22% of institutes reported increased mortality rates resulting from ransomware attacks and 71% said it causes patients to have longer lengths of stay. In fact, ransomware attacks in 2020 affected 18,069,012 individual patients/records, which signifies a 470% increase from 2019. While other sectors manage financial and tangible losses after a cyber attack, the healthcare sector has far more devastating repercussions.
Case in point, Springhill Medical Center has been sued by an Alabama-based mother who claims that when her son Nicko was born, the hospital failed to deliver proper attention to him, ultimately leading to his death. A ransomware attack had crippled all electronic devices in the hospital, leaving the doctor unable to properly monitor the child’s condition during delivery. Is this the first life lost/impaired as a result of a cyberattack? It isn’t…
There are three key areas healthcare providers draw the short straw when it comes to cyber risks:
- Medical device security: 83% of medical imaging devices are still legacy systems. For perspective, there will be ~50 billion medical devices by 2028, with 15 – 20 IoMT in each hospital room!
- Insider threats: The HIMSS survey 2020 revealed that 89% of initial compromise in hospitals is still through emails, and 57% of cyberattacks began with trusted insiders.
- Third-party risks: Hospitals share PHI with ~1600 insurers per institute, and third-party vendors/suppliers; each equally liable to be a point of entry for cybercriminals.
Current cybersecurity practices need to adapt
To date, the healthcare industry has been heavily dependant on a compliance-first approach with traditional risk management practices. With the increased sophistication of cyber attack Tactics, Techniques, and Procedures (TTP), the widespread availability of ‘ransomware-as-a-service’ and other attack tools on the deep and dark web – present risk management strategies make it difficult to remain agile and respond with speed. While continuous compliance management forms the bedrock of risk management, it only detects functional threats and is not enough to bring enterprise-wide visibility of cyber risks in real-time.
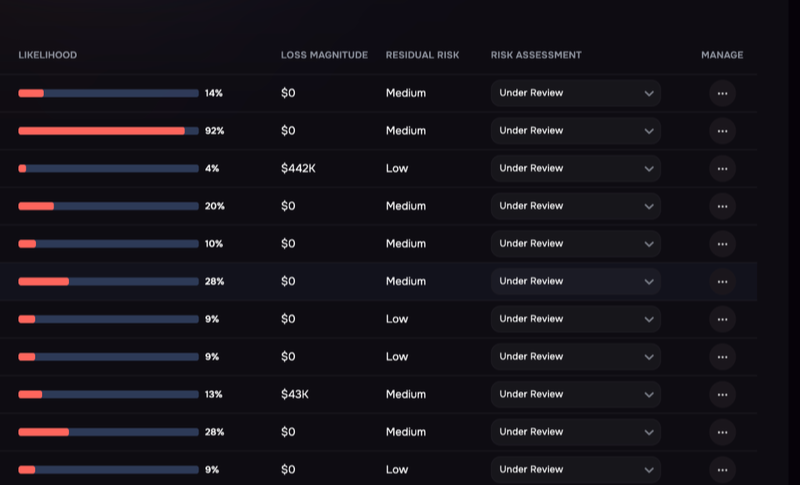
Enterprise cyber risk is a function of the business impact of a data breach and the probability of such an event happening. This probability is termed the “breach-likelihood”. Banks and insurance enterprises use credit scoring systems to predict the likelihood of repayments or claims. Medical diagnosis and treatment also rely on prediction models to improve patient care. The same method can be used to assess the possibility of a breach.
How does knowing your breach-likelihood help?
The knowledge of breach-likelihood becomes a single metric for cybersecurity communication across people (insiders, medical and non-medical departments), processes (policy, governance, and compliance), technology (IoMT and medical devices), third-party (vendors, drug suppliers, insurers, etc.), and cybersecurity products. Through its prioritized and actionable insights, the security team can make confident, data-driven decisions to manage and mitigate cyber risks.
Ultimately, security and risk management leaders like yourself, get a holistic picture of enterprise-wide cybersecurity from a currently siloed process.
Why should you trust SAFE’s breach-likelihood?
Today, multiple Fortune 500 companies in the healthcare sector are using SAFE’s breach-likelihood score and algorithm to get actionable insights and improve their cyber risk posture in real-time.
SAFE’s breach-likelihood score helps hospitals and healthcare providers by:
- Providing continuous visibility into the risk posture for all business-critical applications
- Overcoming cybersecurity communication barrier by introducing a common vernacular
- Showing a granular score per Employee, Hybrid Asset, LoB/Crown Jewels, cloud assets, and more
Know more about how we help Our Customers