How to Bring Infosec and IT Together to Report on Cyber Risk to the Board
Different silos, different priorities, different metrics but you can find common ground
By Gina Hayden
Both the Infosecurity and the IT management teams share a common goal – safe operation of IT assets to best serve the organization’s initiatives – but they often come at that goal from different perspectives. That divide can come to a head when the board demands they put the puzzle pieces together, reconcile their risk assessments into a coherent view, and do it urgently to meet demands of regulators.
Gina Hayden is an Enterprise Account Executive for SAFE
Here’s how to break down, and work through this communication gap.

Cybersecurity vs IT Administration: Why the Different Perspectives on Cyber Risk?
In many organizations, the two teams operate out of separate silos: Infosec reporting up through a CISO to Compliance/Legal while IT answers to the CIO.
On the IT side, leadership tends to focus on the Crown Jewels of the organization with staff responsibilities centered on minimizing risk/downtime. In this situation, risk management is viewed in terms of controls in place to minimize threats to the Crown Jewels.
Contrast that to the Infosec side with a broader focus on business processes – and particularly on the critical processes (manufacturing, billing) that keep the business going – not just the component capabilities.
Differing perspectives drive the IT side to prioritize technical metrics and the cybersecurity side to prioritize whole-of-business metrics – in other words, loss exposure quantified in financial terms.
To the extent that IT Admin quantifies risk, it might be in terms of “maturity” ratings for numbers of controls implemented off a standard list of best practices from NIST, ISO, CISO or other authority. Most likely, IT is still assessing risk in qualitative terms, that is numeric or color-coded rankings based on the staff’s subjective judgements.
Bringing the Two Sides to a Common View of Cyber Risk
Let’s say up front that, when it comes to board reporting, Infosec has it more right than IT but both sides need to be heard.
First, when communicating to the board or stakeholders in the business, the language needs to be quantitative and in two dimensions: Likelihood (percentage chance in a year) and Impact (in dollars) of cyber loss events so decision-makers can get the clearest picture of what’s at stake for various probable risk and mitigation scenarios.
The Likelihood dimension still leaves a critical role for IT Management on controls assessment in communicating up the chain of command. And there’s another reason to win IT’s buy-in: If they don’t understand the risk, they may not be compelled to take action to mitigate, which ultimately frustrates the Information Security team.
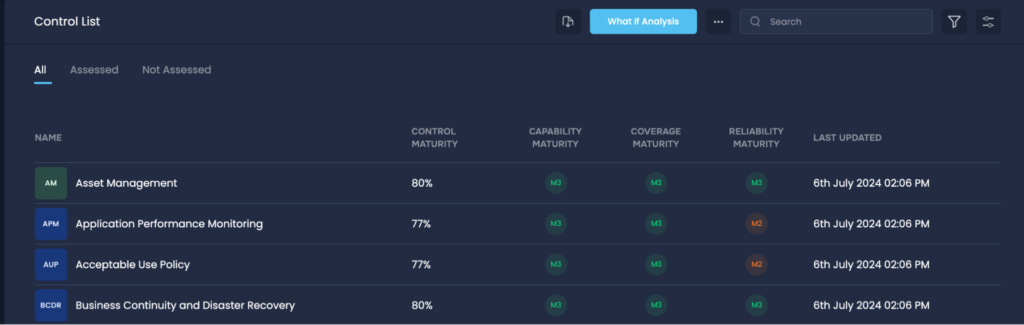
Controls analysis on the SAFE One platform
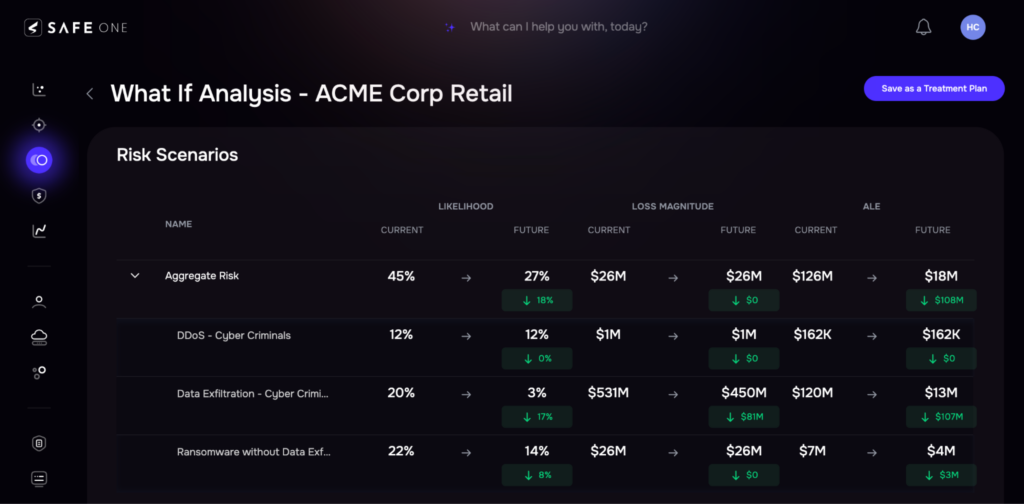
What If analysis
SAFE Can Help
The SAFE One platform for quantitative cyber risk management offers each team a view of risk that fits its needs.
A CIO can track controls effectiveness in detail with continuous monitoring through the FAIR Controls Analytics Model.
At the same, a CISO can also track the changing risk posture of the organization for likelihood and impact expressed in FAIR risk scenarios.
Each can group assets, services and processes and monitor them through customized dashboards. And it’s all done with the defensibility of the open-source FAIR standards for risk analysis.
From there, the platform aggregates reporting based on overall financial impact that the board and senior management want to see – ultimately unifying cyber risk reporting from any perspective.
Learn more in a blog post:
IT and Cybersecurity: The Missing Pieces in Business AlignmentLearn more about the SAFE One Platform


