SAFE Risk Radar Report Reveals Data-Driven Insights on Cyber Resilience and More
New research digs into third-party risk data, ransomware payouts, SEC filings and more sources to reveal surprising truths.

SAFE, in collaboration with the FAIR Institute, has released the first in a series of Risk Radar quarterly reports that will dig deep into data science and threat intelligence for actionable insights for CISOs, CROs and other cybersecurity leaders.
In our research, we analyzed more than 1,000 third-party attacks, 210 8-K filings to the SEC on cyber incidents, an extensive database of losses due to cyber-attack, accessible at the FAIR Institute’s How Material Is that Hack site, and more sources. SAFE is sponsoring the Risk Radar initiative.
Our initial findings challenge some accepted beliefs behind cyber risk management. Whether you are using the Verizon DBIR, CrowdStrike Global Threat Report or other standard data source, they all focus on threats – hacks, breaches, etc. – not risk. No organization really manages threats – but they can manage risk, if they understand it, the educational goal of the Risk Radar initiative.
We invite you to dig into the Risk Radar report:
View the Report Summary Findings
Replay a Webinar hosted by SAFE Chief Operating Officer Pankaj Goyal and Head of Product Marketing Resha Chedda
Key Insights from the Risk Radar Report
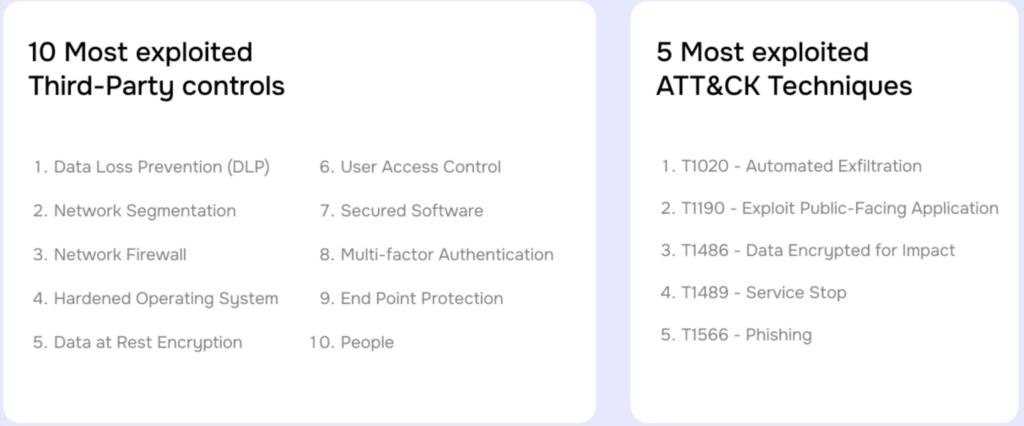
Third-Party Cyber Risk: Must-Have Controls
Enterprises commonly prioritize their third-party vendors or partners for risk by the size of the third party or the contract. The report found, as Pankaj says, “a small startup might be holding your most sensitive data. The risk is determined by how much data exposure or business interruption they could cause.”
In fact, the report found that “smaller third parties were disproportionately attacked,” Pankaj says, as criminals have discovered they are an easier vector into larger, better defended enterprises. Data is where the danger lies; over 90% of the attacks in the study were data exfiltration for financial gain.
Third party risk management today is broken, the report finds, with first and third parties overloaded with lengthy questionnaires or reporting of evidences. The Risk Radar report provides a valuable service by revealing the most exploited third-party controls and most common attack techniques – important clues to a focused, rational approach to TPRM.
Materiality: How to Benchmark
It’s been over a year since the SEC’s new requirements to report on material cyber incidents shook boards and risk managers alike, as recognition sunk in that they didn’t have a reliable way to estimate the financial impact of cyber attacks.
The Risk Radar Report shines a light on a way forward. With the FAIR Institute’s How Material Is That Hack data, the SAFE research team studied SEC filings and calculated losses as a percent of quarterly revenue: median losses were 1.2%, average losses 4.1% of quarterly revenue. “You can use these benchmarks to have a discussion around risk tolerance in your organization,” Pankaj notes. The report also uncovered that two-thirds of the losses were due to business interruption, a good indicator that investing in resilience is also investing in risk mitigation.
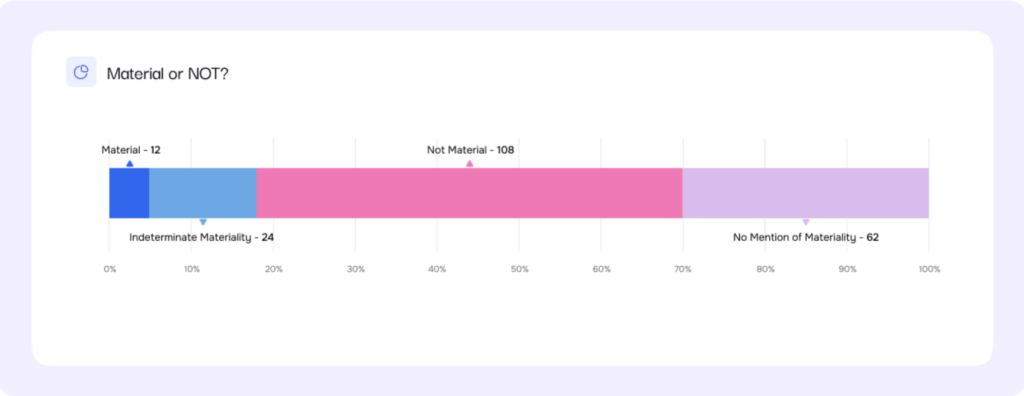
Regulatory Reporting: Filing First, Asking Questions Later
Risk Radar took a close look at the 2024 SEC filings and found some surprising results. “The big question is, did this ruling improve the reporting of materiality?” Pankaj says. “The answer, at least for the first 12 months, seems to be yes.” But only 6% of the companies reported on incidents they called material. More than half reported incidents that were not material. Pankaj said this could be confirmation that regulated companies still don’t have a handle on their cyber incident loss exposure, compounded by the requirement to report within four business days, and were filing fast but not full disclosures.
Key Tadeaways for CISOs from the Risk Radar Report
Watch the webinar for the full menu of recommendations generated by the report findings. Some of the key takeaways:
- Rationalize your TPRM strategy – less flipping through questionnaires, more focus on the ten top controls.
- Start prioritizing among your third parties based on the size of the loss exposure they create, not the size of the company or contract.
- The dynamic threat landscape requires continuous monitoring and testing of third parties,
- Shift investment to solutions that minimize business disruption.
Dig into the Risk Radar Report
View the Report Summary Findings
Replay the Webinar
Learn more about SAFE, the leader in AI-powered, continuous cyber risk management,



