Are you worried about the cyber risks for your crown jewel applications? Do you need an objective, quantifiable approach to calculating the top risks for them, not for the whole organization? This article will help you understand how to filter out the noise and measure cyber risks using SAFE for your specific crown jewel applications or business units.
Core Concepts:
Risks analysis on a specific attack surface for a Business Service
In the world of measuring cyber risks, CISO and risk analysts get requests to measure risks for either the whole organization or for specific business applications or business services. Some of the critical business applications, also commonly known as Crown Jewels, are one of the most important assets that organizations strive hard to protect from cyber attacks. Depending on the type of Business Service – whether they are external customer-facing or internal employee-facing, the type of risks scenarios vary.
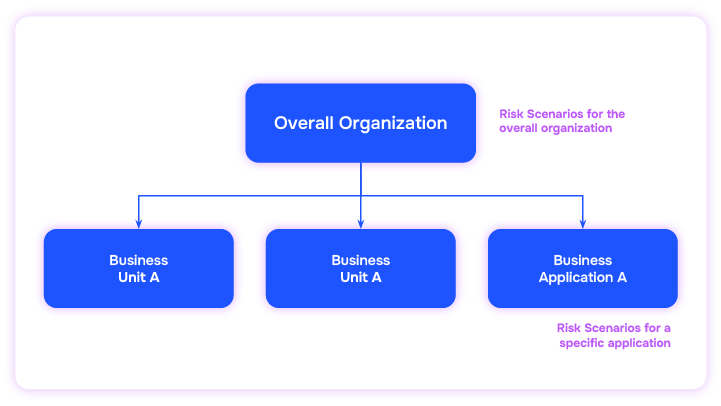
Implementation Using SAFE:
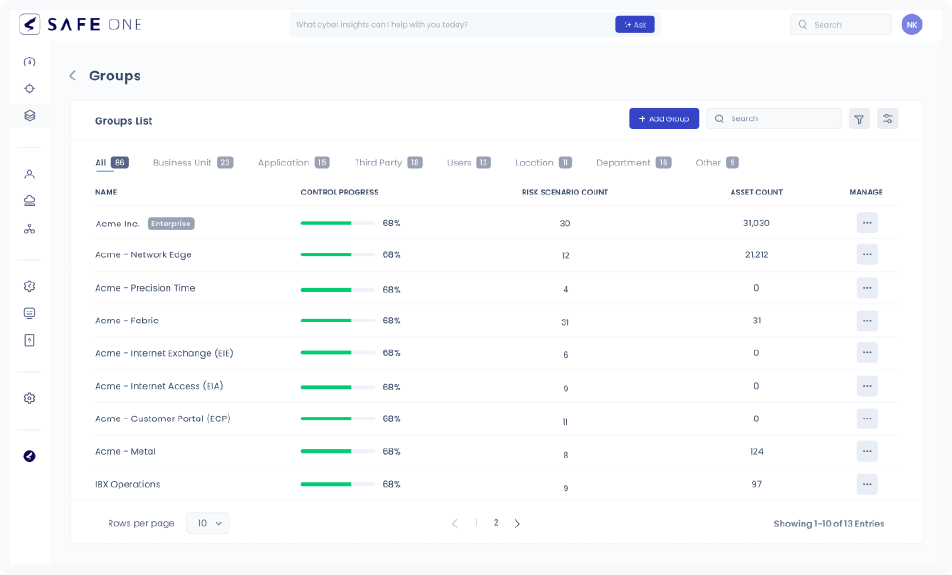
Mapping Assets to Business Services
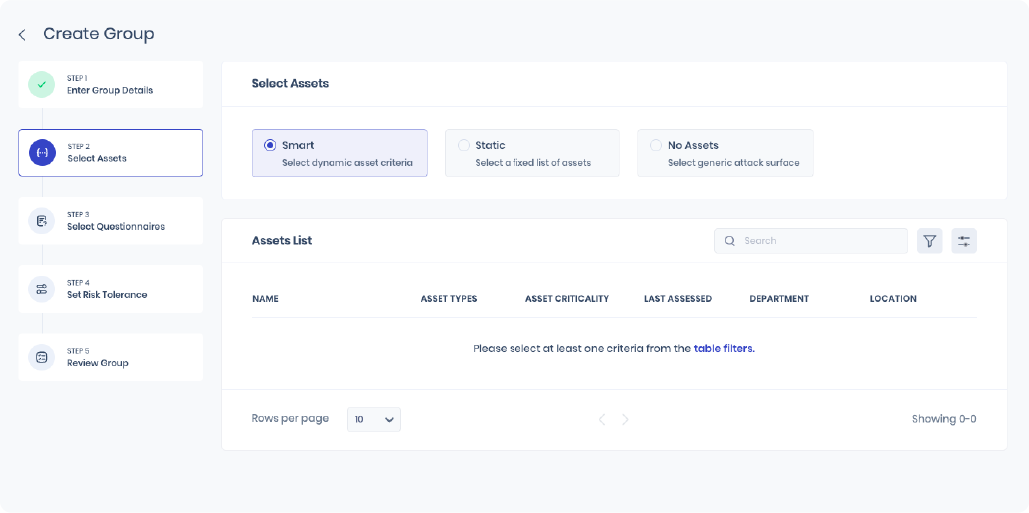
To measure the risk using scenarios for a specific business service, the first step is to get the right set of underlying assets mapped to them. This age-old challenge of how one maps the underlying assets to the business services and keeps them up to date has remained unsolved in the industry. CMDB’s have tried to address this through automated service discoveries, but it has not been a solid answer to this problem. Most organizations use a mix of automated and manual processes to map the right assets to a business service. SAFE offers a different approach to creating smart groups based on any of the asset’s properties.
Smart Groups to the Rescue
Smart Groups in SAFE allow users to create a dynamically updating list of assets based on any of the asset’s properties. For example, asset-to-business service mapping is better maintained for cloud assets, as each asset’s cloud cost has to be paid for. That’s where “Tags” come in. Cloud providers encourage using tags to map these assets to a business service or a cost center. SAFE can use these tags from sources like Azure or Wiz to let users create a “Smart” Group that dynamically adds/removes these assets within the group. This makes it much easier to maintain the right group of assets mapped to a group. The cyber risks associated with such groups accurately represent the correct set of underlying assets.
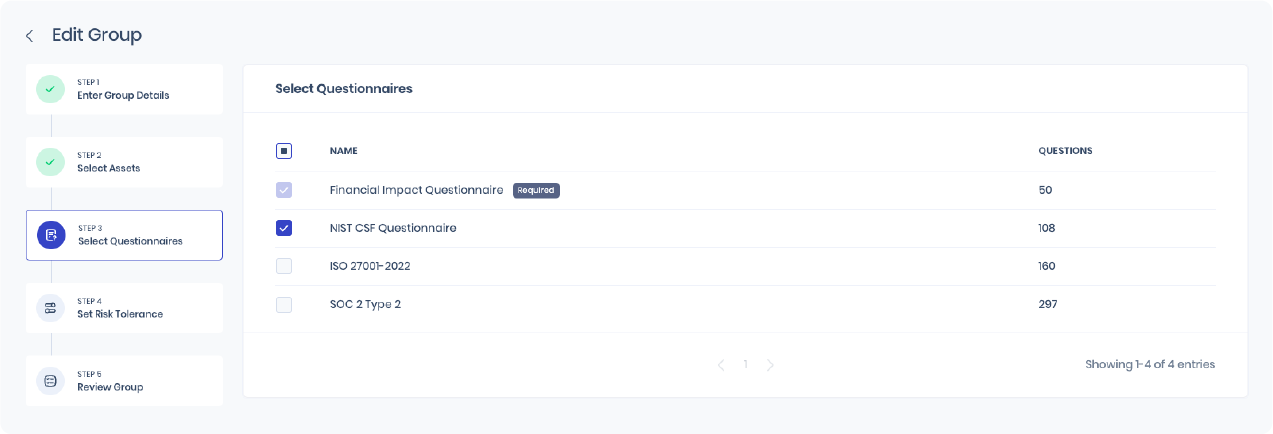
Financial Impact and Control Assessments for a Business Service
For each Group, two aspects help determine the Likelihood and the Loss associated with a Risk scenario. These are the Financial Impact of a breach occurring on any of its assets and the cybersecurity controls to prevent such breaches. There can be two possibilities regarding the group structure in your organization
- The groups can inherit the same assessment levels from the top-level group (the “enterprise” group that contains all assets)
- They can have a separate assessment level specific to the Business Service.
SAFE allows you to easily take any of the above approaches by attaching a Questionnaire at the Group level. You can copy the assessment from the top-level enterprise group or answer it individually at the Group level.
Risk Scenarios Specific to a Business Service
The next step is to use the Risk Scenario builder in SAFE to create specific risk scenarios for a business service, such as data exfiltration for a customer-facing website.
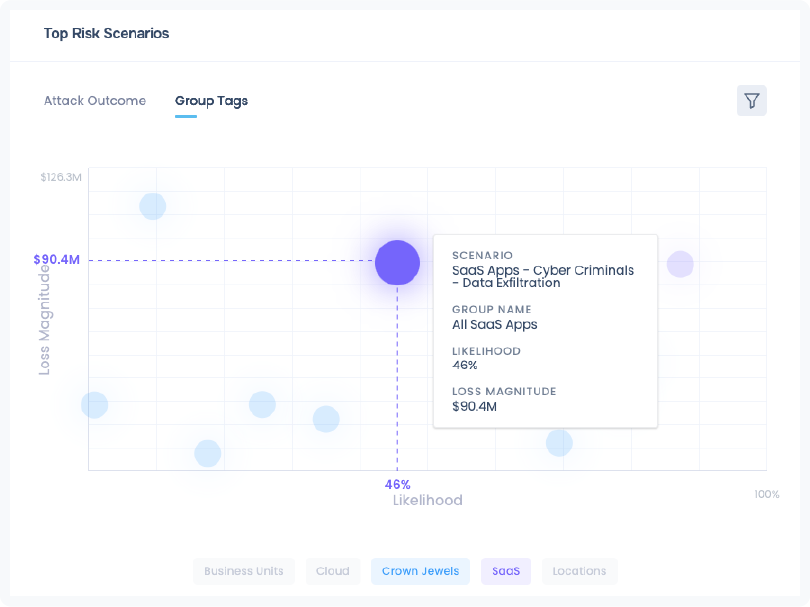
Organize your business services in SAFE using Group Tags, like Crown Jewels and Business Units, and map the risk scenarios for them to measure your cyber security risk posture.
This gives your business decision-makers a visual way of showing the risks they are most concerned with. For example, data exfiltration occurs on any of their Crown Jewel applications.
Dashboard for a Business Service Owner
Finally, you can use Dashboards in SAFE to use various widgets to organize the risk information for your business decision-makers to communicate the top concerns.
A specific custom role can also be created in SAFE to give users, like the Risk Owners, access to only the risk scenarios of the business services that are relevant to them.
Organizations must manage their cyber risks at the enterprise level and specifically for a business unit or a crown jewel application. This enables them to utilize their annual cyber security budgets most efficiently. The above approach helps them use SAFE to quantify these risks for specific business applications using an open methodology based on FAIR.
Need more information? Schedule a demo with our cyber risks experts to see this in action.