How SAFE Protects against Software Single Points of Failure
It’s the most extreme form of third-party cyber risk. Let’s get you a comprehensive controls strategy.
A recent article in the Wall Street Journal detailed how a ransom attack on CDK Global, the dominant software supplier to US car dealerships, forced the dealers to “break out pen and paper to do business, putting a spotlight on other sectors critically reliant on just a handful of vendors.”
CDK controls 50% of the dealership market for systems “essential for all functions,” the Journal reported, a uniquely high level of dependency for an industry sector. But, as the Journal noted:
- In finance, three core providers hold over 70% of the US market for payment processing.
- In healthcare, two vendors control 59% of the electronic medical records market – and Change Healthcare, processor of 44% of medical and pharmacy bills, is still recovering four months after a ransomware attack that disrupted healthcare across the US.
- In airlines, three software providers hold nearly 100% of global distribution.
What’s worse, in many industries, all software has been tweaked to work with a dominant legacy application and “all required the one to work,” one analyst told The Journal, describing the interconnectedness of airline booking, scheduling, and maintenance systems.
Single Points of Failure Are Signs of the Broken State of Third-Party Cyber Risk Management (TPRM) in Cybersecurity
Do you know the single points of failure in your software supply chain? Quite possibly, not. A large organization today may engage with thousands (even tens of thousand) of third-party software vendors and only monitor a small fraction of them because it can’t practically handle third party cyber risk management for the time, money or resources required.
Compounding the scale problem of TPRM: The common tools and practices are merely check-the-box, point-in-time, manual exercises that don’t effectively aid organizations in prioritizing or reducing third-party loss exposure. Examples:
- Cybersecurity ratings, typically based on outside-in scans; can’t assess the partner’s internal controls.
- Questionnaires, lengthy annual exercises with some major limitations: They may list security controls as present but can’t verify their working condition.
- Reporting on compliance with cybersecurity frameworks – not a direct measure of risk
- Integrated methods that pull together questionnaires, ratings, compliance reports – and pull in their limitations.
Learn more in our third party cyber risk management (TPRM) whitepaper.
How SAFE Can Help Protect against Single Points of Software Failure and More Third-Party Cyber Risk Management Blind Spots
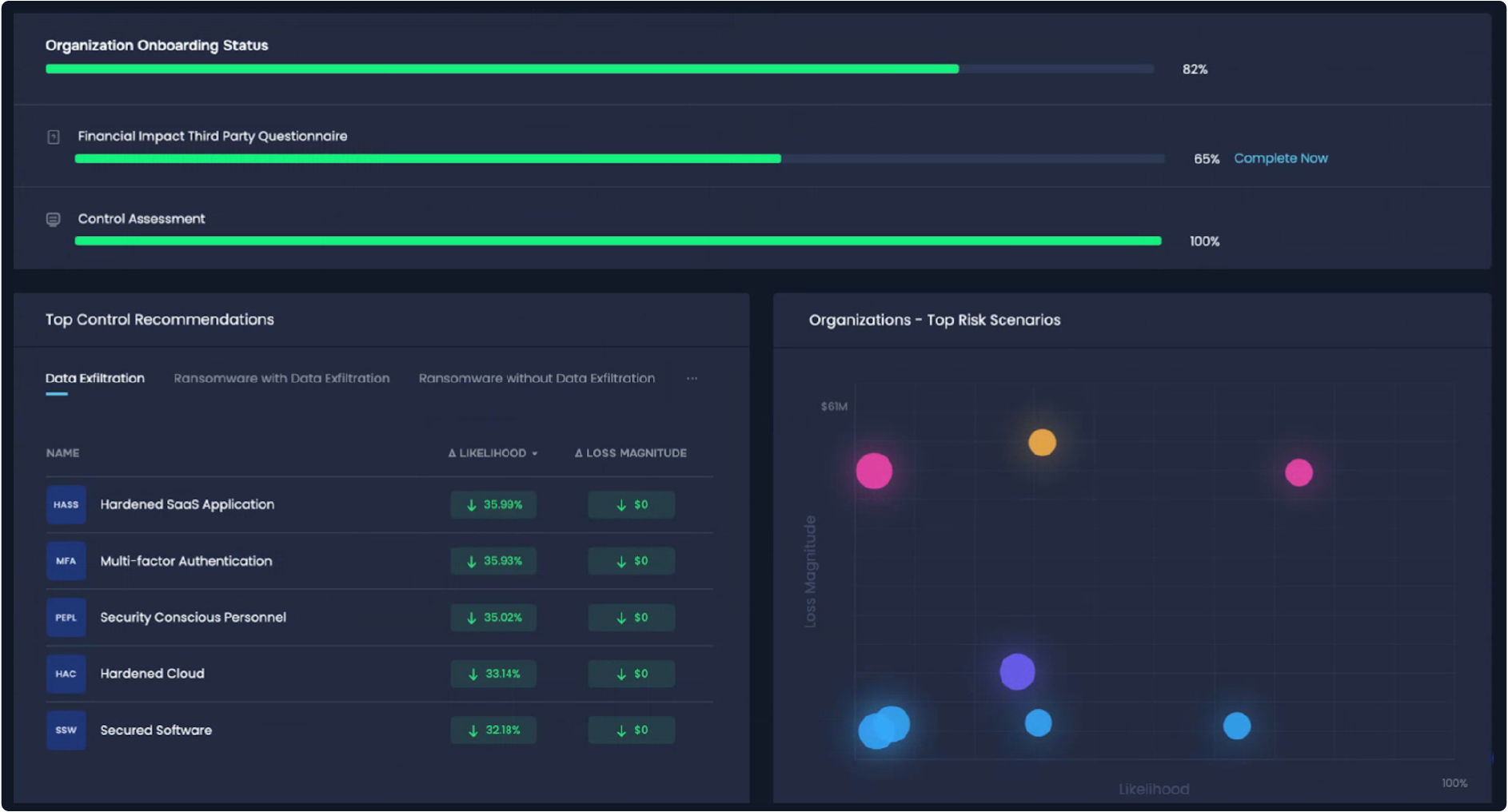
We developed our SAFE One platform from the ground up to solve the particular issues of TPRM and more. Here’s how we approach this problem space in five steps.
- Scope all third parties. We help platform users identify and scope all their third parties and quantify their inherent risk, based on what kind of data they are processing, access to network, revenue dependency and other parameters. We keep these records on each vendor updated continuously.
- Identify critical third parties. Based on their inherent risk, we identify the critical third parties to go to the next step: risk assessment with FAIR-CAM, the Controls Analytics Model based on FAIR, the standard for cyber risk quantification. A FAIR-CAM assessment could leverage outside-in or inside-out scans, questionnaires or other tools to map the controls environment.
- Identify the appropriate controls using SAFE’s comprehensive library of 61 controls. FAIR-CAM outlines how controls “physiology” – the interaction among controls – affects the frequency and magnitude of loss events. We particularly focus on these categories:
- Business Continuity and Disaster Recovery controls that help organizations understand how they can work with critical third-parties to build redundancy and resilience and reduce the impact in the event of a breach or disaster.
- Incident Response controls that make up a systematic approach to managing and mitigating security events.
- Zero trust controls in place at the first party to respond to and/or minimize a breach originating from a third party. This is a grouping that includes the controls for Third-Party Cyber Risk Management, Security Rating Service, Third-Party Risk Exposure Likelihood Reduction and Third-Party Risk Loss Magnitude Reduction provided by SAFE’s SAFE One platform.
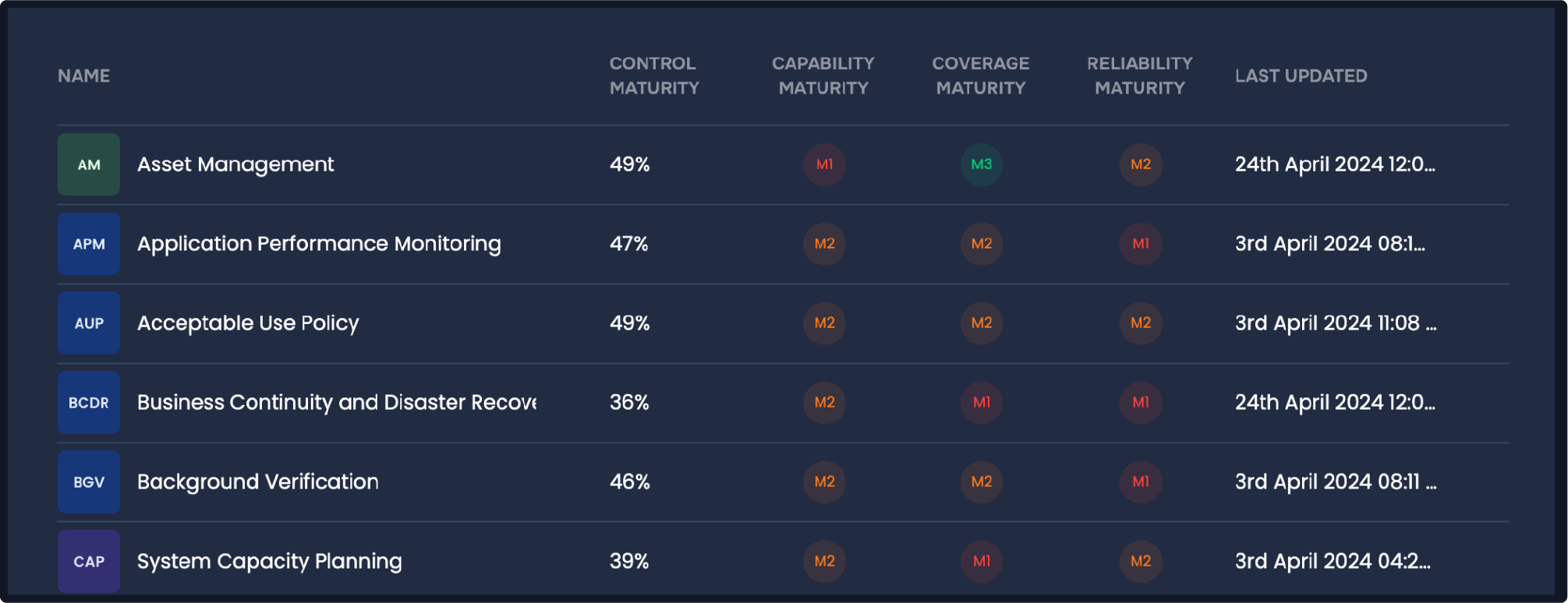
- Rate the controls. The SAFE One platform rates controls for maturity across Capability, Coverage,and Reliability.For instance, on Incident Response, Capability ratings would include:
- M0 – Control not implemented
- M1 – Basic capabilities to communicate about an incident in real time but not to analyze, eradicate and recover
- M2 – A comprehensive response plan with post-incident review, documentation and integration with other security controls.
- Identify the residual risk. With this systematic and disciplined approach implemented on the SAFE One platform, we achieve
- A clear, quantified, defensible view of third party risk
- Continuous monitoring of third party risk, no longer dependent on point-in-time, partial readings on risk
- A clear sense of the priorities for a third party cyber risk management program – including a good grasp of the single points of failure with the most serious implications for the business.
Explore how you can deploy the power of quantitative cyber risk modeling to solve your TPRM challenges. Contact us for a demo.



