A three-step action plan to a validated, risk-informed win.

Every so often, you hear me talking about the importance of a risk-based framework—not because I enjoy scaring people, but because, frankly, the rhetoric around Cyber Risk Quantification (CRQ) can be daunting. No CISO is infallible, and the biggest mistake is not having a structured way to understand and prioritize cyber risk.
Cybersecurity leaders don’t get infinite do-overs. But you do get Day One—every 100 days.
The 100-Day Reset is your chance to stop dwelling on yesterday’s gaps and start proving defensible, measurable wins today.
That’s why I love the concept of the 100-day reset. Inspired by the energy of the “Day One” rides you see at places like Peloton, we need to bring that same focus and acknowledgment to our cybersecurity risk programs. You are not defined by the worst decision you made in the last 100 days. Instead, use today to acknowledge where you are and set a clear, actionable path for the next three months.
The secret? The Minimum Effective Dose approach. Don’t try to boil the ocean. Let’s focus on the one to three things that will deliver the most impactful, risk-informed results for your team.
Below are some goals for your first 100 days, categorized by where you are in your cyber risk management journey. Remember, these goals are flexible—you can (and should!) adjust this timeline based on your team’s resources and availability.
What You’ll Learn in This Post
- Why a 100-Day Reset matters in cyber risk management
- How to pick 1–3 high-impact goals that deliver fast, defensible wins
- Beginner, intermediate, and advanced goals you can adopt today
- A 3-step framework to turn CRQ concepts into board-ready and leadership ready results
Beginner Goals: Building Your Foundational Risk Muscle
If you’re just starting to formalize your cyber risk management program, these goals offer immediate, actionable value by pivoting you to a risk-informed perspective using the SAFE platform and the FAIR model.
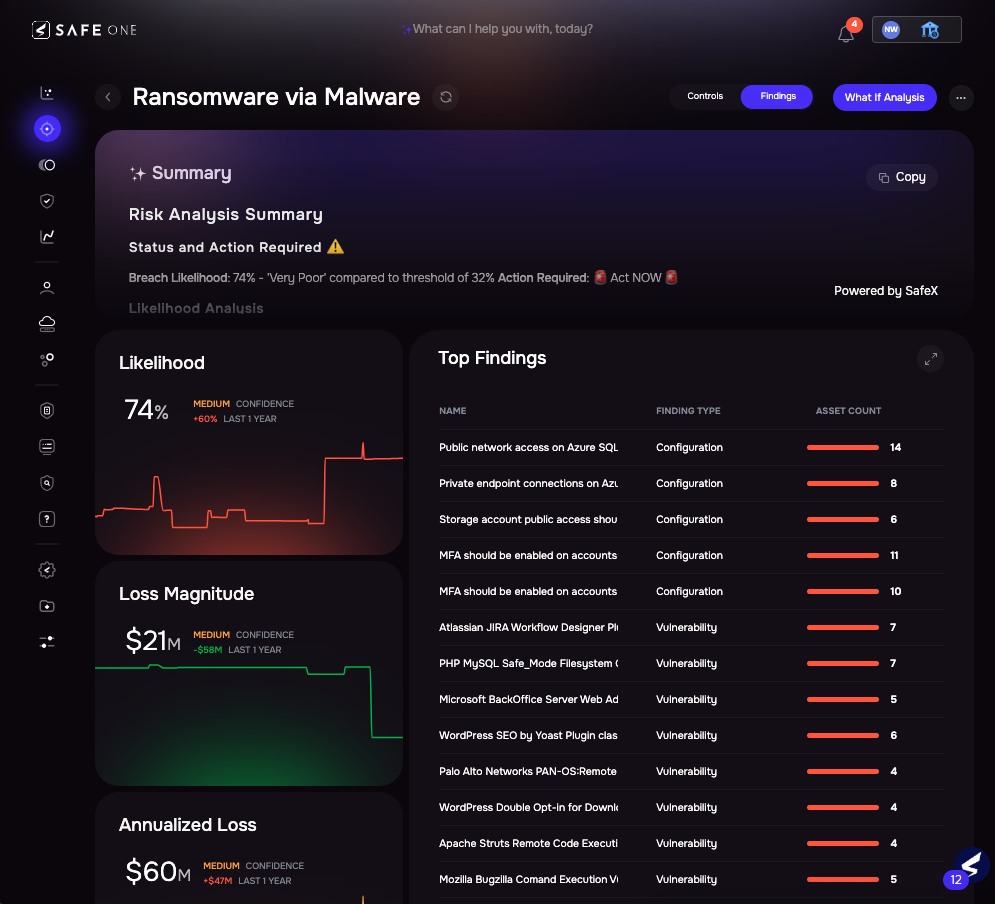
Ransomware analysis, SAFE One platform.
Goal 1: Understand Your Ransomware Risk in Financial Terms
| Explanation | How to Do it Safely (in SAFE) | |
| What It Is | Moving beyond a “High” or “Red” label for ransomware to a concrete understanding of potential financial loss. This allows you to justify controls and budget based on dollar-and-cents risk reduction. | By plugging in integrations for your current control landscape and financial information, SAFE automatically maps everything to the FAIR model. This helps you understand where to prioritize based on the likelihood and impact of a successful ransomware attack. |
| Confronting Failure | IF my security team says the ransomware model is too complex to understand, THEN I will provide a simplified, one-page executive summary focusing only on the top three controls that have the biggest impact on reducing the financial loss exposure. | IF someone questions my data outputs, THEN I will transparently share the data used, including control maturity scores and financial inputs. |
Goal 2: Produce a Risk-Informed Board Report
| Explanation | How to Do it Safely (in SAFE) | |
| What It Is | Transforming your traditional, often subjective, Red/Yellow/Green KPI reports into a methodology-backed report on top risks (e.g., ransomware, data breach). Even if it’s just informing the red, yellow, green with a direct correlation to the likelihood of these scenarios happening not producing actual numbers yet. | Use SAFE to run specific scenarios, inputting control data and likelihood/impact figures. This shifts your reporting from “educated guesses” to a defensible, risk-based methodology, informing whether a risk is truly “High” or “Low.” |
| Confronting Failure | IF the board prefers to stick with the old color-coded report, THEN I will use the SAFE output to transparently show how the old Red topics correlate to the new Financial Risk Exposure to build confidence in the new method. | IF they say my data is wrong, THEN I will ask them for their better data input and proactively offer a re-review or follow-up once the data has been updated. |
Goal 3: Prioritize All Security Findings with a Risk-Based Model
| Explanation | How to Do it Safely (in SAFE) | |
| What It Is | Moving away from a “CVSS score is high, so fix it now” mentality to prioritizing security issues (like vulnerabilities) based on their real-world contribution to your top financial risk scenarios. | Set up integrations in SAFE and define your top risk scenarios (e.g., ransomware, data breach). The platform maps all findings to the FAIR methodology, giving you a clear, risk-based prioritization of what to fix first because it reduces the most financial risk. |
| Confronting Failure | IF my vulnerability management team pushes back on the prioritization, THEN I will transparently show them the underlying risk model and inputs to help them validate why certain findings matter more than others in a financial context. | IF my team gets bogged down in too many findings, THEN I will scope the goal to only prioritize findings related to our single most critical asset group for the first 100 days. |
Goal 4: Risk-Prioritize Third-Party Vendors
| Explanation | How to Do it Safely (in SAFE) | |
| What It Is | Shifting from a generic third-party risk score (or the endless questionnaire cycle) to prioritizing which vendors require the most attention based on the financial impact their compromise could have on your organization. | You’ll monitor third parties in SAFE by using external and internal data (like contract details or services provided). The platform automatically uses a risk-based methodology (FAIR) to prioritize which third parties have the largest risk contribution to your organization, allowing you to focus your team’s limited resources where they matter most. |
| Confronting Failure | IF the procurement team pushes back on risk-based tiering, THEN I will use the financial loss projection to demonstrate to them that a delay in vetting the high-risk vendor is less costly than a breach from a critical, unvetted vendor. | IF a vendor assessment is blocked by an unreturned questionnaire, THEN I will use SAFE’s outside-in monitoring data to generate a preliminary, risk-informed SAFE Score to keep the prioritization process moving forward. |
Intermediate Goals: Integrating Cyber Risk into Security Operations, Compliance and Beyond
You have a basic understanding of CRQ and are ready to embed the risk language into your daily security and threat intelligence processes.
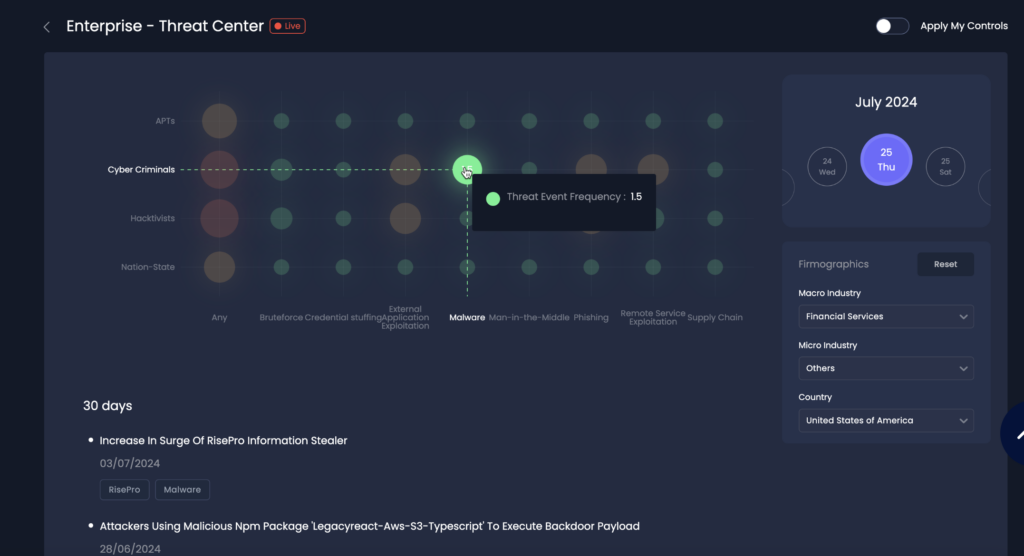
SAFE One Platform Enterprise Threat Center
Goal 1: Model Top Threat Actors to Inform Threat Intel
| Explanation | How to Do it Safely (in SAFE) | |
| What It Is | Shifting your threat intelligence team from reporting on a generic list of threat actors to modeling how the most relevant and active threat actors would successfully attack your specific organization. | In SAFE’s Threat Center. The platform tracks relevant threat actors, models their attack likelihood and impact within your environment, and within each scenario provides a prioritized list of findings and controls that contribute to reducing that specific threat actor’s success. |
| Confronting Failure | IF my threat intel team struggles to speak the language of risk (likelihood and impact), THEN I will dedicate one hour a week to a joint session with the risk team to translate threat indicators into risk factors. | IF the models show a high-risk scenario that my threat team believes is irrelevant, THEN I will use their expertise to update the control evidence inputs for that specific scenario to make the model more accurate. |
Goal 2: Standardize Risk Exceptions Based on Financial Impact
| Explanation | How to Do it Safely (in SAFE) | |
| What It Is | Using data to determine the actual risk exposure from a policy exception (e.g., a lack of MFA on a system) rather than a simple gut feeling. This informs who needs to sign off and whether an exception is tolerable. | Use SAFE to analyze specific control gaps (like MFA or poor password rotation) and understand their financial impact on your top risk scenarios. This allows you to inform sign-off levels and make data-driven decisions on whether to accept the risk or invest in remediation. |
| Confronting Failure | IF a business leader refuses to accept the risk value shown, THEN I will ask them what their maximum acceptable loss exposure is for that system and work backward to see if the exception still fits. | IF the exception process slows down business operations, THEN I will create pre-defined risk tolerance tiers so common, low-impact exceptions can be fast-tracked without full analysis. |
Advanced Goals: Integrating Risk into Business Strategy
You’ve mastered the basics and intermediates and are ready to truly be a partner to the business, leveraging CRQ to inform major financial and strategic decisions.
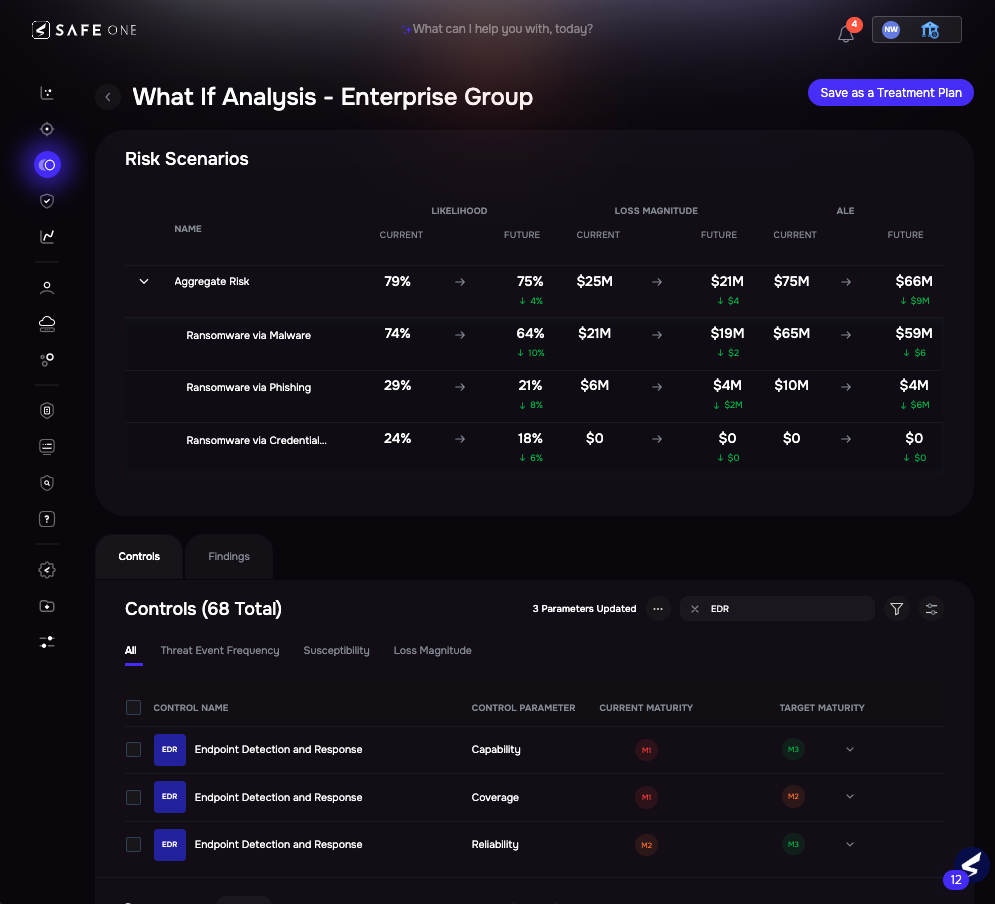
“What If” Risk Analysis by Business Unit, SAFE One Platform
Goal 1: Present Real Financial Risk Data to the Board by Business Unit
| Explanation | How to Do it Safely (in SAFE) | |
| What It Is | Moving beyond a single “Enterprise Risk” number to presenting risk exposure broken down by key organizational structures, such as business units, product lines, or critical asset groups. | Utilize SAFE’s advanced tagging feature to pull in signals from different asset groups and map them to the FAIR methodology. Combining control, financial, and top-risk data, you can confidently state the likelihood and Loss Expectation (in dollars) for each unit. |
| Confronting Failure | IF a specific business unit challenges their risk number, THEN I will partner with their team to ensure the asset values and financial impact figures used in the model are accurate and mutually agreed upon. | IF the board asks for an ROI on a security investment in a specific unit, THEN I will leverage the model to show the risk reduction (in dollars) achieved by implementing the suggested control. |
Goal 2: Quantify Cyber Risk Reduction from Planned Security Projects
| Explanation | How to Do it Safely (in SAFE) | |
| What It Is | Shifting from saying “Project X will make us more secure” to “Project X will reduce our Ransomware Loss Exposure by $2.5 Million.” | SAFE has the capability to model the impact of maturing specific controls or remediating findings. This directly translates your security projects into financial dollars and cents, proving to the risk committee exactly how they are burning down identified risks. |
| Confronting Failure | IF the measured risk reduction is lower than expected, THEN I will QA the data inputs, adjust the scope or explore additional controls to maximize the financial impact before presenting the results. | IF a project fails to deliver the promised risk reduction, THEN I will treat it as a lesson, not a failure, and openly share the model’s new prediction to adjust expectations and future prioritization. |
Goal 3: Continuously Monitor your Annual HIPAA Risk Assessments
| Explanation | How to Do it Safely (in SAFE) | |
| What It Is | Transforming the cumbersome, manual process of an annual regulatory risk assessment (like HIPAA) into an automated, continuous, and financially quantifiable risk program. This is not just a compliance checkbox; it’s a risk-based view of regulatory exposure. | SAFE has the ability to map your control data directly to the required HIPAA Security Rule sections. This automates part of the evidence gathering and scoring, allowing you to use the platform’s financial modeling to report on your actual Risk Exposure (in dollars) related to HIPAA compliance failures. |
| Confronting Failure | IF my compliance team says the output doesn’t match the old spreadsheet, THEN I will show them the underlying technical evidence driving the score and how the platform’s automation saves hundreds of hours of manual compilation around uploading exports of vulnerabilities and other security tool findings for someone to review manually. | IF auditors or internal legal teams question the data source, THEN I will show them the direct integrations and control inputs that feed the model, providing an immutable audit trail. |
Conclusion and Your Next 100-Day Action Plan
I often hear the refrain, “CRQ sounds great, but where do I actually start?” The notes above are not just goals; they are a roadmap for execution. Your first 100 days are not about achieving perfection; they are about establishing a defensible, repeatable process that translates cybersecurity chatter into financial risk language.
Remember: You are not defined by the worst decision you made in the last 100 days. You are defined by the structure you put in place today to make better decisions tomorrow.
This brings me to a critical point: Dr. Gail Matthews’ research at Dominican University found that people who wrote down their goals were 42% more likely to achieve them. You’ve read the roadmap; now you need to ink your commitment.
Next Steps: Taking This Information into Action
Here is your concrete, three-step action plan for the next 100 days to move from concept to quantitative results, regardless of whether you choose a Beginner, Intermediate, or Advanced goal:
1. Write Down and Define Your Core Scenario (Day 1-5)
- Action: Select one to two defined goals from the lists above (e.g., “Risk-Prioritize Third Parties” or “Quantify Project Risk Reduction”). Write this goal down and identify the specific risk scenario it addresses (e.g., Supply Chain Data Breach, Ransomware Loss, or Regulatory Fine).
- Focus: Document this specific focus area and share it with your core risk and business teams. Making this commitment public ensures accountability.
2. Establish Your Core Data Feed and Scope (Day 6-30)
- Action: For your chosen scenario, identify and onboard the two to three most critical data feeds required by the FAIR model (e.g., vulnerability integrations for control maturity, or financial data for Loss Magnitude).
- Focus: Prioritize getting these connections stable and accurate. If you are challenged on data accuracy, if the data is wrong, ask them for their better data input and proactively offer a re-review or follow-up. The transparency of sharing inputs with data owners is non-negotiable.
3. Run the Quantification and Drive a Business Decision (Day 31-100)
- Action: Run your risk scenario using the live data in SAFE. Translate the output into a simple statement of Loss Exposure (a dollar amount) or Risk Reduction (ROI).
- Focus: Use this quantified number to inform one key decision—a budget justification, a board reporting slide, or a policy exception decision. This is your tangible proof point. If this financial output is questioned, remember: if someone questions my data outputs, then I will transparently share the data used—the simple inputs that drove the result, not the model’s complexity.
By applying this three-step process to any goal—from understanding your entry-level ransomware risk to automating advanced HIPAA reporting—you will end the next 100 days with a validated, risk-informed win that you can use to justify the next phase of your risk journey.
Now, which goal are you making your Day One commitment? Write it down.
Resources:
Re-Tuned: Understanding the Risk-Based Scoring of SAFE’s Findings Prioritization
HIPAA: How to Use SAFE to Be Compliant on Cybersecurity Risk Program Requirements


