ToolShell Fallout: From CVE to Crisis in 48 Hours
SAFE Threat Team Analysis of the unauthenticated RCE exploitation campaign against Microsoft SharePoint
By SAFE Threat Research Team
SharePoint Exploitation Resurfaces with New CVEs
A critical SharePoint exploit chain—ToolShell—is being actively weaponized to target unpatched Microsoft SharePoint servers across government, education, and enterprise environments. By chaining two newly assigned CVEs—CVE-2025-53771 and CVE-2025-53770—adversaries are achieving unauthenticated remote code execution (RCE) on public-facing infrastructure with low complexity and high impact.
This blog post dissects the ToolShell attack sequence, examines real-world exploitation patterns, and quantifies the fallout through dynamic risk modeling.
Why It Matters?
- Unauthenticated exploitation – No credentials are required for full server compromise.
- Enables full RCE – Attackers can gain complete control over vulnerable servers.
- Public exposure – Internet-facing SharePoint instances are at immediate risk.
- Targets widely deployed legacy versions – Especially 2016 and unpatched 2019 editions.
- Evolves to fileless payloads – In-memory execution bypasses traditional detection.
What Is ToolShell and How Does It Work?
ToolShell is a two-part exploit chain exploiting flaws in SharePoint’s access control and ViewState deserialization handling. While Microsoft had previously patched similar issues, these two new CVEs reopened the same attack path.
- CVE-2025-53771 – Auth bypass via a spoofed Referer header.
- CVE-2025-53770 – Unsafe ViewState deserialization enabling RCE once machine keys are stolen.
The Backstory: A Patch That Fell Short
Earlier in July, Microsoft released patches for two issues disclosed during Pwn2Own Berlin:
- CVE-2025-49706 – Authentication bypass
- CVE-2025-49704 – Unsafe ViewState deserialization
Although those patches aimed to close off unauthenticated RCE in SharePoint, attackers found a way around. ToolShell uses techniques similar to those seen in the Pwn2Own exploit but works via slightly different paths, effectively sidestepping the original patch.
Attack Path: From Zero-Auth to RCE
| Mitre ATT&CK Tactic | Stage | Description | Mitre ATT&CK Technique |
| Reconnaissance | Identify Vulnerable SharePoint Servers | Adversary scans public-facing infrastructure to identify exposed SharePoint instances and checks for access to ToolPane.aspx. | T1595: Active Scanning |
| Initial Access | Bypass Authentication via Referer Header | Sends unauthenticated HTTP GET to restricted SharePoint page (e.g., ToolPane.aspx) with Referer: /_layouts/SignOut.aspx header — exploiting CVE-2025-53771 to bypass authentication. | T1190: Exploit Public-Facing Application |
| Persistence | Upload Web Shell via UI Components | Now that they can access admin pages, the adversary uploads a malicious .aspx file (e.g., spinstall0.aspx) using UI upload mechanisms. | T1505.003: Server Software Component: Web Shell |
| Credential Access | Extract Machine Keys from Config Files | Web shell reads sensitive keys (ValidationKey and DecryptionKey) from web.config or machine.config. These keys are necessary for generating signed ViewState payloads. | T1552.004: Private Keys |
| Defense Evasion | Generate Signed ViewState Payload | The attacker uses ysoserial.net or a similar tool to craft a malicious __VIEWSTATE payload, signed using stolen keys to evade validation. | T1027: Obfuscated Files or Information |
| Execution | Trigger ViewState Deserialization RCE | The malicious signed ViewState payload is sent to a vulnerable SharePoint page in an HTTP POST request. Deserialization leads to remote code execution (CVE-2025-53770). | T1059: Command and Scripting Interpreter |
| Discovery | Gathering Host Details | Collects system metadata, OS version, environment variables, and user info from the compromised host. | T1082: System Information Discovery |
| Exfiltration | Transmit Stolen Keys or Data Over HTTP | Exfiltrates machine keys, web config contents, or command output via outbound HTTP request back to the C2 server or encoded parameters. | T1041: Exfiltration Over C2 Channel |
| Privilege Escalation / Lateral Movement | Use of Valid Tokens or Domain Credentials | If credentials are obtained from the system, lateral movement via SMB/RDP may follow. | T1078: Valid Accounts |
Exploitation Timeline: ToolShell in the Wild
- July 14, 2025: Security researchers from CODE WHITE GmbH publicly reproduced the original ToolShell exploit chain and published a working PoC.
- July 18, 2025: Eye Security observed active exploitation in the wild, using zero-day bypasses for the earlier vulnerabilities. A second wave of attacks was observed on July 19.
- July 20, 2025: Microsoft acknowledges patch bypasses, assigns CVEs (CVE-2025-53770 and CVE-2025-53771), and CISA adds CVE-2025-53770 to its Known Exploited Vulnerabilities (KEV) catalog.
- July 21, 2025: Emergency patches were released for the SharePoint Server Subscription Edition and 2019 versions.
- July 21–23, 2025: Confirmed breaches reported across U.S. federal agencies, EU government bodies, and critical infrastructure sectors.
- July 23, 2025: Fileless ToolShell variants using in-memory DLL injection observed in active campaigns.
Affected SharePoint Versions
| Version | Status | Patch Available |
| SharePoint Subscription | Exploited | Yes (KB5002768) |
| SharePoint 2019 | Exploited | Yes (KB5002754) |
| SharePoint 2016 | Exploited | No |
| SharePoint Online | Not affected | N/A |
Refer Microsoft’s official advisory for patch instructions, mitigation steps, and machine key rotation guidance.
SAFE Threat Center Insight: Quantifying the Fallout
As exploitation surged, SAFE’s Threat Center detected a sharp and sustained spike in events associated with External Application Exploitation. It wasn’t a series of isolated incidents – the telemetry pointed to a coordinated, rapidly evolving campaign.
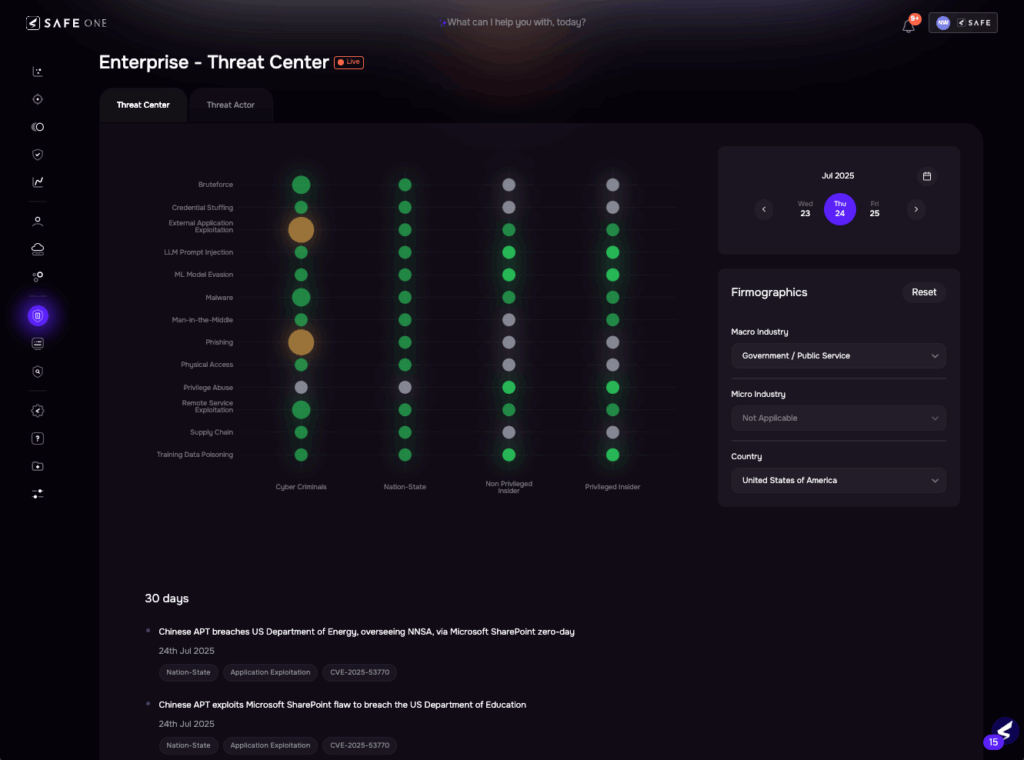
Image 1: SAFE’s Threat Center View
This activity was captured in real time in SAFE’s Threat Event Frequency (TEF). This dynamic metric quantifies the likelihood of adversaries targeting organisations in specific industries and geographies through defined Initial Attack Methods. TEF is continuously recalibrated using validated threat intelligence, public disclosures, and exploitation telemetry.
Where It Hit Hardest: Threat Event Frequency Spike
SAFE’s dynamic TEF modeling revealed pronounced surges in threat activity across the government, education, and critical infrastructure sectors in the US, UK, and the EU, indicating concentrated targeting in high-impact verticals.
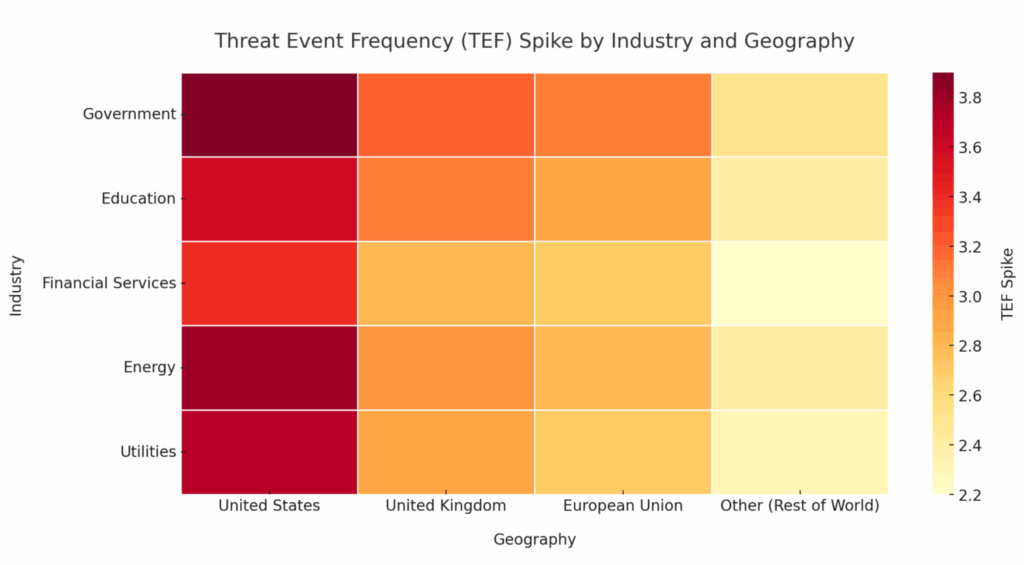
Image 2: Threat Event Frequency Spike across Industries and Geographies
These sector- and region-specific spikes directly influenced breach likelihood scores, triggering real-time reprioritization of affected risk scenarios.
From Threat to Breach: How Risk Shifted Overnight
SAFE’s scenario-based risk modeling recalculated breach likelihood for multiple risk scenarios as exploitation signals rose. Scenarios involving exposed SharePoint servers moved into the critical risk zone within 48 hours.
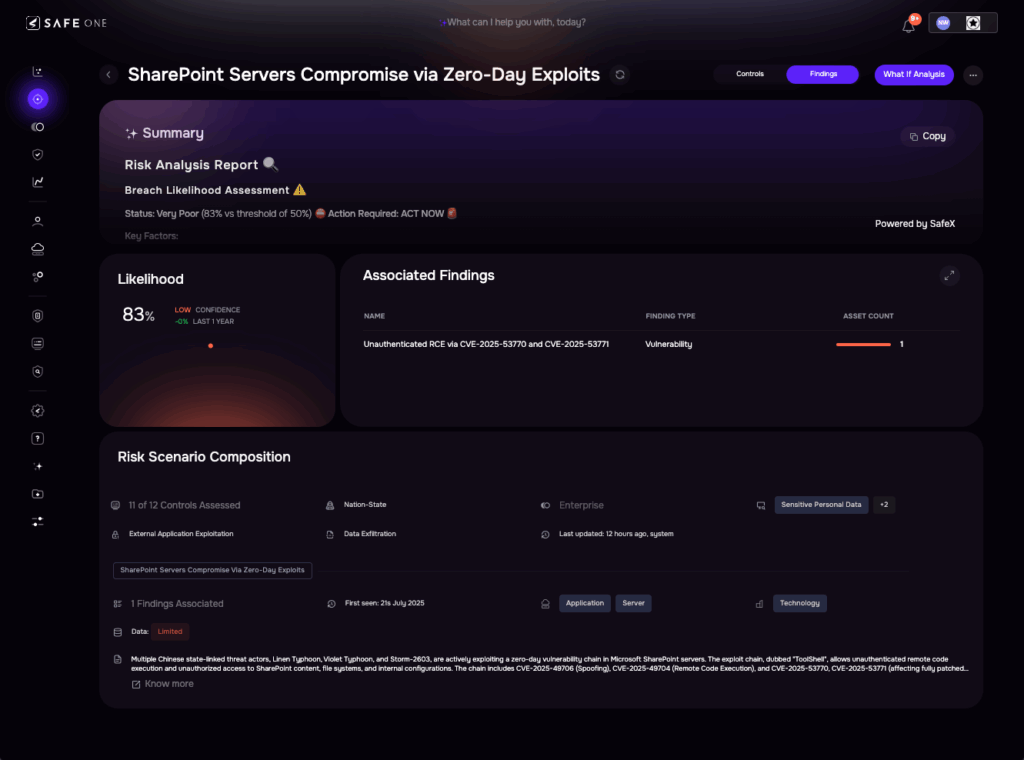
Image 3: SAFE’s Risk Scenario modeling of SharePoint Servers Compromise via ToolShell Exploit
The corresponding findings in SAFE were enriched with telemetry, threat validation, and exploitability context, enabling high-confidence risk quantification and faster stakeholder response.
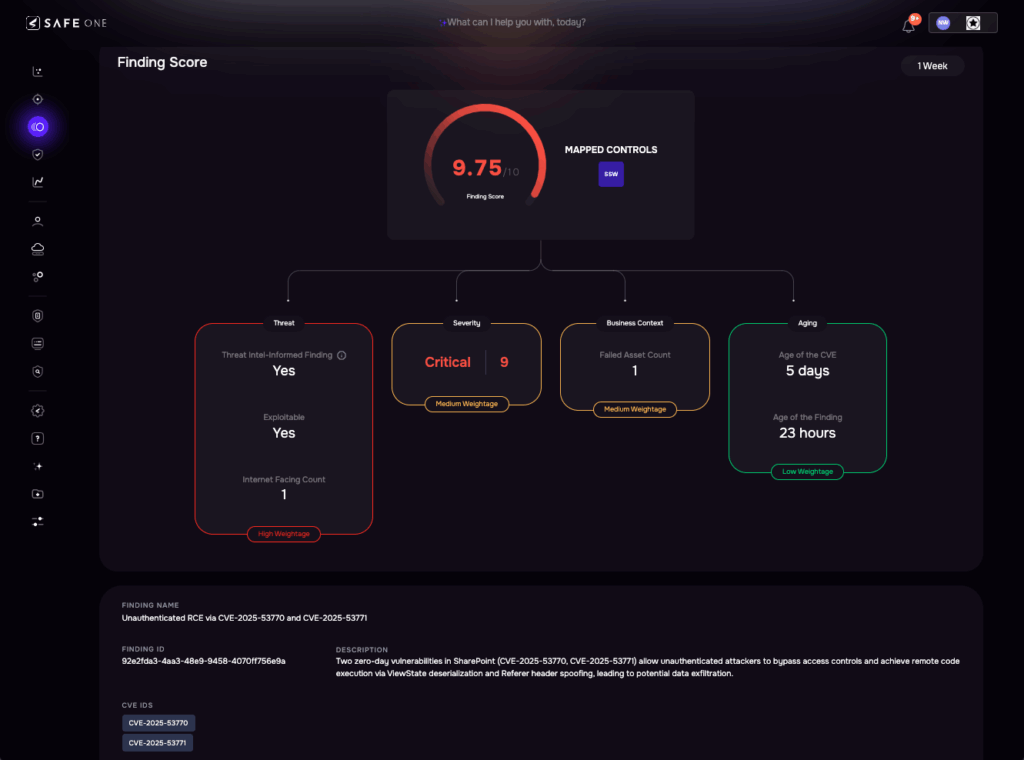
Image 4: SAFE’s Finding View: Unauthenticated RCE via CVE-2025-53771 and CVE-2025-53770
Closing Thoughts: From Noise to Action
The ToolShell campaign reminds us that exploitation timelines are shrinking — and threat actors aren’t waiting for patch cycles to close. Unauthenticated RCE chains like CVE-2025-53770 and CVE-2025-53771 don’t just test technical controls — they test how fast organizations can detect, model, and prioritize risk based on real-world threat activity.
SAFE empowers organizations to do exactly that. By correlating live threat telemetry with dynamic breach likelihood, SAFE helps security teams shift from reactive patching to continuous threat exposure management — tracking which CVEs exist and which ones matter now.
Meet Us at Black Hat USA 2025
We’re excited to showcase the next evolution of our platform at Black Hat USA — including our newly launched CTEM (Continuous Threat Exposure Management) module. Designed to close the loop between threat intelligence, attack surface, and breach simulation, CTEM helps organizations stay ahead of fast-moving campaigns like ToolShell.
Stay ahead of evolving threats by managing cyber risk in continuous, business-aligned terms.
📍Visit us at Booth #3851 at Black Hat USA 2025
Or let us show you the SAFE Enterprise Threat Center in a live demo any time.



