Overcoming fragmented tooling, budgetary pressures, and miscommunication through a carefully executed CRQ plan

By Grant Rexer
The world of cybersecurity is often shrouded in technical jargon and a seemingly endless list of threats. But what if you could translate that complexity into the language of business – cold, hard cash?
That’s precisely what we do with large, multinational organizations, behemoths operating across Europe, North America, India, and South America. And, against a backdrop of decentralized tools, tight budgets, and diverse regional requirements, we achieve the seemingly impossible: a fully operational cyber risk quantification (CRQ) program stood up in months.
Grant Rexer is Senior Partner, Risk Strategy at SAFE, with 20+ years of enterprise software implementation experience.
The Multinational Company Challenge: A Fortress with Many Doors
Imagine a company with operations spanning continents, each region boasting its own IT infrastructure, preferred security tools, and unique regulatory landscape. This is typically the reality we face. Their existing cybersecurity posture, while robust in many areas, we often find suffers from a common multinational predicament: decentralization.
- Fragmented Tooling: Different regions mean different security information and event management (SIEM) systems, vulnerability scanners, and control frameworks. This makes it incredibly difficult to get a holistic view of an organization’s cyber risk.
- Budgetary Pressures: Every dollar spent on cybersecurity needs to demonstrate clear ROI, a tough sell when risk is discussed in abstract terms like “high” or “medium.”
- Regional Nuances: A cyber threat in Germany might have a different impact or require a different response than one in Brazil or India. Tailoring a quantification program to account for these variations is crucial.
- Bridging the Language Gap: Security teams speak “threats” and “vulnerabilities.” Leadership teams speak “profit” and “loss.” Our biggest challenge typically is translating the former into the latter.
Our Cyber Risk Quantification Program Strategy: Precision, Persuasion and a Phased Approach
We’ve learned a “big bang” approach doesn’t work. Instead, we adopt a highly collaborative and iterative strategy, focusing on rapid value delivery.
- Pilot Program & Executive Buy-in: We start with a focused pilot in one key region, demonstrating the power of risk quantification with real-world scenarios. This tangible proof-of-concept secures crucial executive sponsorship, without which global rollout would be impossible. We show how a potential ransomware attack isn’t just “bad,” but could cost X million dollars in lost production and recovery costs.
- Standardization, Not Overhaul: We don’t rip and replace existing security tools. Instead, we focus on establishing a common data ingestion and normalization layer. This allows us to pull relevant data from disparate sources into a centralized platform for analysis, bridging the gap between fragmented systems.
- Risk Scenarios Tailored to Business Impact: We work closely with business units to identify their most critical assets and the cyber threats that could impact them directly. Instead of generic threats, we focus on standardizing risk scenarios across regions to be able to quickly see which business units are most at risk. This also makes the risks tangible and relevant to business leaders.
- Leveraging FAIR Methodology: Utilizing the SAFE One platform allows us to quickly adopt the Factor Analysis of Information Risk (FAIR™) methodology and MITRE ATT&CK framework. These industry-standard models allow us to express risk in financial terms (e.g., “There is a 70% chance of experiencing a cyber event costing between $500k and $2M in the next 12 months”). This provides the objective, quantifiable data the leadership team needs.
- Regional Champions and Training: We establish “risk champions” in each major region. These individuals are trained extensively on the new methodology and tools, becoming local evangelists and ensuring the program’s sustainability. They understand the local context and can articulate the value of the program to their regional stakeholders.
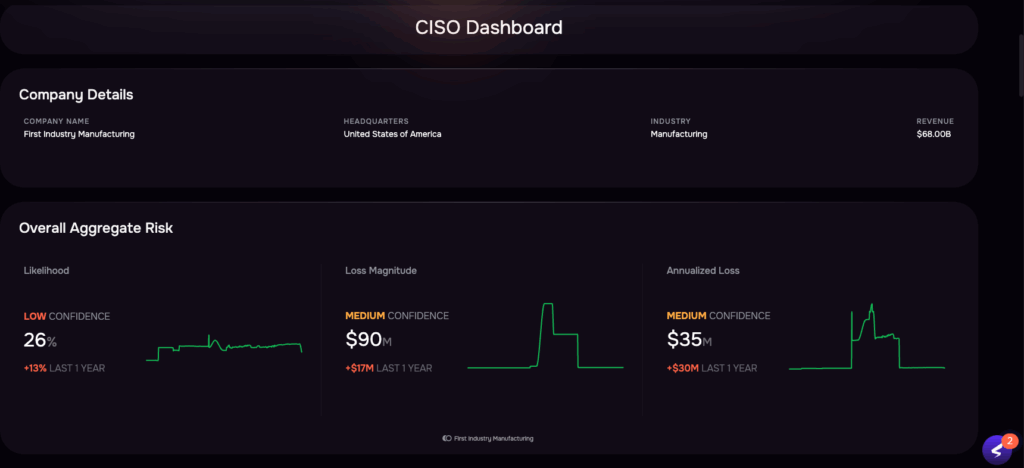
Overall view of risk from a CISO dashboard, SAFE One platform
The Risk Management Outcome: Clarity, Control and Continuous Improvement
In months, a giant multinational has a fully functional cyber risk quantification program. The impact is immediate and profound:
- Clearer Prioritization: For the first time, the leadership team can see which cyber risks pose the greatest financial threat to the organization. This enables them to make data-driven decisions about security investments, allocating resources to where they will have the most impact.
- Empowered Budgeting: Cybersecurity budgets are transforming from being seen as a “cost of doing business” but as strategic investments with a clear ROI. Security teams can now justify their requests with quantifiable financial risk reduction.
- Enhanced Communication: The language barrier between technical security teams and business executives dissolves. Everyone can now discuss cyber risk in a common, financially-oriented framework.
- Proactive Risk Management: The new cyber risk management program provides a continuous feedback loop, allowing the organization to model the financial impact of new threats or the effectiveness of proposed security controls before implementation.
- Regional Alignment: While local autonomy remains, a standardized approach to risk quantification ensures that all regions are assessing and reporting risk using the same metrics, providing a truly global picture.
This journey can be a testament to the power of collaboration, strategic implementation, and the ability to translate complex technical challenges into understandable business metrics. For a company of huge scale and complexity, achieving such a transformation in months isn’t just a success story; it’s a blueprint for resilient cybersecurity in the modern industrial landscape.
Now, imagine seeing the financial impact of a cyber attack on your organization visualized in a clear, concise report – like the CISO dashboard from SAFE above. Schedule your customized demo now!


