How to Uplevel Threat Modeling for a Proactive Cyber Defense
Real-time risk quantification and continuous threat intelligence are revolutionizing cyber risk management.
In today’s dynamic cyber threat landscape, organizations must take a proactive approach to security. Threat modeling has emerged as a critical process for identifying, analyzing, and mitigating potential threats before they can be exploited. However, traditional threat modeling often falls short due to a lack of real-time data, reliance on static risk assessments, and an inability to quantify risk effectively.
A cutting-edge solution should integrate advanced risk quantification and continuous threat intelligence, enabling organizations to rapidly make data-driven decisions and strengthen their cyber resilience.
The Challenges of Traditional Threat Modeling
While threat modeling is a powerful technique, organizations often struggle with:
- Static Assessments: Many threat models rely on outdated or one-time assessments that fail to capture evolving attack vectors, resulting in delayed response to threats.
- Scattered Threat Data: Security teams often rely on multiple tools, leading to fragmented threat information and inefficiencies.
- Limited Vendor Risk Visibility: Organizations can’t estimate third-party risk, which can introduce vulnerabilities into the supply chain.
- Lack of Quantifiable Data: Traditional approaches rely on qualitative measures, making it difficult to prioritize security efforts effectively, leading to wasted time on low-priority issues.
- Disconnect from the Business: Standard threat monitoring tools often treat individual threat events as isolated data points with no connection to business impact.
Transforming Threat Modeling into a Business Tool
SAFE Security addresses these challenges by leveraging its cutting-edge SAFE One platform running threat analysis based on FAIR (Factor Analysis of Information Risk), MITRE ATT&CK and other trusted open standards.
1. Risk Quantification for Prioritization
SAFE enables organizations to quantify specific cyber risk scenarios in financial terms, helping security teams prioritize threats based on probable business impact. This ensures that threat modeling efforts focus on the most critical vulnerabilities and most likely attacks
2. Continuous Threat Intelligence Integration
Unlike static assessments, SAFE continuously ingests threat intelligence, attack surface data, and breach likelihood insights, keeping threat models up to date with real-world attack scenarios.
3. Third-Party and Supply Chain Risk Assessment
With SAFE’s vendor risk management capabilities, organizations can model loss exposure to third-party risks and the effectiveness of internal security measures.
4. Automated Security Posture Assessment
SAFE’s platform integrates with existing security tools to assess an organization’s security posture dynamically. This allows security teams to identify gaps and refine their threat models based on actual security performance rather than assumptions.
5. Scenario-Based Threat Simulations
SAFE facilitates scenario-based simulations, allowing organizations to test various attack pathways and understand the potential impact of different threat actors. These simulations help refine threat models with accurate attack data.
The Business Impact of Enhanced Threat Modeling
By leveraging SAFE’s capabilities, organizations can:
- Improve decision-making with real-time, data-driven insights.
- Reduce risk exposure by proactively addressing high-priority threats.
- Enhance collaboration among security, risk, and executive teams with a common language for risk quantification.
- Optimize security investments by focusing on threats with the highest financial impact.
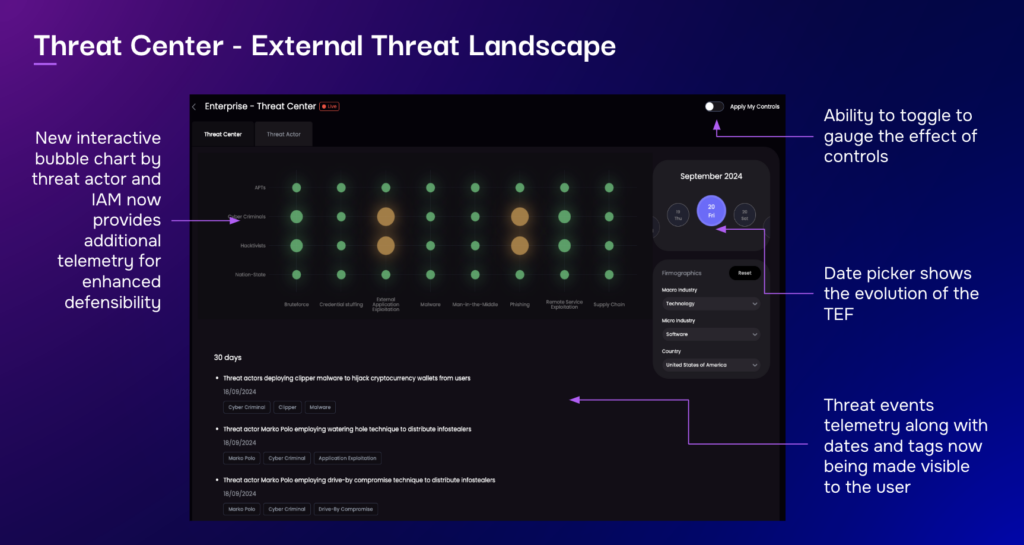
SAFE One Enterprise Threat Center: Bringing Teams Together around a Common View of Threats
The SAFE One platform’s Enterprise Threat Center plays a crucial role in streamlining threat modeling across cybersecurity teams. By providing real-time data on hundreds of threat actors and their techniques, as well as leveraging FAIR-based Threat Event Frequency (TEF) data from over 100 security tool integrations, SAFE One ensures that threat models are built on the best threat intelligence.
Using the platform, teams across Cyber Risk Management, Security Operations, Penetration Testing, and Risk Reduction can collaborate effectively. Threat scenarios are continuously validated and refined, with penetration testing results feeding directly into the FAIR-CAM Control Library, ensuring security controls are aligned with emerging threats.
Furthermore, SAFE One’s Risk Treatment Plans and “What If?” analysis enable security leaders to prioritize remediation strategies based on financial impact, making cyber risk analysis actionable across all relevant teams. By aligning cyber risk management with business objectives, organizations can demonstrate measurable improvements in security posture, as reflected in quarterly board reports generated through SAFE One’s reporting capabilities.
Conclusion
Threat modeling is a vital part of any cybersecurity strategy, but it must evolve to keep pace with modern threats. SAFE enhances threat modeling with continuous risk quantification, real-time intelligence, and automated security assessments, empowering organizations to move beyond static models and adopt a dynamic, data-driven approach to cybersecurity.
By integrating SAFE into their threat modeling processes, organizations can stay ahead of emerging threats, make informed risk management decisions, and build a more resilient cybersecurity posture. If you’re looking to take your threat modeling to the next level, SAFE provides the intelligence and tools needed to stay ahead of the curve.
Learn more:
Automating FAIR: How SAFE Gives CISOs Real-Time Control of Cyber Risk
How One Client Transformed Cybersecurity to Outsmart Threat Groups
See SAFE’s threat modeling solution for yourself; Schedule a demo now.



