Scattered Spider Expands Its Web: Rising Threat Activity Across the U.S.
By SAFE Threat Research Team
Who is Scattered Spider?
Scattered Spider—also tracked under aliases like UNC3944, Muddled Libra, Oktapus, and Octo Tempest—is a financially motivated cybercriminal group that rose to prominence in 2022. Uniquely composed of native English speakers, primarily from the U.S. and U.K., this group deviates from the traditional Eastern European ransomware model. Instead of relying heavily on malware, they specialize in social engineering, identity compromise, and abusing legitimate enterprise tools.
Their operations blur the line between technical intrusion and psychological manipulation, frequently targeting internal help desks, support channels, and identity infrastructure. Over time, they’ve evolved from opportunistic attackers into coordinated adversaries working closely with ransomware affiliates such as ALPHV/BlackCat and Qilin to maximize financial gain through data theft and extortion.
Scattered Spider is known to target the following sectors:
- Retail Organizations
- Hospitality Industry
- Financial Services Firms
- Technology Platforms & SaaS Providers
- Telecommunication Industry
While the group initially focused on the United Kingdom, with high-profile attacks on retailers like Marks & Spencer and Co-op, recent intelligence confirms a deliberate pivot toward U.S.-based targets. Breaches involving MGM Resorts, Caesars Entertainment, and other financial and tech platforms indicate a strategic expansion, with the United States now representing the group’s primary area of operation. Confirmed activity has also been observed in France and Canada, reinforcing their growing global reach and adaptability across regions and industries.
What makes Scattered Spider dangerous?
Scattered Spider isn’t just another ransomware affiliate — it’s one of the most capable and adaptive threat groups targeting enterprise environments today. Their sophistication doesn’t come from advanced malware or zero-days. Instead, their real strength lies in manipulating trust, navigating internal processes, and abusing native tools that most defenders overlook.
Here’s what makes them particularly dangerous:
- Help Desk Exploitation
Scattered Spider excels at social engineering internal support teams. Convincingly impersonating employees or contractors can initiate password resets, register new MFA devices, or escalate privileges, often without triggering technical alarms. Even well-configured MFA can be bypassed if the help desk is tricked into assisting the attacker. - Living-off-the-Land (LotL)
Scattered Spider avoids detection by leveraging legitimate tools, including PowerShell, PsExec, RDP, and remote access clients like AnyDesk. Operating within the expected noise of system administration, they remain stealthy while conducting reconnaissance, lateral movement, and persistence. - Operational Security and Agility
Scattered Spider uses disposable infrastructure (short-lived phishing domains, burner accounts), clears forensic artifacts post-breach, and constantly evolves its playbook based on the defender’s response.
This group understands enterprise security posture and human behavior and exploits the blind spots between them with intent and accuracy.
How AI is amplifying Scattered Spider
While Scattered Spider is primarily known for its hands-on social engineering and identity-based attacks, recent evidence suggests the group is beginning to integrate AI to scale its operations and enhance deception. What was once a manually executed campaign of impersonation and phishing now shows signs of automation, precision, and voice-based manipulation powered by accessible AI tools.
One of the most notable shifts is using AI-driven voice cloning for vishing attacks (MITRE ATT&CK ID# T1566.004). Threat actors can convincingly impersonate IT staff, executives, or vendors with a short audio sample, calling internal support desks to bypass authentication or trigger credential resets. The FBI has warned that such AI-generated voice deepfakes are on the rise and present a serious threat to enterprise identity systems.
Scattered Spider also uses generative AI to craft highly personalized phishing emails (ID# T1566.002), mimicking internal communication styles and referencing real organizational events to increase success rates. These emails are no longer generic but dynamic, brand-specific, and context-aware.
In addition, AI is used to automate reconnaissance tasks, such as scanning company org charts, LinkedIn profiles, breach databases, and ticketing systems to build tailored attack paths at scale. As noted in recent research, AI-assisted recon allows actors to pivot quickly across geographies and industries with minimal human effort.
These developments show that Scattered Spider isn’t just evolving tactically—it’s accelerating. With AI as a force multiplier, its operations are becoming faster, more scalable, and harder to detect.
Notable Incidents
Scattered Spider’s operations are no longer hypothetical — they’ve executed some of the most high-profile and disruptive attacks in recent enterprise history. Each breach highlights a different dimension of their playbook, from help desk compromise to ransomware deployment, and illustrates their ability to scale across industries and geographies.
Marks & Spencer (UK, April 2025)
One of the earliest confirmed victims in the UK retail sector, Marks & Spencer, suffered a breach attributed to Scattered Spider. The attackers compromised customer and employee data, leading to widespread operational disruption. The incident highlighted how identity abuse and social engineering can bring down large-scale consumer-facing platforms without malware.
Co-op (UK, April 2025)
Another major UK retail chain, Co-op, experienced a ransomware attack that disrupted store operations and inventory systems. Investigations revealed that Scattered Spider had gained access through support channel impersonation and passed control to a ransomware affiliate — a classic example of their affiliate-driven model.
Pure Storage (US/Canada, 2024)
In early 2024, enterprise storage provider Pure Storage disclosed a breach stemming from the compromise of a third-party file transfer tool. Scattered Spider reportedly leveraged stolen credentials and phishing infrastructure to access internal systems. While the impact was contained, the incident underscored the group’s interest in tech infrastructure providers.
From the UK to the U.S.: A Strategic Pivot in Targeting
Scattered Spider’s campaign trajectory shows a clear evolution—from a series of UK-centric attacks to a deliberate and sustained focus on U.S. retail organizations. What began with high-profile breaches in British retail has now expanded across the Atlantic, with the group replicating its successful tactics to target major retail brands in the United States.
Multiple intelligence providers, including Google’s Mandiant division, have flagged this shift, warning that U.S. retailers are now firmly in the group’s crosshairs. Recent campaigns show that Scattered Spider replicates previously successful TTPs at scale across new geographies and industries.
Tracking Scattered Spider with Threat Event Frequency (TEF)
To quantify this targeting pattern, SAFE tracks the Industry Benchmark Threat Event Frequency (TEF). Based on historical activity and active campaign telemetry, this dynamic metric estimates the likelihood of a specific threat actor targeting organizations in a given industry and geography.
The current TEF values for Scattered Spider show this pivot clearly:

These TEF values highlight the need for organizations in these sectors to invest in risk monitoring, control validation, and scenario-based risk modeling—all of which are core to SAFE’s proactive defense approach.
How can SAFE spot this spider?
As threat actors like Scattered Spider grow more agile, security teams need more than static defenses. They need continuous visibility into attacker behavior, real-time exposure modeling, and threat actor-centric risk assessment. SAFE is built to deliver exactly that.
SAFE helps organizations move from reactive detection to threat-driven risk prioritization. It uses live intelligence and the context of the organization’s security controls to quantify the risk posed by active adversaries like Scattered Spider.
Factoring Threat Actor Activities for Risk Quantification and Management
Effectively quantifying cyber risk starts with understanding how threat actors operate—the specific tactics and techniques they use to infiltrate systems, escalate access, and impact business operations. SAFE translates these behaviors into actionable insights by mapping each threat actor’s techniques to relevant FAIR-CAM Controls.
This mapping allows organizations to simulate real-world attack paths, identify control gaps, and prioritize remediation efforts based on their actual risk exposure. The result is more accurate risk modeling and a sharper focus on security investments.
ATT&CK techniques associated with Scattered Spider and the relevant FAIR CAM controls available in SAFE:
| ATT&CK Tactic | ATT&CK Technique | Controls in SAFE |
|---|---|---|
| TA0043: Reconnaissance | T1589 – Gather Victim Identity Information |
|
| TA0042: Resource Development | T1583 – Acquire Infrastructure |
|
| TA0001: Initial Access | T1566.002 – Phishing: Spearphishing Link |
|
| T1566.004 – Phishing: Spearphishing Voice |
| |
| T1078 – Valid Accounts |
| |
| TA0002: Execution | T1204 – User Execution |
|
| TA0003: Persistence | T1098 – Account Manipulation |
|
| TA0005: Defense Evasion | T1070.004 – Indicator Removal on Host |
|
| T1556.006 – Modify Authentication Process: Multi-Factor Authentication |
| |
| TA0006: Credential Access | T1003.001 – OS Credential Dumping |
|
| T1555.003 – Credentials from Password Stores: Credentials from Web |
| |
| T1552 – Unsecured Credentials |
| |
| TA0007: Discovery | T1083 – File and Directory Discovery |
|
| T1046 – Network Service Discovery |
| |
| TA0008: Lateral Movement | T1021 – Remote Services |
|
| T1570 – Lateral Tool Transfer |
| |
| TA0009: Collection | T1530 – Data from Cloud Storage |
|
| TA0011: Command and Control | T1219 – Remote Access Software |
|
| TA0010: Exfiltration | T1567.002 – Exfiltration to Cloud Storage |
|
| TA0040: Impact | T1486 – Data Encrypted for Impact |
|
Monitoring Threat Actors in SAFE
SAFE’s Threat Center contains live profiles for over 150 tracked threat actors, including Scattered Spider. Our Threat Research team curates and continuously updates these profiles, aggregating intelligence from open-source feeds, commercial providers, breach disclosures, MITRE ATT&CK updates, and underground forums.
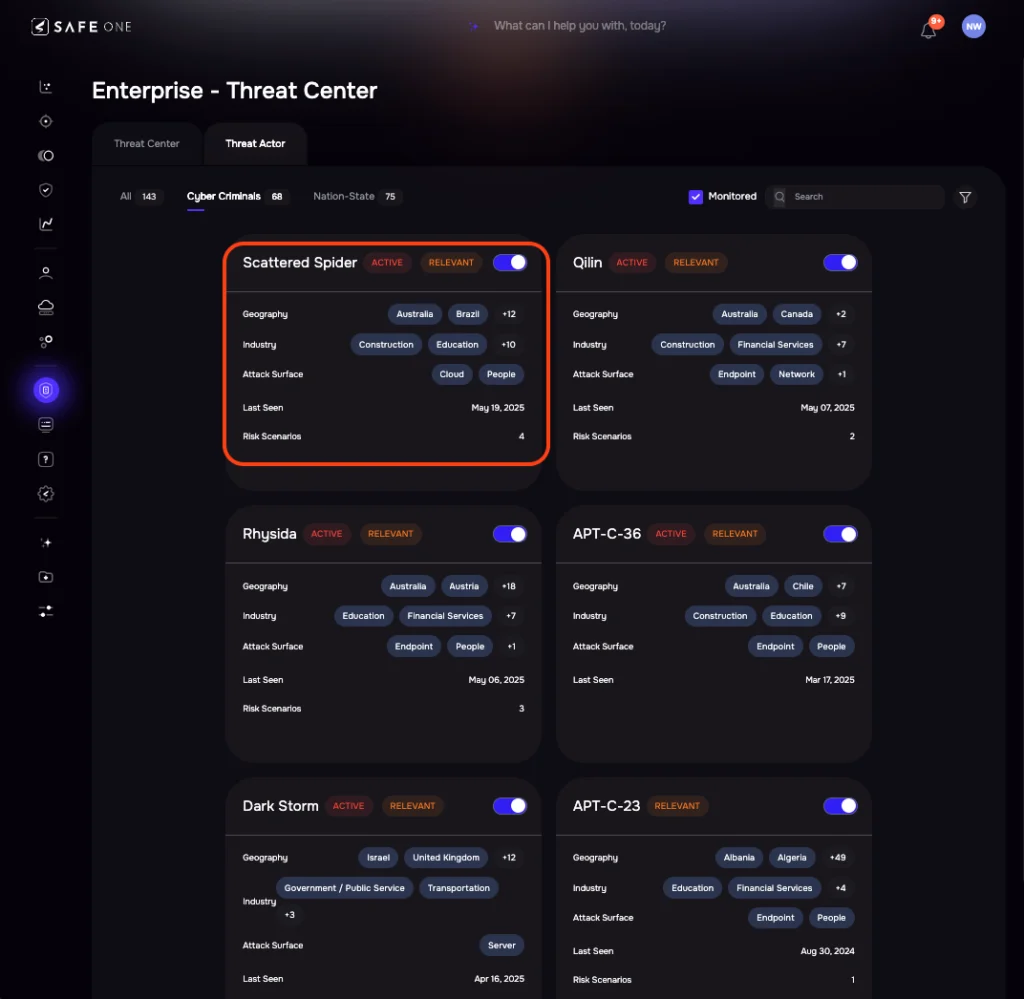
You can begin monitoring Scattered Spider in real-time with a single toggle. The platform correlates attacker behavior with your organization’s control posture, asset exposure, and identity configurations. Once monitoring is enabled, users gain immediate access to dynamic risk scenarios—from phishing-led data exfiltration to credential-stuffing-driven ransomware deployments—all designed to reflect how this threat actor would realistically compromise your systems.

With SAFE, Scattered Spider is no longer a distant, headline-level threat. It’s a quantifiable, model-ready adversary—mapped to your exact weaknesses and prioritized through real-world risk scenarios.
Conclusion
Scattered Spider exemplifies the modern cyber threat: agile, identity-focused, and capable of bypassing even mature security programs through a mix of human manipulation and control evasion. Their shift from UK retailers to U.S. enterprises shows how quickly an adversary can evolve once tactics prove successful.
SAFE helps organizations stay ahead of attackers like Scattered Spider by translating threat intelligence into actionable, control-mapped risk. With real-time monitoring, scenario-based modeling, and exposure quantification, SAFE transforms headline threats into operational insight—so defenders can take targeted, proactive action.
Don’t get caught in the Spider’s web!
Ask your team: Are we safe enough?
Or better: Let SAFE tell you.


