Hear what our customers say about the only AI-driven platform for comprehensive first and third party cyber risk management
by Sachin Jha
In today’s rapidly expanding digital landscape, Chief Information Security Officers (CISOs) face the pressing challenge of scaling cyber risk management strategies to keep pace with business growth. Traditional cybersecurity approaches often become constraints rather than catalysts for growth due to their reliance on manual processes and subjective assessments. These legacy methods are increasingly inadequate for today’s needs for real-time, data-driven decision-making.
The Growing Demand for Real-Time, Data-Driven Cybersecurity
As businesses evolve and digital transformations accelerate, the need for an agile and informed cybersecurity strategy becomes critical. CISOs are required not only to safeguard the organization’s assets but also to position cybersecurity as a driver of business growth. This shift demands a departure from conventional, static risk management practices which often lag behind the fast-paced changes in the threat landscape and business environments.
The Pressing Challenges in Cybersecurity
Across industries, CISOs and security practitioners face several daunting challenges:
- Fragmented View of Security Posture: Many organizations struggle with siloed cybersecurity tools that provide incomplete views of risks, making effective management and decision-making difficult.
- Inadequate Risk Quantification: Traditional security solutions often lack the ability to translate cyber risks into business impacts, which is crucial for aligning security initiatives with business objectives.
- Resource Misallocation: Without clear insights into which risks pose the greatest threat, organizations can neither prioritize their responses effectively nor allocate their resources efficiently.
These challenges make it difficult for CISOs to demonstrate the value of cybersecurity investments and secure their position in strategic discussions at the board level.
SAFE One: A Unified Solution
The SAFE One Platform emerges as a modern solution designed to overcome these hurdles by harnessing the power of automation and artificial intelligence. This platform provides a unified approach to managing both first-party and third-party cyber risks, offering a suite of tools tailored to enhance decision-making capabilities across various organizational levels.
Utilizing SAFE One, organizations can effectively navigate the complexities of cyber risk management (CRM) with a series of decision areas tailored to various stages of their cybersecurity maturity.
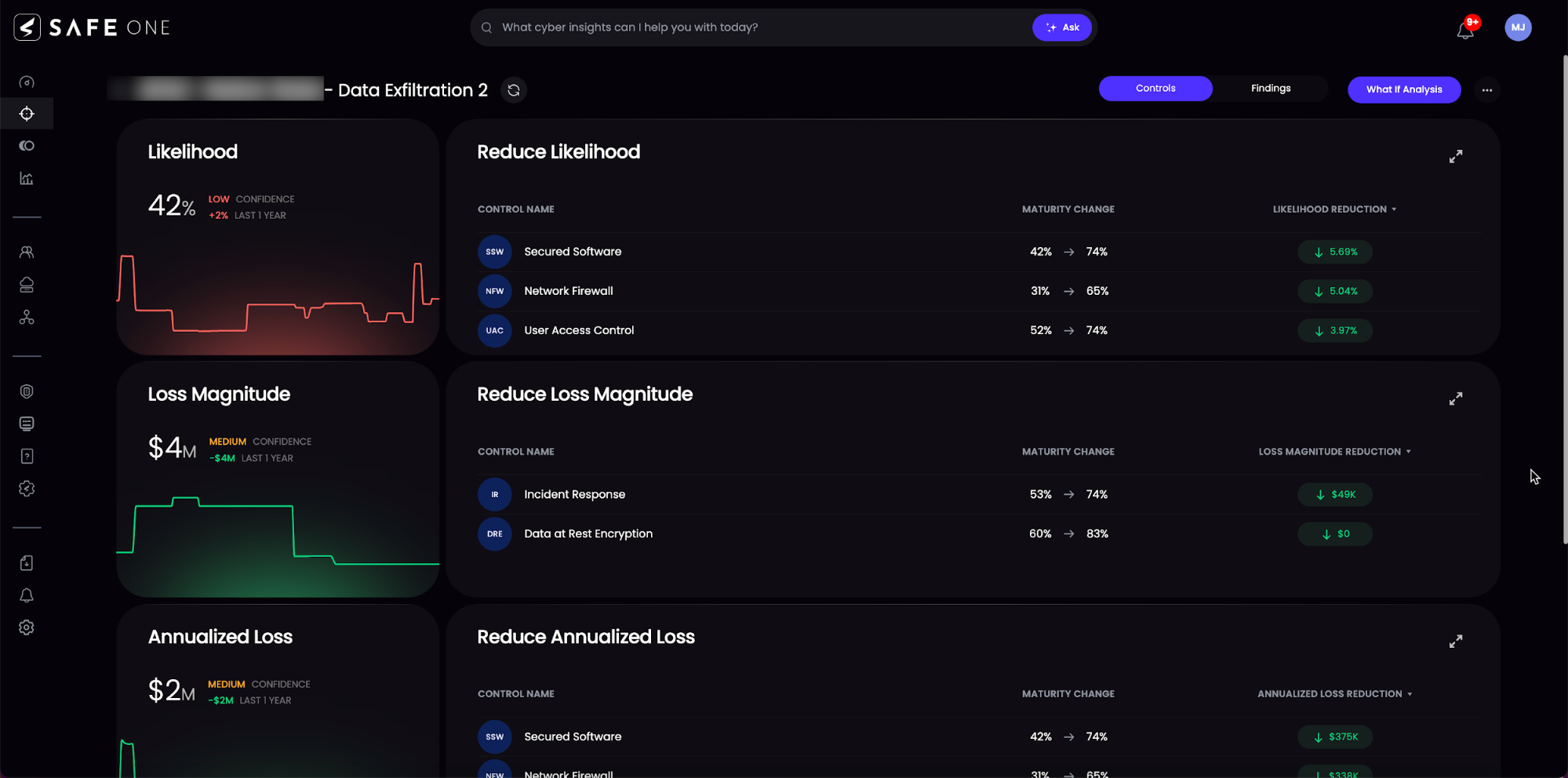
Decision Areas for Comprehensive Cyber Risk Management with SAFE One
1. Know, Understand and Communicate Risk: This decision area empowers organizations to fully understand and articulate their cybersecurity risks from a business-centric perspective, in financial terms. By answering critical questions such as “How are my controls working?” and “How much risk did I burn down?”, CISOs can provide actionable insights to stakeholders, ensuring that cybersecurity strategies are aligned with business objectives.
2. Operational Risk Prioritization and Treatment: Addressing operational challenges head-on, this area focuses on the day-to-day management of cyber risks. Questions like “Which security controls to fix?” guide the operational tactics, allowing businesses to mitigate risks to an acceptable level and enhance their overall cyber resilience. This proactive approach supports operational efficiency by streamlining processes and optimizing the allocation of security resources.
3. Strategic Risk Treatment and Investment Planning: Strategic risk management goes beyond immediate threats, addressing long-term planning and investment. It answers pivotal questions such as “Where do I invest $” and “How should I launch this new business/capability?” By developing business cases that justify the cost-effective allocation of budgets towards cybersecurity, this area enables organizations to plan their investments strategically, ensuring maximum return on investment (ROI) and sustained business growth.
4. Meet Reporting Requirements: Compliance and reporting are critical components of an effective cybersecurity strategy. Organizations must navigate the complexities of meeting both internal and external audit and regulatory risk reporting requirements. This decision area assists in streamlining these processes, ensuring that all cybersecurity measures are up to code and that reporting is conducted efficiently and transparently.
5. Manage Third-Party Risk: As businesses increasingly rely on third-party vendors, managing external risks becomes crucial. This area focuses on prioritizing and managing third-party risks based on the direct cyber loss exposure they pose. It addresses essential queries like “A peer got attacked, am I secure?” and “How secure are my crown jewels?” which are vital for safeguarding against breaches stemming from third-party interactions.
Tailored for Business Leaders
Each of these decision areas is designed not only for CISOs but also for Chief Information Officers (CIOs), Chief Financial Officers (CFOs), and business unit leaders who need to integrate robust cyber risk management practices into their strategic planning. The SAFE One Platform facilitates a comprehensive understanding of the cyber landscape, empowering leaders to make informed decisions that bolster security, enhance compliance, and drive business innovation.
Streamlined Compliance and Reporting
SAFE One simplifies compliance reporting by providing clear insights into an organization’s security posture and the effectiveness of its controls, tailored to meet various regulatory requirements. This not only aids in maintaining compliance but also in demonstrating security assurance to stakeholders.
Transformative Customer Success Stories from SAFE One Users
Kettering Health
Before SAFE: Needed a robust method to protect patient data and manage related cyber risks.
After SAFE: Implemented targeted risk management strategies based on quantifiable risk assessments, significantly enhancing patient data protection.

Read More About Kettering Health’s Transformation in Our Detailed Spotlight
IHG Hotels
Before SAFE: Struggled with a unified approach to managing risks across global operations.
After SAFE: Gained a comprehensive risk visibility and management capability, resulting in strengthened security measures across properties.
Read More About IHG’s Transformation in Our Detailed Spotlight
Glovo
Before SAFE: Limited visibility into cybersecurity risks, challenging the prioritization and mitigation processes.
After SAFE: Enhanced decision-making capabilities with a clear understanding of risk priorities, leading to more strategic resource allocation and improved compliance with international standards.
Read More About Glovo’s Transformation in Our Detailed Spotlight
Blue Cross Blue Shield of Arkansas
Before SAFE: Faced challenges in assessing and quantifying risks comprehensively.
After SAFE: Achieved a holistic view of cybersecurity risks, enabling better protection of sensitive information and adherence to industry standards.
Read More About Blue of Arkansas’ Transformation in Our Detailed Spotlight
Empowering CISOs for Business Growth
By providing a solution that aligns with the pace of business growth and the dynamic nature of cyber threats, SAFE One empowers CISOs to transform their roles. No longer seen merely as gatekeepers, they are now strategists capable of using cybersecurity as a tool for business enablement. This shift not only protects shareholder value but also secures the CISO’s seat in the boardroom, proving that effective cyber risk management is a key component of modern business strategy.
SAFE One’s approach not only meets but exceeds regulatory requirements and board expectations, making it an indispensable tool for any forward-thinking CISO looking to elevate their organization’s cybersecurity posture in the digital age.
Learn more about the SAFE One unified platform for first- and third party cyber risk management. Contact us for a demo.
New! The SAFE X mobile assistant for CISOs puts cyber risk management at your fingertips.


