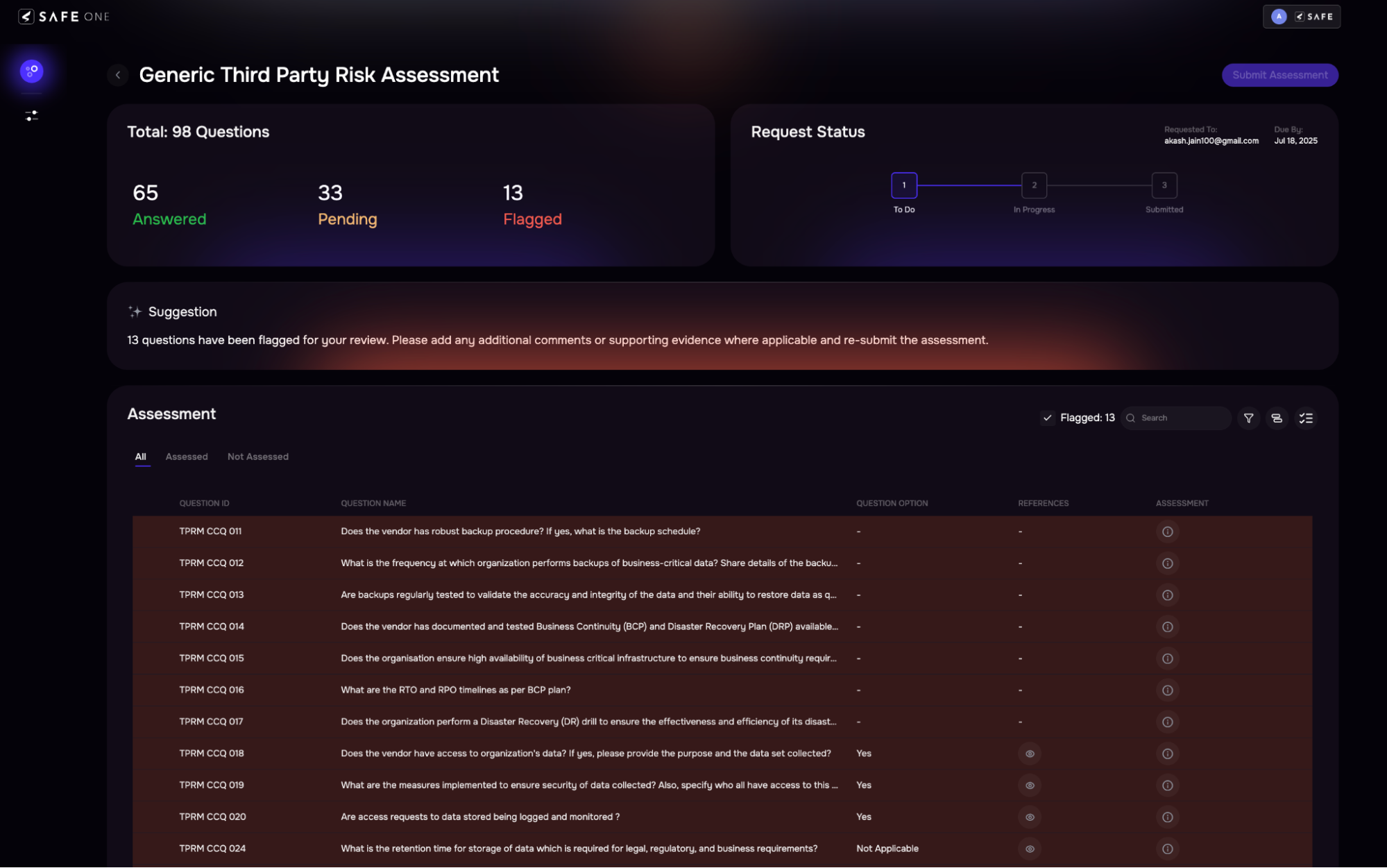
Get the data and the proven process to jump into cyber risk quantification.
By Jay Soni
Security organizations today want to move to a risk-based approach to make decisions such as
- What controls to invest in that will reduce ransomware risk the most or
- What is the right security architecture to implement to support our cloud migration.

The means to support these decisions are foundationally embedded in cyber risk quantification (CRQ) with defensible risk measurement in financial terms – FAIR (Factor Analysis of Information Risk) is the proven standard for CRQ. However, we often hear from organizations considering making the shift to quantitative cyber risk management, that they feel or perceive they are not ready or have not hit the right risk management maturity capability levels.
When digging deeper into these perceptions, we typically get a common set of concerns or barriers that can be grouped into three main buckets. The goal of this post is to identify those potential barriers and talk about how automation and the ease of use found in SAFE’s technology and solutions are solving specifically for the maturity dilemma.
CRQ Barrier #1 Data
We don’t fully understand what data we need to do quantification of cyber loss event scenarios from the likelihood and magnitude perspective to use the FAIR model and still be defensible.
Security and cyber risk teams have lots of data they can pull from their existing technology stack and security tools but those data points fail to help us understand how they contribute to either the likelihood or magnitude of a breach. Other elements often left out are the impact of compensating controls, the value of assets or the business context.
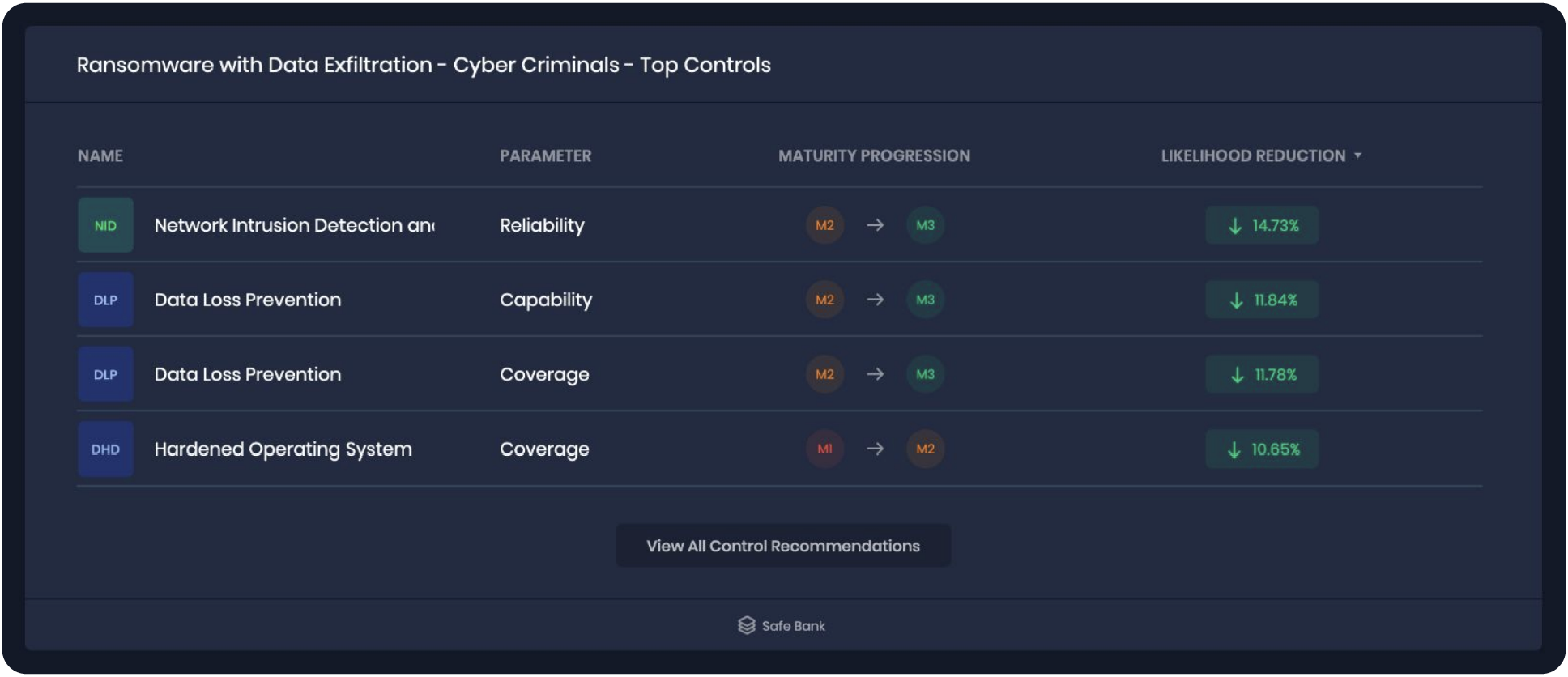
This makes it extremely difficult for organizations to consistently and reliably measure risk that can hold up to scrutiny, leading to a perception that the organization is just not ready to take on risk quantification.
SAFE addresses this through our SAFE One platform purpose built to leverage standard models and frameworks like FAIR and the MITRE ATT&CK, with an API-driven approach for up-to-the-minute, inside-out/outside-in data collection on assets, controls and threats.
We have partnered with MITRE, FAIR Institute, MIT, and thought leaders like Jack Jones, and Doug Hubbard to map the relevant risk data to the MITRE ATT&CK framework to help us objectively understand our susceptibility and control reliability/maturity in the context of a FAIR analysis.
This takes the guesswork out of the hands of risk analysts trying to make sense of an overload of data. The platform allows us to
- Double click to inspect data used in an analysis
- Gain full transparency and understanding of the rationale that went into producing the quantitative outputs.
CRQ Barrier #2 Process
We don’t have the processes in place to get that data in an efficient or pragmatic way. With so much security data siloed and fragmented across the environment and governed by different teams and programs, the level of effort and resources required to scale CRQ and deliver sustainable value just isn’t feasible.
This is a very valid concern and many CRQ programs have failed for this very reason. The SAFE One platform tackles this problem head on by having 100+ APIs that can connect into your cloud infrastructure, security tools and different SaaS apps to automatically collect and ingest relevant data for a FAIR based quantitative analysis (i.e. the capability, reliability and coverage of controls).

This lowers/eliminates the barrier in terms of resources required for data collection, accelerates time to value and produces high fidelity results that are more objective than estimates. And because the platform can continuously collect this data, it allows for dynamic changes in the risk landscape to reflect real time changes in your risk exposure across your entire attack surface.
CRQ Barrier #3 Where to Start
We are not sure where to start to provide value to the business/options on how we want to slice/dice and model our environment.
We know the value of risk management begins when a report is handed to a stakeholder and a decision is made (treat, accept, transfer). So if we can accelerate the outcomes driven by risk quantification to support decisions and provide a continuous view of risk then the value of risk programs goes up dramatically, as they can be integrated in strategic, operational, and tactical decision making. Now there are areas of maturity that fall outside of what SAFE One or any technology can provide; we’ll address those “cultural” components in part two of this series.
Defining Risk Management Maturity with Jack Jones
Jack Jones, creator of the FAIR model and Chairman of the FAIR Institute (where SAFE is a sponsor), defines “maturity” for cyber risk management in simple, actionable terms:
“A mature organization is one that can cost-effectively achieve and maintain an acceptable level of risk.” To hit that goal, Jack continues, an organization needs to “reduce noise and focus more effectively on truly high-risk concerns, choose cost-effective solutions for the risk management priorities, and execute reliably.”
Jack counts as noise or distractions the typical risk management maturity model that keeps organizations busy acquiring new controls to check them off a list. “They don’t really define what maturity represents…Many of us know organizations that score reasonably well on common risk maturity assessments but have significant difficulty prioritizing well or executing reliably.”
Learn more in this blog post: What’s Risk Management Maturity?