Learn the steps — and the benefits — of quantitative analysis
Cyber risks are business risks. The pace and sophistication of cyber-attacks and other cyber-related loss events mean that any business needs to know with certainty the impact in financial terms of cyber loss exposure. In 2024, we’ve seen:
- Change Healthcare, the leading US payments processor of medical charges, made one of the largest ransomware payments in history, but not before the health records of one-third of Americans were leaked.
- A bug in CrowdStrike’s security controls software resulted in the grounding of airline flights, TV stations going off the air, and more business impacts around the world.
A cybersecurity risk assessment is simply good business practice. But how to get the maximum value from a cyber risk assessment? Let’s look at the latest thinking, starting with a useful definition of cyber risk.
What Is Cyber Risk?
Search for definitions of “cyber risk” and you’ll find a lot of wordy, high level or vague language. For instance, this definition from the ISO IEC 27001 standard: “Effect of uncertainty on objectives of entities in cyberspace.”
For clarity and usefulness, let’s turn to the definition used in Factor Analysis of Information Risk (FAIR), the standard for quantifying cyber risk in business terms. According to FAIR, cyber risk is:
“Probable Frequency and Probable Magnitude of Future Loss”
This definition recognizes that risk has two variables, each of which can be quantified to arrive at an overall picture of cyber risk. A higher or lower probability of an event occurring, and a higher or lower probable cost of an event are the two sides of a seesaw that give decision-makers a realistic understanding of the range of risk management choices before them.
Look at this schematic representation of FAIR and you’ll see that Frequency and Loss Magnitude are in turn made up of sub-variables that determine their values, such as the susceptibility of the organization to attack (based on the strength of its controls) on the Frequency side, or the value of the data or other assets on the Magnitude side.
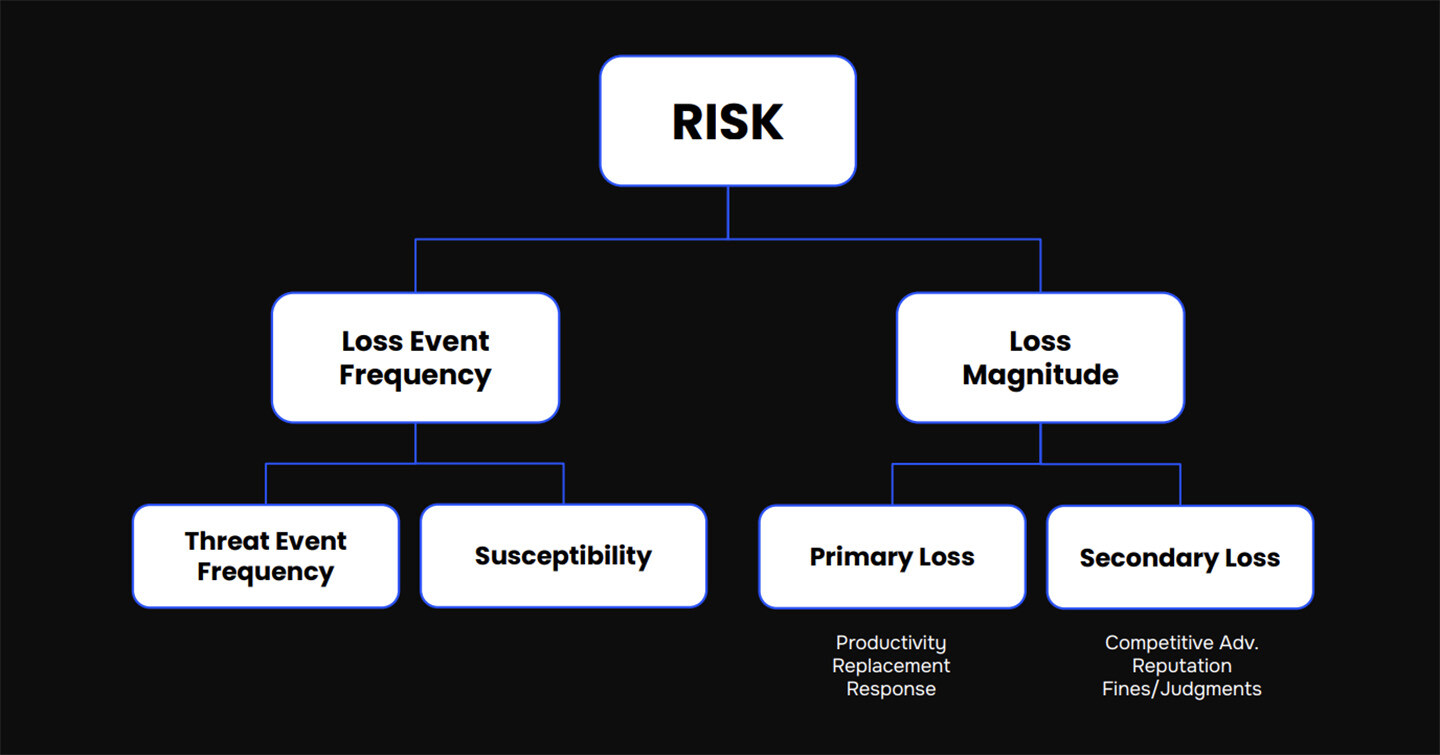
Frameworks such as ISO 27001 and Cyber Risk
Let’s clear up an important distinction between FAIR, which is a standard model of risk (in other words, it defines the relationship among factors that make up risk), and a framework such as the NIST CSF or ISO 27001 (and the updated 27002) or ISO 27005.
The ISO standards recommend types of security controls and help define a risk strategy based on business needs. They are useful as compliance frameworks, and indicators of maturity for security organizations.
But they can’t answer the basic questions for the business, such as “How much risk do we have?” and “If we invest in security controls, how much less risk will we have?”—questions that can only be answered with a model to quantify risk in financial terms.
This definition recognizes that risk has two variables, each of which can be quantified to arrive at an overall picture of cyber risk. A higher or lower probability of an event occurring, and a higher or lower probable cost of an event are the two sides of a seesaw that give decision-makers a realistic understanding of the range of risk management choices before them.
The ISO 27000 standards don’t prescribe a specific approach to analyzing risk and leave it to the risk practitioners to select their preferred analytics model. This is where FAIR comes in, delivering financially derived results that can be communicated across the enterprise as loss exposure and return on investment.
What Is Cybersecurity Risk Assessment?
The FAIR model gives us an accurate definition of cyber risk as well as a method to use the model to analyze and assess cybersecurity risk. That method is 1) a risk scenario plus 2) a Monte Carlo simulation. Let’s dig into 1 and 2 – but first…
Vocabulary Break: Risk Assessment vs. Risk Analysis: What’s the difference?
A cyber risk analysis examines risk scenarios (see below) and quantifies them for Frequency and Magnitude. A cyber risk assessment is a broader effort to evaluate risk scenarios and remediation options (say for information systems or for a business unit) to give decision-makers an overall view of risk management. The distinction is often overlooked – too bad, because risk assessments should be based on rigorous risk analysis.
Definition: Cyber Risk Scenario
A risk scenario is the basic building block of quantitative cyber risk analysis. Here’s what one looks like:
“Scenario: Analyze the amount of risk associated with cybercriminals breaching personally identifiable information (PII) from a ‘crown jewel’ database.”
The three key elements of a cyber risk scenario are
- An asset: crown jewel database containing PII
- A threat: cybercriminals
- An effect: confidentiality loss
Definition: Scoping a Risk Scenario
Defining the asset, threat, and effect is “scoping” a risk scenario. Scoping forces us to be specific in identifying the problem we want to solve. It keeps us from wandering off in pursuit of things that may exist in the world of cybersecurity but are not information security risks with an asset, a threat, and an effect – for instance, “the cloud” or “generative AI.” Scoping also guides us to gather the appropriate data to add quantification to our analysis.
Finally, scoping serves a fundamental goal of producing risk analysis that’s useful to decision makers: pointing us toward focusing on the probable scenarios, not the possible ones – there are always an infinite number of possibilities.
Gathering Data for a Cybersecurity Risk Assessment
Our goal in a FAIR analysis is to quantify the Frequency of cyber incidents (expressed as some number of occurrences in a year) and the Magnitude of impact (expressed in dollar terms).
On the Frequency side, we can tap our own organization’s records of incident frequency, as well as an increasingly improving industry data on incidents. But, of course, we are also keenly interested in what percentage of incidents make it through our controls. In FAIR practice that’s Susceptibility – and we have a vital tool for data gathering in the FAIR Controls Analytics Model (FAIR-CAM), an extension of the FAIR standard that allows us to accurately quantify the effect of controls on Frequency and Magnitude.
On the Magnitude side, we have another tool in the FAIR toolkit for data gathering: the FAIR Materiality Assessment Model (FAIR-MAM). Organizations use FAIR-MAM to build a loss model guided by categories and subcategories of cost drivers to arrive at highly accurate cost estimates based on their existing financial risk projections.
Definition: Monte Carlo Simulation
The FAIR model is a powerful tool on its own but we pair it with a Monte Carlo simulation analysis engine that runs our data through thousands of scenarios to produce the clearest view of the outcomes in a range of probabilities.
Comprehensive Definition of Cybersecurity Risk Assessment
To sum up, a cybersecurity risk assessment provides decision-makers with a clear picture in business terms of the risk (or loss exposure) for the organization from a specific scenario or set of scenarios that include identifiable threats, assets at risk, and the potential impacts to the organization.
The assessment should be expressed as a range of probable outcomes, quantified in terms of likelihood of occurrence and magnitude of financial impact.
The assessment should be transparent and defensible, both in the model that generates the analysis and in the data that feeds it.
Finally, a cyber risk assessment should always address a problem that is important to the organization.
7 Benefits of Performing Cybersecurity Risk Assessment with Risk Quantification
A cybersecurity risk assessment in quantitative terms confers a long list of advantages including:
- Identify vulnerabilities and risks, prioritizing top risks for greater efficiency in cyber risk management processes.
- Focus defenses on top controls for best cyber risk reduction
- Communicate on cyber risk to the business in business terms — cost/benefit analysis, return on investment, risk tolerance – avoid technical jargon
- Prioritize cybersecurity budgets based on risk.
- Run a “what if” analysis on new investments in cybersecurity
- Calculate risk reduction over time – justify cybersecurity program performance, set KRIs, KPIs
- Comply with regulatory reporting on material loss exposure
7 Steps to Perform a Cybersecurity Risk Assessment
These are some of the common steps that risk management and security teams follow in executing an assessment:
Step 1: Determine Asset Value
A critical first step on your way to estimating Loss Magnitude is to identify the asset or assets in your risk scenario and figure probable loss. The FAIR-MAM model is of high value here. Some assets to consider might be:
- Customer databases with sensitive personal information could be breached, leading to legal or regulatory liability costs
- Intellectual property on servers that could suffer data breaches, leading to loss of market position and sales
- Web applications critical for e-commerce attacked, leading to business interruption
- Hardware that could be bricked in a ransomware attack requiring replacement – and ransom payment
Step 2: Conduct Data Audit and Prioritize Assets
A two-step process both to identify the value of the data contained in the asset and the strength of data protection controls around the asset.
Step 3: Identify and Prioritize Cyber Threats and Vulnerabilities
An opportunity to apply FAIR analysis, coupled with the MITRE ATT&CK framework. MITRE can show the likely cyber threat actors for your organization, their typical methods, and their relative strengths. FAIR-CAM can analyze the strength or vulnerability of your control array. Together you can derive a good reading on the Frequency side of your assessment.
Step 4: Analyze and Evaluate Security Controls
A job for FAIR-CAM, the derivative model of FAIR that describes and quantifies the function of each control for risk reduction, documents the interdependence among controls, and the effectiveness of a multi-control environment overall.
Step 5: Analyze the Impact and Probability of Different Cyber Risk Scenarios
The FAIR method guides us to identify the threat, asset, and effect of a cyber risk scenario, gather the relevant data, and run a Monte Carlo simulation to analyze both the likelihood and financial impact of a cyber risk scenario, enabling us to give business decision-makers a clear picture of the range of probable outcomes of a single scenario or an assessment of the security posture of a corporate entity such as a business unit.
Step 6: Prioritize Risks Based on the Cost of Prevention Compared to Information Value
With quantitative cyber risk analysis, we can score and prioritize risks against each other, from the point of view of the likelihood of a cyber event and probable cost. We can then assess preventative controls for their cost compared to the probable risk reduction they would confer.
Step 7: Monitor and Document Results
Regular risk assessments are a must in a changing risk landscape – but continuous monitoring of risk scenarios and controls is the best solution.
SAFE’s Approach to Cyber Assessments
While FAIR has been widely recognized as the gold standard for cyber risk assessments, SAFE’s cyber risk quantification (CRQ) platform (SAFE One) takes FAIR to a new level. We bring the benefits of cyber risk assessment automation plus integrations with the world’s leading cybersecurity tools and products – all augmented with AI. The result is CRQ scaled to the enterprise, with real-time risk monitoring and management.
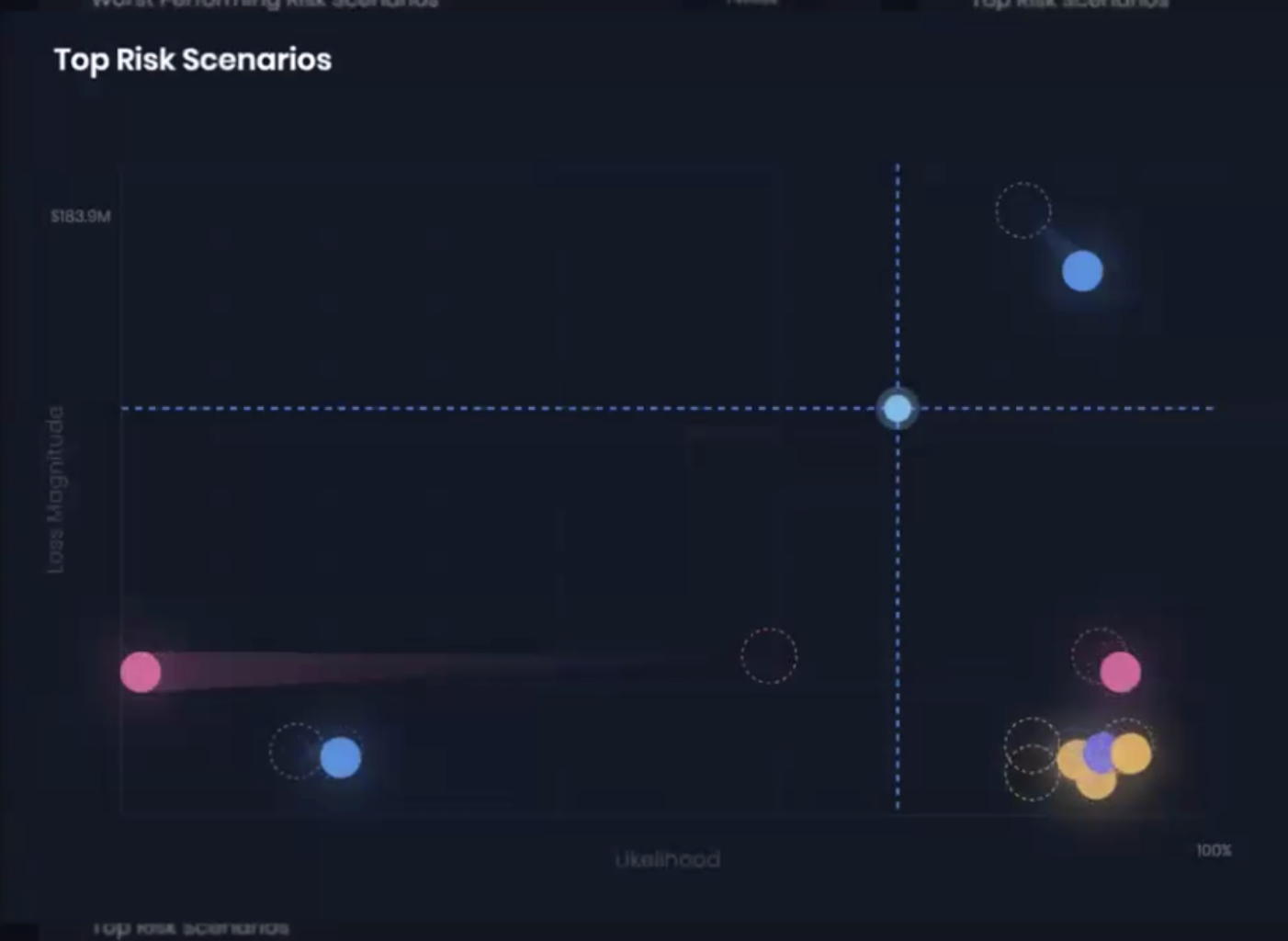
The SAFE platform quantifies risks in FAIR terms for frequency and magnitude.
7 Benefits of Moving Your Cyber Risk Assessment Program to Automated FAIR
1. Graduate from static risk assessment to dynamic and real-time
SAFE One aggregates multiple cyber signals in a single place, providing organizations with a singular view of enterprise security risk and empowering leaders to manage risk with a standardized, real-time automated solution.
2. Gain a continuous view of changing cyber risk and control effectiveness.
Don’t settle for point-in-time analyses anymore. Get a continuous view of the state of your cybersecurity controls and most critical cyber risks with AI-driven reporting.
3. Quantify risk based on open standards, FAIR and MITRE ATT&CK.
Gain the confidence in your cyber risk assessments that open standards bring. The SAFE One platform enables FAIR, MITRE ATT&CK, and NIST CSF in a transparent and easy-to-justify way, ensuring a CISO can demonstrate alignment with business requirements.
4. Quickly react to actionable insights to prioritize critical control gaps.
The solution provides breach likelihood and financial impact – and how it compares to industry standards.
5. Built-in, detailed risk scenarios specific to your industry.
Our solution includes 120-plus, ready-to-use risk scenarios tailored to your industry to speed up your risk assessment. Or your choice to create your own scenarios.
6. Continuous cyber risk monitoring, alert to emerging cybersecurity threats. We use the MITRE ATT&CK framework to scope scenarios to meet threat actor practices with continuous updating to counter emerging risks.
7. FAIR-CAM and FAIR-MAM are built-in and automated. We lead the industry in the adoption of these game-changing models, FAIR-CAM (for controls assessment) and FAIR-MAM (for measuring impact).
Enable your business to go safely, faster. Let us show you cyber risk assessment on the SAFE One. Schedule a demo now!



