How to Manage Risk From Attack Surface Expansion

The attack surface of every organization across the world is growing in complexity. Rapid digitalization, cloud adoption, and interconnected systems increase the volume of possible entry points for attackers, which organizations cannot afford to ignore if they are to prevent a breach of their systems. So what should organizations do to address the risk from attack surface expansion?
Changes in the way we work, together with greater use of public cloud, highly connected supply chains, and use of cyber-physical systems have exposed new and challenging attack “surfaces.” This leaves organizations more vulnerable to attack. Gartner recommends security leaders look beyond traditional approaches to security monitoring, detection, and response to manage a wider set of risks.
– Gartner’s 7 Top Cybersecurity Trends in 2022
The problem with current technology stacks
Working with some of the world’s largest companies on their transformation to cloud and hybrid environments, here at SAFE we see the evolving challenges that security teams are up against. Despite spending billions on deploying the latest technologies to identify risk from internal and external signals, SOC teams, security teams, and security analysts find themselves overwhelmed by the number of data signals they have to deal with on a constant basis. Most organizations leverage solutions such as Security and Information and Event Management Systems (SIEMs) that help aggregate and manage the signals. Although security teams might be able to centralize this data, do they know the likelihood of a breach? How do they know what to prioritize?
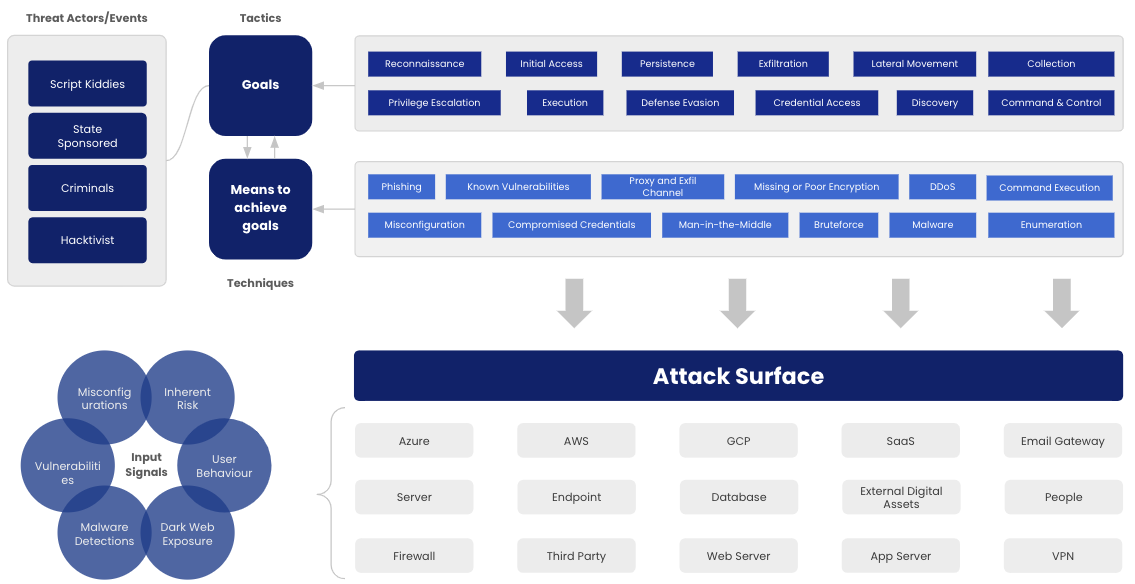
Translating signals into risk
The SAFE platform’s data aggregation and correlation engine helps put signals into context. Signal collection is not limited to open vulnerabilities like most aggregators, instead, SAFE ingests vulnerabilities, misconfigurations, malware, threat intelligence, open source intelligence, user behavior, plus more.
From public cloud infrastructure to on-premise servers, web applications to SaaS applications, and employees to third parties, SAFE has the ability to collect signals from across your entire technology ecosystem and your ever-expanding attack surface. Unlike other platforms, SAFE can also detect Shadow IT using automated outside-in assessments.
Signal collection is not limited to security related information. We integrate with Configuration Management Databases (CMDBs) such as ServiceNow, and automatically import tags from your cloud assets. This metadata is used to categorize signals based on business context and help measure cyber risk for each of your business units.
The SAFE platform has API-based connectors allowing you to collect signals from virtually any source
- It integrates with some of the world’s leading cybersecurity technologies, including Qualys, Tenable, and Crowdstrike to import vulnerabilities, misconfigurations and malware from across your hybrid environment.
- It monitors your cloud attack surface using our one click connectors for AWS, Azure and GCP.
- It imports misconfigurations from your business applications, such as Salesforce, Snowflake, and G-Suite.
How can SAFE’s CRQM platform transform your cyber risk management?
Modern cyber risk management is broken. It’s siloed, point-in-time, and manual. None of these attributes are conducive to managing the volumes of complex risk faced by enterprise organizations. SAFE has created a better way: combining the power of automation and AI with cyber risk quantification – in real-time. Our dedicated Cyber Risk Quantification and Management platform (CRQM) automatically collects signals from your internal attack surfaces – people, technology, and third parties. These signals are aggregated and combined with external threat intelligence and global cybersecurity frameworks. Once complete, the data is parsed through data science- based algorithms to generate three outputs:
- A SAFE score representing your enterprise’s cybersecurity health and how likely your business is to be breached in the next twelve months.
- Expected financial loss by attack vector, which can be used to calculate Return on Security Investments (ROSI).
- A prioritized list of security actions – both at the enterprise and asset level.
Our solution can be implemented and layered over your existing cybersecurity products to give you a quantified view of cyber health, financial exposure, and actions optimized to maximize your business goals.
Want to see how SAFE take the guesswork out of cybersecurity? Request a session with one of our CRQ experts who will help you navigate your journey towards effective, real-time cyber risk management.



