Learn the capabilities that separate effective platforms from compliance theater

By Jeff Copeland
Third-party vendors represent one of the largest and least visible components of enterprise cyber risk. A single compromised supplier can expose customer data, halt operations, or trigger regulatory penalties—yet most organizations still manage vendor risk through annual questionnaires and static spreadsheets that fail to capture real-time threats.
The gap between traditional vendor management and actual risk exposure has become impossible to ignore as regulators demand continuous oversight, breach statistics increasingly implicate third parties, and supply chain attacks dominate headlines. This guide examines what modern TPRM solutions actually do, which capabilities separate effective platforms from compliance theater, and how to build a vendor risk program that scales without proportional headcount increases.
What Are Third Party Risk Management Solutions?
Third party risk management (TPRM) solutions are software platforms that help organizations identify, assess, monitor, and mitigate risks across their vendor ecosystem throughout the entire relationship lifecycle—from onboarding through continuous monitoring to offboarding. The platforms automate repetitive tasks like vendor intake and risk questionnaires, provide centralized repositories for all third-party information, and generate risk scores based on security posture, compliance status, and external threat intelligence. Modern TPRM tools integrate with existing security infrastructure to create a unified view of risk exposure, moving organizations beyond manual spreadsheets and annual assessments to continuous, data-driven vendor risk management.
Think of TPRM solutions as the difference between checking your bank account once a year versus having real-time alerts on your phone. Traditional vendor management relied on annual questionnaires—a vendor could pass a security review in January and suffer a major breach in March, yet you wouldn’t know until next year’s assessment cycle. TPRM platforms monitor vendor risk continuously, alerting you the moment something changes.
The fundamental distinction between TPRM solutions and general vendor management software comes down to focus. TPRM platforms prioritize cybersecurity risk, regulatory compliance, and financial impact quantification. Traditional vendor management systems emphasize procurement workflows and contract administration. A vendor might excel operationally yet pose significant security risks that only specialized TPRM tools can detect and measure.
Why Effective TPRM Matters For Today’s Enterprise
The average enterprise now works with hundreds or thousands of third-party vendors, suppliers, and service providers. Each relationship represents a potential entry point for cyber threats or compliance failures. Research consistently shows that over 60% of data breaches involve a third-party vendor, yet many organizations still rely on annual questionnaires and static risk ratings that fail to capture real-time changes in vendor risks.
Regulatory pressure has intensified dramatically. The SEC now requires public companies to disclose material cybersecurity incidents within four business days. Regulators like NYDFS mandate comprehensive third-party risk management programs with specific documentation and oversight requirements. Organizations without robust TPRM capabilities face regulatory fines potentially reaching millions of dollars, plus reputational damage that can persist long after an incident.
The financial impact extends beyond direct breach costs. When a critical vendor experiences an outage or security incident, the ripple effects can halt operations, delay revenue recognition, and force expensive emergency remediation. A mature TPRM program transforms reactive firefighting into proactive risk mitigation, allowing security teams to identify and address vulnerabilities before they materialize into business-impacting events.
| Business Impact | Without TPRM Solutions | With TPRM Solutions |
| Regulatory Risk | Fines, audits, non-compliance penalties | Streamlined compliance, audit-ready |
| Operational Risk | Service disruptions, supply chain delays | Proactive risk mitigation, resilience |
| Reputational Risk | Loss of trust, negative publicity | Enhanced brand reputation, trust |
| Financial Risk | Unplanned costs, revenue loss | Cost savings, risk-based allocation |
Core Features To Look For In Third Party Risk Management Tools
Real-Time Risk Scoring
Effective TPRM platforms generate dynamic risk scores that update continuously as new information becomes available rather than remaining static between annual reviews. The scores aggregate multiple data sources—security ratings, compliance certifications, financial health indicators, breach history, and geopolitical factors—into a single, actionable metric that helps prioritize which vendors require immediate attention.
The best scoring systems account for both inherent risk (what could happen based on the vendor’s access and criticality) and residual risk (what remains after considering the vendor’s security controls and your organization’s mitigating factors). This dual perspective directs resources toward the highest-impact risk reduction opportunities rather than spreading effort evenly across all vendors regardless of actual threat level.
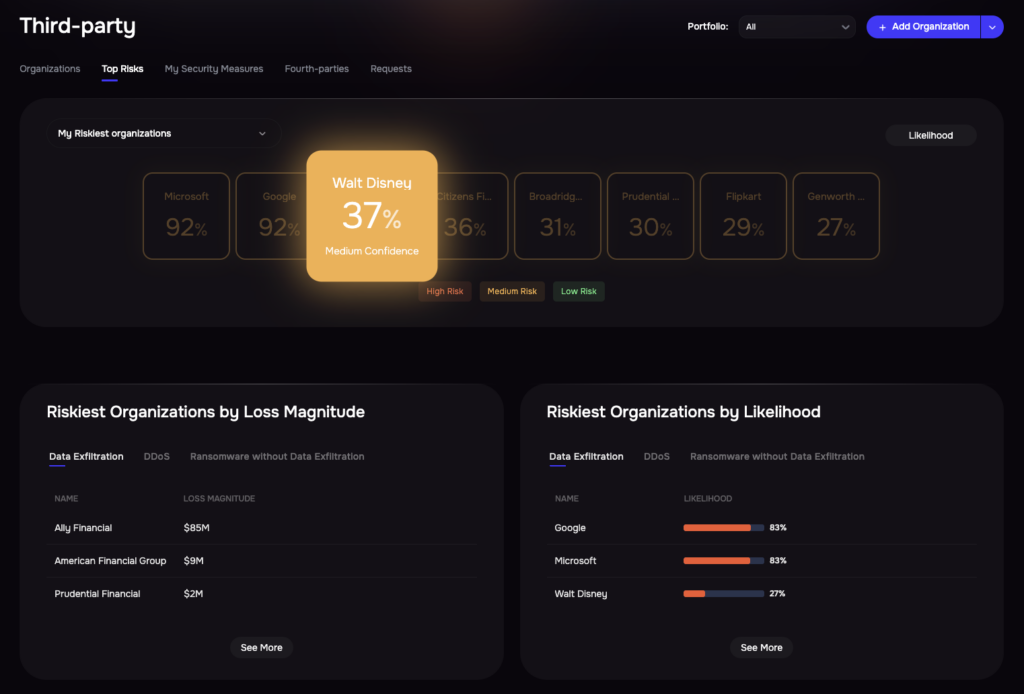
Ranking vendors by risk, SAFE TPRM platform
Automated Risk Assessment
Automated vendor risk assessment transforms this process by digitizing intake workflows, pre-populating responses based on previous assessments or shared industry data, and automatically validating evidence against stated claims.
Manual vendor assessments consume enormous time. Security teams often spend weeks reviewing questionnaire responses, validating documentation, and following up on incomplete submissions. Automation transforms this process by digitizing intake workflows, pre-populating responses based on previous assessments or shared industry data, and automatically validating evidence against stated claims.
Advanced platforms use natural language processing to review vendor documentation, flagging inconsistencies or concerning language that human reviewers might miss. This technology can reduce assessment timelines from weeks to days while simultaneously improving accuracy and consistency across the vendor portfolio.
Regulatory Compliance Alignment
Organizations operating across multiple jurisdictions face a complex web of overlapping regulatory requirements—GDPR in Europe, HIPAA for healthcare data, PCI DSS for payment processing, and dozens of industry-specific frameworks. Leading TPRM solutions map vendor controls to various standards, allowing a single assessment to satisfy multiple compliance obligations simultaneously.
The platform generates audit-ready reports that demonstrate due diligence to regulators, complete with evidence trails showing when assessments occurred, what findings emerged, and how remediation was tracked to completion. This documentation proves invaluable during regulatory examinations or in defending against claims of negligent vendor oversight.
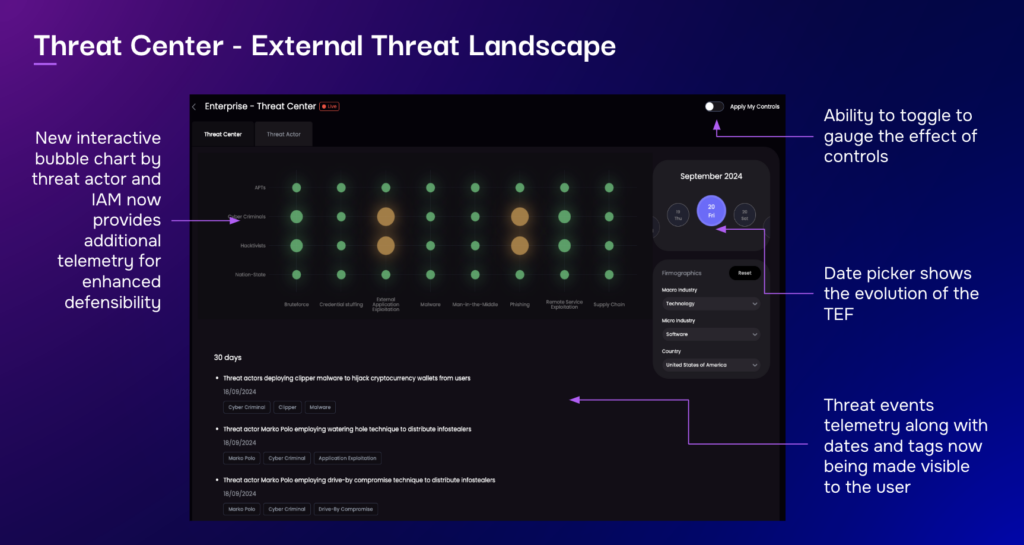
SAFE Threat Center
Threat Intelligence Integrations
Static vendor assessments provide a snapshot in time, but the threat landscape evolves continuously. Integration with external threat intelligence feeds enables TPRM platforms to alert organizations immediately when a vendor experiences a data breach, becomes the target of ransomware, or shows signs of financial distress that could impact service delivery. The difference between learning about a vendor breach from a news report versus receiving an automated alert within hours can mean the difference between controlled response and crisis management.
Integrations also surface newly disclosed vulnerabilities affecting software or services your vendors use, allowing proactive outreach before exploitation occurs. You can contact the vendor about a critical vulnerability before attackers even know it exists.
Scalable Vendor Onboarding
As organizations grow, the vendor population expands exponentially—new business units bring their own supplier relationships, acquisitions add entire vendor ecosystems, and digital transformation initiatives require dozens of new technology partners. TPRM platforms handle this scale through standardized workflows that route vendors to appropriate assessment tiers based on risk classification.
- Low-risk vendors: Brief self-assessment
- Medium-risk vendors: Detailed questionnaires with evidence validation
- High-risk vendors: Comprehensive reviews including possible on-site audits
This tiered approach balances thoroughness with efficiency, ensuring critical vendors receive appropriate scrutiny without creating bottlenecks for lower-risk relationships.
Leveraging AI For Automated Third-Party Risk Assessment
Artificial intelligence is fundamentally changing how organizations approach vendor risk assessment by handling tasks that previously required extensive manual effort. AI-powered contract analysis can review vendor agreements in minutes, automatically identifying problematic clauses around liability limitations, data handling requirements, or security obligations that might create risk exposure.
AI agents trained on historical incident data can predict which vendors face elevated risk based on patterns invisible to human analysts. Combinations of factors like industry sector, company size, technology stack, and recent personnel changes correlate with future security events. The predictive capabilities enable proactive intervention before problems materialize.
Natural language processing analyzes vendor questionnaire responses for consistency, completeness, and potential red flags, automatically escalating concerning answers for human review. This technology also monitors news feeds, social media, and dark web forums for mentions of your vendors, providing early warning of emerging issues that might not appear in official communications.
The most sophisticated AI applications function as virtual analysts, autonomously performing routine risk assessments, generating reports, and even initiating remediation workflows when predefined thresholds are exceeded.
Request a demo to see how AI agents can transform your TPRM program from a resource-intensive compliance exercise into an automated, strategic capability.
How To Evaluate The Best Third Party Risk Management Software
1. Identify Key Requirements
Start by documenting your organization’s specific needs based on industry regulations, vendor population size and complexity, existing security tool ecosystem, and team capacity. A financial services firm with thousands of vendors and strict regulatory oversight will prioritize different capabilities than a mid-sized manufacturer with a smaller, more stable supplier base.
2. Check AI And Automation Capabilities
Dig deeper than marketing claims about “AI-powered” features by requesting specific demonstrations of how automation functions in practice. Ask vendors to show how their platform handles questionnaire distribution, evidence validation, and remediation tracking without manual intervention. Inquire about the underlying AI models—are they generic natural language processors or purpose-built for risk assessment?
3. Assess Integration Options
Evaluate how the TPRM platform connects with your existing technology stack, including GRC systems, procurement tools, ITSM platforms like ServiceNow or Jira, and security tools such as vulnerability scanners and SIEM solutions. Poor integration creates data silos that undermine the unified risk visibility TPRM platforms promise to deliver.
4. Review Reporting And Analytics
Examine sample reports to confirm they communicate risk in business terms that executives and board members can understand, not just technical security metrics. The platform needs to support both detailed operational dashboards for day-to-day risk management and executive summaries that quantify risk in financial terms or business impact.
5. Validate Scalability And Support
Confirm the platform can accommodate your organization’s growth trajectory by asking about maximum vendor counts, user licensing models, and performance benchmarks at scale. Equally important is understanding the vendor’s customer success model—implementation support, training resources, and ongoing assistance can significantly impact time-to-value and long-term program effectiveness.
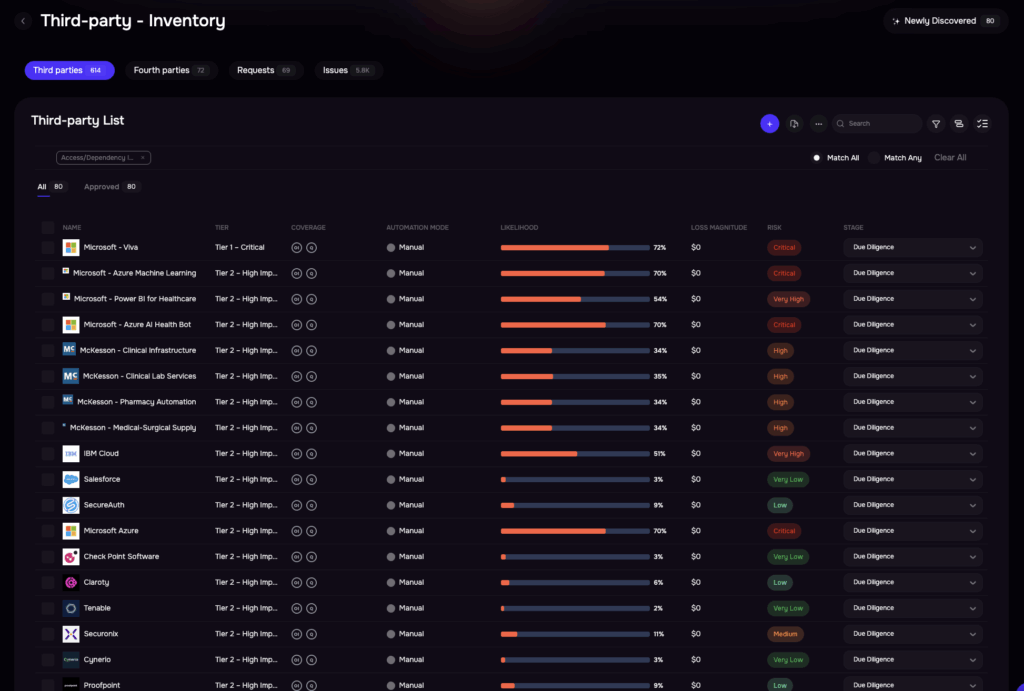
Inventorying third parties, SAFE TPRM platform
Proven Steps to Implement A Scalable TPRM Program
1. Map Your Vendor Ecosystem
Begin by creating a comprehensive inventory of all third-party relationships, including shadow IT vendors that business units engage without formal IT or security review. This mapping exercise often reveals surprising findings—organizations typically discover 30-40% more vendors than they initially believed they had, including fourth-party relationships where your vendors rely on their own critical suppliers.
2. Categorize Vendors By Risk Level
Establish a risk-based tiering system that classifies vendors according to factors like data access, system criticality, regulatory scope, and potential business impact. This classification determines assessment depth and monitoring frequency, ensuring high-risk vendors receive appropriate scrutiny while avoiding unnecessary burden on low-risk relationships.
3. Automate Assessments And Workflows
Configure your TPRM platform to handle routine tasks automatically—sending assessment requests, tracking completion status, escalating overdue responses, and routing completed assessments to appropriate reviewers. Automation frees your team to focus on high-value activities like analyzing complex risks, engaging with critical vendors on remediation, and improving program effectiveness.
4. Establish Continuous Monitoring
Move beyond annual or periodic assessments by implementing continuous monitoring that tracks key risk indicators in real-time. This might include security ratings from external providers, breach notifications, financial health metrics, compliance certification status, and threat intelligence alerts specific to your vendor population.
5. Use ROI Metrics And KPIs
Track program effectiveness through metrics that demonstrate business value—assessment completion rates, time-to-onboard new vendors, percentage of vendors with current risk assessments, number of critical findings remediated, and ultimately, reduction in vendor-related incidents. The metrics prove program value to leadership and justify continued investment in TPRM capabilities following vendor risk management best practices. The metrics prove program value to leadership and justify continued investment in TPRM capabilities.
Real-Time Risk Visibility And Continuous Monitoring
Traditional vendor risk management relied on point-in-time assessments that quickly became outdated as vendor environments evolved. A vendor passing a comprehensive security review in January might experience a significant data breach in March, yet organizations often wouldn’t learn about this changed risk profile until the next scheduled assessment cycle.
Continuous monitoring solves this problem by tracking vendor risk indicators in real-time through automated data collection from multiple sources. Security rating services provide ongoing assessments of vendor external security posture, financial monitoring services alert to signs of distress that could impact service delivery, and threat intelligence feeds surface emerging risks affecting specific vendors or their technology stack.
Modern TPRM platforms aggregate diverse data streams into unified dashboards that provide instant visibility into vendor risk across the entire portfolio. Automated alerts notify risk teams when significant changes occur—a vendor’s security rating drops below acceptable thresholds, a data breach affects a critical supplier, or compliance certifications lapse—enabling immediate investigation and response rather than discovering problems weeks or months later during scheduled reviews.
Future Trends Shaping TPRM
The next generation of TPRM solutions will leverage increasingly sophisticated AI to automate not just assessment but also remediation orchestration, automatically generating and tracking corrective action plans when vendor risks exceed acceptable levels. The systems will function more like autonomous risk management agents than passive assessment tools, continuously working to reduce exposure across the vendor ecosystem.
Fourth-party and nth-party risk visibility will improve dramatically as platforms develop capabilities to map extended supply chains and assess risks that cascade through multiple vendor relationships. A vendor might maintain excellent security practices, but if they depend on a critical supplier with significant vulnerabilities, that risk flows through to your organization.
Industry collaboration will accelerate through shared assessment frameworks and vendor trust exchanges where commonly used vendors complete standardized assessments once rather than responding to similar questionnaires from hundreds of customers. This efficiency gain benefits both assessors and vendors while maintaining or improving assessment quality through standardization. Regulatory technology will become more sophisticated, with TPRM platforms automatically adapting to new regulatory requirements and updating assessment criteria as frameworks evolve.
Accelerate Vendor Risk Reduction With A Unified Platform
The most effective approach to third-party risk management integrates vendor assessment with broader cyber risk quantification and continuous threat exposure management in a single platform. This unified view enables organizations to understand how vendor risks interact with internal vulnerabilities, prioritize remediation based on actual business impact measured in financial terms, and demonstrate risk reduction to executives and boards in language they understand.
Organizations using integrated platforms can quantify vendor risk in dollars rather than abstract risk scores, showing leadership exactly how much potential loss exposure each vendor relationship creates and what investment in risk reduction delivers measurable ROI. This financial translation transforms TPRM from a compliance checkbox into a strategic capability that informs business decisions about vendor selection, contract terms, and risk acceptance. Ready to see how autonomous TPRM powered by AI agents can transform your vendor risk program?
Request a demo to experience the difference between traditional vendor management and truly intelligent, automated third-party risk management.
FAQs About Third Party Risk Management Solutions
How do third party risk management solutions differ from GRC platforms?
TPRM solutions focus specifically on external vendor risks with specialized features for vendor assessment, continuous monitoring, and supply chain visibility, while GRC platforms typically address broader internal governance, risk, and compliance needs across the entire organization. Many organizations use both, with TPRM platforms feeding vendor risk data into the broader GRC system for enterprise-wide risk reporting.
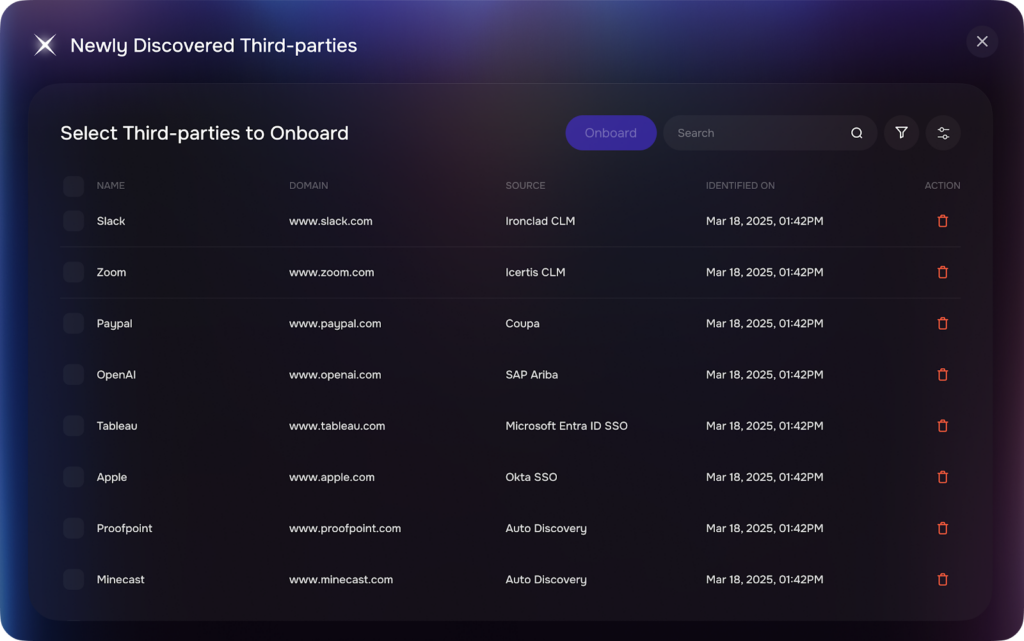
Third-party discovery and onboarding with SAFE
What ROI can organizations expect from implementing TPRM software?
Organizations typically reduce vendor assessment time by 60-70% through automation, decrease vendor-related security incidents by identifying and remediating risks proactively, and improve compliance outcomes by maintaining current, audit-ready documentation. The financial return comes primarily from avoided incident costs, reduced manual labor, and more efficient vendor onboarding that accelerates time-to-value for new vendor relationships.
How long does implementing a third party risk management platform typically take?
Modern cloud-based TPRM solutions can be operational within 4-8 weeks for basic functionality, though achieving full program maturity including vendor population migration, workflow customization, and integration with existing systems typically requires 3-6 months. Implementation timeline depends heavily on vendor population size, data quality in existing systems, and organizational readiness to adopt new processes.
How do third party risk management tools handle different compliance frameworks?
Advanced TPRM platforms map vendor controls to multiple regulatory frameworks simultaneously, allowing organizations to conduct a single comprehensive assessment that satisfies requirements from GDPR, HIPAA, SOC 2, ISO 27001, and other standards. The platform maintains mappings between assessment questions and specific regulatory requirements, automatically generating framework-specific reports that demonstrate compliance to auditors and regulators.



