments of specific critical ICT services, ICT systems, or ICT products supply chains, taking into account technical and, where relevant, non-technical risk factors. | Implements SAFE provides visibility into first-party and third-party risk assessment that can help in security assessment by cooperation group |
| Article 22, Union level coordinated security risk assessments of critical supply chains – 2 The Commission, after consulting the Cooperation Group and ENISA, and, where necessary, relevant stakeholders, shall identify the specific critical ICT services, ICT systems, or ICT products that may be subject to the coordinated security risk assessment referred to in paragraph 1. | Implements SAFE provides visibility into first-party and third-party risk assessment that can help in security assessment by cooperation group |
| Article 23, Reporting obligations – 1 Each Member State shall ensure that essential and important entities notify, without undue delay, its CSIRT or, where applicable, its competent authority in accordance with paragraph 4 of any incident that has a significant impact on the provision of their services as referred to in paragraph 3 (significant incident). Where appropriate, entities concerned shall notify, without undue delay, the recipients of their services of significant incidents that are likely to adversely affect the provision of those services. Each Member State shall ensure that those entities report, inter alia, any information enabling the CSIRT or, where applicable, the competent authority to determine any cross-border impact of the incident. The mere act of notification shall not subject the notifying entity to increased liability. Where the entities concerned notify the competent authority of a significant incident under the first subparagraph, the Member State shall ensure that that competent authority forwards the notification to the CSIRT upon receipt. In the case of a cross-border or cross-sectoral significant incident, Member States shall ensure that their single points of contact are provided in due time with relevant information notified in accordance with paragraph 4. | Informs SAFE provides visibility into the type of losses that can be experienced by incidents to assist in response efforts and planning. |
| Article 23, Reporting obligations – 2 Where applicable, Member States shall ensure that essential and important entities communicate, without undue delay, to the recipients of their services that are potentially affected by a significant cyber threat any measures or remedies that those recipients are able to take in response to that threat. Where appropriate, the entities shall also inform those recipients of the significant cyber threat itself. | Informs SAFE provides visibility into what a significant incident would look like for an organization in order to better prepare for this type of reporting. |
| Article 23, Reporting obligations – 3 An incident shall be considered to be significant if:(a) it has caused or is capable of causing severe operational disruption of the services or financial loss for the entity concerned;(b) it has affected or is capable of affecting other natural or legal persons by causing considerable material or non-material damage. | SAFE provides visibility into what a significant incident would look like for an organization in order to better prepare for this type of reporting. |
| Article 23, Reporting obligations – 4 Member States shall ensure that, for the purpose of notification under paragraph 1, the entities concerned submit to the CSIRT or, where applicable, the competent authority: (a) without undue delay and in any event within 24 hours of becoming aware of the significant incident, an early warning, which, where applicable, shall indicate whether the significant incident is suspected of being caused by unlawful or malicious acts or could have a cross-border impact; (b) without undue delay and in any event within 72 hours of becoming aware of the significant incident, an incident notification, which, where applicable, shall update the information referred to in point (a) and indicate an initial assessment of the significant incident, including its severity and impact, as well as, where available, the indicators of compromise; (c) upon the request of a CSIRT or, where applicable, the competent authority, an intermediate report on relevant status updates; (d) a final report not later than one month after the submission of the incident notification under point (b), including the following:(i) a detailed description of the incident, including its severity and impact;(ii) the type of threat or root cause that is likely to have triggered the incident;(iii) applied and ongoing mitigation measures;(iv) where applicable, the cross-border impact of the incident; (e) in the event of an ongoing incident at the time of the submission of the final report referred to in point (d), Member States shall ensure that entities concerned provide a progress report at that time and a final report within one month of their handling of the incident.By way of derogation from the first subparagraph, point (b), a trust service provider shall, with regard to significant incidents that have an impact on the provision of its trust services, notify the CSIRT or, where applicable, the competent authority, without undue delay and in any event within 24 hours of becoming aware of the significant incident. | Informs SAFE is capable of producing reporting with the FAIR Framework that drives a risk based approach to any progress post incident and specifically hone in on controls that are most impactful to reducing risk. |
Article 23, Reporting obligations – 5 The CSIRT or the competent authority shall provide, without undue delay and where possible within 24 hours of receiving the early warning referred to in paragraph 4, point (a), a response to the notifying entity, including initial feedback on the significant incident and, upon request of the entity, guidance or operational advice on the implementation of possible mitigation measures. Where the CSIRT is not the initial recipient of the notification referred to in paragraph 1, the guidance shall be provided by the competent authority in cooperation with the CSIRT. The CSIRT shall provide additional technical support if the entity concerned so requests. Where the significant incident is suspected to be of criminal nature, the CSIRT or the competent authority shall also provide guidance on reporting the significant incident to law enforcement authorities. | Informs SAFE can assist in this scenario by providing a centralized platform to document and analyze the financial impact of “significant incidents” reported to CSIRTs or competent authorities. It enables organizations to quantify potential losses and prioritize mitigation measures, facilitating faster, more informed responses within the 24-hour timeframe. Moreover, SAFE’s reporting capabilities can generate evidence-based documentation to support communication with law enforcement, especially when criminal activity is suspected, aiding in the reporting process. |
| Article 23, Reporting obligations – 6 Where appropriate, and in particular where the significant incident concerns two or more Member States, the CSIRT, the competent authority or the single point of contact shall inform, without undue delay, the other affected Member States and ENISA of the significant incident. Such information shall include the type of information received in accordance with paragraph 4. In so doing, the CSIRT, the competent authority or the single point of contact shall, in accordance with Union or national law, preserve the entity’s security and commercial interests as well as the confidentiality of the information provided. | Informs SAFE can assist in this scenario by providing a centralized platform to document and analyze the financial impact of “significant incidents” reported to CSIRTs or competent authorities. It enables organizations to quantify potential losses and prioritize mitigation measures, facilitating faster, more informed responses within the 24-hour timeframe. Moreover, SAFE’s reporting capabilities can generate evidence-based documentation to support communication with law enforcement, especially when criminal activity is suspected, aiding in the reporting process. |
Article 23, Reporting obligations – 7 Where public awareness is necessary to prevent a significant incident or to deal with an ongoing significant incident, or where disclosure of the significant incident is otherwise in the public interest, a Member State’s CSIRT or, where applicable, its competent authority, and, where appropriate, the CSIRTs or the competent authorities of other Member States concerned, may, after consulting the entity concerned, inform the public about the significant incident or require the entity to do so. | Informs SAFE can assist in this scenario by providing a centralized platform to document and analyze the financial impact of “significant incidents” reported to CSIRTs or competent authorities. It enables organizations to quantify potential losses and prioritize mitigation measures, facilitating faster, more informed responses within the 24-hour timeframe. Moreover, SAFE’s reporting capabilities can generate evidence-based documentation to support communication with law enforcement, especially when criminal activity is suspected, aiding in the reporting process. |
| Article 23, Reporting obligations – 8 At the request of the CSIRT or the competent authority, the single point of contact shall forward notifications received pursuant to paragraph 1 to the single points of contact of other affected Member States. | N/A |
| Article 23, Reporting obligations – 9 The single point of contact shall submit to ENISA every three months a summary report, including anonymised and aggregated data on significant incidents, incidents, cyber threats and near misses notified in accordance with paragraph 1 of this Article and with Article 30. In order to contribute to the provision of comparable information, ENISA may adopt technical guidance on the parameters of the information to be included in the summary report. ENISA shall inform the Cooperation Group and the CSIRTs network about its findings on notifications received every six months. | N/A |
| Article 23, Reporting obligations – 10 The CSIRTs or, where applicable, the competent authorities shall provide to the competent authorities under Directive (EU) 2022/2557 information about significant incidents, incidents, cyber threats and near misses notified in accordance with paragraph 1 of this Article and with Article 30 by entities identified as critical entities under Directive (EU) 2022/2557. | N/A |
| Article 23, Reporting obligations – 11 The Commission may adopt implementing acts further specifying the type of information, the format and the procedure of a notification submitted pursuant to paragraph 1 of this Article and to Article 30 and of a communication submitted pursuant to paragraph 2 of this Article. By 17 October 2024, the Commission shall, with regard to DNS service providers, TLD name registries, cloud computing service providers, data centre service providers, content delivery network providers, managed service providers, managed security service providers, as well as providers of online marketplaces, of online search engines and of social networking services platforms, adopt implementing acts further specifying the cases in which an incident shall be considered to be significant as referred to in paragraph 3. The Commission may adopt such implementing acts with regard to other essential and important entities.The Commission shall exchange advice and cooperate with the Cooperation Group on the draft implementing acts referred to in the first and second subparagraphs of this paragraph in accordance with Article 14(4), point (e).Those implementing acts shall be adopted in accordance with the examination procedure referred to in Article 39(2). | Informs SAFE can support compliance with these upcoming implementing acts by providing a flexible framework to adapt to the specified information types, formats, and procedures for incident notifications and communications. It enables organizations to quantify the financial impact of incidents, aligning with the “significant” incident definitions that will be specified for various digital service providers by October 2024. Furthermore, SAFE’s reporting functionality can be configured to generate reports in the required formats, facilitating efficient communication with authorities and supporting the examination procedures outlined in Article 39(2). |
| Article 24, Use of European cybersecurity certification schemes – 1 In order to demonstrate compliance with particular requirements of Article 21, Member States may require essential and important entities to use particular ICT products, ICT services and ICT processes, developed by the essential or important entity or procured from third parties, that are certified under European cybersecurity certification schemes adopted pursuant to Article 49 of Regulation (EU) 2019/881. Furthermore, Member States shall encourage essential and important entities to use qualified trust services. | Implements SAFE can quantify the financial risk associated with non-compliance by modeling the potential impact of vulnerabilities in uncertified ICT products and services, aligning with Article 21’s requirements. It allows organizations to prioritize investments in certified alternatives and qualified trust services by demonstrating their risk reduction value in monetary terms. Finally, SAFE’s continuous monitoring capabilities provide evidence of ongoing compliance efforts, supporting audits and regulatory reporting. |
| Article 24, Use of European cybersecurity certification schemes – 2 The Commission is empowered to adopt delegated acts, in accordance with Article 38, to supplement this Directive by specifying which categories of essential and important entities are to be required to use certain certified ICT products, ICT services and ICT processes or obtain a certificate under a European cybersecurity certification scheme adopted pursuant to Article 49 of Regulation (EU) 2019/881. Those delegated acts shall be adopted where insufficient levels of cybersecurity have been identified and shall include an implementation period.Before adopting such delegated acts, the Commission shall carry out an impact assessment and shall carry out consultations in accordance with Article 56 of Regulation (EU) 2019/881. | Informs SAFE can help organizations prepare for and respond to these potential delegated acts by providing a risk-based framework to assess the current cybersecurity posture of their ICT products, services, and processes. This allows for proactive identification of areas needing certification, aligning with the Commission’s intent to address “insufficient levels of cybersecurity.” By quantifying the financial impact of potential non-compliance and demonstrating the risk reduction benefits of certified solutions, SAFE supports informed decision-making during the implementation period mandated by the delegated acts. |
| Article 24, Use of European cybersecurity certification schemes – 3 Where no appropriate European cybersecurity certification scheme for the purposes of paragraph 2 of this Article is available, the Commission may, after consulting the Cooperation Group and the European Cybersecurity Certification Group, request ENISA to prepare a candidate scheme pursuant to Article 48(2) of Regulation (EU) 2019/881. | N/A |
| Article 25, Standardisation – 1 In order to promote the convergent implementation of Article 21(1) and (2), Member States shall, without imposing or discriminating in favour of the use of a particular type of technology, encourage the use of European and international standards and technical specifications relevant to the security of network and information systems. | Implements FAIR is an international standard for managing risk. the SAFE platform implements a FAIR-based methodology to risk management. |
| Article 25, Standardisation – 2 ENISA, in cooperation with Member States, and, where appropriate, after consulting relevant stakeholders, shall draw up advice and guidelines regarding the technical areas to be considered in relation to paragraph 1 as well as regarding already existing standards, including national standards, which would allow for those areas to be covered. | N/A |
Learn more about regulatory compliance with SAFE.

Cyber risk quantification with the FAIR model on the SAFE One platform.
Chapter 3
Compliance with NIS2: Building a Roadmap with the SAFE Platform
Compliance with NIS2: Building a Roadmap with the SAFE Platform
Building a robust Cybersecurity Risk Management Program aligned with NIS2 is an ongoing journey. Organizations operate at varying levels of maturity, and the target state should be tailored to their specific needs and risk profiles. The SAFE platform facilitates this journey, enabling organizations to achieve and maintain NIS2 compliance. Here’s a structured approach for CISOs and GRC leaders:
Step 0: Defining the “Why” and Securing Stakeholder Alignment
Begin by articulating the rationale for pursuing NIS2 compliance and a robust CRMP. This “Why” should resonate with stakeholders and can encompass:
- Enhancing cybersecurity resilience and responsiveness to meet NIS2 requirements.
- Establishing a data-driven framework for informed decision-making.
- Optimizing cybersecurity investments for better ROI.
- Improving cyber insurance coverage.
- Meeting the specific governance and reporting obligations of NIS2.
Document the “Why” and ensure alignment among key stakeholders. Without this foundational agreement, implementation efforts may falter.
Step 1: Assessing Current Maturity Against NIS2 Requirements
We recommend using the NIST CSF 2.0 as the framework to assess the current maturity of your organization. Even if you don’t use the broader NIST CSF framework, we think that it does a good job of defining the maturity requirements. Use the definitions of the implementation tiers, as defined in the white paper by the FAIR Institute, to workshop the current maturity state of your program. Involve the relevant stakeholders. This assessment should:
- Identify gaps in alignment with NIS2’s mandated technical, operational, and organizational measures (Article 21).
- Evaluate existing risk management practices against NIS2’s risk assessment and reporting obligations (Articles 21, 23).
- Determine the current state of supply chain security in relation to NIS2’s requirements (Article 21.3, 22).
- Analyze current training programs versus NIS2’s training requirements for management and employees (Article 20.2, 21.2.g).
- Involve relevant stakeholders in the assessment process to ensure a comprehensive understanding of the organization’s current state.
Step 2: Defining and Aligning on the Target Maturity State for NIS2 Compliance
Establish the desired end state for cybersecurity maturity, considering NIS2’s specific requirements. This involves:
- Setting realistic and achievable goals for each NIS2 requirement.
- Prioritizing areas that require immediate attention to address critical compliance gaps.
- Considering the organization’s risk tolerance, operational complexity, and the evolving threat landscape.
- Do not allow resource constraints to limit the discussion of the ideal target state. These constraints should be addressed in the execution plan.
Step 3: Identifying and Empowering Responsible Owners
Assign clear ownership for each workstream related to NIS2 compliance. Ensure that:
- Owners are incentivized to achieve their assigned objectives.
- Owners are granted the necessary authority and resources to fulfill their responsibilities.
- The SAFE platform can assist owners by providing clear visibility into risk, and progress toward goals.
Step 4: Developing a Sprint-Based Execution Plan for NIS2 Compliance
Create a tactical execution plan that:
- Breaks down NIS2 compliance efforts into manageable sprints.
- Identifies dependencies between different workstreams.
- Establishes clear timelines and milestones.
- Consider utilizing a dedicated program manager to oversee the execution plan.
- The SAFE platform can assist in tracking progress, and providing data to support the execution plan.
FAQ
What is the NIS regulation 2? NIS2
(Network and Information Security 2) is the European Union’s updated directive that significantly expands and strengthens cybersecurity requirements for a wider range of critical sectors and digital service providers across the EU, replacing its predecessor NIS1.
Is there a US equivalent to NIS2?
While the US has various cybersecurity regulations and frameworks like NIST CSF, CISA’s critical infrastructure guidance, and SEC’s cybersecurity disclosure rules, there isn’t one single, comprehensive US equivalent to the broad, mandatory, and harmonized scope of NIS2 across critical sectors.
What is the difference between NIST and NIS2?
NIST (National Institute of Standards and Technology) develops voluntary cybersecurity frameworks and guidelines, primarily for U.S. federal agencies and industry, whereas NIS2 is a mandatory EU Directive that sets specific legal obligations and a common baseline for cybersecurity across critical entities in EU member states.
Is NIS2 mandatory?
Yes, NIS2 is mandatory for medium and large entities operating in designated “essential” and “important” critical sectors within the EU, or those providing services to EU markets, requiring them to implement specific cybersecurity risk management measures and incident reporting.
What do I need to do to be NIS2 compliant?
To be NIS2 compliant, organizations must adopt a risk-based approach to cybersecurity, implement specific technical and organizational risk management measures (e.g., incident handling, supply chain security, MFA), establish strict incident reporting procedures, and ensure management oversight and accountability.
Conclusion
Building a continuous Cybersecurity Risk Management Program aligned with NIS2 is essential for organizations within the EU. The SAFE platform provides the necessary tools and capabilities to achieve and maintain compliance, enabling organizations to effectively manage cybersecurity risks and meet their regulatory obligations. By following a structured roadmap, CISOs and GRC leaders can leverage SAFE to enhance their cybersecurity posture and ensure ongoing compliance with NIS2.
Appendix: Achieving Compliance with a Robust Cybersecurity Risk Program
A robust cybersecurity risk program not only facilitates NIS2 compliance but also supports adherence to other relevant frameworks, including:
- ISO 27001 (International Organization for Standardization): Provides a framework for information security management systems (ISMS), aligning with NIS2’s emphasis on risk management and security controls.
- ISACA COBIT 2019: Offers a governance framework that aligns IT security with business objectives, supporting NIS2’s governance requirements.
- AICPA TSC SOC 2: Addresses data management based on trust service criteria, relevant to NIS2’s focus on data security and availability.
- PCI DSS (Payment Card Industry Data Security Standard): Ensures secure handling of cardholder data, crucial for organizations processing payment transactions.
- HITRUST CSF (Health Information Trust Alliance Common Security Framework): Provides a comprehensive security framework for the healthcare industry, integrating various standards including NIST and ISO.
- FFIEC Cybersecurity Assessment Tool: Designed for the financial sector, assisting institutions in assessing their cybersecurity maturity.
- GDPR (General Data Protection Regulation) & CCPA (California Consumer Privacy Act): While focused on data privacy, these regulations reinforce the importance of robust cybersecurity measures, which are also mandated by NIS2.



