NIST Third-Party Risk Management: 800-53, 800-161, CSF
Ensure compliance, reduce vendor risk with a new, risk-based approach to these standards
Key Takeaways
- NIST’s three main frameworks for third-party risk are SP 800-53, SP 800-161, and the Cybersecurity Framework (CSF 2.0).
- 800-53 sets foundational security controls, including supplier risk management.
- 800-161 focuses on supply chain-specific vulnerabilities, including fourth-party risks.
- CSF 2.0 (NIST Cybersecurity Framework) unifies risk management with governance, resilience, and business alignment.
- Compliance requires vendor onboarding, SBOM transparency, risk scoring, and continuous monitoring.
- A unified approach combining all three frameworks reduces complexity and strengthens security.
What Is NIST Third-Party Risk Management?
If you know NIST standards, you already grasp the basics of building a secure foundation. But when it comes to protecting your extended business ecosystem—suppliers, vendors, and partners—the game changes. That’s where NIST’s supply chain risk management standards, like SP 800-161, step in.
NIST third-party risk management (TPRM) is about looking beyond your own walls. It builds on core NIST guidelines by focusing on the specific challenges of managing cyber risk throughout your supply chain.
The standard lays out practical steps for identifying, assessing, and monitoring risks that emerge when you connect with external providers. It’s less about securing just your network, and more about safeguarding the entire web of digital relationships your organization relies on.
Why is this critical? Because attackers rarely go straight through the front door. More often, they look for cracks in your supply chain—targeting your least prepared vendor as the easiest way in.
The supply chain standard gives you a framework for closing those gaps. It covers everything from verifying vendor security controls, to ongoing due diligence, to responding fast when something goes wrong.
In short, applying NIST’s supply chain framework isn’t just a compliance exercise. It’s the proactive groundwork that protects your business and builds confidence with every partner in your ecosystem.
Overview of NIST 800-53, 800-161, and CSF 2.0
When it comes to managing third-party risks, the National Institute of Standards and Technology (NIST) provides three foundational frameworks to guide organizations. Each framework serves a unique purpose but works harmoniously to strengthen your security posture. Here’s a closer look at NIST 800-53, NIST 800-161, and the Cybersecurity Framework (CSF 2.0)—and how they help with vendor risk controls.
NIST 800-53
If you think of NIST standards like a toolbox, NIST 800-53 would be the multi-tool everyone needs. Its primary goal is to provide a catalog of security and privacy controls designed to protect information systems, assets, and individuals. It’s comprehensive and applicable across industries, focusing on everything from access control to incident response.
For third-party risk management, 800-53 emphasizes supplier risk (SR) controls, laying the groundwork for managing vendor relationships in risky environments. Imagine these controls as guardrails ensuring that vendors meet specific security criteria, such as encryption standards, incident reporting, and access restrictions. These SR controls are a key component for ensuring that external parties don’t introduce vulnerabilities into your ecosystem.
Key takeaway? 800-53 is broad, actionable, and forms the baseline for structuring vendor controls.
NIST 800-161
Now, zoom in closer to the supply chain. That’s where NIST 800-161 comes into play. If 800-53 establishes the rules of engagement, 800-161 provides a laser focus on supply chain risk management (SCRM). This framework is all about minimizing risks introduced by third parties and their suppliers by addressing vulnerabilities inherent to global supply chains.
Think of it as tiered protection for your vendors. It emphasizes identifying critical suppliers, understanding their risks, and verifying their resilience before signing on the dotted line. For instance, imagine working with a cloud provider that outsources database services. Under 800-161, your organization would evaluate not just the cloud provider, but also their database subcontractor, ensuring risk visibility through the full supply chain.
Key takeaway? 800-161 digs deeper into supply chain-specific risks, enabling finer control over vendor tiers and dependencies.
Cybersecurity Framework (CSF) 2.0
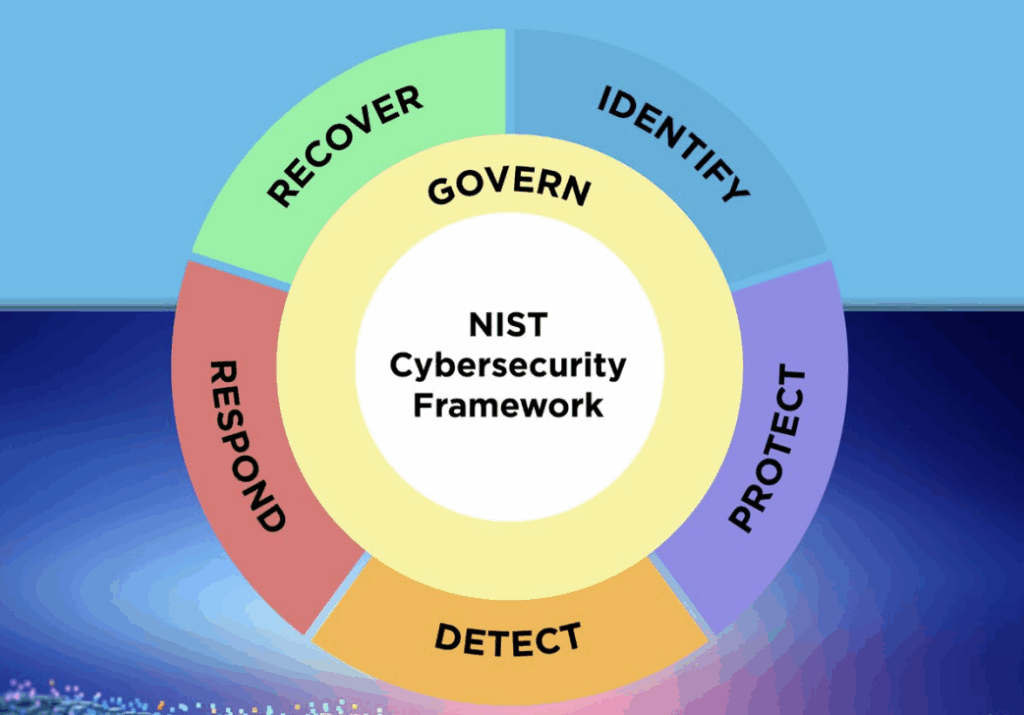
Finally, there’s CSF 2.0, NIST’s flexible guide for building and improving cybersecurity programs. The CSF brings in a holistic view, covering not only technical controls but also governance. Its five core functions—Identify, Protect, Detect, Respond, and Recover—help organizations think beyond risk mitigation, focusing on resilience and proactive defense. For third-party risk, the new “Govern” function in CSF 2.0 is a game-changer.
Imagine that you’re orchestrating a symphony of vendors, each contributing to your overall operations. The CSF framework ensures every “instrument” stays in sync, with defined protocols for vendor access, real-time monitoring, and ongoing assessments. It’s not just about compliance—it’s about ensuring that your third-party ecosystem doesn’t break the harmony of your operations.
Key takeaway? CSF 2.0 provides a high-level structure to unify risk management practices while emphasizing overarching business objectives.
How They Work Together
While each of these frameworks has its strengths, their real power lies in how they complement each other:
- 800-53 sets the foundational controls everyone should follow.
- 800-161 takes these controls deeper into the supply chain, focusing specifically on vendors (third-party risk) and their vendors (fourth-party risk)
- CSF 2.0 brings it all together, linking technical implementation with big-picture strategies like governance and resilience.
Think of it this way—800-53 is your foundation; 800-161 is your blueprint for fine-tuning vendor-specific risks, and CSF 2.0 is your project manager tying it all together seamlessly.
By integrating these frameworks into your NIST third-party risk management framework, you’ll not only meet compliance requirements but also create a robust system that reduces vulnerabilities and fosters trust across your supply chain.
Warning: Many organizations fall into a “compliance-first” mentality, treating these standards like checklists – check the box that a control is present and the risk-management job is done. But controls in place may or may not be effective and may or may not interact with other controls for better or worse. Sophisticated organizations measure the maturity of their controls environment with both the NIST CSF 2.0 and FAIR-CAM (FAIR Controls Assessment Model), the recognized model for quantitative assessment of controls efficacy.
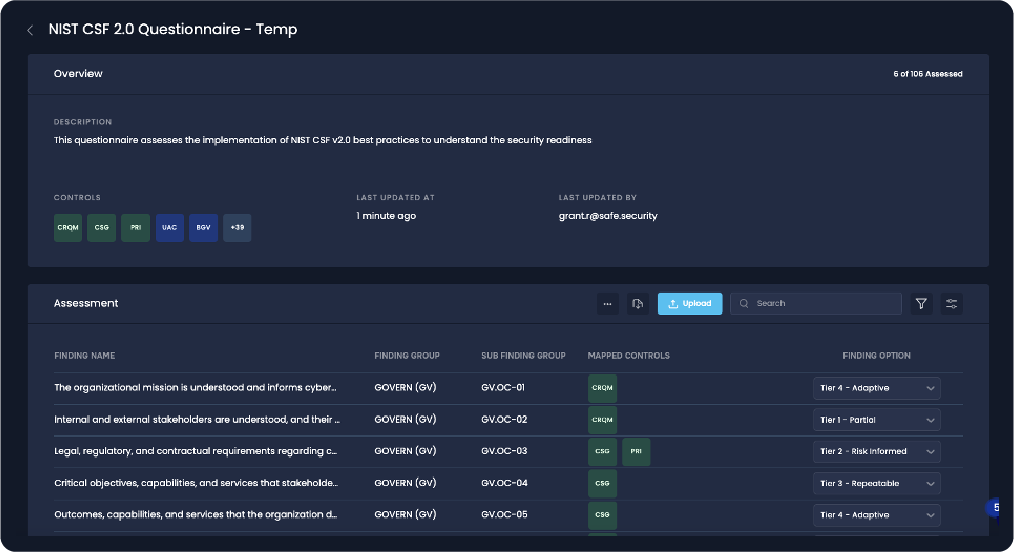
NIST CSF questionnaire for onboarding a vendor, SAFE platform
NIST Compliance Requirements for Vendors and Third Parties
To build a secure, transparent, and trusted supply chain, vendors must meet several compliance benchmarks defined by the NIST third-party risk management framework. These requirements go beyond technical checks—they create a shared responsibility for cybersecurity, ensuring that vulnerabilities don’t slip through the cracks and ripple across your entire supply chain. Here’s a breakdown of key compliance areas for vendors and how they drive confidence and security throughout the ecosystem.
Vendor Onboarding Processes
Imagine hiring an employee without doing a background check—it’s risky, right? Well, onboarding vendors without a strong compliance process is just as dangerous. NIST compliance starts with structured vendor onboarding to establish baseline security expectations.
Here’s what this involves:
- Due diligence assessments: Vendors must provide documented evidence of their security protocols. This can include penetration testing results, certifications (like ISO 27001), and responses to structured questionnaires. The most sophisticated approaches to due diligence also assess the vendor’s controls from both “outside-in” and “inside-out” scans.
- Contractual clauses: Agreements must specify compliance with applicable NIST standards, such as 800-53 or 800-161. This ensures vendors understand their security requirements before gaining access to sensitive systems or data.
- Access controls: Vendors should only receive the bare minimum access necessary for their role—following the principle of least privilege (PoLP).
Onboarding sets the tone for vendor relationships, establishing that security isn’t optional—it’s a requirement.
Software Bill of Materials (SBOMs)
An SBOM is like the ingredient list for software. It’s a detailed inventory of all components, libraries, and dependencies within a product, and under NIST guidelines, it’s critical for reducing third-party vulnerabilities.
Vendors must:
- Provide transparent SBOMs for any software they supply, allowing organizations to identify potential risks within their digital ecosystem.
- Validate the security of included components to ensure they don’t contain known vulnerabilities, outdated libraries, or malicious code.
- Support regular updates and patches to reduce exposure to newly discovered threats.
By prioritizing SBOM compliance, vendors make it easier for organizations to spot weaknesses, enabling proactive defenses against supply chain attacks.
Risk Scoring and Monitoring
NIST compliance requires vendors to maintain transparency into their risk levels throughout the vendor lifecycle.
Here’s how it works:
- Quantitative risk scores: Vendors are often assessed on cybersecurity factors like vulnerability management, incident history, and regulatory adherence. These scores highlight their risk exposure, giving organizations an objective way to compare and prioritize vendors. Key to transparency is scoring based on open standards like FAIR-CAM (FAIR Controls Analytics Model), not black-box, proprietary models. Also key: assessing vendors based on actual risk (loss exposure) not the size of the vendor contract.
- Continuous monitoring: Meeting NIST standards means vendors can’t “set and forget” their cybersecurity protocols. Ongoing audits, vulnerability scans, and threat intelligence sharing keep everyone proactive about identifying and addressing new risks. Advanced systems now use Agentic AI to autonomously drive risk discovery and remediation, as well as discovering fourth-party “shadow” vendors.
- Incident response plans: Vendors must demonstrate readiness to handle breaches or disruptions—quickly notifying clients, containing the issue, and restoring services.
By measuring and monitoring risks regularly, vendors increase their accountability, reducing the chance of surprises down the line.
5 Steps to Implement NIST-Compliant Third-Party Risk Management
Implementing NIST third-party risk management might seem like a daunting task, but breaking it into clear, actionable steps makes it manageable. Here’s how you can ensure compliance and build a stronger, more resilient vendor ecosystem.
1. Establish Governance and Accountability
Compliance starts at the top. Define who owns third-party risk management within your organization, and set clear expectations for accountability. Create oversight committees or assign dedicated leaders—like your CISO or risk managers—to ensure compliance becomes a continuous priority.
What this looks like in practice:
- Formalize roles and responsibilities for managing vendor risk.
- Schedule regular leadership updates to monitor progress and compliance.
- Align third-party risk management with broader business goals to secure stakeholder buy-in.
When everyone knows the game plan and their role in it, compliance becomes a team sport instead of an individual struggle.
2. Develop Comprehensive Risk Policies
Think of risk policies as your playbook. A well-documented plan ensures that your entire organization evaluates vendors using consistent criteria. Develop policies that align with the NIST third-party risk management framework, covering areas like vendor selection, data handling, and incident reporting.
Key elements to include:
- Minimum security standards vendors must meet (e.g., encryption protocols, access control).
- Detailed onboarding requirements, such as assessments or SBOM submissions.
- Contingency plans for responding to third-party incidents quickly and effectively.
These policies become the backbone of your compliance efforts, offering clear instructions for every part of the vendor lifecycle.
3. Implement Risk Assessment Tools
Trying to manage vendor risks is inefficient and sets you up for mistakes. Instead, leverage risk assessment tools to automate and standardize how vendors are evaluated.
Here’s what to look for in a tool:
- The ability to quantify risk for individual vendors based on open, validated standards to identify high-priority third parties.
- Automated functionality, for instance for compliance checks, documentation gathering, and audit trails.
- Integration of reporting capabilities with third parties and centralized data dashboards that combine first- and third-party risk
For example, using platforms that map NIST 800-53 controls to your vendor evaluations eliminates guesswork and ensures nothing slips through the cracks.
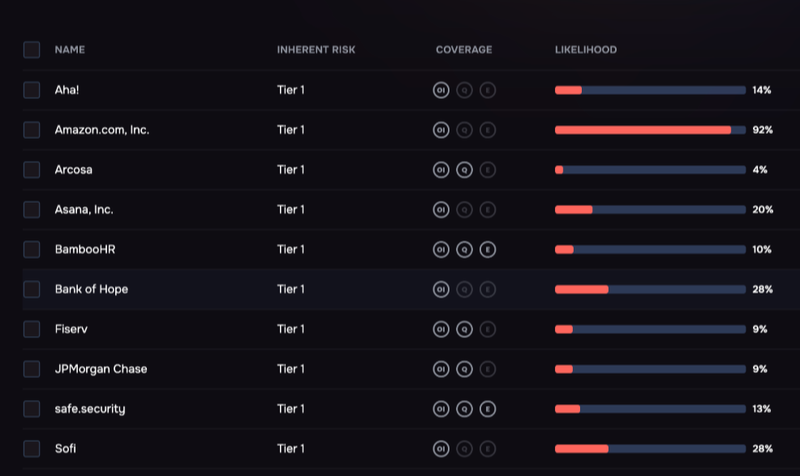
Tiering vendors based on risk, SAFE One platform
4. Conduct Ongoing Due Diligence
NIST compliance isn’t a one-and-done process. While onboarding assessments are a critical first step, ongoing monitoring is where you ensure vendors continue to meet your standards. This is especially important as vendor landscapes and cyber threats evolve.
Practical steps for due diligence:
- Continuous reviews and risk reassessments for high-risk vendors, based on their access to highly sensitive data, critical network infrastructure or core revenue-generating systems.
- Monitor vendor activities, including incident reports, reports of new cyber threats or vulnerabilities, or changes to their operational scope.
- Maintain open communication with vendors to address emerging risks in real time.
Think of this as your cybersecurity wellness check—you’re ensuring your vendor ecosystem stays healthy.
5. Automate Risk Monitoring with Technology
Today’s threats require real-time oversight, not sporadic check-ins. Automation tools add a layer of continuous protection by monitoring activity and alerting you to anomalies or vulnerabilities before they become problems.
Automation to simplify compliance:
- Use AI-powered dashboards to monitor performance and flag non-compliance.
- Implement automated notifications for key updates, like expired certifications or unresolved incidents.
- Leverage technology to track and report on compliance metrics for audits or leadership reviews.
By automating the heavy lifting, you free up your team to focus on strategic initiatives instead of hunting for red flags.
Common Challenges and How to Avoid Them
Even the most well-intentioned TPRM programs into a labyrinth of inefficiencies. Here are three frequent challenges in NIST third-party risk management—and how to tackle them head-on.
1. Overlaps That Waste Time and Effort
When teams approach third-party risk from silos, you end up with repetitive tasks. For example, one team might assess a vendor’s data privacy protocols while another reviews the same vendor’s system security—without sharing findings. Overlapping workflows create bottlenecks and leave gaps where critical risks slip through unnoticed.
How to Fix It:
- Centralize workflows. Use an integrated platform that consolidates security and compliance across departments. This reduces duplication and improves efficiency.
- Standardize assessments. Develop templates and processes grounded in the NIST third-party risk management framework, ensuring everyone starts from the same playbook.
- Facilitate collaboration. Regular cross-departmental meetings can help align priorities and eliminate redundancies.
Think of it as streamlining your orchestra so each section plays its part—without stepping on anyone else’s toes.
2. Manual Tracking That Drains Resources
If your vendor risk management (TPRM) program relies on spreadsheets, email threads, or ad-hoc systems, you’re setting yourself up for headaches. Manual tracking is time-consuming, error-prone, and unable to keep pace with evolving risks. Your team can quickly get bogged down in chasing paperwork instead of analyzing threats.
How to Fix It:
- Automate routine tasks. Automated tools handle tedious processes like onboarding documents, compliance checks, and real-time monitoring.
- Adopt dashboards. Centralized dashboards provide instant insights into vendor statuses, audit trails, and compliance metrics.
- Focus your team. With automation handling repetitive tasks, your team can focus on high-priority risks and strategic decision-making.
By letting technology take over the grunt work, you free up valuable capacity to focus on what really matters.
Scoring a vendor on the SAFE platform
3. Lack of Risk Visibility
It’s tough to protect what you can’t see. Without clear visibility into vendor risks, you’re effectively flying blind. This makes it nearly impossible to prioritize or demonstrate compliance with standards like those in the NIST third-party risk management framework. The result? Vulnerabilities that lurk undetected until it’s too late.
How to Fix It:
- Implement continuous monitoring. Technology solutions can keep tabs on vendor risks and flag issues in real-time.
- Score vendor risks. Use quantifiable scoring systems to understand the strength of a vendor’s cybersecurity controls
- Conduct frequent reviews. Regulations and risks change over time. Regularly reevaluating vendor compliance helps you stay proactive.
When you shine a light on risks with tools and consistent reviews, you prevent surprises and build trust across the supply chain.
Reducing Complexity, Increasing Confidence
By addressing these common challenges—overlaps, manual inefficiencies, and visibility gaps—you give your organization a fighting chance to reduce third-party risks effectively. Establishing streamlined processes, leveraging automation, and creating full transparency can help you stay compliant with NIST third-party risk management requirements while reclaiming your team’s time and peace of mind.
Unified Cyber + Supply Chain Risk Management Strategy
When it comes to managing third-party risks, piecemeal approaches just don’t cut it anymore. Cyber threats are evolving, and supply chains are growing more complex. That’s why integrating NIST third-party risk management frameworks—800-53, 800-161, and CSF 2.0—isn’t just a best practice; it’s essential for keeping your organization secure and resilient.
Think of it as building a bridge between cybersecurity and supply chain management. On one side of the bridge, you have detailed controls from 800-53 ensuring your vendors meet key security thresholds. On the other side, 800-161 provides a clear roadmap for managing supply chain-specific risks. CSF 2.0 ties it all together, offering a governance framework that unifies your efforts and ensures alignment with broader business goals.
This unified approach has tangible benefits:
- Stronger resilience against third-party vulnerabilities by addressing both systemic and specific risks.
- Clear compliance alignment, reducing the chances of regulatory penalties while building trust among stakeholders.
- Efficient operations through automated tools and streamlined policies that reduce manual effort and complexity.
- Improved visibility into vendor risks, so you can make proactive, data-driven decisions.
At the end of the day, a unified strategy isn’t just about checking compliance boxes—it’s about peace of mind. With the NIST third-party risk management framework, you’re not only safeguarding your data but protecting the trust that your business hinges on. By connecting the dots between cybersecurity and supply chain resilience, your organization takes a significant leap toward ensuring both stability and success.
How SAFE Supports NIST Third-Party Risk Management
Using cutting-edge automation, actionable insights, and a user-friendly platform, SAFE simplifies the complexities of NIST third-party risk management while strengthening your compliance posture. Here’s how SAFE’s key features align with NIST requirements and transform vendor risk management from a headache into a seamless process.
Automated Mappings for NIST Standards
Understanding and implementing NIST standards like 800-53, 800-161, and CSF 2.0 can feel overwhelming. SAFE cuts through the complexity with automated control mappings, instantly aligning your organization’s third-party risk management processes with NIST guidelines
Risk Quantification That Makes Compliance Actionable
SAFE introduces quantitative risk scoring, turning abstract threats into concrete numbers. Think of it like a credit score for your vendors—simple, measurable, and based on quantifiable measurement of cyber incident likelihood and impact following the FAIR Model (Factor Analysis of Information Risk), widely accepted as the standard for cyber risk quantification. Risk scores prioritize which vendors need immediate attention, letting you focus on the suppliers that pose real threats.
Dynamic Dashboards for Full Visibility
SAFE’s unified, real-time dashboards put your first- and third-party ecosystem under the magnifying glass, delivering visibility that’s often missing in traditional workflows. A centralized view of vendor compliance status, showing exactly where you stand against NIST benchmarks like SR controls and SCRM guidance.
Streamlined Vendor Onboarding and Monitoring
SAFE doesn’t just help you evaluate vendors—it makes onboarding and continuous monitoring painless. By integrating NIST third-party risk management framework requirements into AI-fulfilled workflows, it ensures vendors meet your compliance expectations from day one.
Redefining NIST Compliance with SAFE
Ultimately, SAFE bridges the gap between NIST standards and the real world of vendor risk management. It goes beyond meeting requirements—it empowers your organization to simplify processes, reduce manual workloads, and build trust across your supply chain.
See the SAFE risk management platform in action. Schedule a demo.


