How to Create a Cyber Incident Response Plan with SEC Materiality Reporting
Tips on analyzing and reporting quantitative risk data before and after a breach

In the ever-evolving world of digital landscapes, where cyber threats lurk around every corner and data breaches can send shivers down your spine, one thing reigns supreme: incident response planning. Picture it as the mighty fortress guarding your organization’s cyber kingdom. But for Chief Information Security Officers (CISOs), it’s not just about building any old fortress – it’s about constructing an impenetrable stronghold that dances gracefully within the bounds of regulatory requirements.
Enter cyber risk materiality reporting for the Securities and Exchange Commission (SEC) – the shining beacon guiding our CISOs through the murky waters of incident response planning.
Buckle up as we embark on a thrilling journey, unraveling the mysteries of incident response planning tailor-made for our CISOs, with a spotlight on those oh-so-important materiality reporting obligations to the SEC. Ready? Let’s dive in!
5 Steps to SEC Compliance on Material Cyber Risk
- Identify the organization’s top cyber risks.
- Create a materiality framework to uncover and quantify all the factors that determine a material loss event.
- Automate data collection so you’re always ready toassess material risk.
- Quantify material risks in financial terms.
- Communicate to the board and business proactively on risk identification and remediation efforts – and reactively with speed for incident reporting, particularly if disclosure to regulators is mandated.
First, You Need to Understand Materiality Reporting
Materiality reporting entails the disclosure of cybersecurity incidents deemed significant enough to impact the financial standing or operations of a publicly traded company. The SEC guidelines mandate timely and accurate reporting of such incidents to ensure transparency and protect investors’ interests.
But the SEC leaves it to the companies to set their own definitions of “material.” CISOs must be well-versed in identifying incidents that meet a threshold of materiality and have mechanisms in place to report them effectively.
So, what are some keys to success to ensure that if you are hit with a cyber incident, you will be backed with the proper details and process to remain in compliance?
Build a Robust Incident Response Plan with Materiality Assessment Baked in
Picture your organization’s cybersecurity posture as a fortress, and at the heart of it lies your robust incident response plan. It’s your go-to playbook, packed with predefined processes and superhero roles ready to swoop in and save the day when cyber threats come knocking. But here’s the million-dollar question: how do you know when it’s time to sound the alarm?
Enter materiality assessments – your trusty compass guiding you through the choppy seas of financial reporting, especially when it comes to cozying up to the Securities and Exchange Commission (SEC). Think of them as your secret weapon in separating the trivial from the game-changers when it comes to financial decisions.
These assessments are like the Sherlock Holmes of the financial world, helping companies sift through the noise to pinpoint what really matters. And for the SEC, that’s gold dust. It’s all about maintaining market integrity and giving investors the full picture, no smoke and mirrors here.
But wait, there’s more! Materiality assessments aren’t just about ticking regulatory boxes – they’re your roadmap to prioritizing risk management efforts and keeping the financial ship sailing smoothly. They’re the backbone of sound corporate governance, ensuring your organization stays one step ahead in the ever-changing world of financial markets overseen by the SEC.
The SAFE Materiality Assessment Module on the SAFE One platform is designed to enable security and risk leaders to present defensible, company-specific, quantified cyber risk readings to stakeholders, C-Suite and Board of Directors. It is based on the FAIR Institute’s bottom-up, fully tunable FAIR-MAM™ model.
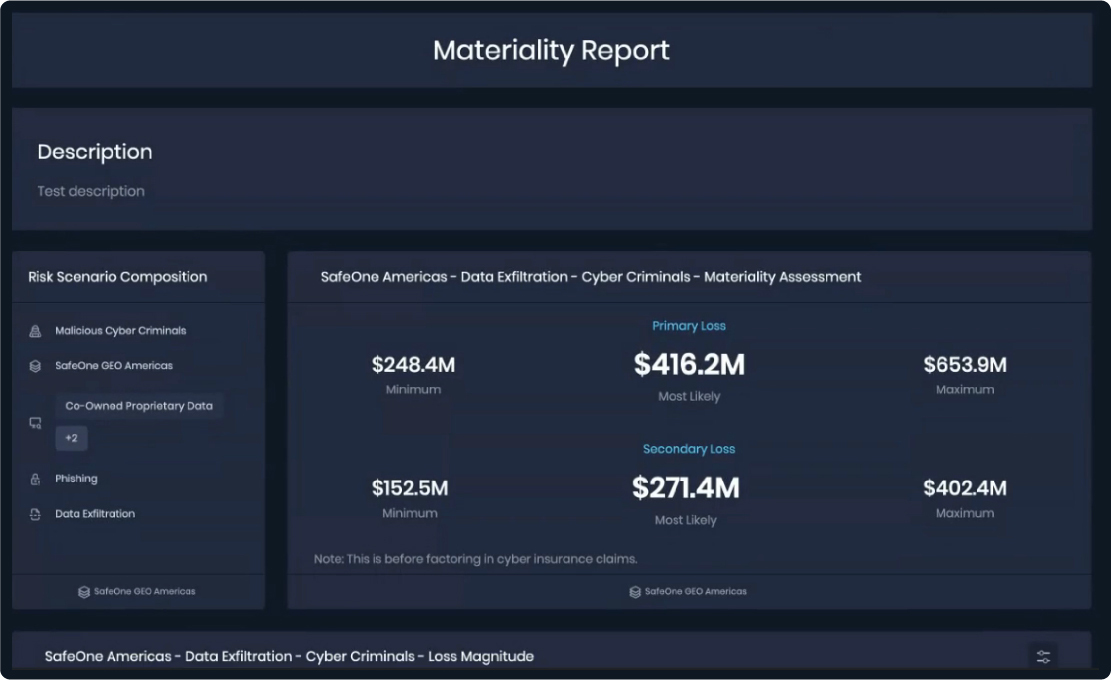
Material risk assessment, SAFE One platform
Don’t Wait for an Incident to Occur
Alright, let’s get proactive: This means regular training sessions and tabletop exercises that are pure functions of your current security control environment and contextualized to your business.
The real game-changer to SEC disclosure is knowing your top risks inside and out through cyber risk quantification. We’re talking about modeling them for the whole organization to see with a material risk reporting framework like FAIR-MAM. It’s like having a crystal ball that shows you exactly where the dragons are lurking in the cyber realm. By quantifying the level of risk you’re facing from those pesky threats that can cause the most damage, you may just be avoiding having to do a disclosure all together.
In addition, with ongoing reporting within your organization on all the factors of cybersecurity risk – likelihood of a cyber event and magnitude of impact — you can also premeasure the material loss of specific incidents before they even occur. You essentially would know which cyber event would most likely be material for your organization and which security controls are helping prevent, or better yet, which security controls are not.
Before the cyber storm hits, your teams are already out there, like cyber-savvy detectives, assessing your controls to ensure they’re firing on all cylinders. It’s all about making sure your defenses are as sharp as a tack and working together like a well-oiled machine.
But here’s the kicker: most security products are like solo artists, each doing their own thing without a care in the world about teamwork. That’s where cyber risk quantification comes in, offering you a blueprint that reveals exactly where you are most vulnerable and what needs your attention pronto. It’s like having a map that shows you the weak spots in your fortress, so you can fortify them before the bad guys even think about knocking. With quantification of cyber risk in financial terms, you are also set to report to business leaders and the board in the terms they best understand.
Conclusion
In conclusion, incident response planning for CISOs must encompass not only technical readiness but also compliance with regulatory requirements, particularly regarding materiality reporting for the SEC.
By building robust incident response plans, collaborating with cross-functional teams, and having a true cyber risk quantification program to help you stay vigilant about emerging threats, CISOs can effectively mitigate the impact of cybersecurity incidents and safeguard their organizations’ financial standing and reputation. However, should an incident occur, you need to be able to know if it is material enough to report. Quantifying the expected loss will be the only way this is possible and will be key to disclosing incidents that are required versus those that are not.
Remember, the goal of incident response planning is not just to react to incidents as they occur but to proactively prepare for them, minimize their impact, and maintain stakeholders’ trust and confidence in the organization’s ability to handle cybersecurity threats. With a strategic approach to incident response planning that is embedded with materiality analysis, CISOs can navigate the complexities of materiality reporting for the SEC with confidence and resilience.
LEARN MORE:
White Paper: CISO’s Playbook For SEC Cyber Risk Compliance
Webinar: From Data to Disclosure: Decoding Cyber Risk Reporting for the SEC and the Board
Product Data Sheet: SAFE Materiality Assessment Module



