We’re excited to share the results of our first backtesting exercise where we tested the Interactive Cost Model (ICM) against eight cyber attacks for which financial impact data was publicly disclosed. The ICM was launched in August 2022 as the first interactive, transparent, and defensible cost model to provide dollar-value estimates of financial risk due to cyber attacks. It received positive reviews from Gartner and IDC analysts for giving organizations a freemium alternative to explore the benefits of cyber risk quantification.
We are encouraged by the first set of results and will continue fine-tuning our model. We value the input of the cyber risk community and welcome your constructive feedback. Please email [email protected]
How We Built Our Backtesting Method and Design
Reported Ransomware Attacks Used for Backtesting
SAFE tested the ICM against eight recent ransomware attacks that were not included in our proprietary database when the model was developed:
- Tenet Health
- Faneuil
- Quincy, IL
- Minerals Technologies
- Radiant Logistics
- WestRock
- Benchmark Electronics
- Sinclair Broadcast Group
Walkthrough of our Backtesting Method
Step 1: Enter company level input data:
Annual revenue, employee count; industry; and headquarter location.
Step 2: Create scenarios around the security controls
The SAFE ICM is tightly linked to impact security controls that do not affect the likelihood of an attack but do reduce the cost of an attack once it has happened.
Deploying a particular impact control (such as data encryption) hugely impacts the backtesting results. The impact controls are:
- Incident Response and Business Continuity plans
- Offsite Data Backup
- Sensitive PII Encryption
- Wire Transfer Protocol
- The leakage of employee records during the attack
This testing exercise was conducted independently of the affected companies. As such, we made informed assumptions about the security controls they had in place.
To keep it simple, we created two scenarios:
- A best-case scenario: where all the controls were implemented
- A worst-case scenario: where none of the controls were implemented
There could be several scenarios based on permutations of impact controls; however, they were not considered during this exercise.
Our Results and Observations
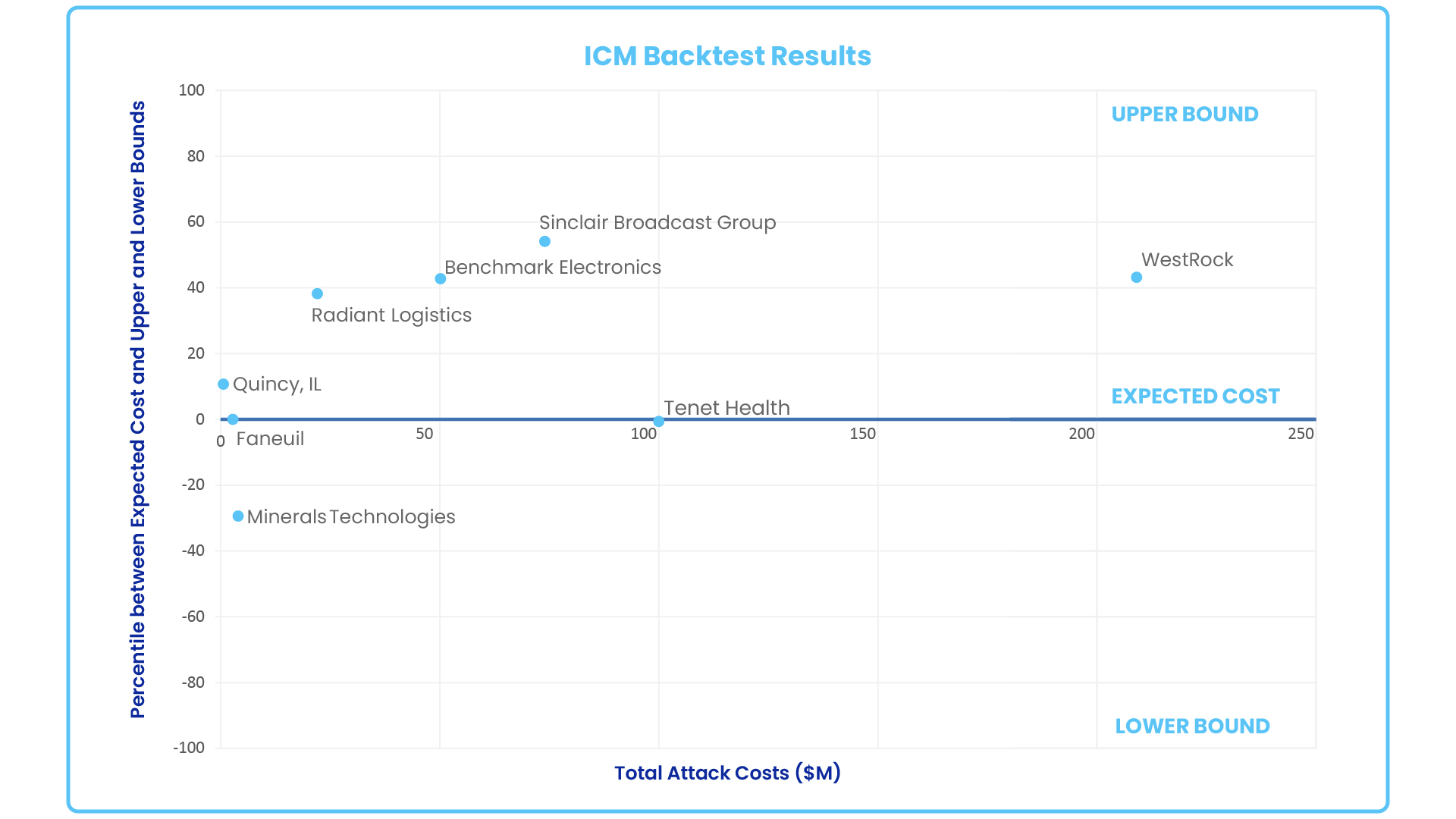
Figure: SAFE ICM backtesting results on eight recent ransomware attacks
- The actual cost of each attack was within the ICM’s predicted range..
- The four companies with total costs farthest above estimated expected cost incurred significant revenue loss or interruption. These results suggest that a strong business continuity plan may play a significant factor in the severity of financial impact following an attack.
- The other four companies reported total costs that were within a 25% deviation from the estimated expected cost.
- Two of the companies reported values equivalent to the estimated expected cost.
- Three of the companies reported no revenue loss.
The table below includes the name of the affected entities, the date of discovery of the attack, its cost, and a brief description of how the total attack cost was calculated.