Get ready for the biggest challenge to cyber and enterprise risk management
In this blog post we cover:
- Understanding the Quantum Threat
- The New Y2K: Why 2030 Is the Deadline
- The Role of AI in the Quantum Future
- The Environmental and Governance Challenge
- What You Can Do Today
- Preparing Now with the SAFE One Platform
- Resources to Learn More about Q-Day
For years, experts have speculated about the inevitable arrival of a fully-functional, large-scale quantum computer, a machine so powerful it could render our current encryption methods obsolete instantly. No, this isn’t a science fiction movie plot. Quantum computing is a very real threat to our digital world as we know it. This event, known as “Q-Day,” is no longer a distant possibility. 2030 is just around the corner, and it’s gearing up to be the new Y2K, but with far more severe consequences.
Meghan Maneval is Director, Community and Education for SAFE
Understanding the Quantum Threat
Quantum computers, unlike the classical computers we use today, leverage the principles of quantum mechanics to perform calculations. While a classical computer uses bits that can be either a 0 or a 1, a quantum computer uses “qubits” that can be a 0, a 1, or both simultaneously- a theory known as superposition. This ability to exist in multiple states at once allows them to solve certain complex problems at speeds that are incomprehensible to even the most powerful supercomputers.
The quantum threat lies in its ability to break public-key cryptography. Encryption is the foundation of modern digital security, protecting everything from online banking and e-commerce to government communications and national defense. Current public-key algorithms, such as RSA and ECC, rely on mathematical problems that are practically impossible for classical computers to solve in a reasonable amount of time. However, a quantum computer, using algorithms like Shor’s algorithm or Grover’s algorithm, could break these encryption schemes in a matter of minutes or even seconds.
This means that all our encrypted data—including confidential business information, personal records, and financial transactions—could be exposed.
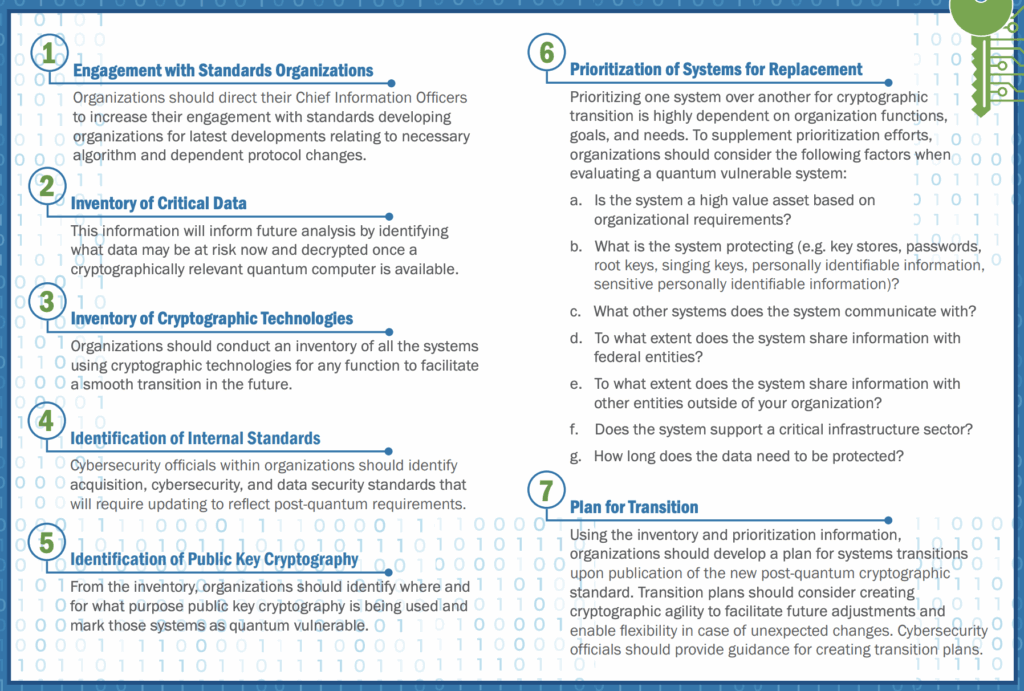
From Department of Homeland Security’s Preparing for Post-Quantum Cryptography
The New Y2K: Why 2030 is the Deadline
The Y2K scare, while it didn’t cause the widespread chaos many feared, served as a global wake-up call about the need for proactive technological preparation. While Q-Day is not a set date, experts expect it will be here before 2030. But the timeline for migrating to new cryptographic algorithms could be years. This massive impending digital transformation is a stark reminder that acting early is critical.
Preparing for Q-day is an enterprise-wide project and will require enterprise-wide effort.
The shift to Post-Quantum Cryptography (PQC) requires a massive, coordinated effort across every industry and government. It involves updating countless hardware and software systems, from routers and servers to mobile devices and smart cards. Unlike a typical cybersecurity upgrade, which might involve patching a specific vulnerability, this is a foundational change to the very fabric of our digital security. This makes it a threat not just to cybersecurity, but to the confidentiality and integrity of all our digital assets.
In addition, keep in mind that malicious actors are already harvesting encrypted data today, knowing that they can store it and decrypt it once a powerful quantum computer becomes available. This concept of “Harvest Now, Decrypt Later” makes the threat an immediate concern, not a future one.
The Role of AI in the Quantum Future
The relationship between quantum computing and artificial intelligence is a profound and symbiotic one, with each field poised to accelerate the other. Quantum computers can dramatically speed up complex AI and machine learning tasks. But this is not merely a faster version of classical computing; it’s a paradigm shift. Quantum computers, using principles like superposition and entanglement, can solve certain optimization problems and analyze vast datasets in ways that are impossible for even the most powerful supercomputers today.
This capability unlocks unprecedented opportunities for AI. For example, in the healthcare industry, quantum-enhanced AI could accurately simulate molecular interactions, leading to the rapid discovery of new medications and the design of novel materials with specific properties. In addition, quantum algorithms could optimize complex financial portfolios and perform sophisticated risk analysis with greater speed and accuracy, providing a competitive edge in a fast-paced industry. And by solving complex optimization problems, quantum AI can revolutionize supply chain management, leading to more efficient routing, reduced costs, and a smaller environmental footprint.
However, the symbiosis is a two-way street. AI is also critical to the advancement of quantum computing itself. The fragile nature of qubits, which are highly susceptible to environmental noise and errors, is a major hurdle in building scalable quantum computers. AI and machine learning can be used to help optimize the design of quantum processors, predict and correct errors in real-time, and manage the complex calibration of quantum systems. AI can even assist in translating classical code into quantum algorithms and even help discover new, more efficient quantum algorithms.
This convergence raises both exciting possibilities and serious ethical concerns. The immense power of quantum AI could widen the digital divide, concentrating power in the hands of a few wealthy corporations or nations. Additionally, if trained on biased data, quantum machine learning algorithms could amplify existing societal prejudices at an unprecedented scale.
As we move forward, a crucial dialogue is needed on data privacy, algorithmic fairness, and global governance to ensure that this powerful technology is developed and used responsibly.
The Environmental and Governance Challenge
While the technological promise of quantum computing is immense, it comes with a significant and often overlooked challenge: its environmental footprint. The massive computational power of quantum systems is not without a cost, and this cost is measured not just in dollars but in energy consumption and its associated Environmental, Social, and Governance (ESG) risks.
Quantum computers require a substantial amount of power to operate, but this is not the primary concern. The real energy drain comes from the need to maintain qubits in a stable state. This requires extreme isolation and, in many cases, cooling to temperatures near absolute zero. These cryogenic systems are incredibly energy-intensive, and as quantum computers scale, so does their power demand.
This raises critical ESG questions for organizations and governments. The push for “quantum readiness” must be balanced with a commitment to sustainable innovation. Companies that fail to address these environmental impacts could face reputational damage, increased regulatory scrutiny, and a backlash from investors who are increasingly focused on green initiatives. The ethical implications extend beyond the digital realm, impacting our physical world and contributing to the global conversation on climate change.
Addressing this challenge requires a proactive approach. The development of more energy-efficient quantum hardware and the exploration of new qubit technologies that don’t require extreme cooling will be crucial. Furthermore, organizations must integrate the environmental costs of quantum adoption into their strategic planning, ensuring that the benefits of this new technology do not come at an unsustainable price.
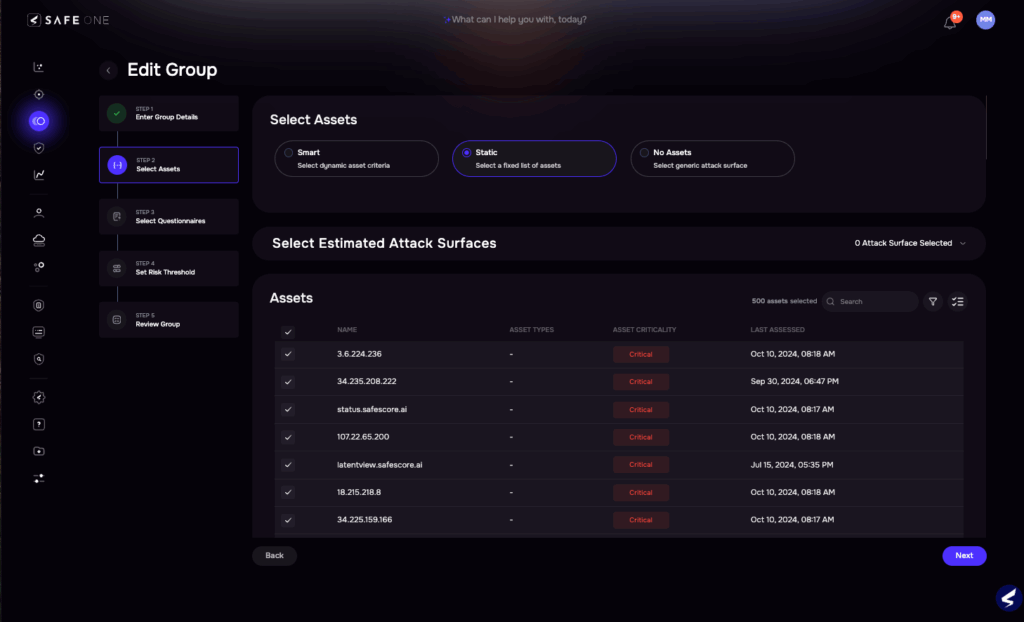
SAFE One Platform: Inventorying Cryptographic Assets at Risk
What You Can Do Today
The good news is that we are not helpless in the face of this threat. The National Institute of Standards and Technology (NIST) has worked for years to standardize new, quantum-resistant algorithms. In August 2024, NIST officially published the first post-quantum cryptography (PQC) standards, providing a clear path forward for organizations to begin their migration.
Here are some actionable steps you can take today:
- Inventory your cryptographic assets: Identify all the systems, applications, and devices that use public-key cryptography. This is the first and most crucial step in understanding your attack surface.
- Evaluate your readiness: Using a standard framework, like the NIST-CSF, evaluate your current state. If you don’t understand the scope of the challenge, you won’t know how to fix it.
- Develop a migration roadmap: Analyze the findings and develop a phased transition to PQC. This is a multi-year effort, not a “rip and replace” project, and requires a systematic approach that will take time and resources.
- Engage with vendors: Work with your technology providers to ensure their products will be PQC-compatible. They may not be already, but they should have a plan.
- Educate your team: Raise awareness about the quantum threat and the importance of PQC. This is a company-wide initiative, not just a job for the IT department.
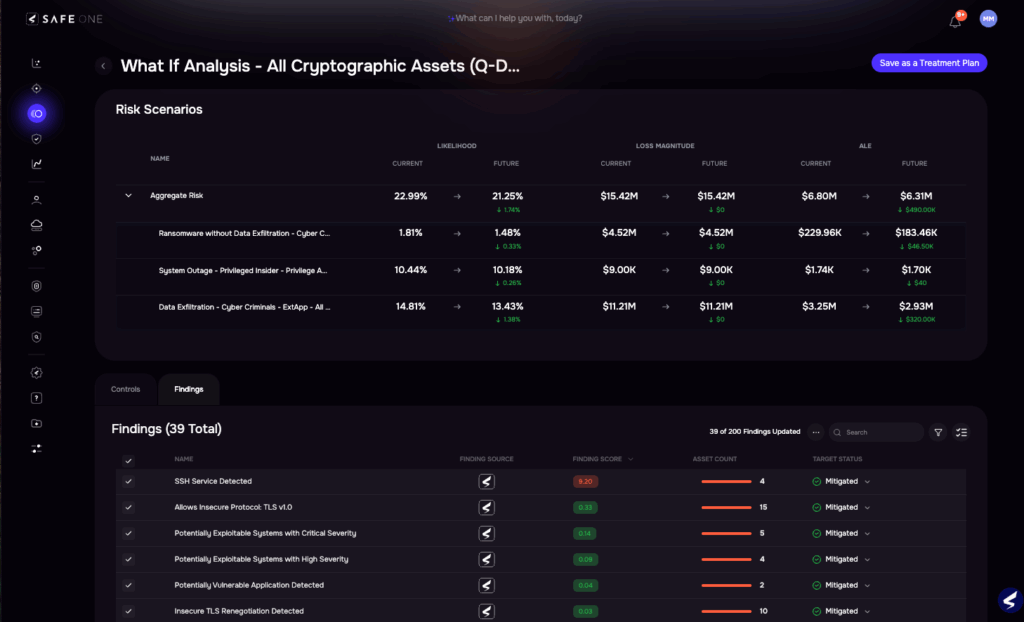
SAFE One Platorm: What-if Risk Analysis for Cryptographic Assets
Preparing Today with the SAFE One Platform
The Quantum Threat is real, but it is not a reason for panic. By understanding the risks and preparing today, you can ensure your digital future remains secure.
- Create a new group for all of your cryptographic assets. Be sure to include anything internet-facing, including servers, applications, and endpoint devices.
- Use the built-in questionnaires and suite of integrations to document your current risk posture. Remember, under “Harvest Now, Decrypt Later”, hackers may be looking to exfiltrate your encrypted data now. Or worse- they already are!
- Sit back, relax, and watch SAFE One identify your top risk scenarios and recommended actions. Create tailored risk treatment plans in phases to maintain momentum over time.
- Continuously monitor your risk for sensitive data and systems. As the threat landscape evolves, you’ll stay in the best possible position to transition to what’s next.
Learn more about how you can prepare for Q-Day
NIST Post-Quantum Cryptography Standardization: The official source for the new PQC standards. This is the definitive guide for anyone looking to understand the technical details of the new algorithms.
Post-Quantum Cryptography (DHS and NIST): A clear and concise overview of the threat from a government perspective. It highlights the national security implications and provides guidance for critical infrastructure owners.
Quantum Computing for Business Leaders (Harvard Business Review): A business-focused article that explains the strategic importance of PQC and why C-suite executives should be paying attention.
Post-Quantum Cryptography at Google: Google has been a pioneer in this space, and their blog posts offer practical insights into how a major tech company is tackling the PQC migration.
See for yourself how SAFE can enable your future with post-quantum preparation today. Schedule a demo.