Run your controls strategy based on return on investment for cyber risk reduction. Cyber risk quantification shows the way.
What’s the most valuable control for risk reduction in your cybersecurity program?
What’s the least valuable control?
How do your controls work together to reduce risk?
What’s the best control to handle a particular risk?
These are basic questions for a profession that spends most of its time, money and effort dealing with controls – yet can’t be answered with certainty by most cyber risk managers.
Assessing the effectiveness and maturity of cybersecurity controls has traditionally been spreadsheet-driven and based on manual inputs and subjective assumptions. Managing disparate and diverse controls requires multiple team members to track different spreadsheets or dashboards – often leaving critical alerts unaddressed or overlooked.
Controls Status Reporting on the SAFE One Platform
The deeper problem
There has been no standardized methodology that codifies how controls work singly or as a system.
Security vendors traditionally have responded with workarounds that don’t solve that core problem.
- “Maturity models” rate an organization’s security stack against a standard list of controls like the NIST CSF, and are based on linear thinking that assumes more controls equal less risk.
- Outside-in scanning applications produce many false positives – and also don’t connect controls to risk in a measurable way.
The confusion around controls has kept their effectiveness from being optimized to date because it has been impossible to translate security telemetry signals from controls into automated, near real-time risk measurements.
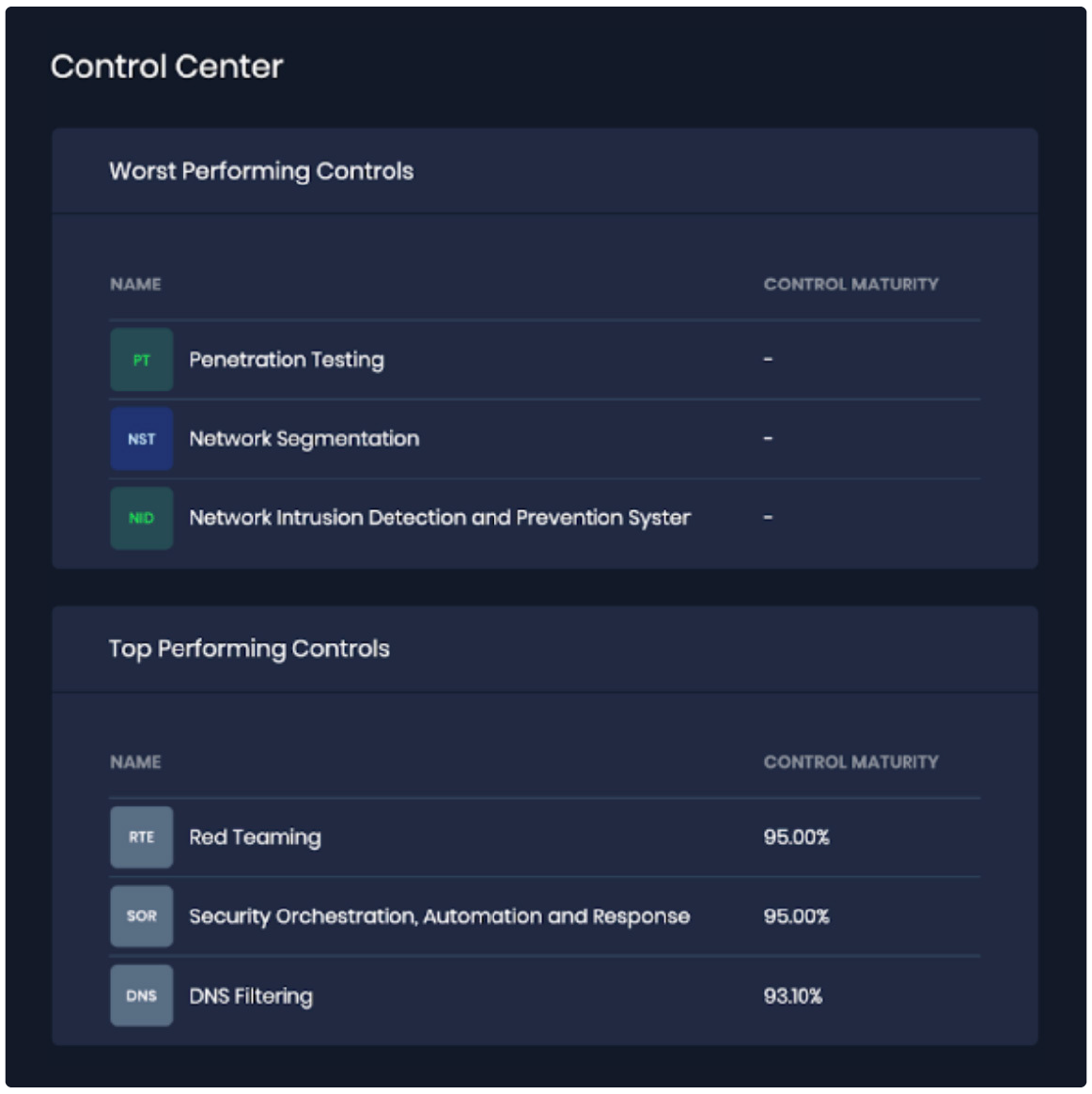
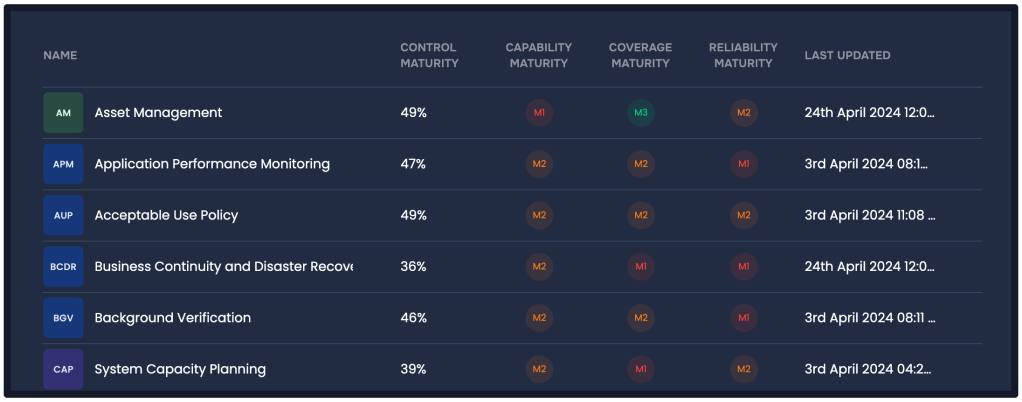
Detail from Top Controls Report on SAFE One Platform
Introducing the FAIR Controls Analytics Model (FAIR-CAM)
Jack Jones created Factor Analysis of Information Risk (FAIR™), which has been recognized by the National Institute of Standards and Technology (NIST) as the standard for quantitative analysis of cyber risk. Jack then created an extension to the standard, the FAIR Controls Analytics Model (FAIR-CAM™), to bring the structure and clarity of quantitative analysis to cyber controls management in a constructive and defensible way.
FAIR-CAM takes control system analysis down to a granular level. It describes and quantifies the function of each control for risk reduction, documents the interdependence among controls and the effectiveness of a multi-control environment overall. Jack borrows a term from medicine and calls it a “controls physiology.”
The value of any cybersecurity control is determined by its effect on the frequency of occurrence or the magnitude of impact of loss events. That can be quantified with the FAIR-CAM™ model in units of measurement (for instance, frequency, probability, or time). (Note: to fully quantify magnitude, we also use FAIR-MAM, the companion Materiality Assessment Model, that pulls in data to cost modules tuned to the organization.)
FAIR-CAM sorts controls into three categories
- Loss Event Controls directly affect risk (like multi-factor authentication)
- Variance Management Controls (like patching) that indirectly affect risk by affecting the reliability of controls
- Decision Support Controls (like threat intelligence) that indirectly affect risk by influencing decision-making
But each of these categories can be broken down further by functionality – the ways in which a control can affect the frequency or magnitude of loss – such as
- Loss Event Detection
- Loss Event Prevention
- Loss Event Response
And those categories can be defined with even more granularity by their subcategories. Some example subcategories:Loss Event Detection, Subcategory Resistance: Reduce likelihood that a threat agent’s act will result in a loss event, such as through authentication or access privileges.Loss Event Prevention, Subcategory Avoidance: Reduce frequency of contact between threat agents and assets, such as through email filtering at the perimeter or URL filtering.Loss Event Response, Subcategory Containment: Enable termination of threat agent activities, such as through affected systems segregation.
The FAIR-CAM™ model is complexity with a purpose. It accounts realistically for the many ways that controls can affect the factors that determine risk, by working singly or together and by including overlapping or even reduction in each other’s effectiveness.
For a complete overview of the model, we suggest reading the white paper by written by Jack Jones,
An Introduction to the FAIR Controls Analytics Model (FAIR-CAM™) ( a free FAIR Institute membership is required).
SAFE One Is the First Cyber Risk Management Platform to Incorporate FAIR-CAM
The SAFE One platform automates FAIR-CAM and customizes it to your organization’s risk landscape and controls environment, seamlessly applying the rigor of FAIR-CAM to any risk analysis you perform.
Key points on SAFE’s implementation of FAIR-CAM:
Questionnaire Library on SAFE One Platform (Partial View)
Compatible with your existing controls framework
Whether it’s NIST, ISO, CIS or other controls framework, you start by uploading the documentation for your controls inventory. The platform matches your controls to a FAIR-CAM-friendly library of dozens of controls.
Real-time readings on controls
You think you’re compliant – but are each of your controls actually working as expected? Pulling in telemetry via APIs, the Controls Center gives you a current reading on controls status and possible gaps for:
- Capability, based on the level of implementation and features
- Coverage, based on how many assets are covered by the control
- Reliability, based on how frequently good cyber hygiene policies are enforced
SAFE provides the largest set of over 100 integrations for cyber risk management from industry leaders such as AWS, CrowdStrike, ServiceNow, Wiz, Tanium, Qualys, Rapid 7, Recorded Future and Databricks, thereby ensuring FAIR-CAM’s capability of providing risk leaders with a continuous view of the state of their cybersecurity controls and their most critical risks.
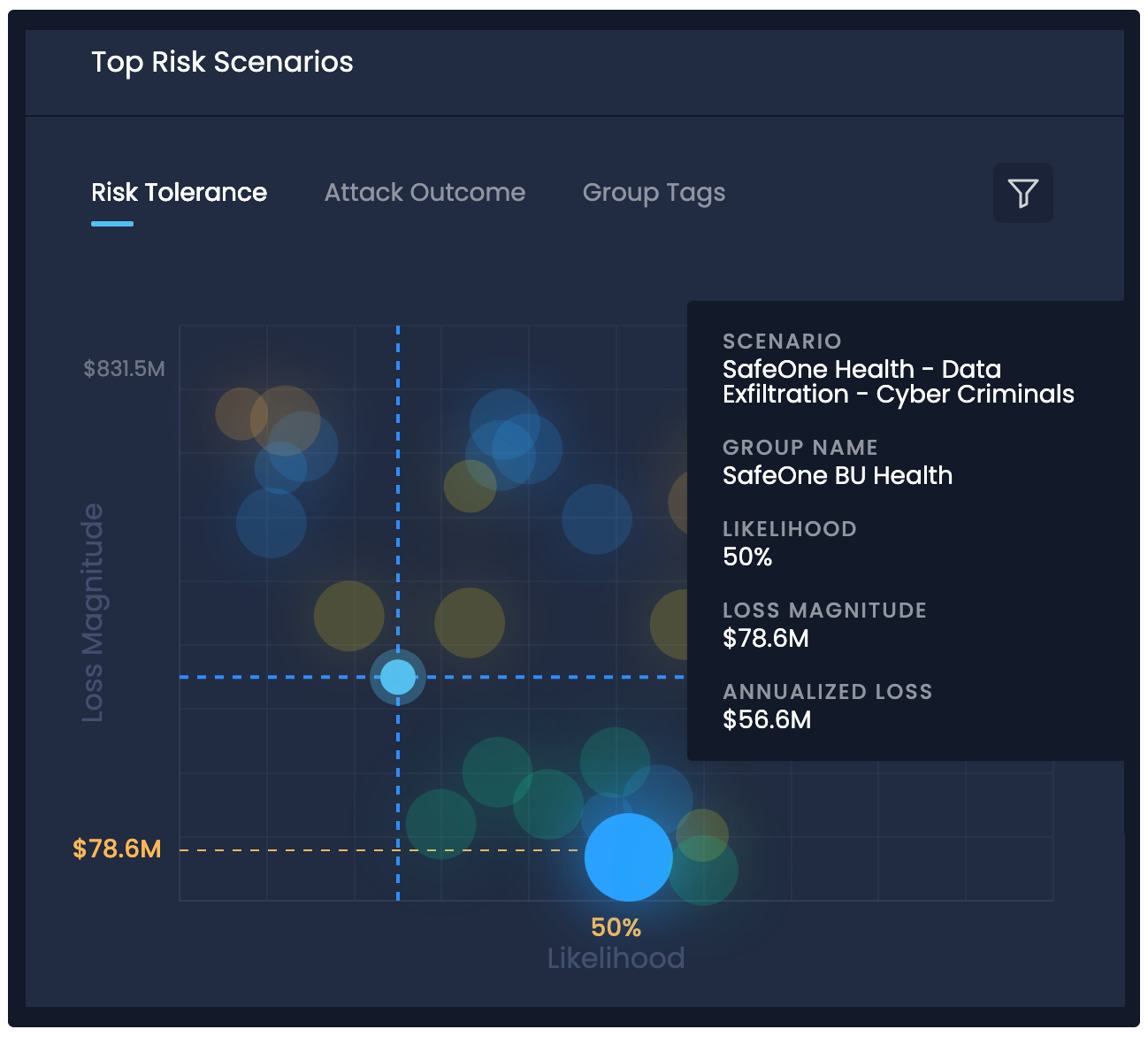
Top Risk Scenarios Modeling on SAFE One Platform
Risk Scenario Modeling
The SAFE One platform also leverages MITRE ATT&CK to identify the controls relevant to each risk scenario by utilizing ATT&CK’s mapping of threat actors to Tactics/Techniques/Sub-Techniques and the mitigations needed to stop them. SAFE One also includes an extensive FAIR-compliant risk scenario library. For each risk scenario assessment, the platform identifies all controls relevant to that risk scenario and identifies how raising maturity levels of certain existing controls or implementing applicable missing controls could reduce likelihood of a cyber event for a measurable ROI. This automatic “what-if” analysis feature of the SAFE One platform provides invaluable control prioritization and remediation insights.
The companion model in the platform, FAIR-MAM (Materiality Assessment Model), is a bottom-up loss magnitude model with fully tunable loss drivers populated by benchmark values calculated from SAFE’s proprietary database of primary attack costs, input from FAIR-CAM for impact controls, your company’s firmographic information, and the input from the Financial Impact Questionnaire, which captures your company’s actual financial and operating data, all to enable high confidence, fully defensible loss magnitude estimates. The applicable loss drivers in FAIR-MAM are automatically updated when the maturities of applicable ‘impact controls’ change. An impact control is one that has the ability to reduce the magnitude of loss, depending on its maturity level. The four CAM controls that are also impact controls are Business Continuity and Disaster Recovery (BCDR), Data Backup and Recovery (DBR), Data at Rest Encryption (DRE), and Incident Response (IR).
NEW: Third-Party Cyber Risk Management Now Included
The SAFE One platform has been updated to leverage FAIR-CAM in identifying the top risk scenarios and most effective controls for third party or supply chain risk. Read our TPRM Solution Brief.
Benefits of Real-time Controls Monitoring and Assessment with FAIR-CAM
FAIR-CAM enables automation of cyber risk quantification. Empowered to run automated, objective, data-driven cyber risk management, organizations can advance from dependence on point-in-time, manual and subjective methods and stay nimble with real-time prioritization of security findings. Done correctly, prioritization decreases the risk of spending on the wrong initiatives. Reducing manual risk assessment also saves time and money and shortens time to value. The net result is more time spent managing risk vs. assessing risk.
FAIR-CAM creator Jack Jones wrote, “The controls landscape is the most nuanced and complex component of an analysis… It’s easy for solution providers to dive into the deep end without understanding some of the important but subtle difficulties of the problem space. It’s also easy for potential customers to be bedazzled by eye candy and good marketing stories, all the while trusting that vendors have done their homework.”
At SAFE, we’ve carefully done our homework developing our FAIR-CAM implementation (including input from Jack) and we’re proud of our work. Contact us for a demo and see for yourself.