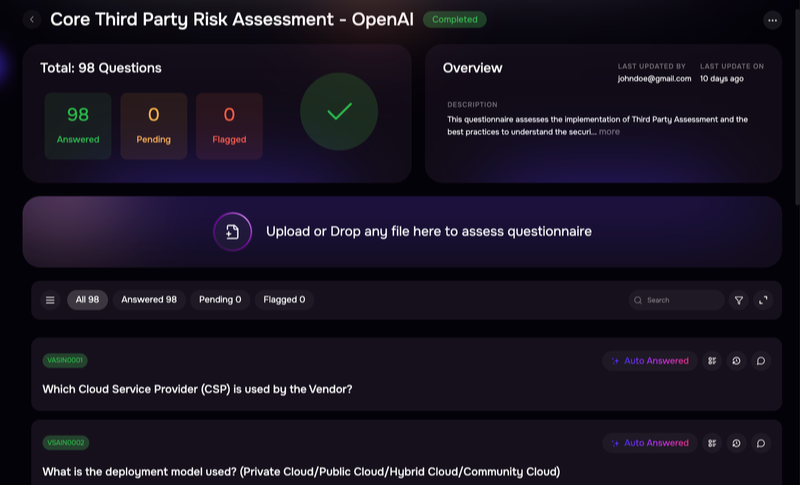
Standard procedure for third party cyber risk management won’t get you there
By Vince Dasta
The outage of CrowdStrike’s endpoint security software in 2024 blue-screened Windows systems around the world. How could business operations at so many technically sophisticated organizations be kneecapped by a small flaw in software delivered by a vendor?

Simple answer: Under standard operating procedure for vendor or Third-Party Risk Management (TPRM), CrowdStrike would not have fit the profile of a high risk or critical vendor.
It’s not that vendor risk is hiding. Standard TPRM is looking for risk in all the wrong places.
What Vendor Risk Management Is Missing
The starting point for most companies with TPRM is an “inherent risk rating.” As a proxy for risk, they tier vendors by metrics like volume of data processed, number of records stored, the operational resilience of payment processors or SaaS tools or other technical markers.
For ongoing third party cyber risk management, they’ve been sold on solutions such as overall risk ratings for the company based on
- scans of outward-facing cybersecurity software or
- answers to questionnaires with 300 one-size-fits-all questions about security practices or
- some combination of the two, packaged by some proprietary algorithm
What’s missing? The business context. We can’t understand risk without talking about the actual effect on our business.
3 Reasons the Business Cares about Risk from Vendors
1. They store or process our data, so we could see risk around legal, privacy or compliance issues.
2. We rely on a vendor for a service (cloud infrastructure, payments processing) and an outage could result in financial loss.
3. They’re tightly connected to us – on our network, running our phones, etc. – so an incident in their environment becomes an incident in our environment.
Get Close to Business Context
Based on the 3 Reasons, we can imagine risk scenarios that clearly define how our business could suffer a loss – and uncover the real drivers of our third-party cyber risk. We could, for instance:
- Scope the risk to our business of a software flaw in one of the patch updates regularly distributed by a trusted vendor to every workstation and server in our environment. We could quantify the likely frequency of the threat events (software updates) and the financial cost in lost revenue of those blue-screened boxes.
- Scope the risk of a payment processor vendor being bricked by ransomware – then factor in risk reduction through redundancy because we have another processor as a backup and could switch over in 15 minutes.
To take this methodical, risk-based approach requires a model and reliable data. The FAIR Framework for Cyber Risk Management is the internationally recognized standard for quantification of cyber risk. With FAIR, risk managers can model the probable frequency and financial impact of cyber loss events.
For greater clarity on risk, they can also leverage other tools in the Framework:
- FAIR-CAM (Controls Analytics Model) for modeling the effect on risk reduction of controls and the inter-relationships among controls.
- FAIR-MAM (Materiality Assessment Model), a comprehensive approach to tracking and reckoning financial impact.
- FAIR-TAM (Third-Party Assessment Model) offering guidance for prioritization among risk scenarios, continuous monitoring of risk factors with telemetry, and application of zero trust controls in the enterprise to help manage third-party risk.
We built the SAFE for Third-Party Cyber Risk Management (TPRM) Solution on the foundation of the FAIR Framework.
But My Ecosystem Has Thousands of Vendors…
It happens at large companies and points out another must-have for effective vendor risk management: a way to identify a targeted set of risk scenarios and controls at scale.
Two innovations from SAFE solve this problem:
- Identification and quantification of probable loss scenarios: On an intake form, answers to 3-10 questions help define the relationship and function of the third party and identify top vendor-related scenarios of concern. SAFE then overlays industry benchmark loss data to those scenarios to identify the probable cost impact of those scenarios.
- Prioritization of most effective controls: With top scenarios identified, SAFE then looks at controls. Using FAIR-TAM, SAFE identifies the most common points of failure in third-party loss events and automatically produces a prioritized list of most effective controls.
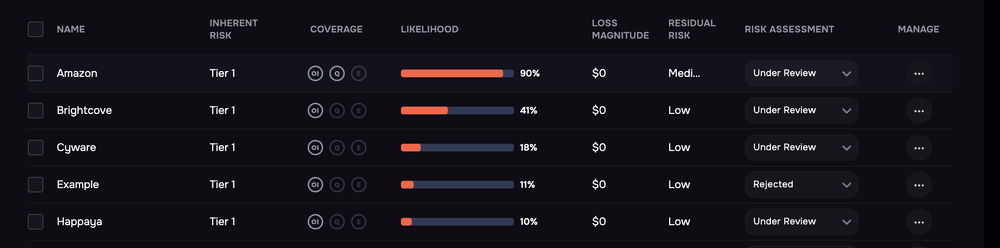
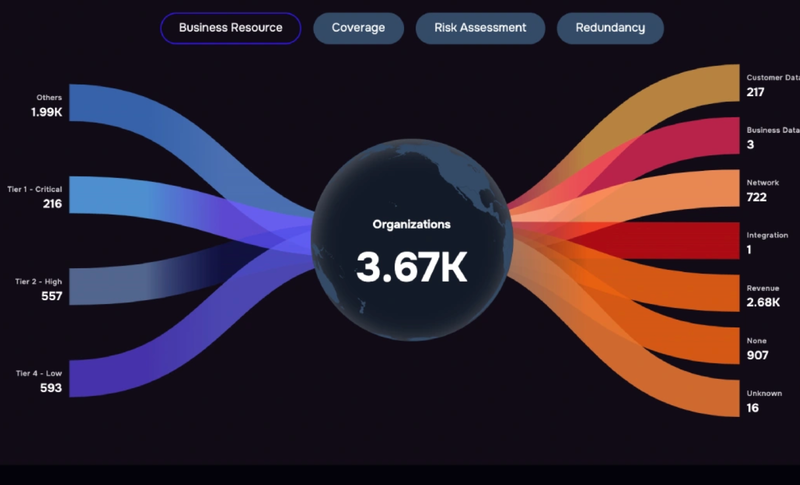
Tiering vendors for risk and controls coverage on the SAFE One platform
Continuous Monitoring plus Automation Catches Risk as It Develops
Highly complex, highly dynamic – A third-party vendor ecosystem morphs far faster than periodic scans or questionnaires can capture – even if they gave you a clear read on risk at a given point in time. Organizations today need risk management tools that provide continuous monitoring and feedback that alerts on new, serious threats and associated risks as they develop and leverage automation to respond quickly.
SAFE accomplishes that by monitoring threat activity and controls effectiveness on a continuous, highly automated basis.
In Conclusion: Uncover Hidden Third-Party Risk in 4 Steps
1. Focus on actual risks to the business, stated in explicit risk scenarios that include measures of likelihood and impact.
2. Tier vendors based on risk and apply mitigation efforts proportionately.
3. Ensure you leverage the most effective controls for TPRM according to an open standard such as FAIR-TAM.
4. Collaborate with supply chain partners on sharing risk and control information, on a common platform, so as to be on the same page on what needs fixing and why.
Discover how SAFE can automate, unify and run your Third-Party Risk Management (TPRM) program at scale. Get your demo today!