How CISOs can be architects of not just security but innovation and trust

By Jeff Copeland
There’s never been a better time to be a Chief Information Security Officer.
Yes, we know the counter arguments: nation state actors more active and better funded than ever, shortages in the cybersecurity workforce, AI powering threats we can’t even anticipate.
But in a new white paper, we make the optimist case for CISOs: We now see a way clear to cracking cyber risk management, meaning CISOs can rationally plan cyber defenses to take our best possible shot at controlling loss exposure – and establish themselves as architects of not just security but also innovation and trust. Our white paper shows the way with five first steps.
Read the whitepaper now: Top 5 Priorities for Today’s CISO. Here’s a preview:
The Top 5 Priorities
1. Quantify Cyber Risks in Financial Terms
Today’s CISOs translate risks into dollars and probabilities—empowering boards and management to make informed choices and prioritize investments with confidence. The FAIR model makes this possible by breaking down risk into understandable, actionable terms. This approach earns greater engagement from executive stakeholders and turns cybersecurity into a quantifiable business enabler.
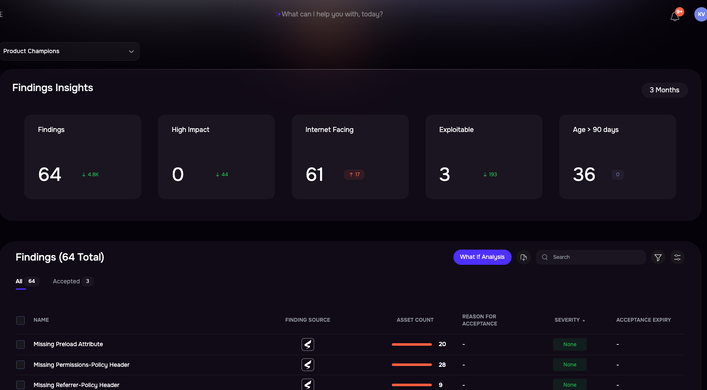
2. Achieve Continuous, Real-Time Risk Visibility
The scale and speed of attacks demands more than periodic reviews. Leading organizations now deploy tools that offer real-time, quantitative risk views. AI-driven platforms can ingest data from dozens of security tools and immediately alert leaders to high-impact vulnerabilities—ensuring nothing falls through the cracks.
3. Enhance Third-Party Risk Management
Third-party vendors remain a major weak point. To close this gap, top CISOs collaborate with vendors on critical security controls, tier suppliers by risk, and focus resources on exposures that truly matter—moving beyond checklists to genuine business partnership. In practice, this could mean segmenting vendors based on the sensitivity of data they access, or requiring high-risk partners to pass more advanced security assessments.
4. Integrate AI-Driven Automation
AI is transforming cyber defense: automating risk analysis, monitoring vendors, and scaling responses to new threats. But successful adoption means careful mapping of business needs and risks, and rigorous control of new potential vulnerabilities introduced by AI itself. Agentic AI platforms can autonomously perform vendor onboarding and compliance checks at unprecedented speed, freeing up analysts to focus on decision-making and strategy.
5. Lead from Risk Management to Resilience
Resilience is more than bouncing back from breaches—it’s aligning cybersecurity to core business functions, clarifying thresholds for action, and preparing teams through simulations. The true differentiator: clear leadership and cross-functional collaboration. Proactive tabletops, effective communication with the board and business units, and mapping mission-critical assets are all part of a modern resilience program.
From Reactive to Strategic Cybersecurity
These five priorities aren’t incremental fixes—they’re a blueprint for evolving cybersecurity into a strategic driver of business growth. CISOs who adopt them will be poised not just to weather the storm, but to turn security into a business advantage.
By quantifying risk, securing the entire value chain, embracing the power of AI, and embedding resilience into the business fabric, today’s CISOs can pioneer a new era. The future of cybersecurity leadership belongs to those who are bold enough to lead change and smart enough to measure its impact.
Read the whitepaper now: Top 5 Priorities for Today’s CISO.
Ready to lead this transformation? Start quantifying risk, modernize your approach, and make cybersecurity a source of strength for your organization. Contact us for a demo of SAFE AI-powered solutions for enterprise risk management, third party risk management and continuous threat exposure management.