Introducing
Focus On Third-Party Cyber Risks That Really Matter with FAIR-Third Party Analytics Model.


SAFE Solution Highlights
Tier vendors based on the risk they pose: the financial impact and likelihood of cyber attacks
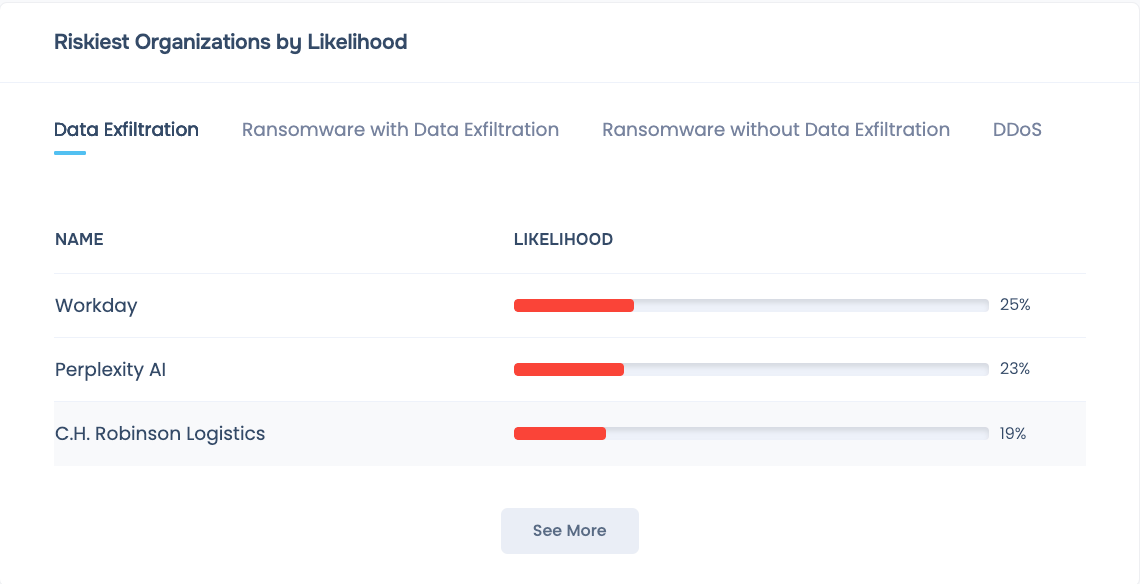
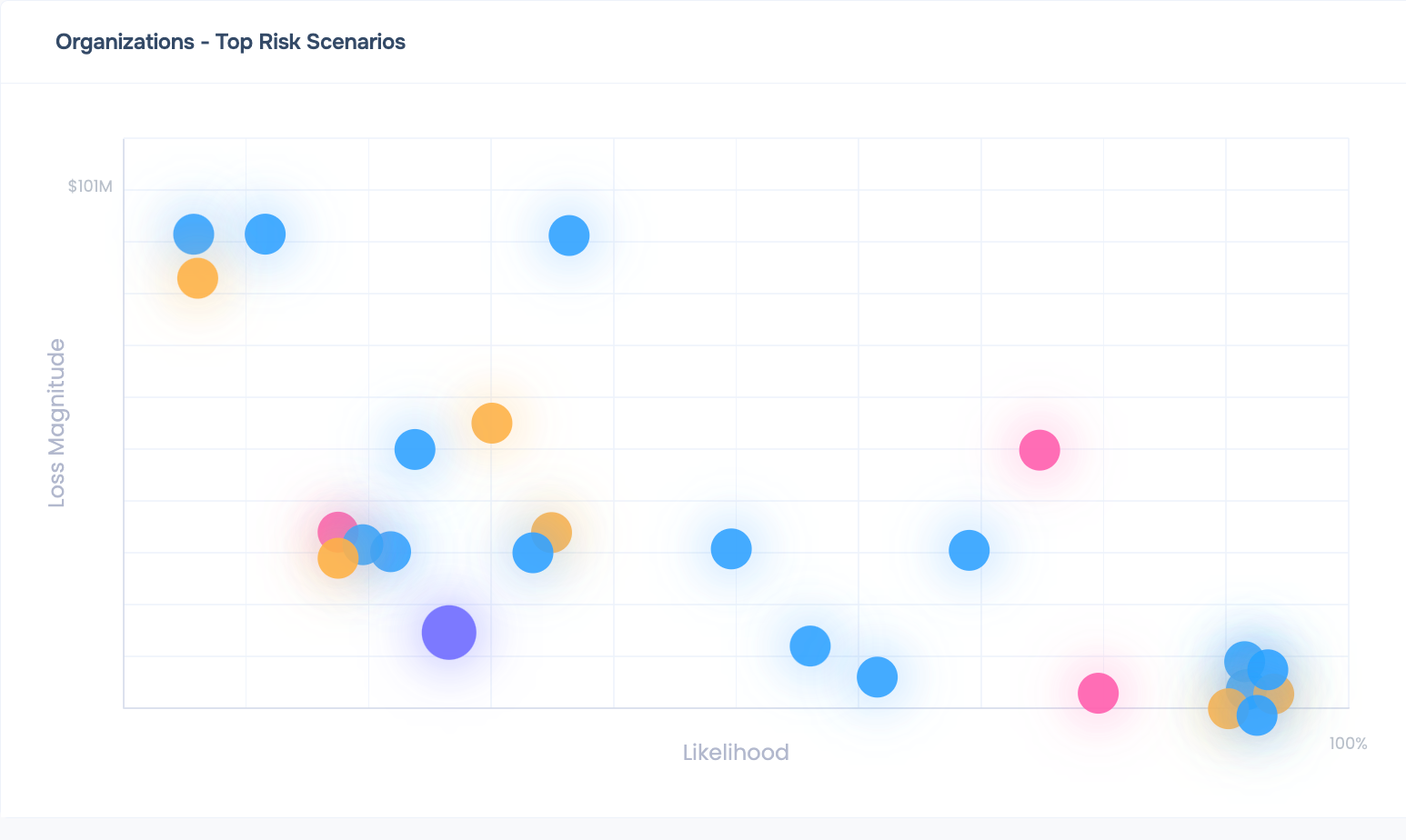
Build or customize cyber risk scenarios for to quantify risks from ransomware attacks, data exfiltration, DDoS, etc
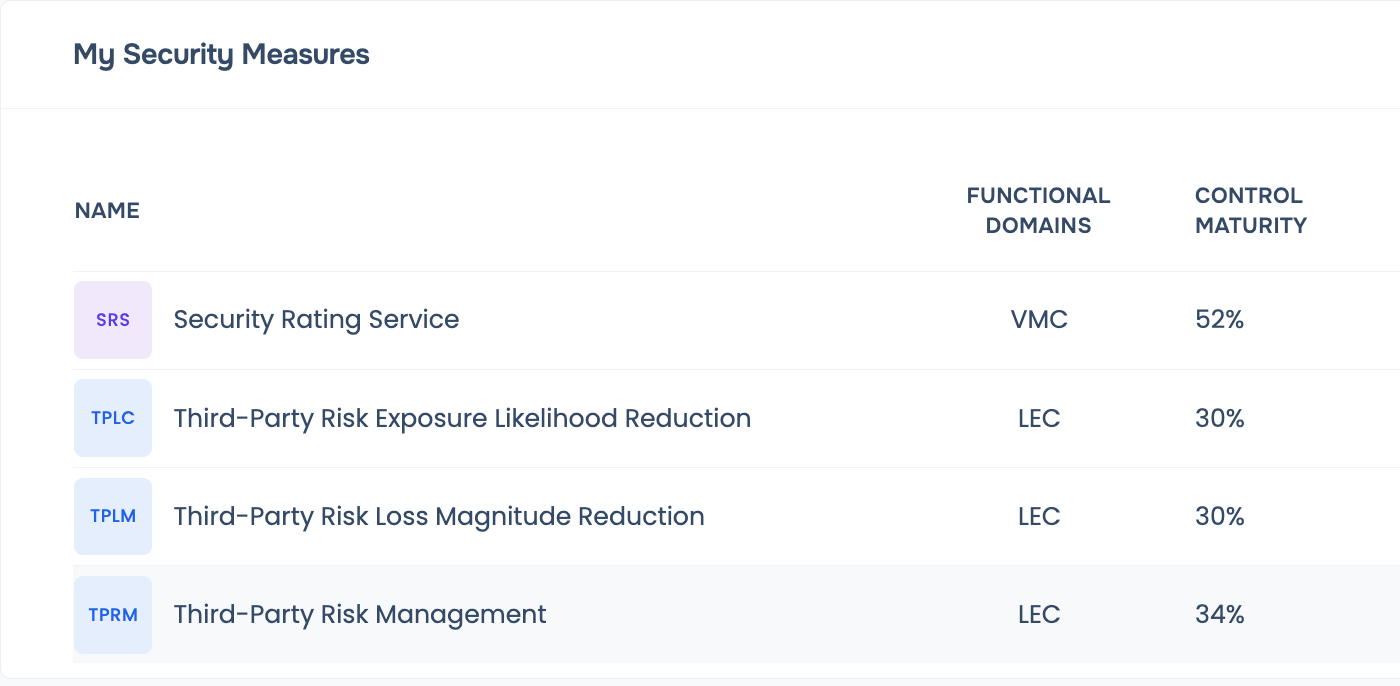
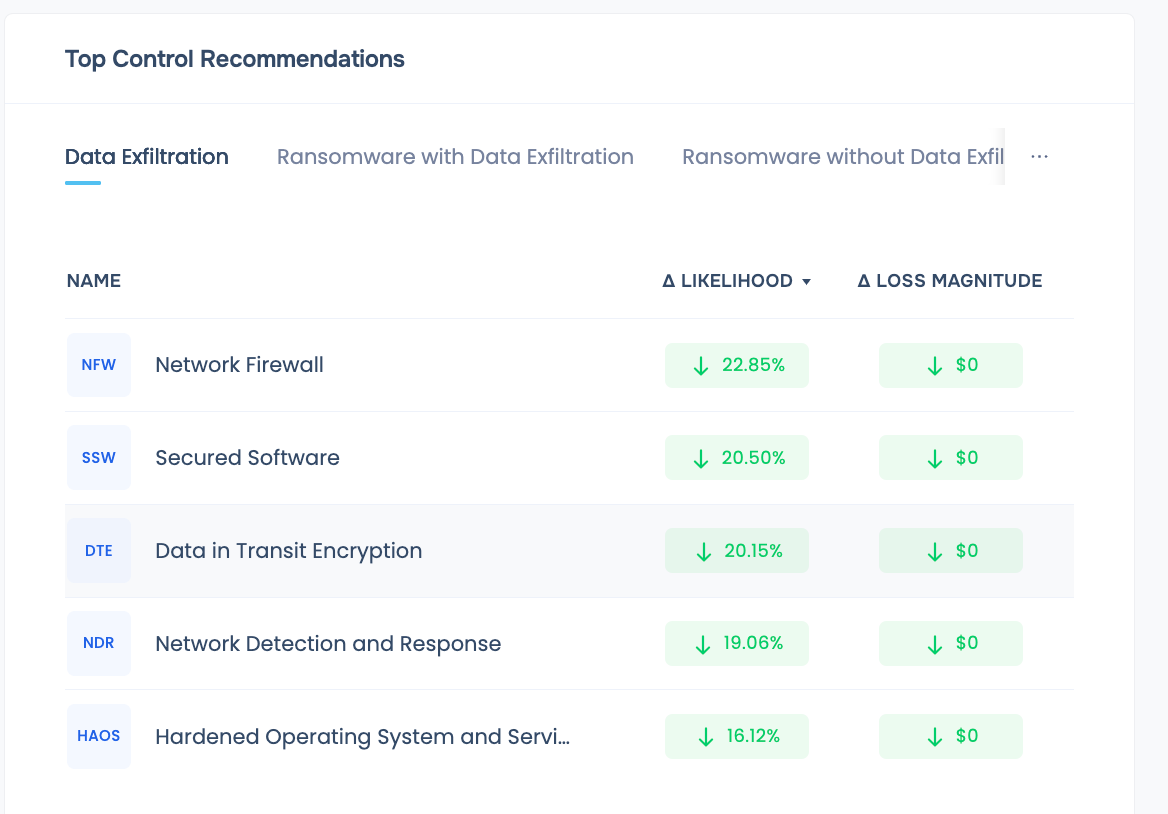
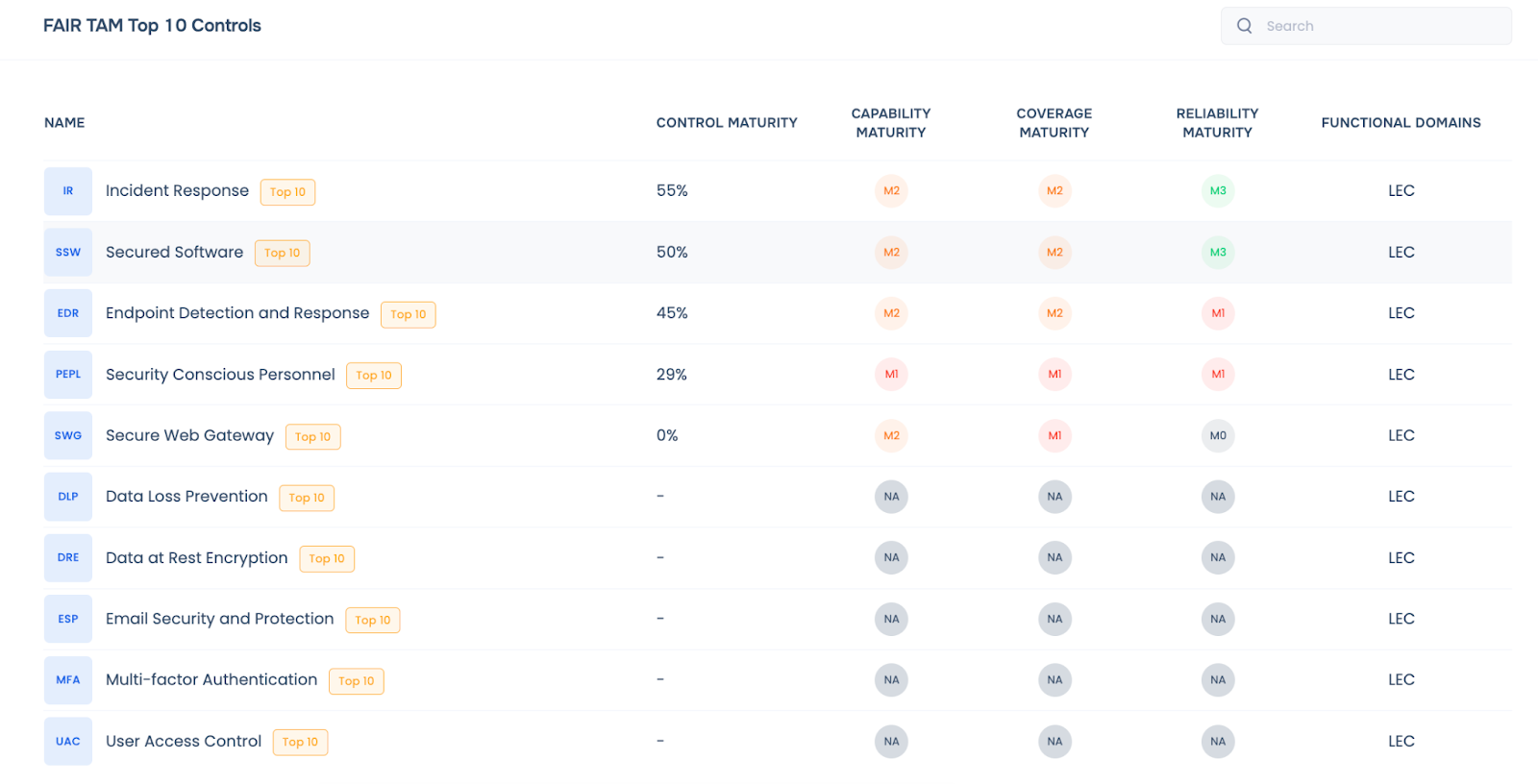
FAIR™-TAM-powered list of top 10 controls to be prioritized by your third-parties for risk reduction
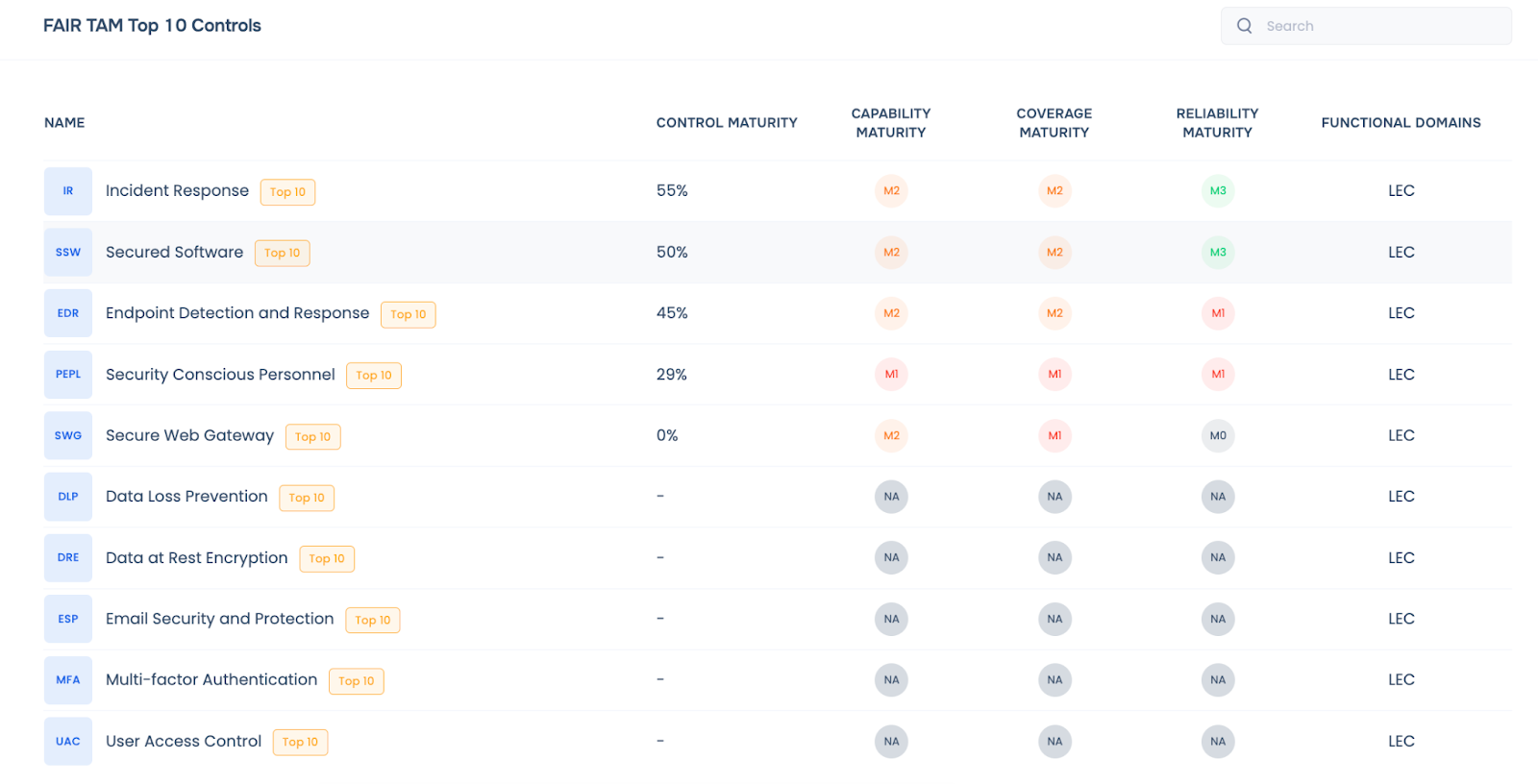
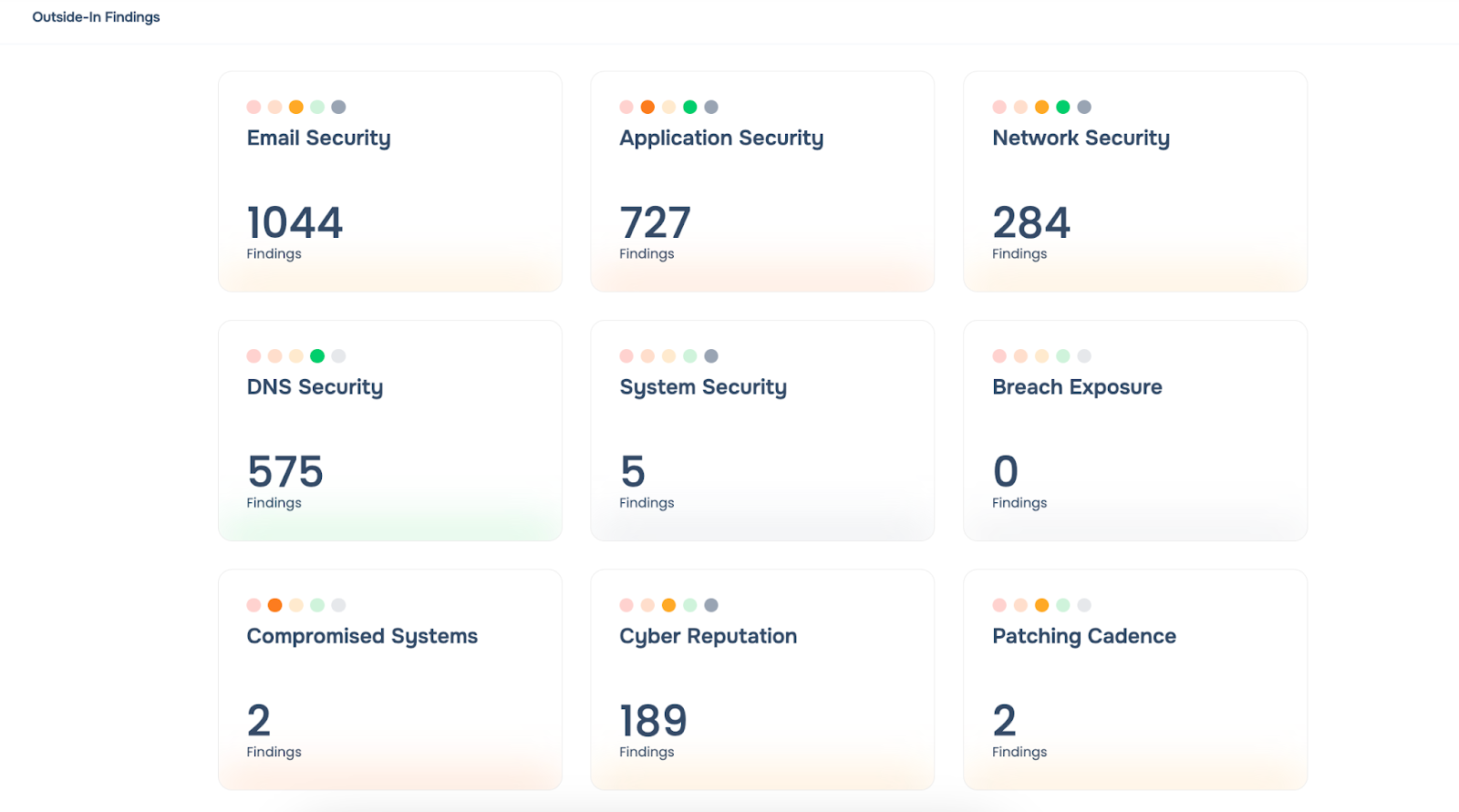
Assess control effectiveness from consolidated view of outside-in, questionnaires, inside-out analysis
ROI-driven zero-trust actionable mitigation strategies for the enterprise to minimize breach impact