
In today’s enterprise, security teams face an increasing volume and complexity of challenges. They struggle to maintain their security posture within an ever-evolving threat landscape, leveraging a growing suite of solutions to monitor and protect their enterprise, while responding to alerts and notifications from these various solutions.
One of the greatest challenges they face is their response to this question: “How should we prioritize the allocation of finite time and resources?”
Ideally, organizations will leverage solutions such as Security and Information and Event Management Systems (SIEMs) that help aggregate and manage the information generated. Although security teams might be able to centralize this data, how do they know what to prioritize?
Alerts that indicate the organization may be under attack will always be assigned highest priority, but what about security gaps that aren’t actively (or knowingly) being exploited? How does a team prioritize misconfigurations vs. discovered vulnerabilities vs. policy gaps? Does the team have insight into how these gaps could be exploited and utilize that information to prioritize resources and develop plans for remediation?
The Security Assessment Framework for Enterprise: The SAFE Platform
SAFE is a real-time Continuous Risk Assessment and Cyber Risk Quantification (CRQ) SaaS platform that contextualizes technical and business risk to enable informed and prioritized data-driven decision-making. SAFE’s approach targets five key vectors: People, Policy, Technology, Cybersecurity Products, and Third-Party.
This article explores two areas where SAFE helps organizations prioritize risk, time, and resources:
- Actionable Insights on failing controls
- Mapping security gaps across the MITRE ATT&CK framework.
Actionable Insights
To assess security gaps across the technology stack, SAFE collects signals from four vectors that impact the security posture of an organization:
- VA: Vulnerability Assessment data
- CA: Configuration Assessment data
- Policy data
- Compensating controls in the form Cybersecurity Products (CSP)
SAFE ingests these signals and enriches the data with external threat intelligence and business context to identify the weakest links. These are presented as Actionable Insights focused on Controls and Assets.
Actionable Insights focused on Controls display the VA and CA information related to an organization’s assets. This is based on the severity of the security gap and the impacted asset. SAFE parses this information further to provide specific control gaps labeled High Impact Controls.
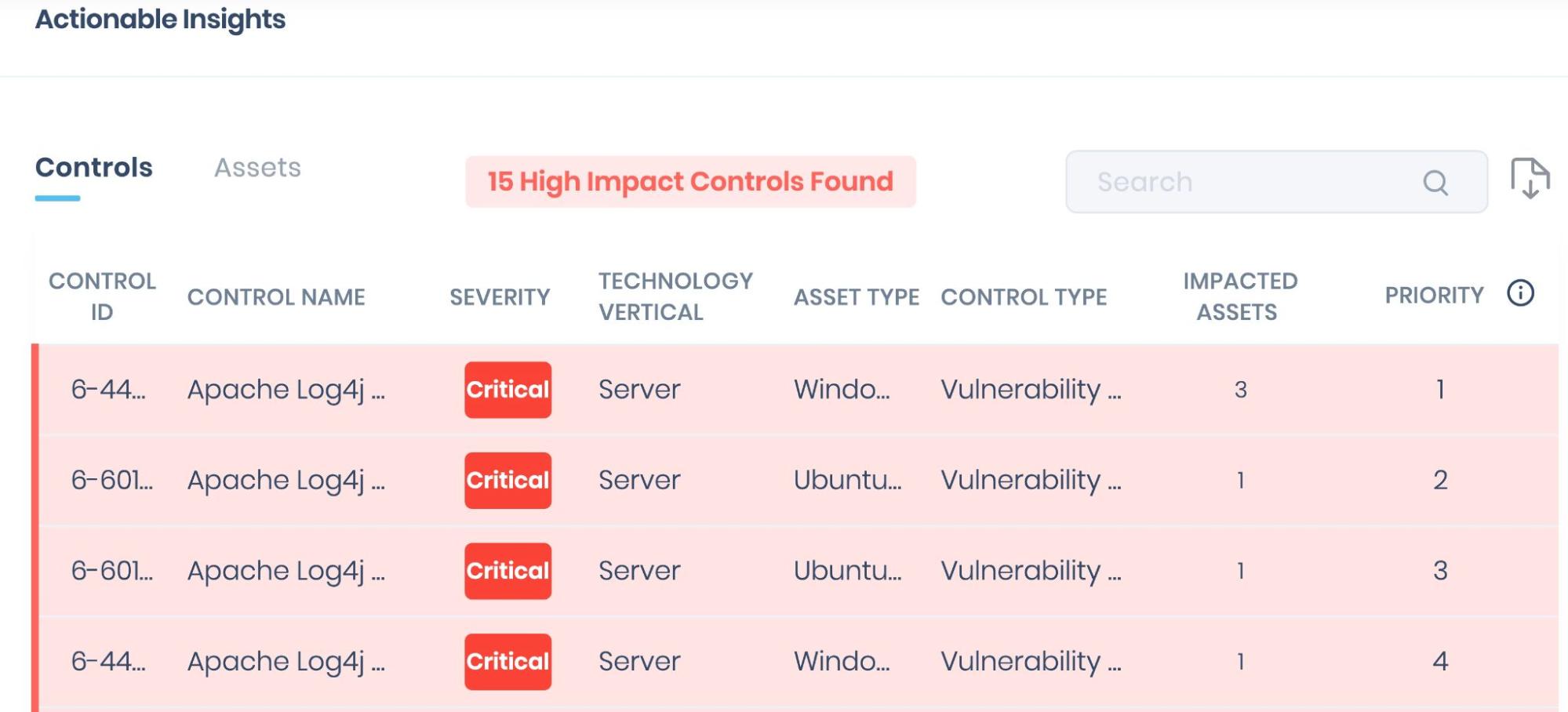
CA High Impact Controls are identified by assessing their Common Configuration Scoring System score (CCSS), or severity score. The configuration controls marked as Critical and High severities are analyzed and mapped to ATT&CK techniques. Once mapped, they are further assessed to establish if any APT groups exploit or leverage them. If confirmed, they are considered High Impact Controls.
VA High Impact Controls are vulnerabilities identified as high-risk that may have a publicly available exploit or have been determined as such by SAFE’s subject matter experts.
High Impact comprises two categories of CVE IDs:
- Remote Code Execution CVEs having critical and high severity are exploitable from adjacent networks and the internet and have publicly available exploits.
- CVE IDs provided by OSCP-certified SMEs of SAFE (from internal red-teaming, vulnerability assessment, and penetration testing research). These CVE IDs may also have a Medium severity rating in addition to High and Critical.
The primary purpose of identifying High Impact controls is to inform customers about the most exploitable weaknesses in their assets and the order of priority for remediation. Often, due to limited resources, weaknesses cannot all be addressed at once, which is why SAFE recommends starting the remediation process by patching High Impact Controls first. Learn more about High Impact Controls in our documentation.
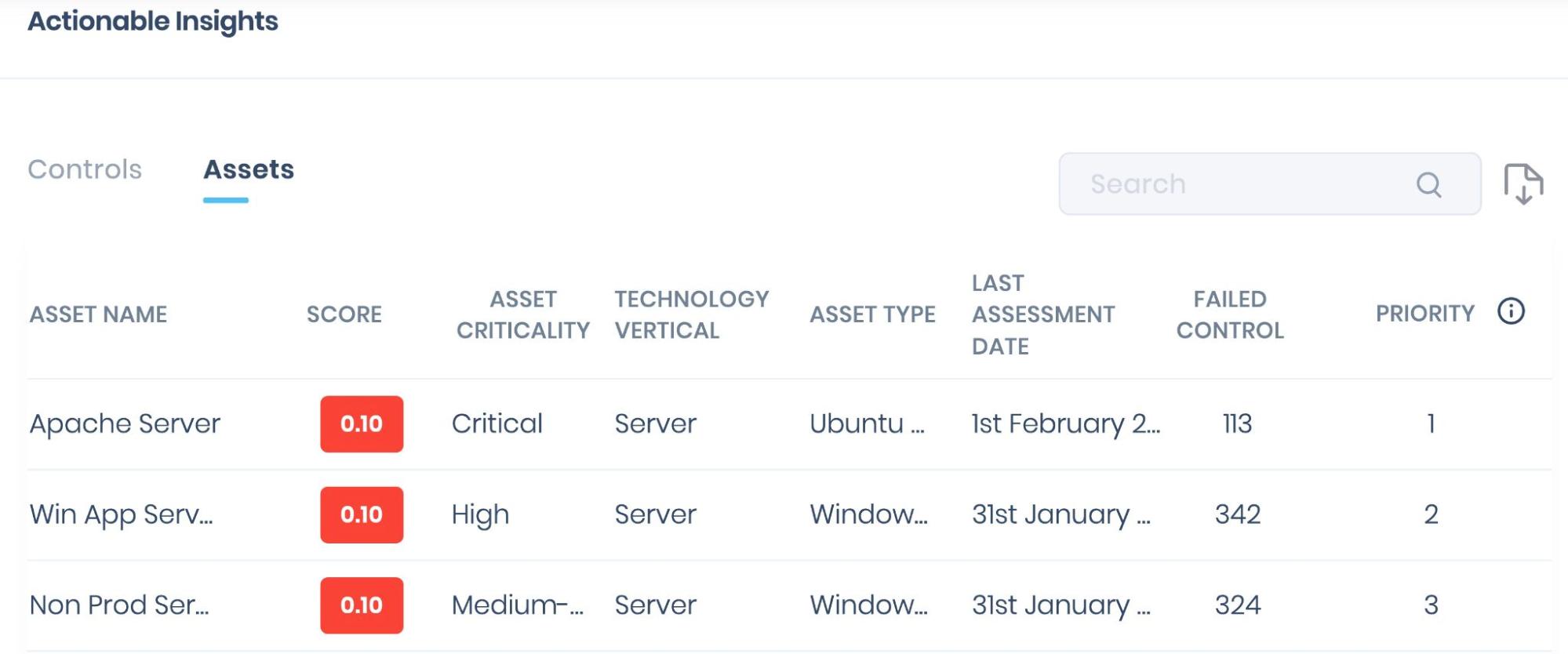
Actionable Insights focused on Assets are based on the SAFE Score. The asset with the lowest SAFE Score will appear first. The SAFE Score indicates the likelihood of a breach occurring over the following 12 months. The Score provides visibility into risk across the entire enterprise: each asset, employee, policy, cybersecurity product, and third-party vendor or partner.
MITRE ATT&CK: Using SAFE to map security gaps in real-time
The MITRE ATT&CK™ framework documents all attacker tactics and techniques identified in real-world attacks. It enables security teams to improve their understanding of the steps adversaries take to successfully execute a particular attack so that they can better protect their systems.
SAFE’s integrated ATT&CK Matrix will give you complete visibility of your security gaps and map each of them to potential exploits at each stage of the attack lifecycle.
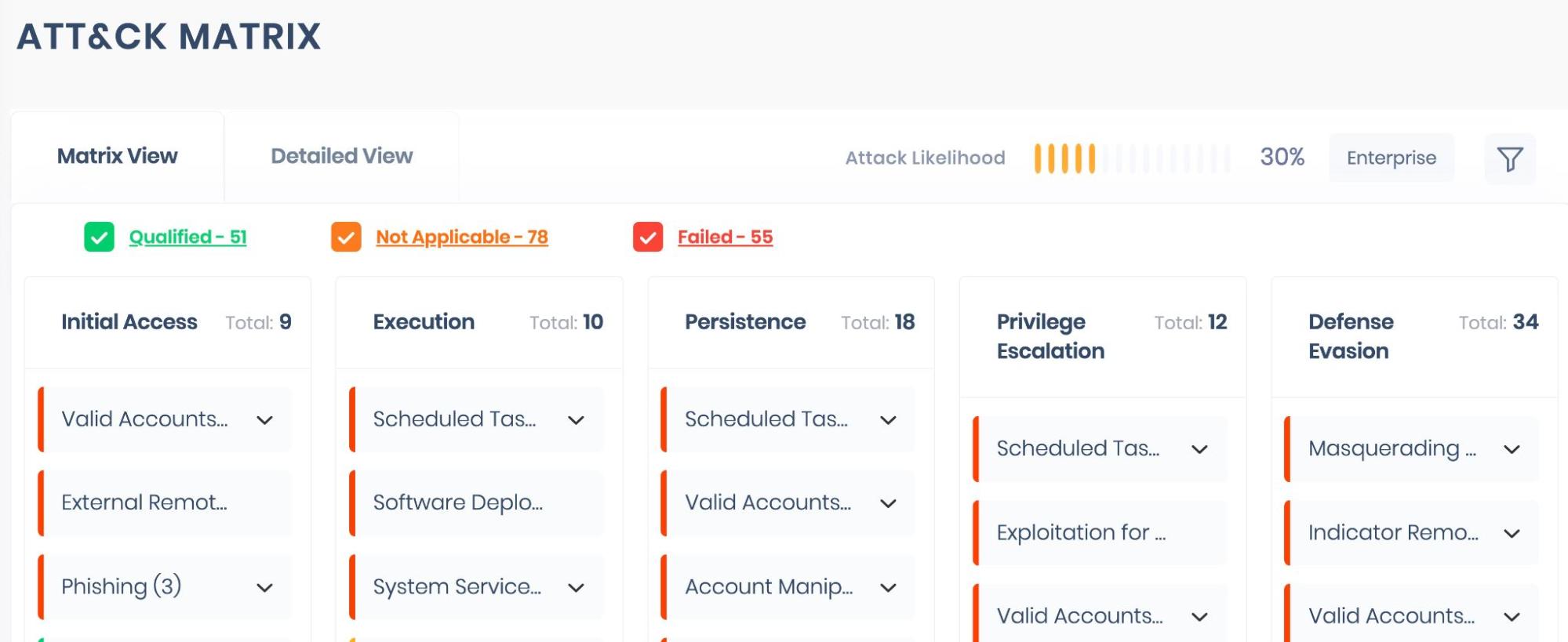
SAFE takes this mapping one step further with its ability to segment the MITRE Matrix into the Attack Lifecycles for five distinct threats: Ransomware, Phishing, Business Email Compromise (BEC), Distributed Denial of Service (DDOS), and Data Compromise.
Equipped with this crucial information, security teams have gained the capability to identify and understand the types of exploits they may become subject to, graded by severity to the organization, which allows them to prioritize remediation. This prioritization enables them to allocate resources to the most pertinent threats and eliminate the most harmful or immediate risks.
Removing the guesswork: How SAFE empowers and protects
SAFE removes the uncertainties and inefficiencies of guesswork by empowering security teams to take control of cyber risk, predict the likelihood of cyber attacks, and proactively maintain a continuous, data- and insights-driven approach to protecting their enterprise.
SAFE automatically aggregates and correlates data from various security sources to provide a single dashboard view of an organization’s security posture in real-time. This makes it ideal for enterprise organizations that require swift identification and 360-degree visibility of their security gaps. It enables a greater understanding of cyber risk exposure by generating Actionable Insights based on High-Impact controls, and Assets are prioritized based on their SAFE scores.
Security teams can also go one step further and automatically map their security gaps to the MITRE ATT&CK Framework. It provides the specific information and intelligence needed for teams to truly understand the attacker mindset and the risks they’re exposed to and puts them in a much stronger position when addressing them.



