Salesloft Drift Breach: What Happened, Why It Matters, and How to Reduce Third-Party SaaS Risk
A sophisticated exploitation of a vendor’s app opened the door to a major supply chain attack
SAFE One Threat Center
By SAFE Threat Research Team
In August 2025, attackers used stolen OAuth credentials from Salesloft’s Drift chatbot integrations to access connected customer SaaS environments, most notably Salesforce. At scale, they enumerated objects and exported support Case text to harvest embedded secrets such as API tokens and cloud keys, enabling potential follow-on compromise. Multiple vendors, including Cloudflare, reported exposure. Google Threat Intelligence dates the activity to August 8–18, with token revocations commenced on August 20 and broader guidance issued on August 28.
In this blog post, we cover:
- Incident Timeline of Affected Entities & the Breach
- Impact of the Salesloft Drift Breach
- Technical Analysis: Tracks of the Attackers
- Recommended actions
- High-Level ATT&CK mapping
- Why It Matters: The Third-Party SaaS Risk Lens
- The structural risk of vendors and other third parties
- Why is this type of attack hard to detect
- Third-party risk implications
- How SAFE Helps Reduce SaaS & Third-Party Incident Blast Radius
- Help with the attack
- Operationalize the response with SAFE TPRM/ SAFE One
Incident Timeline of Affected Entities & the Breach
August 8–18, 2025 — Google Threat Intelligence (GTIG) has observed a widespread campaign leveraging compromised Drift OAuth tokens to exfiltrate large volumes of Salesforce data, with the attackers’ objective assessed as credential harvesting from support Case text.
August 9, 2025 — GTIG identifies a small number of Google Workspace accounts configured with Drift Email accessed via stolen tokens. Google revokes tokens and disables that integration. (Google Cloud). Cloudflare also reports the first signs of reconnaissance, where the Threat Actor used “Trufflehog”.
August 12–17, 2025 — Cloudflare reports an attacker compromising internal systems using stolen credentials for reconnaissance to learn more about the internal architecture, thereby facilitating the bulk export of Case text via the Salesforce Bulk API 2.0; the API job is subsequently deleted to reduce traces.
August 20, 2025 — Salesloft and Salesforce revoke active tokens; Drift is removed from the AppExchange pending investigation.
August 23, 2025 onward — Impacted customers receive notifications; Cloudflare initiates full response and rotates discovered secrets.
September 2, 2025 — Salesloft takes Drift Offline temporarily to reduce impact and damage.
Impact of the Breach
Hundreds of organizations using the Drift–Salesforce integration were affected, per Cloudflare’s Cloudforce One and Google Threat Intelligence.
The primary exposure was the text fields of Salesforce “Case” objects, where customers often paste tokens, keys, logs, and configuration details during support. In Cloudflare’s instance, attachments were not accessed. Cloudflare identified and rotated 104 API tokens discovered in case text and notified impacted customers.
Google Threat Intelligence indicates the compromise extended to other Drift integrations. Customers should treat any tokens stored in or connected to Drift (including Drift Email) as compromised and rotate them.
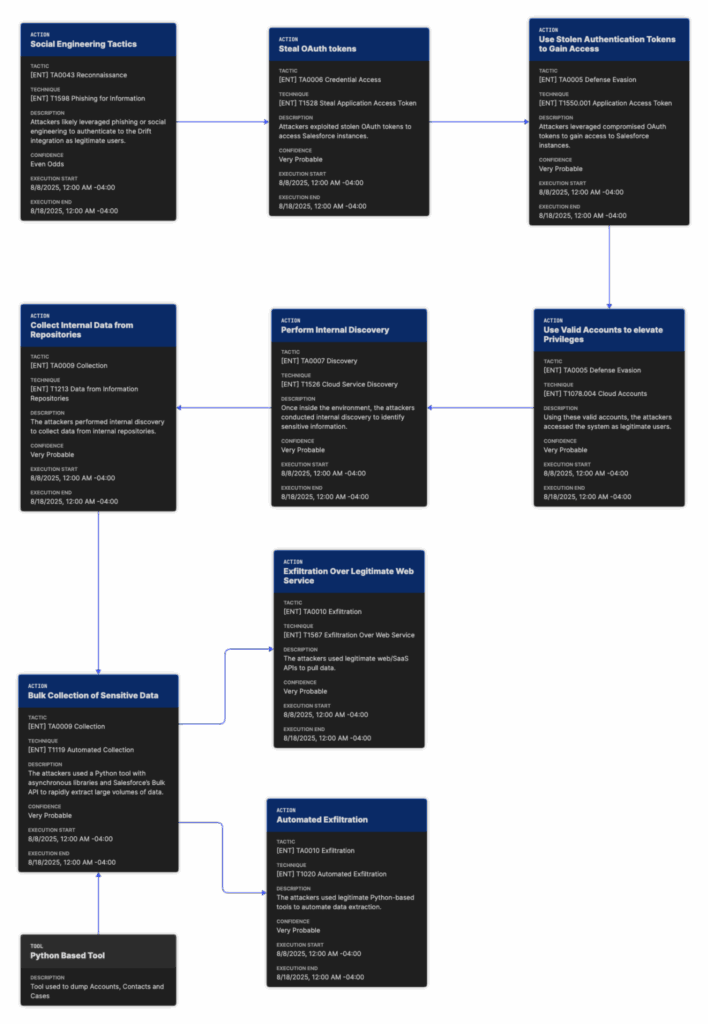
Technical Analysis
- Token acquisition
- Attackers obtained valid OAuth/refresh tokens associated with Drift integrations. (Salesloft has engaged Mandiant; root cause remains under investigation.)
- Abuse of the Salesforce connected app
- Authenticated to Salesforce using the connected app’s permissions.
- Enumerated objects and the Case schema (/sobjects/Case/describe/).
- Counted records to gauge scope.
- Launched Bulk API 2.0 jobs to export Case text at scale, then deleted the jobs to reduce traces.
- Post-exfiltration credential mining
- Parsed exported Case text for secrets (e.g., AWS AKIA keys, passwords, Snowflake tokens) to enable downstream access beyond Salesforce.
- Operational security
- Demonstrated API/logging awareness; while some Bulk API jobs were deleted, relevant logs (e.g., Event Monitoring, connected-app auth/API usage) typically remained available for review.
- Indicators of compromise
- Source IPs: 44[.]215[.]108[.]109 (AWS), 208[.]68[.]36[.]90 (DigitalOcean).
- User-agents: TruffleHog observed during token verification attempts.
Recommended Actions
1. Disconnect or restrict Drift access
Immediately disable or strictly limit all Salesloft/Drift integrations (e.g., Salesforce, email relays, ancillary connectors). Remove unused apps, tighten scopes on any required connections, and document the change.
2. Revoke and rotate credentials
Across every connected platform (Salesforce, Slack, Google Workspace, etc.), revoke existing OAuth grants and rotate all API keys, tokens, and passwords that may have been exposed. Establish and enforce a frequent rotation cadence and shorten token lifetimes going forward.
3. Hunt for exposed secrets
Search Salesforce Case text and other integrated data stores for high-risk patterns (e.g., AKIA, password, secret, snowflakecomputing.com). Use a dedicated secret-scanning tool to accelerate coverage and ensure findings are tracked to closure.
Cloudflare customers: Review Dashboard → Support → My Activities and rotate any credentials ever pasted into support cases.
4. Review and preserve logs
Do not assume evidence is absent. Collect and analyze Salesforce Event Monitoring (e.g., UniqueQuery), Connected App authentication/API usage, and Bulk API job activity even where jobs were later deleted. Preserve logs under legal hold as needed and baseline normal query volumes to aid detection.
High-Level ATT&CK Mapping
Why this Matters: the Third-Party SaaS Risk Lens
This was not a Salesforce flaw. It is the risk you inherit when deeply permissioned, always-on third-party OAuth applications sit between your data and a vendor’s environment. If a vendor-side token is stolen, an attacker can query your tenant from outside your perimeter using legitimate scopes, no malware, no endpoint foothold, blending neatly into ordinary API traffic. Google’s guidance to treat all Drift-stored/connected tokens as compromised underscores how far this SaaS-to-SaaS trust can extend once a single integration is abused. Separately, industry reporting highlights the downstream exposure of secrets beyond Salesforce, and the scramble to invalidate them before use, turning support case text into a high-value target.
The Structural Risk
Always-on access: Refresh tokens keep sessions alive for background jobs; compromise yields durable, headless access.
Broad scopes, shared across tenants: “Convenience” permissions (read_all, export) often exceed least-privilege needs, widening blast radius.
Transitive trust: One vendor’s token can touch hundreds of customer orgs simultaneously, true supply-chain scale.
Why Is It Hard to Detect?
First-party APIs, normal routes: Calls hit standard endpoints (e.g., Bulk API 2.0) and mirror admin workflows.
Legitimate identities: The traffic is “authorized,” so traditional IOC- or malware-centric controls underperform.
Evasive hygiene: Attackers can delete jobs or limit query windows; without robust telemetry (e.g., Event Monitoring), evidence is thin.
Secrets in plain text: Troubleshooting often leads users to paste API tokens, keys, passwords, and logs into case text.
Cascade risk: A single export of case content can unlock downstream systems (cloud providers, data warehouses, CI/CD), expanding impact far beyond the original SaaS.
Third-Party Risk Implications
Govern the OAuth surface, not just the vendor: Inventory connected apps, review scopes, and set IP restrictions/session policies where supported.
Contract for security controls: Token lifetimes, logging/retention, breach notification SLAs, and customer-visible revocation levers should be explicit.
Continuously monitor: Pull Event Monitoring/audit logs, alert on Bulk API jobs, unusual query spikes, and logins from atypical networks.
Operate with revocation in mind: Maintain playbooks for mass token revocation and secret rotation across integrated platforms.
How SAFE TPRM Helps Reduce SaaS & Third-Party Blast Radius
SAFE TPRM automates vendor discovery and intake, tiers third parties by business criticality and access, and builds a digital risk profile using both inside-out and outside-in signals. AI agents extract firmographics, pull artifacts from trust centers, and pre-populate questionnaires, shrinking time-to-insight while enforcing contractual safeguards from day one.
Instead of point-in-time reviews, SAFE continuously watches vendors for breach signals, posture changes, and control drift. You receive real-time alerts on vendor control gaps, including treatment plans and SLA tracking, so revocations, rotations, and remediations occur on schedule, not after an incident has occurred..
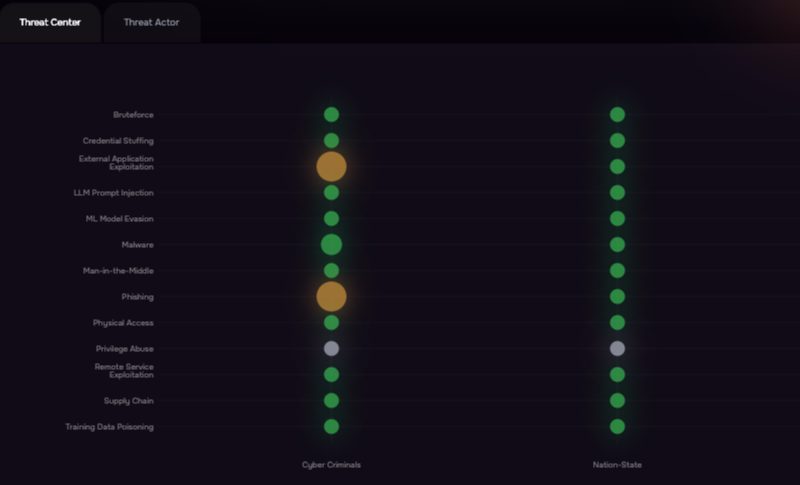
SAFE’s Threat Center is the live hub in SAFE One that unifies threat-actor intelligence with quantitative risk signals. It tracks hundreds of actors and their techniques, and continuously updates Threat Event Frequency (TEF) using live telemetry and 100+ product integrations—so teams see which actors and initial-attack methods are most likely to target their industry today.
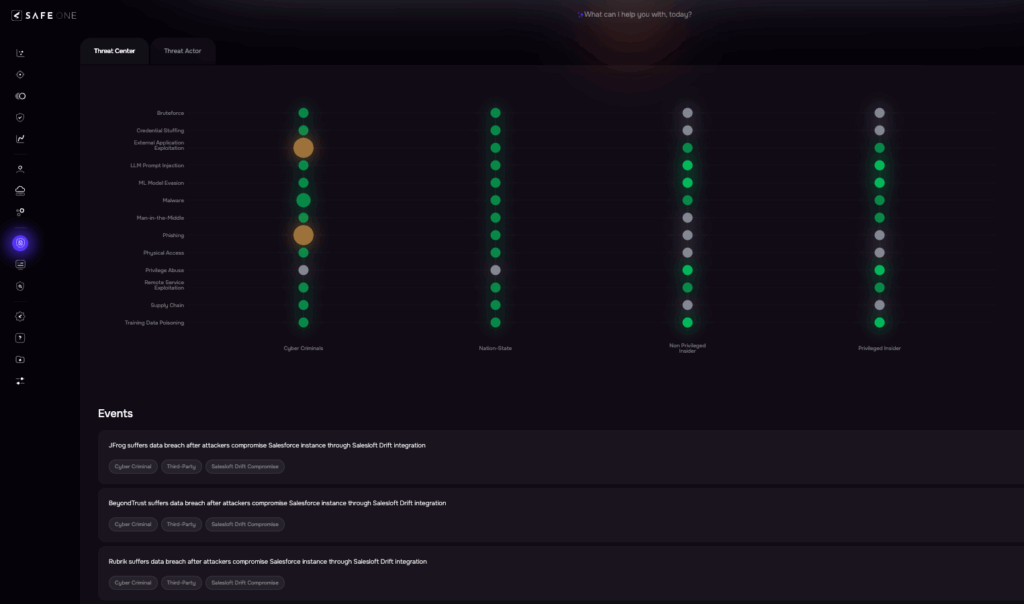
It ties directly into FAIR-based risk modeling and the FAIR-CAM controls library, enabling collaborative scenario building, validation, and treatment planning grounded in current threat behavior. In practice, TEF is refreshed from observed campaigns, breach disclosures, access-broker activity, and TTP shift, driving dynamic scenario scores instead of static assumptions.
From onboarding through offboarding, SAFE provides AI-guided recommendations, automated remediation tracking, and verification of data destruction, helping you maintain least-privilege access, reduce token lifetimes, and de-risk transitive (fourth-party) dependencies as vendors evolve. SAFE can generate compliance outputs with financial-impact context for vendor risks, helping CISOs explain exposure, justify budgets, and prove progress during audits without spreadsheet gymnastics.
SAFE TPRM gives each supplier a single, living profile that’s built for decision-making. The page brings together approval status, tier/criticality, and the business resources the vendor touches, alongside an assessment overview of risk posture, remediation in progress, questionnaire completion, digital-footprint discovery, outside-in findings, and even fourth-party relationships. Reviewers don’t have to jump tools; everything needed to approve, hold, or escalate a vendor sits in one place.
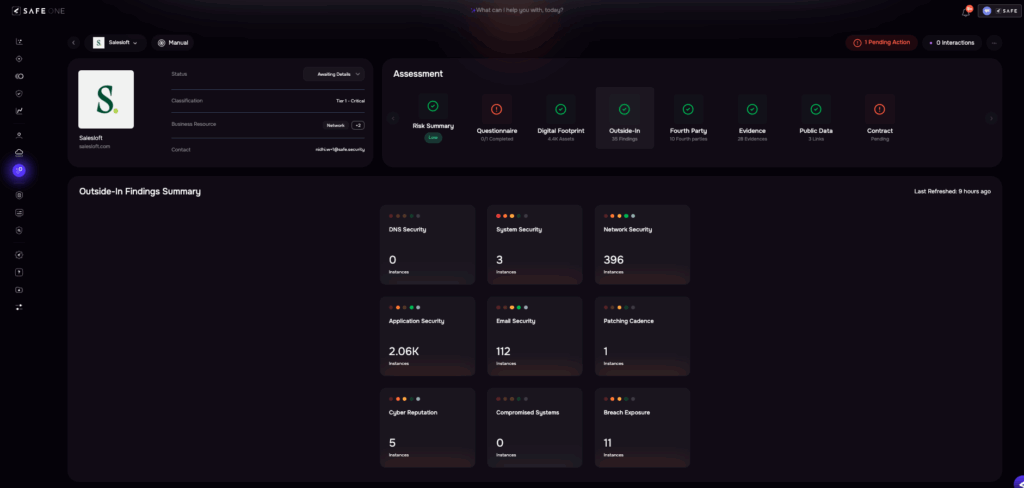
External exposure is translated into work you can actually do. Outside-in signals are organized into operational buckets DNS hygiene, patching cadence, cyber reputation, breach exposure, and system security so you can validate claims from questionnaires against independently observed evidence. Breach exposure summarizes credible disclosures and reporting about prior security events tied to the vendor such as incidents, credential leaks, or abused integrations and links them to likely control gaps and concrete next steps. SAFE continuously discovers internet-facing assets tied to the vendor and reflects changes into the profile, keeping that exposure current without chasing screenshots or PDFs.
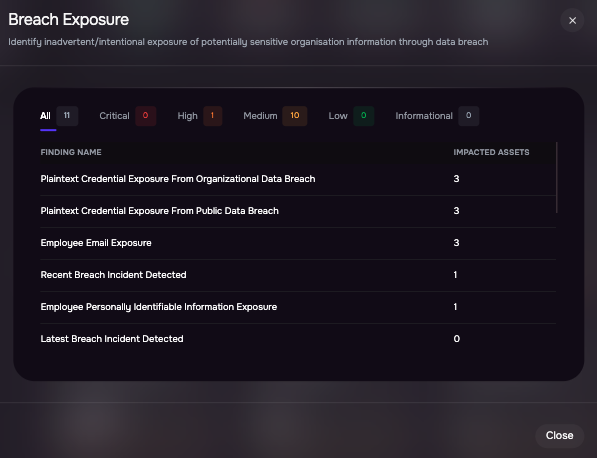
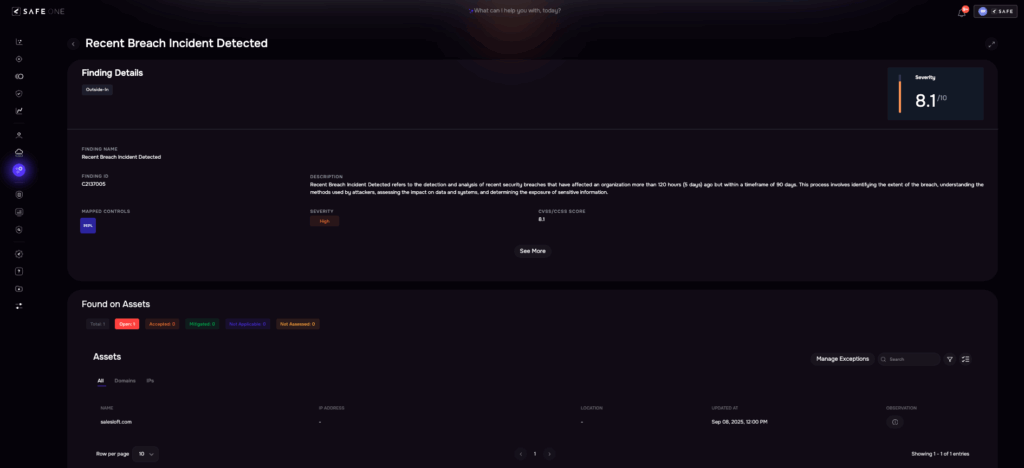
From there, treatment is streamlined. Findings convert into trackable remediation plans, and tiering lets you enforce different baselines for critical suppliers’ scope reviews for connected apps, secret-handling rules in support workflows, and token-rotation expectations for OAuth-heavy SaaS integrations. Monitoring hooks surface behaviors that matter in incidents like Drift–Salesforce high-volume exports, unusual connected-app access, or policy drift, so security, procurement, and legal can coordinate approvals, evidence requests, remediation, and even offboarding within the same workflow.
Operationalize the Response with SAFE TPRM/ SAFE One
| SAFE’s capability | Description | How SAFE counters a Salesloft Drift-style attack |
| Vendor addition, discovery & tiering (TPRM) | Builds a single profile per supplier and assigns criticality based on business impact and access. | Elevates OAuth-heavy connectors (e.g., Drift to Salesforce) to stricter scrutiny before and after onboarding |
| Outside-In & digital footprint monitoring | Continuously discovers a vendor’s internet-facing assets and surfaces exposure changes. | Highlights external weaknesses or drift at third parties that increase the likelihood of OAuth abuse. |
| Threat Center & TEF prioritization | Tracks campaigns/IOCs and quantifies scenario likelihood, which maps to FAIR-CAM controls. | Focuses defenses on “OAuth-based SaaS exfiltration,” flags relevant IOCs, and drives control hardening. |
| Fourth-party visibility | Maps a vendor’s dependencies and applies tier-based controls across the chain. | Exposes transitive risk if a supplier relies on integrations like Drift. |
| Questionnaire to evidence reconciliation | Cross-checks vendor attestations against observed outside-in evidence and internal telemetry. | Surfaces undisclosed over-permissioned apps or weak token practices before they’re exploited. |
| Remediation management | Visibility to findings and help in tracking to Remediation. | Ensures scope tightening, token policies, and monitoring are implemented, not just recommended. |



