By Cody Whelan
On the road to risk management maturity, most organizations start with some kind of maturity framework, most likely the NIST Cybersecurity Framework (NIST CSF). Frameworks are relatively easy to implement, and carry industry acceptance. But at this early stage of development, there is a misconception that maturity frameworks are either the same thing as, or close enough to, a well-vetted and defensible risk analysis model.

Over time, organizations learn the differences between the FAIR™ (Factor Analysis of Information Risk) model and CSF risk assessments. Then they may feel that the two are diametrically opposed and that one approach has to be chosen over the other, which is another common misconception.
In order to properly assess cyber risk, an organization must be able to identify specific risk scenarios, assess the loss magnitude of said scenarios, and then compare the results to the company’s risk appetite. Once an organization has that information, it can decide which risks need to be addressed and in what order.In this post, I’m going to outline the differences between the NIST CSF and Factor Analysis of Information Risk (FAIR), the risk analysis model that powers the RiskLens platform, and show how the two can be used in a complementary way.
What Are the Desired Outcomes for NIST CSF and FAIR Assessments?
To make sure that expectations match desired outcomes, it’s important to understand what each is intended to achieve and the differences between them.
NIST CSF
According to the NIST, the goal of CSF is to provide a common taxonomy and mechanism for organizations to:
- Describe their current cybersecurity posture;
- Describe their target state for cybersecurity;
- Identify and prioritize opportunities for improvement within the context of a continuous and repeatable process;
- Assess progress toward the target state;
- Communicate among internal and external stakeholders about cybersecurity risk.
CSF, which was largely created for use in the private sector, is not to be confused with NIST Risk Management Framework (RMF), which was designed mostly for use by government entities. While both can be applied to private organizations, Ultimately, in the case of RMF vs CSF, the only main difference is that RMF is more stringent and harder to adopt, and will likely only apply if your organization works for the government (see here for more details).Key Points about the NIST CSF
- The NIST CSF is a framework to help organizations understand their controls environment, broken down by their areas of greatest strength, as well as areas of greatest potential improvement.
- Organizations assess themselves using a 1 – 4 scale (Partial, Risk Informed, Repeatable, and Adaptive) through 108 sub categories.
- The outcome is an average score for each of the Five Functions of the framework (Identify, Protect, Detect, Respond, and Recover)
Ultimately, this tool shows you what areas of your business to focus attention on by making it clear what assets are clearly in need of more security.
FAIR (Factor Analysis of Information Risk)
The FAIR model that powers the RiskLens application is the only international standard quantitative model for cybersecurity and operational risk. Unlike risk assessment standards that focus their output on qualitative color charts or numerical weighted scales, the FAIR model specializes in financially derived results tailored for enterprise risk management. The FAIR Institute has over 12,000 members sharing information on use of the FAIR approach to risk.
NIST has formally published FAIR as an Informative Reference to the NIST CSF. This means that there is mapping between FAIR and the NIST CSF standard in the sections covering risk analysis and risk management.
Key Points about FAIR
- FAIR is a quantitative risk analysis model that helps organizations understand their risks in financial terms (FAIR is also an international standard model maintained by the Open Group).
- Organizations define their concerns in terms of a structured scoping format (Assets, Threats, Effects, and Loss Event) by which a frequency of occurrence and a probable financial impact can be estimated.
- The outcome: Seeing risks in financial terms.
With the help of Monte Carlo simulation and the RiskLens platform, we can see these results in a variety of different ways, from histograms, to loss exceedance curves, to per-event frequencies and magnitudes.
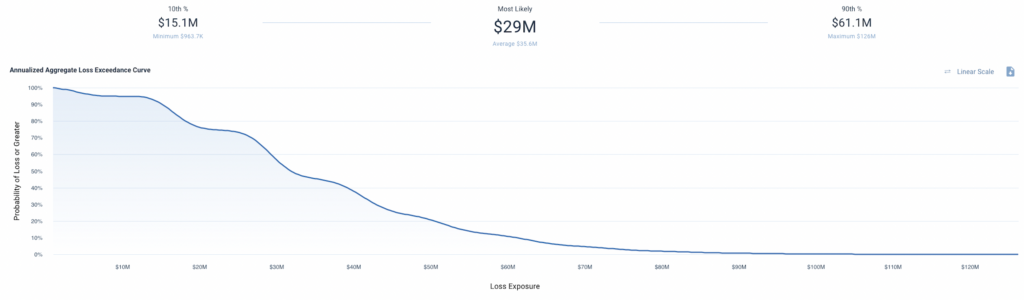
The end product of doing a quantitative analysis is data that your cybersecurity professionals can take directly to your business executives; both groups understand the language of dollars and cents, which helps bridge the gap so the organization can address risks as a collective.
Using NIST CSF and FAIR Together
Now that we understand what each tool is meant to achieve, let’s walk through how we can leverage one where the other leaves off.
A common problem with NIST CSF assessments is that they pull a risk team’s focus down into the weeds and then leave them there, so to speak. So you’re at Risk Informed status in the Data Security category, and could move up a notch to Repeatable status — but should you?
Organizations really want to know “How much risk do we have?” and “Which of the NIST CSF activities reduces risk the most?” The CSF model alone can’t answer those questions. This is where FAIR and seeing risks in financial terms becomes important. By quantifying the cost of the risks discovered by a CSF assessment, the organization can make an informed decision about what actions need to be taken to keep risk within an acceptable range.
The chart below shows how FAIR analysis picks up where the NIST CSF assessment leaves off. Based on the NIST CSF areas of concern on the left, I defined two measurable events on the right for which we can figure a likely frequency of occurrence and a dollar-cost magnitude of impact.
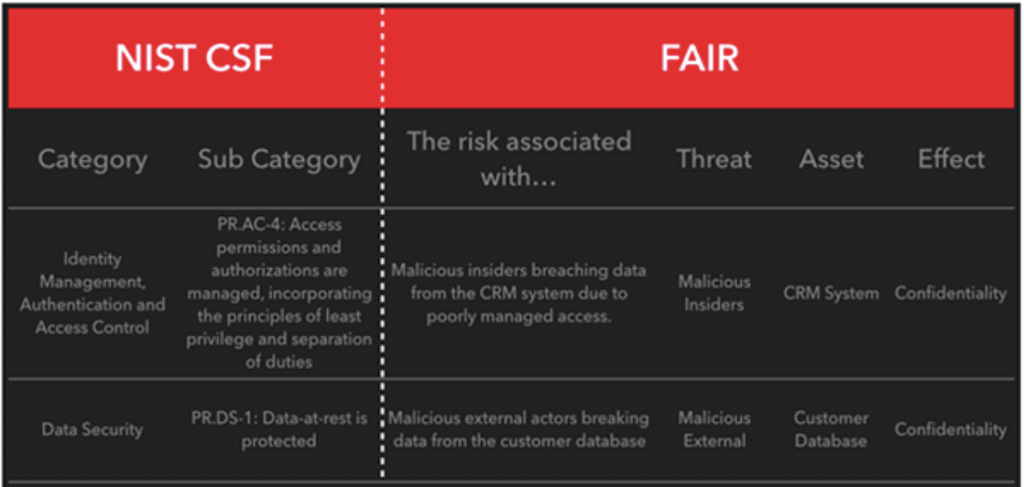
This practice in FAIR analysis is known as scoping, and is actually the first step in the risk analysis process. When it comes to preparing for security risk scenarios, it’s less of making a decision between NIST CSF and FAIR and more about combining the outputs from both to decide what risk reduction steps should be taken. Without using NIST CSF, you might struggle with deciding where your greatest risks lie, and if you pass up on FAIR, you might have difficulty quantifying risk in a way that makes it clear to your organization what steps need to be taken and which items should be prioritized.
FAIR + NIST CSF = More Effective Risk Management
To recap, both NIST CSF and FAIR serve a purpose and are complementary to one another. The NIST CSF helps organizations understand broad areas of control deficiency within their environment. Through the use of FAIR and quantitative risk analysis, organizations can understand how to prioritize the risk management efforts suggested by NIST CSF based on an estimation of risk in financial terms.
For additional information about how to use the two together, check out our on-demand webinar “Combining NIST CSF and FAIR to Drive Better Cyber Risk Decisions.”
Learn more: NIST Maps FAIR to the NIST CSF, Major Recognition of the Power of Cyber Risk Quantification
The FAIR model that powers the RiskLens platform is the only international standard quantitative model for cyber security and operational risk. Unlike risk assessment standards that focus their output on qualitative color charts or numerical weighted scales, the FAIR model enables financially derived results tailored for enterprise risk management.
The RiskLens enterprise platform includes
- Guided FAIR risk assessment workflow
- Industry benchmark data for frequency and magnitude
- Pre-formatted risk scenarios
- Embedded Monte Carlo risk quantification engine
- Flexible reporting, including portfolio management to track risks by business unit, revenue stream or any other category
- Risk treatment analysis – compare alternatives for ROI for risk reduction
and many more features. Contact us for a demo of the RiskLens platform.
RiskLens also offers the RiskLens Pro managed service and the My Cyber Risk Benchmark self-service tool.



