Cloud Outages Could Massively Cost Your Company—Follow this Guidance from NYDFS
Key regulator elevates third-party risk management (TPRM) from a compliance checkbox to an executive-level mandate.

Data centers everywhere
That moment of complete dependency—where your entire customer experience, financial stability, and regulatory standing hang on the uptime of a third-party service—is the heart of the modern cyber risk challenge. The October 2025 outages of both Amazon AWS and Microsoft Azure, followed by Cloudflare in November, heavily underlined this reality. For AWS, the failure of a core system in a single US region cascaded into disruptions across global banking, social media, finance, and logistics, costing businesses three hours of initial disruption, followed by intermittent service breaks over 16+ hours. Probable losses in the tens of billions of dollars.
Jacqueline Lebo is Director of Risk Advisory at SAFE
This systemic risk is precisely why the New York State Department of Financial Services (NYDFS) has issued critical new guidance on managing risks related to Third-Party Service Providers (TPSPs). This is not just regulatory housekeeping; it’s a direct response to the escalating danger of our interconnected supply chain. The message is clear for the financial industry: You cannot delegate responsibility for compliance and resilience.
Even if you are not in finance, you’ll find the NYDFS Guidance on Managing Risks Related to Third-Party Service Providers highly actionable.
NYDFS Guidance: An Executive Mandate for Third-Party Resilience
The DFS guidance serves as a crucial clarification of the expectations under 23 NYCRR Part 500 (the Cybersecurity Regulation), with a specific focus on the entire TPSP lifecycle. It elevates third-party risk management from a compliance checkbox to an executive-level mandate, requiring Senior Governing Bodies and Senior Officers to actively oversee and challenge TPSP risk decisions.
Here is the essential, four-part lifecycle demanded by the DFS:

Tiering venors on the SAFE One platform
1. Assessment (Due Diligence and Selection)
The initial phase must be characterized by data-driven risk classification. You must:
- Risk-Classify TPSPs: Vendors must be tiered based on the sensitivity of data accessed (Nonpublic Information or NPI), the type of system access (especially privileged access), and the criticality of the service to your operations.
- Validate Controls: Due diligence must verify the TPSP’s existing cybersecurity program, incident response capabilities, and its management of downstream vendors (fourth-parties). External audits (e.g., SOC 2, ISO 27000) are explicitly mentioned as validation mechanisms.
2. Mitigation (Contracting)
The vendor contract is your primary control. It must contain strict, enforceable provisions that enforce your security standards:
- Access and Encryption: Mandate compliance with Part 500 requirements for Access Controls (including Multi-Factor Authentication) and Data Encryption (in transit and at rest).
- Cyber Event Notification: Require immediate or timely notice of any Cybersecurity Event that impacts your Information Systems or NPI (Non-Public Personal Information).
- Exit Obligations: Crucially, specify requirements for data deletion/migration and the formal certification of destruction upon termination.
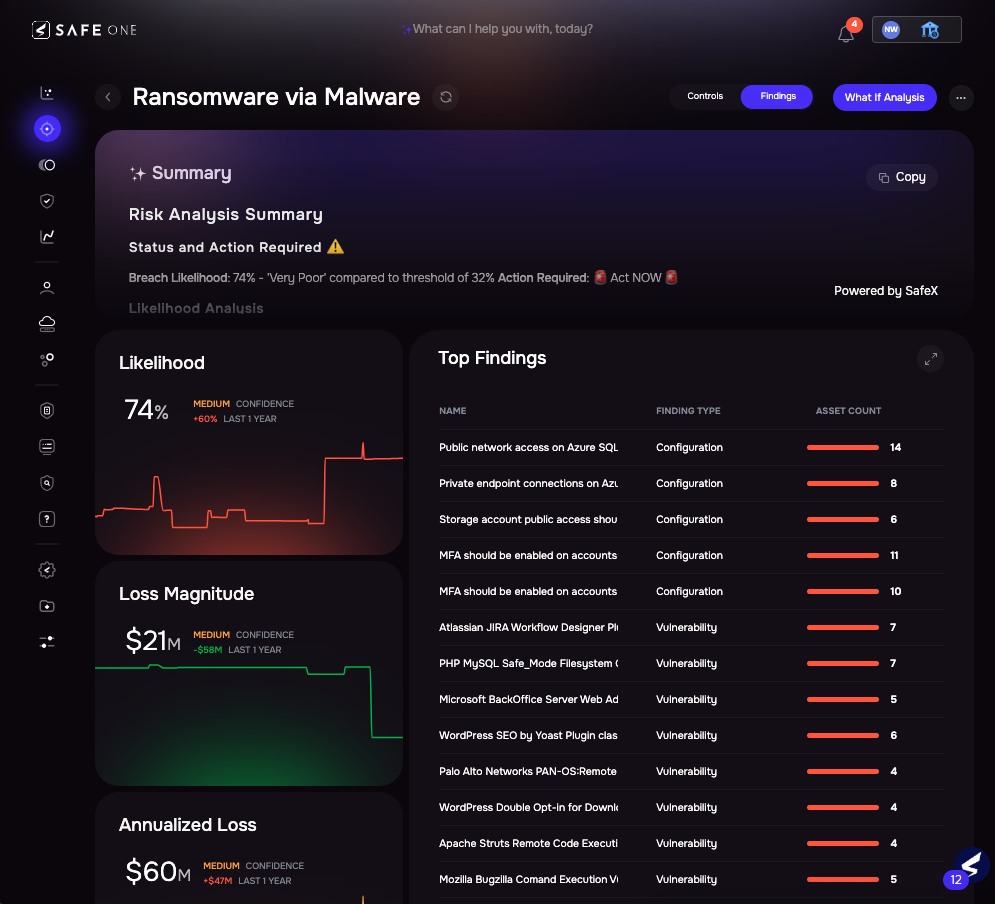
Monitoring risk with the SAFE One platform
3. Control (Ongoing Monitoring and Oversight)
Risk is dynamic; monitoring must be continuous. The DFS requires:
- Periodic, Risk-Informed Assessment: Oversight must be layered and informed by the TPSP’s evolving risk profile, moving past outdated annual questionnaires.
- Resiliency Integration: TPSP risk must be incorporated directly into your Incident Response and Business Continuity Plans (IR/BCP). The requirement to test how you would rapidly transition away from a disruptive TPSP is a clear link to the concentration risk exposed by last week’s cloud outage.
4. Verification (Termination)
The relationship offboarding must be secure and auditable:
- Access Revocation: Ensure the TPSP’s access is immediately and comprehensively disabled at termination, with special attention paid to residual access points like shared cloud tokens and API keys.
- Final Review: Conduct a final risk review to confirm all obligations were met, access is fully revoked, and all data control requirements were successfully enforced
The SAFE Path: Automatically Meeting the New York DFS Mandate
Complying with this guidance using legacy, manual TPRM tools is slow, resource-intensive, and inherently reactive—leaving you exposed to the very concentration and outage risks the DFS and the recent AWS failure highlighted.
The SAFE Third-Party Risk Management (TPRM) solution is architected to automatically force organizations to meet these new requirements by pivoting to a quantitative, risk-based approach.
1. Automated, Contextual Risk Classification 🎯
The DFS mandates classifying vendors based on risk and criticality, precisely to prevent the kind of blind spot that amplified the recent AWS service disruption. SAFE automates this process by moving beyond generic scoring to contextual Smart Tiering—a critical capability for meeting regulatory demands efficiently.
The initial process for Smart Tiering is not solely based on the SAFE Score itself, but on the customized criteria that truly define a vendor’s impact:
- Risk-Based Tiering: You define the criteria for categorization, often centered on the business impact, which directly aligns with the DFS’s requirement to classify TPSPs based on factors like:
- The criticality of services provided to the business (e.g., an outsourced claims processing platform vs. a marketing software tool).
- The volume and sensitivity of Nonpublic Information (NPI) the TPSP is permitted to access.
This is a dynamic capability that proved invaluable following the massive AWS outage on October 20, 2025:
Customer Success Snapshot: One of our financial services customers, facing an immediate crisis following the AWS disruption, leveraged the SAFE platform to quantify their exposure. In just two clicks, they were able to:
- Automatically pull a complete list of all third parties known to leverage AWS for critical services.
- Filter that list by their predefined Smart Tiering (e.g., Tier 1: High Criticality/High NPI Access).
This allowed them to immediately report to the board, within hours, on which critical service lines and high-risk data stores were directly impacted by the outage, satisfying the urgent executive-level clarity needed during a systemic event.
This capability—to apply predefined business context to real-time outage data—is how SAFE ensures that your periodic assessment and incident response are always informed by a truly risk-based and accurate vendor classification, far exceeding the speed and relevance of manual processes.
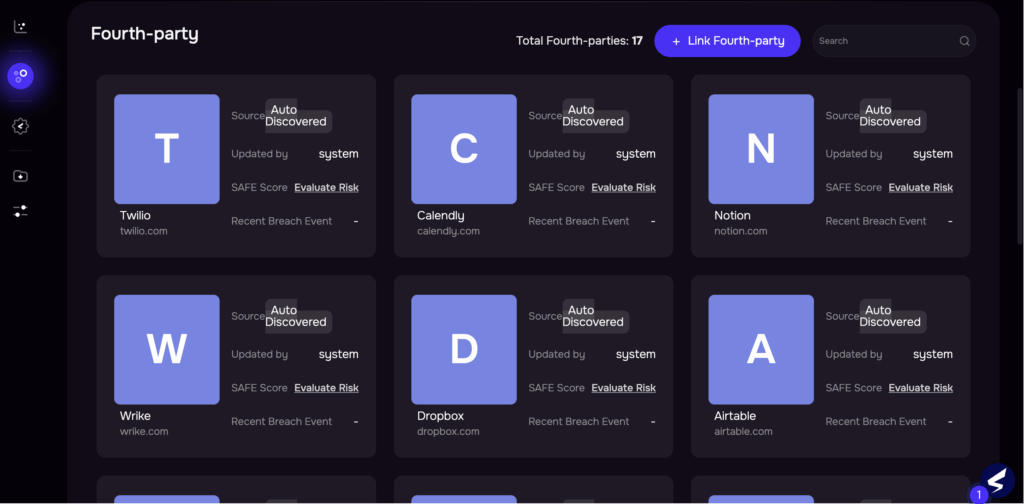
Mapping fourth partiew on SAFE One
2. Focus on Operational Resilience Scenarios (Meeting NYDFS Mandate)
The NYDFS guidance directly calls for entities to integrate third-party risk into their Incident Response and Business Continuity Planning and to test how they would rapidly transition to alternate providers in the event of a disruption. This moves the conversation beyond data breaches and into the territory of systemic operational failure—the precise kind demonstrated by the recent AWS outage.
The SAFE One platform is specifically engineered to address this regulatory requirement through:
- Translating Compliance to Quantifiable Resilience: The DFS requires planning for major vendor outages. Unlike simple security ratings that only measure technical hygiene, the SAFE Score uses a quantitative risk model to specifically assess and measure the financial loss exposure from key scenarios.
- Prioritizing Outage Risk: Outage Scenarios—the large-scale operational disruption, like the DNS failure that sparked the AWS incident—are consistently modeled as one of the top three scenarios contributing to a third-party’s SAFE Score. This modeling ensures that your TPSP risk program is inherently focused on the most critical operational threat vectors, providing a data-driven justification for resilience investments.
- The AWS Resilience Test Case: Dynamic Concentration Risk Reporting: The true value of the platform during a systemic event, such as the AWS outage, lies in its ability to provide immediate fourth-party concentration visibility, enabling rapid response:
- Automated Fourth-Party Mapping: The SAFE platform automatically tracks fourth parties for the organization. When a large, systemic outage occurs (like the AWS service disruption), this capability allows risk teams to instantly pull a list of all their vendors leveraging that affected platform.
- Rapid Executive Reporting: By combining this list with your predefined Smart Tiering (based on service criticality), you can identify the exact business lines facing disruption. This allows decision-makers to rapidly determine which critical services are affected and to immediately report to the board on the associated financial loss potential.
- Enabling Mitigation: This rapid, context-aware reporting allows the organization to initiate calls to switch to backups or alternative providers within hours, directly satisfying the DFS’s directive to assess and test transition capabilities.
This capability ensures your organization can demonstrate to regulators that it has a data-driven process to identify, quantify the impact of, and rapidly respond to large-scale third-party concentration and operational disruption risks, directly satisfying the spirit and letter of the DFS’s IR/BCP and monitoring requirements.
3. Quantifiable and Defensible Reporting (The Language of the Board)
The DFS guidance requires Senior Officers to review and approve cybersecurity policies and to engage actively in risk management. They won’t approve budgets based on vague security scores or technical jargon; they only understand risk when it’s translated into dollars.
The recent AWS outage provides a stark financial case study, with billions most likely lost to systems downtime.
These numbers are critical because they instantly change the conversation from technical failure to business loss exposure. The question shifts from, “Did the vendor follow the controls?” to, “What is the probability we will lose $50 million in revenue and regulatory fines due to this vendor’s failure?”
- The Power of Quantified Loss: The SAFE One platform provides this quantified, financial view of third-party risk. By leveraging Cyber Risk Quantification (CRQ), we replace subjective ratings with a defensible, financial loss magnitude for each TPSP relationship.
- Actionable Data Points: The SAFE Score uses a robust risk model (based on the Open FAIR™ standard) that allows you to calculate the Expected Loss from various scenarios (e.g., a data breach, a major outage). This means you can report to your board with precision:
- “We are facing an expected annual loss of $X million due to control gaps in our Tier 1 TPSP base.”
- “An investment of $Y in remediation will reduce our third-party loss exposure by Z%.”
This is how SAFE empowers you to communicate with the executive suite: by framing the third-party risk program not as a cost center, but as a mechanism for avoiding tangible financial losses like the hundreds of millions seen in the wake of the recent AWS outage. This satisfies the DFS mandate by providing the transparency and quantifiable data necessary for executive oversight and strategic decision-making.
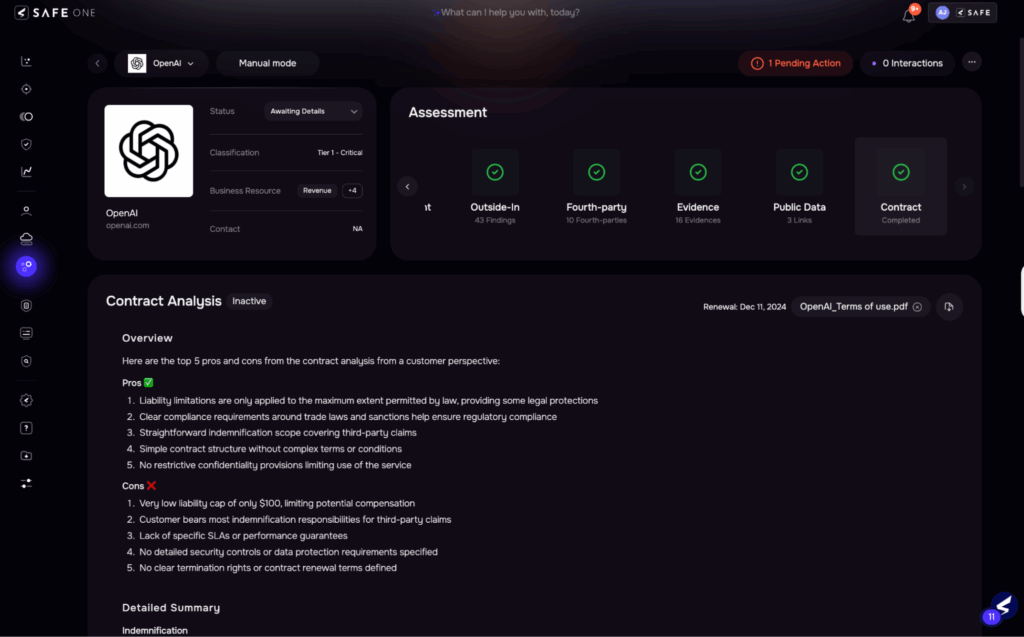
Contract analysis, SAFE One
4. AI Automation: The End of the Manual Contract Disaster
Manual contract review is the antithesis of the efficiency and scalability demanded by the DFS. It is slow, reactive, and prone to human error, leaving your business exposed to non-compliant clauses. Legal and risk teams cannot keep pace with the volume of contracts when relying on manual reading and redlining.
This is precisely where the SAFE Contract Analyzer Agent steps in. As part of SAFE’s Agentic AI-driven platform, it automates the most time-consuming part of the TPSP risk lifecycle, ensuring immediate compliance with NYDFS contractual mandates:
| DFS Contractual Mandate (23 NYCRR § 500.11(b)) | SAFE Contract Analyzer Action |
| Access Controls (MFA) & Encryption | Automatically scans contracts for language requiring Multi-Factor Authentication(§500.12) and Encryption for NPI in transit and at rest (§500.15). |
| Breach Notification | Flags missing or insufficient notice clauses for Cybersecurity Events, ensuring the TPSP’s reporting timeline meets your required threshold. |
| Compliance Representations & Warranties | Analyzes the contract’s representations of the TPSP’s cybersecurity policies, flagging vague or non-specific language that weakens your legal protection. |
| Data Use and Exit Obligations | Identifies clauses related to data deletion and transfer restrictions, ensuring alignment with your offboarding policies. |
With the drag-and-drop of a vendor agreement, the Contract Analyzer Agent reviews these provisions against your internal playbook and regulatory requirements in minutes, not weeks. This automation is critical for meeting the DFS’s requirement for strong contractual protections without creating internal operational delays or bottlenecks.
Is your TPRM program ready for the next systemic outage? Discover how to future-proof your third-party ecosystem with SAFE’s risk-based solution.



