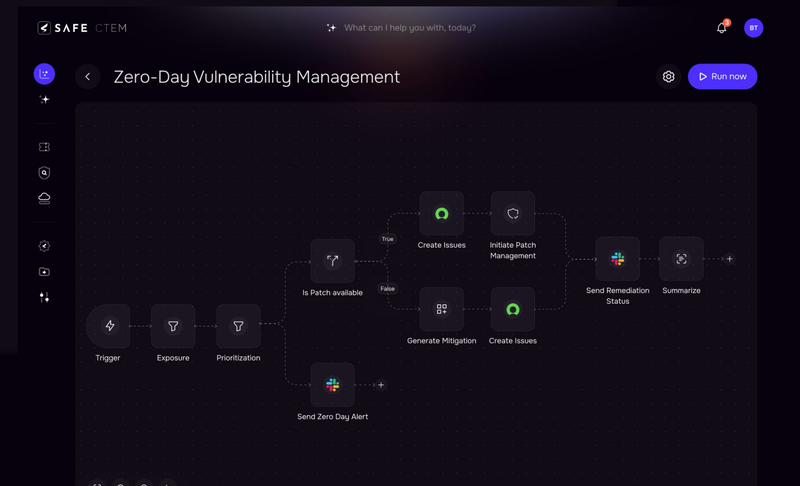
Despite an overall increase in spending on cybersecurity, budgets continue to be tight and obtaining agreement from the Board for investment in new tools or software can present a challenge for many security leaders. The key to getting all Board members on-side is not only to communicate security in terms of ROI, but to anticipate what each Board member cares about. To prepare for this, CISOs need to undertake the following groundwork which will enable them to present their case in a clear, concise manner with metrics that are comprehensible by all.
1. Risk & Budget Prioritization.
Understanding the impact of individual security risks and assigning a monetary value to each one helps to direct investment to where it is needed most. It is likely that most budgets won’t stretch far enough to invest in every activity, so CISOs should be able to determine not only the total risk their business faces, but the difference in value of each risk, applying consistent criteria for reliable measurement.
2. Define the Business Tolerance/Appetite for Risk.
Levels of acceptable cyber risk vary across organizations and industries, location and more depending on how risk averse they may be. When an agreed risk tolerance framework is in place, CISO’s can use it to align and justify individual investment decisions and priorities at Board level.
3. Check Human Resource Allocations.
Taking stock of your manpower including the skills and expertise available will help determine whether any staffing changes are needed or if outsourcing is required to fill gaps. In 2020, 70% of ISSA members believed their organization had been impacted by the global cybersecurity skills shortage, resulting in an inability to learn or use cybersecurity technologies to their full potential, leaving their organization at risk. When looking to invest in new software or tools, ensure you have the human infrastructure in place to support it and prevent misconfiguration.
4. Be Aware of Industry Specific Standards.
Sectors such as finance or healthcare are highly regulated and these regulations can also vary between countries and regions, so it is important to understand the requirements of your industry by geography to ensure any investments made will meet those standards. For example, the NIST Cybersecurity Framework (CSF) is a set of guidelines that were originally developed for government entities and have been adapted for private sector use across the United States. Similarly, organizations in the EU region need to comply with the General Data Protection Regulation (GDPR) standards.
5. Rationalization of Products & Services.
Understanding how current investments are performing is critical – especially when presenting new plans to the Board. It is worthwhile reviewing all tools and capabilities, ascertaining their ROI and determining whether cost savings can be made as a result of duplication or redundancy.
6. The Situation Now Vs Where You Will Be.
Present a real-time picture of how secure the organization currently is, compared to how much more secure it will be by adding specific tools or services.
For many CISO’s, undertaking any of the above can be an arduous task, eating into vital resources and time. It is also not uncommon for some of the information required to be unattainable or unquantifiable, making it increasingly difficult to gain confidence at Board level for new investment proposals.
The solution to the problem is a breach likelihood score, delivering dynamic, real-time and consistent visibility into the efficacy of an organization’s entire technology stack and resources, quantifying risk and identifying areas requiring immediate action.
How does a breach-likelihood score help?
A breach-likelihood score is a simple-to-understand risk metric that spans the whole enterprise, getting all parties from employees to security practitioners and the Board onto the same page when it comes to cybersecurity – effectively answering the question – ‘how secure are we right now?’
When an organization knows how secure they are in real-time, it becomes much easier to determine what needs fixing and how quickly.
The breach-likelihood score offered by SAFE , aggregates signals from existing cybersecurity products, external threat intelligence, policies/regulatory compliance and business context including geography, industry and size, applying our unique machine learning capability and Bayesian based risk prediction engine, to produce a score that accurately determines the likelihood of a breach.
The results are published on a single platform, from which a CISO can view the breach-likelihood score for their organization as a whole or by employee, application, cybersecurity product, policy, IP address, or third-party vendor. This score is also converted into a monetary value, translating IT risk into operational risk that is understandable by all members of the Board.
Through the use of a breach-likelihood score, CISO’s can save time wading through endless data reports and undertaking hours of research. With the ability to measure and manage cybersecurity risk consistently, accurately and in real-time, security leaders can clearly communicate individual cases for future investment, prioritize security improvements and mitigate the risk of a breach.