Traditional third party cyber risk management (TPRM) just isn’t working. Save it with these new techniques.
by Jeff Copeland
“87% of Fortune 1000 companies were affected by a significant cyber incident at a third party in the past 12 months.”
–RSA Conference Survey, 2024
Third-party risk management has hit a crisis point. As the dependence on third-party vendors of software and SaaS has grown, so has the attack surface. Attackers have figured out that rather than hitting hardened targets at major companies, they can hijack their vendors, often smaller companies with more limited cybersecurity defenses.
The effects on business operations are often devastating, as companies discover the hard way their vulnerability to single points of failure. Case in point: the UnitedHealth/Change Healthcare cyber-attack that disrupted payment systems for medical offices and pharmacies across the US in 2024.
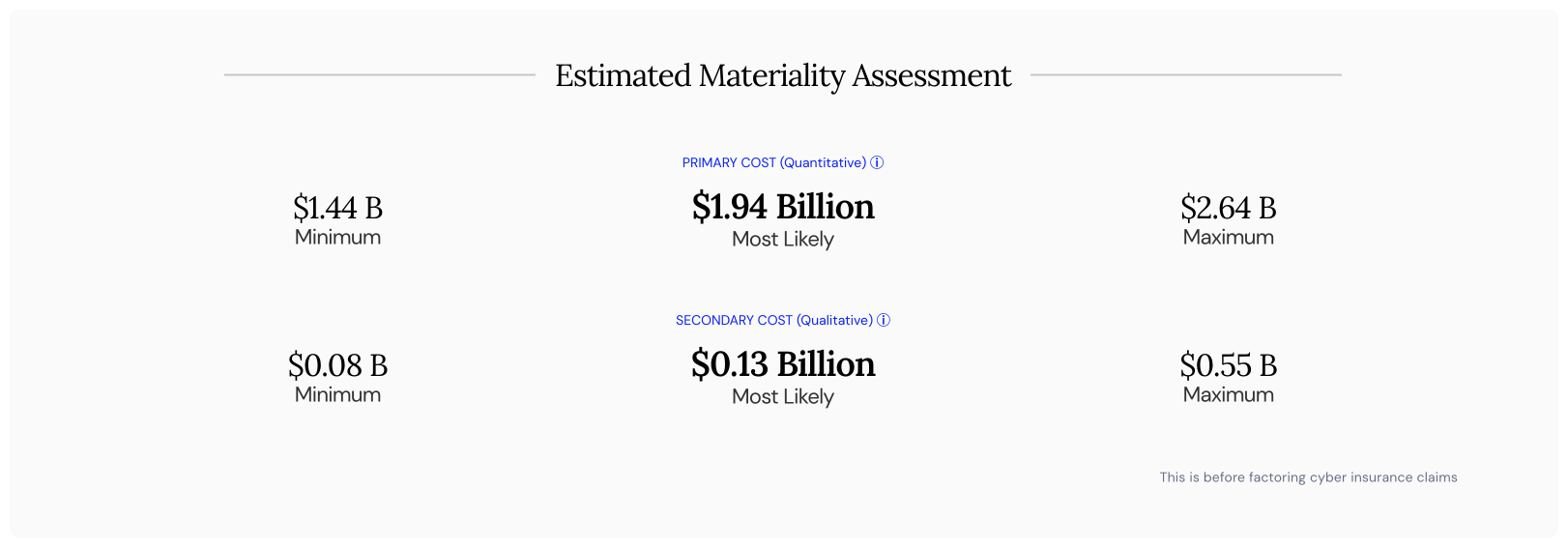
At the same time, confidence in the accepted techniques of third-party cyber risk assessment and management has plummeted. The RSAC Executive Security Action Forum (ESAF) issued a report in 2024 that found:
“The consensus in the ESAF community of CISOs is that traditional third party cyber risk management in information security is ineffective. Traditional methods, centered around self-assessment questionnaires and cybersecurity ratings, do not provide an accurate picture of third-party risk nor reduce risk. The need for change is growing more urgent.”
What do you need to know to protect your organization from third-party cyber threats? Let’s explore some answers.
What Is a Third-Party?
A third party could be:
- Suppliers of software or hardware for IT or OT environments, devices and equipment, components for manufacturing
- Service providers for IT/Cloud/SaaS, facilities maintenance, HR/Finance/Payroll, manufacturing
- Distributors, brokers or other business partners
What Is a Third-Party Cyber Risk Assessment?
A third-party risk assessment should be
- A collaborative effort between first- and third-party
- Fundamentally driven by a goal of reducing potential risks
- Quantitatively and reliably assessing the risk posture of the third party
- Continuously updated in real time, not an annual event
- Equally concerned with assessing the risk posture of the first party to protect against third-party risk
Why You Should Do Third-Party Cyber Risk Assessments
Third parties are deeply connected to the operation and success of your business. How deep? Look at the outage in 2024 of CrowdStrike, a leader in anti-virus, endpoint security that pushed out buggy code to its clients. It turned out that CrowdStrike was operating at the deepest “kernel” level of Microsoft Windows, taking down Windows systems around the world; just one effect was a global “ground stop” on flights of major airlines.
Third-party cyber risk assessments can help you answer these 5 questions:
1. What is the risk posture of my third parties?
2. What sources of information do our risk managers utilize regarding our third party relationships – are they reliable?
3. What risk scenarios originating from third parties could cause the most financial, legal or reputational harm to my business? How could I prioritize my focus on the riskiest third parties?
4. Where do I have single points of failure – over-reliance on a single vendor or partner? Which vendor relationship has the deepest reach into my systems?
5. What is my risk and resilience posture facing third parties for limiting my exposure to them?
Limitations of Typical Third-Party Cyber Risk Assessments
The predominant techniques in third-party risk assessment have not been updated in a decade and are increasingly under question as to whether they provide sufficient value to justify the large amounts of money and time required. Typical practices are:
Self-assessment questionnaires
Often 200-plus questions answered by the third party annually reporting on the organization’s cybersecurity controls in place.
Problems: “Checklist approach” – assumes that the presence of controls reduces risk, though with no indication of how well the controls perform. Promotes a “shopping spree” approach to security tools acquisition Only accurate for a point in time. Labor-intensive for both third parties to complete and first parties to ingest.
Security ratings services
Cybersecurity risk ratings conduct a scan of the third party’s network as visible from the outside plus a check on publicly available information to produce a loosely defined numeric rating.
Problems: Just a partial view of the third party’s risk posture – no visibility into internal controls or other capabilities. A single, numeric score gives a false sense of accuracy and is disconnected from the financial aspect of TPRM.
Compliance with frameworks
A self-attestation that the third party has in place controls recommended by framework such as SOC 2.
Problems: Rarely conducted by an outside auditor; typically limited in scope.
In general, these approaches to third party cyber risk management are time-consuming and ultimately don’t give reliable indicators to first- or third-parties of how much risk they have, where it is concentrated, and actionable steps they might take to mitigate risk.
Key Things to Consider Before Doing a Third-Party Risk Assessment
Roles and Responsibilities
Your organization:
- Recruit partners within the business: Legal, Business Continuity, Finance, etc. – each will have their own perspective on third parties
- Create a directory of vendors and other third parties
- Identify a set of critical controls required for third parties; make those the focus of your TPRM questionnaire.
- Implement a standard for criticality/redundancy or financial impact to prioritize among third parties
- Foster a sense of shared responsibility for security with third parties; involve them into strategic planning
A third party:
- Fill out and return questionnaires to first party accurately and within deadlines – as well as attestations, compliance records, vulnerability reports or other documentation
- Cooperate with inside-out and outside-in scans of controls in security assessments
- Participate in shared planning for security with first party
Data Classification Grade
- Assess nature and extent of data accessed or managed by the third party
Third-Party Risk Assessment Best Practices
Maintain an Accurate Vendor Inventory
Not an easy task; some large companies have thousands, even tens of thousands of vendors and supply chain partners and each may operate under a separate deal with different parts of the business. Best approach is bottom-up: Collect the information by business unit and aggregate in one central management system.
Tier Third Parties by Loss Exposure for Your Organization
Assess your vendors for the risk they pose based on their access to your data, your network and capability to create business interruption, including redundancy. Rank the third parties and prioritize your security efforts toward them accordingly.
Select an Appropriate Vendor Questionnaire
Questionnaires should focus only on critical controls, not overload vendors with a large, catch-all list. Take a zero-trust approach to your partner-facing controls and consider yours and theirs as a whole and triage appropriately. Extend the reach of your questionnaire into the fourth party and beyond; do they know the status of security posture of their vendors’ vendors?
Utilize Technology to Streamline Processes
Automate wherever possible in distributing and tracking questionnaires as well as ingesting questionnaires and other reports from vendors. Large Language Models (Artificial Intelligence) can now speedily interpret and sort communication from third parties.
Regularly Review Vendor Performance
Conduct formal reviews several times a year. Annual reporting is a thing of the past when it comes to security measures
Continuous Monitoring and Adaptation
Following best practice today, integrations can pull status reports directly from controls at the third party. This inside-out reporting plus outside-in scans of internet-facing controls plus questionnaires gives a truly wraparound, continuous view of security at the third-party level. Controls gaps are quickly spotted and remediated, and defenses can quickly pivot to meet new threats.
The Role of Third-Party Risk Assessments in TPRM Programs
Successful third party cyber risk management programs deliver three values. Each depends on a well-tuned risk assessment:
Visibility
–TPRM should identify the riskiest vendors, as identified by a standardized risk assessment.
Mitigation
–TPRM enables ROI-driven, prioritized and actionable insights to quantifiably reduce third-party risks
Automation & Scale
–Whether it’s always-on reporting on controls status or ingestion of risk questionnaires, TPRM must be automated to keep up with today’s risk landscape.
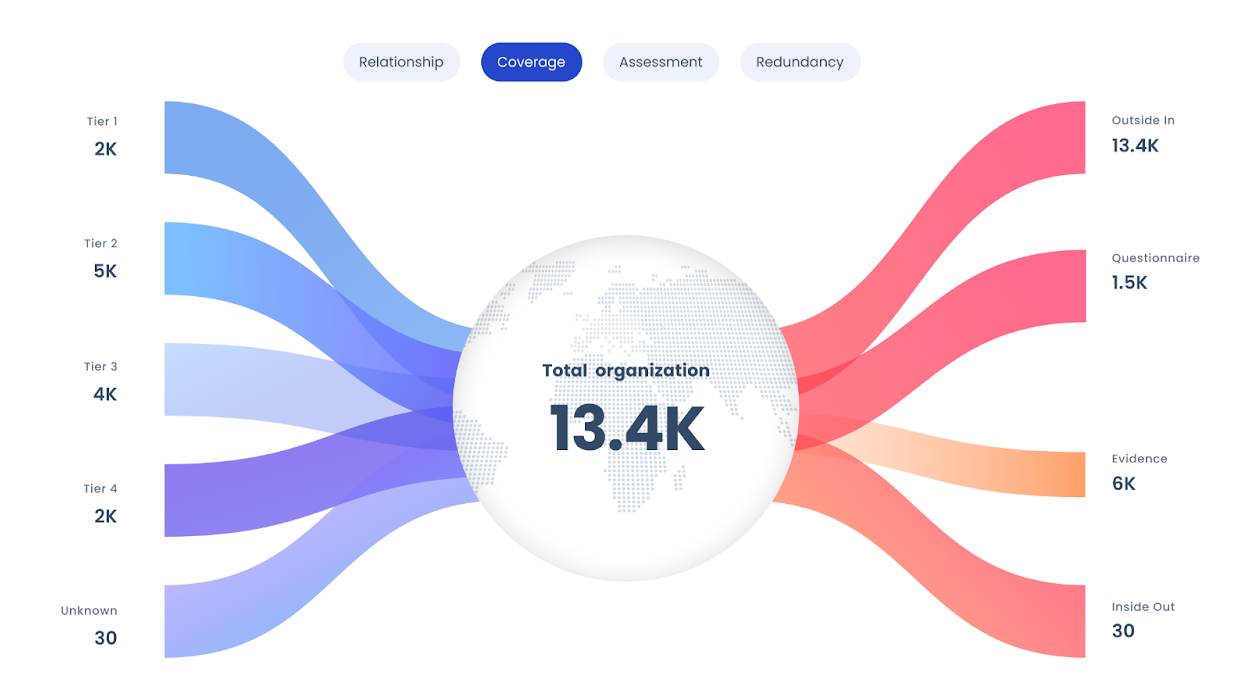
Third-Party Risk Assessment with SAFE
SAFE has re-imagined third party cyber risk management. Using the SAFE One platform, enterprises can finally get holistic, realistic, dynamic, and dollar-driven insights into their third-party risk posture, delivered in the same view as their enterprise cyber risk management. With data-driven insights, control recommendations, and a unified risk view, CISOs and third parties are in a strong position to achieve resilience.
Our key features, unique in the industry, include:
A Prioritized Approach to TPRM
We simplify managing third party risk by focusing on the most critical controls, derived from our extensive research of data on third-party cyber-attacks. As a result, third parties can submit highly focused reporting on questionnaires, compliance documentation and other evidence, shifting the focus from quantity of reporting to quality and ensuring speed and accuracy. Using AI and large language models (LLMs) SAFE TPRM also takes in and consolidates data from outside-in scans and inside-out data feeds via API integrations, for real-time assessment of the whole controls environment, revealing a highly focused list of an organization’s critical controls for TPRM.
Managing Third-Party Risk Impact Using Zero Trust Controls
SAFE has pioneered applying zero-trust principles to the TPRM problem space, drawing on the insight that the enterprise’s internal resilience controls facing third parties are as important as the third party’s controls. SAFE TPRM groups enterprise controls into likelihood-reduction controls and business continuity controls to enable enhanced control effectiveness in minimizing third party data breaches. These insights into third- and first-party risk in one view equip risk management teams to redistribute resources and improve their internal cyber risk resilience – minimizing the impact of potential breaches.
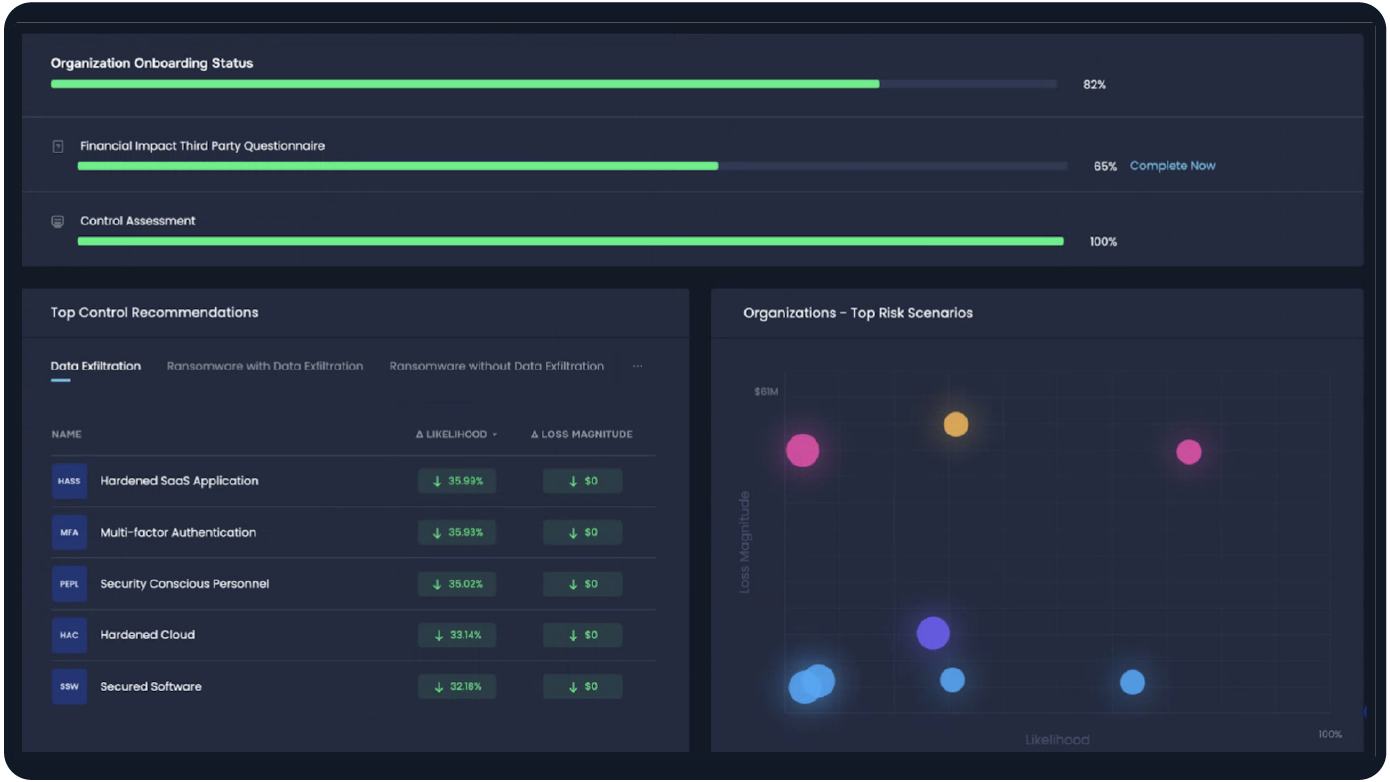
Deepest Partnership with Third Parties to Improve Security
The SAFE One platform shows a real-time view of the security posture of vendors. The platform makes that easy by 1) giving supply chain partners direct access to the platform for uploading questionnaires or compliance documents and 2) continuous monitoring of the security posture of partners with API-mediated, AI-interpreted status reports on controls. The result is meaningful partnership with third parties on risk reduction.
Tier Third Parties Based on Risk
The SAFE One platform leverages a huge library of risk scenarios such as ransomware attacks or data breaches assuming third-party data access or network access and resulting in business interruption – all assessed for likelihood of occurring and likely financial impact. This enables CISOs to tier their most critical vendors based on probable loss exposure and prioritize controls for maximum reduction of third-party risk.
All Your Third Parties Covered
SAFE recognizes the dynamic nature of vendor risk management and associated costs. Our response: Users can add an unlimited number of vendors at a fixed price since SAFE TPRM pricing is independent of the number of vendors – 100% of your vendors will be assessed. It’s a scalable pricing model so you can manage expenses of a growing third-party portfolio.
Let us show you the power of SAFE TPRM to solve third party cyber risk management for your organization. Schedule a 1:1 demo today to start your re-imagined TPRM journey.



