2026 Guide to Third Party Risk Management (TPRM)
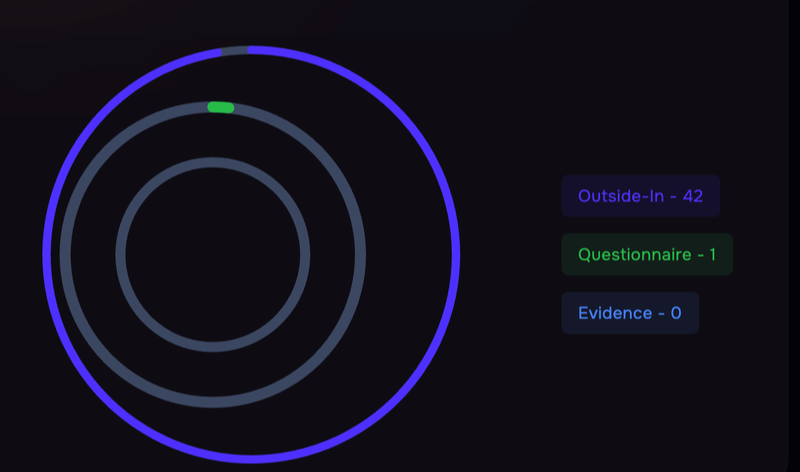
Image from SAFE TPRM platform
In this guide, you’ll find comprehensive, actionable insights into:
- Building a third-party risk management program
- Key steps for effective third party risk assessments
- Risk tiering and continuous vendor monitoring
- Aligning TPRM with regulatory frameworks
- AI automation and the future of TPRM
- Elevating your strategy with autonomous risk management
Third-party risk management (TPRM) is the systematic process organizations use to identify, assess, and mitigate risks from external vendors, suppliers, and service providers—ensuring these relationships don’t introduce cybersecurity vulnerabilities, compliance violations, operational disruptions, or reputational damage.
When Delta Air Lines’ crew-tracking software failed during the 2024 CrowdStrike outage, the airline faced an estimated $350 million loss and a Department of Transportation investigation. That single vendor issue cost Delta roughly 7% of its annual net income—a stark reminder that your vendors’ problems become your problems, often with financial consequences that show up directly on the balance sheet.
This guide covers what TPRM is, why it matters in 2026’s regulatory and threat landscape, how to build and scale a program, and how AI automation is transforming third-party risk from a compliance burden into a strategic capability.
What is third party risk management
Third-party risk management (TPRM) is how organizations identify, assess, and reduce risks that come from outside vendors, suppliers, and service providers. Think of it as a systematic way to make sure the companies you work with—your cloud providers, software vendors, payment processors, managed service providers—don’t accidentally become your biggest security problem.
A “third party” is any external organization that touches your systems, sees your data, or plays a role in your business operations. The term “vendor risk management” gets used interchangeably with TPRM, though vendor risk management typically focuses more on procurement and contracts while TPRM casts a wider net across cybersecurity, compliance, operational, and reputational risks.
TPRM covers the full relationship lifecycle: onboarding new vendors, assessing their security posture, monitoring them continuously, managing contracts, validating compliance, and eventually offboarding them when the relationship ends. It’s not a one-time checkbox exercise—it’s an ongoing program that evolves as your vendor relationships and the threat landscape change.
Why TPRM is essential in 2026
The average enterprise now relies on hundreds or thousands of third parties. Each one represents a potential entry point for attackers or a source of disruption if something goes wrong on their end.
High-profile breaches like SolarWinds and MOVEit showed how a single compromised vendor can cascade into massive incidents affecting thousands of downstream customers. When attackers compromise your vendor, they gain a trusted pathway into your environment—bypassing your perimeter defenses entirely.
Regulatory pressure has intensified. DORA (Digital Operational Resilience Act) and NIS2 (Network and Information Security Directive 2) in the EU now require financial institutions and critical infrastructure operators to demonstrate comprehensive third-party oversight. In the US, SEC cybersecurity rules mandate that public companies disclose third-party cybersecurity risks, while NYDFS requires financial services firms to conduct due diligence on critical service providers.
Traditional manual approaches can’t scale anymore. Organizations managing thousands of vendors with spreadsheets and annual questionnaires face an impossible task, which is why AI and automation have shifted from nice-to-have features to essential capabilities.
Common vendor risks and emerging threats
Third parties introduce multiple risk categories at once, often in ways that compound each other. A single vendor breach can trigger cybersecurity, compliance, operational, and reputational consequences simultaneously.
Cybersecurity risk shows up through vulnerabilities in vendor systems, weak access controls, lack of encryption, and susceptibility to ransomware.
Compliance risk arises when vendors fail to meet regulatory requirements like GDPR, HIPAA, PCI DSS, or SOC 2—exposing your organization to fines and legal liability even though the violation happened entirely within their infrastructure.
Operational risk includes vendor outages, service disruptions, and failure to deliver contracted services, like the CrowdStrike incident that affected airlines, hospitals, and financial institutions worldwide.
Financial risk involves vendor bankruptcy, fraud, or financial instability that threatens service continuity.
Reputational risk results from vendor misconduct, data breaches, or unethical practices that damage your brand by association—customers and regulators hold you responsible for your vendors’ actions regardless of contractual boundaries.
Emerging threats in 2026 include AI-powered attacks targeting vendor ecosystems, supply chain attacks exploiting trusted relationships, and deepfakes used in vendor impersonation schemes. There’s also growing concern about “nth-party risk”—the risks introduced by your vendors’ vendors, which can be nearly impossible to track without automated tools.
Vendor Inventory, SAFE TPRM
Building a third party risk management program
A TPRM program establishes a formalized, repeatable process for managing vendor risk across the entire vendor lifecycle. Success requires executive buy-in, cross-functional collaboration between security, procurement, legal, and business units, clear policies, and enabling technology.
1. Identify key vendors and suppliers
Creating a comprehensive vendor inventory is foundational—you can’t manage risks you don’t know exist. This centralized repository captures vendor names, services provided, data access levels, contract details, and risk classifications for every third-party relationship.
Gathering this information requires collaboration across procurement, IT, legal, and business units. You’ll often uncover “shadow IT” vendors—third parties that individual departments engaged without going through official channels, which frequently represent the highest risks because they’ve never been assessed.
Key data points to capture:
- Vendor contact information and legal entity details
- Services or products provided
- Data types accessed (PII, financial data, intellectual property)
- Contract start and end dates
- Business owner or sponsor
- Criticality to business operations
2. Define your TPRM framework and governance
A TPRM framework establishes the policies, procedures, roles, and responsibilities for managing third-party risk across your organization. This structured approach ensures consistency, accountability, and auditability.
Key governance elements include a TPRM policy document that defines standards and requirements, a steering committee with representatives from security, legal, procurement, compliance, and business units, and defined escalation paths for high-risk findings. Executive sponsorship and board-level reporting for high-risk vendors provide the authority and resources the program needs to function effectively.
Aligning with industry standards like NIST, ISO 27001, FAIR, and MITRE ATT&CK provides a recognized foundation and simplifies regulatory compliance. The frameworks offer proven methodologies that reduce the need to reinvent processes from scratch.
3. Develop a vendor risk management workflow
A TPRM workflow defines the end-to-end process for managing vendors from initial due diligence through contract signing, ongoing monitoring, periodic reassessment, and eventual offboarding.
The vendor lifecycle breaks down into five stages.
- Pre-contract due diligence involves risk assessment, security questionnaires, and compliance validation before any contract is signed.
- Onboarding includes contract review, access provisioning, and documentation of security requirements.
- Ongoing monitoring tracks risk in real time through continuous risk scoring, threat intelligence, and compliance checks.
- Periodic reassessment conducts scheduled reviews based on the vendor’s risk tier—critical vendors quarterly, lower-risk vendors annually.
- Offboarding securely terminates relationships through access revocation, data return or destruction, and final audits.
Workflows become repeatable and auditable when documented properly and integrated with procurement and contract management systems. This integration ensures that security and risk considerations are embedded in business processes rather than bolted on afterward.
4. Implement third party risk management tools
Manual TPRM processes collapse under the weight of hundreds or thousands of vendors. Spreadsheets, email chains, and annual questionnaires simply can’t provide the continuous oversight modern risk management demands.
TPRM platforms automate vendor inventory, risk assessments, continuous monitoring, and reporting. Key capabilities include centralized vendor data repositories, automated questionnaire distribution and response collection, integration with external threat intelligence and security rating services, continuous monitoring of vendor security posture and compliance status, workflow automation for assessments and remediation tracking, and dashboards for executives and auditors.
SAFE TPRM uses Agentic AI to autonomously handle vendor onboarding, assessment, and continuous monitoring—reducing manual effort by up to 90% while scaling coverage to thousands of vendors without adding headcount.
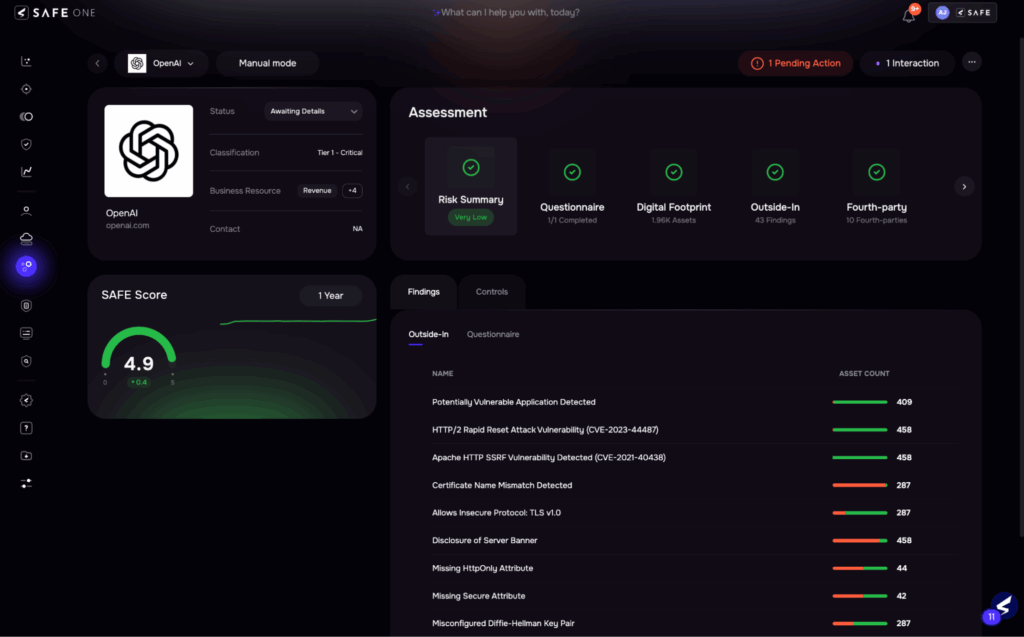
Vendor risk assessment, SAFE One platform
Key steps for effective third party risk assessments
A third-party risk assessment evaluates a vendor’s security controls, compliance posture, operational resilience, and financial stability to determine the level of risk they introduce. Assessments follow a risk-based approach: high-risk vendors undergo rigorous evaluation while low-risk vendors receive lighter-touch reviews.
1. Gather vendor data and contracts
The first step involves collecting comprehensive information about the vendor: legal entity details, services provided, data access requirements, subcontractors, geographic locations, and existing certifications like SOC 2 or ISO 27001. This data collection typically happens through standardized intake forms or questionnaires during vendor onboarding.
Contract review is equally critical. Security and compliance clauses, liability terms, data handling requirements, breach notification obligations, and audit rights all shape your risk exposure and remediation options when issues arise.
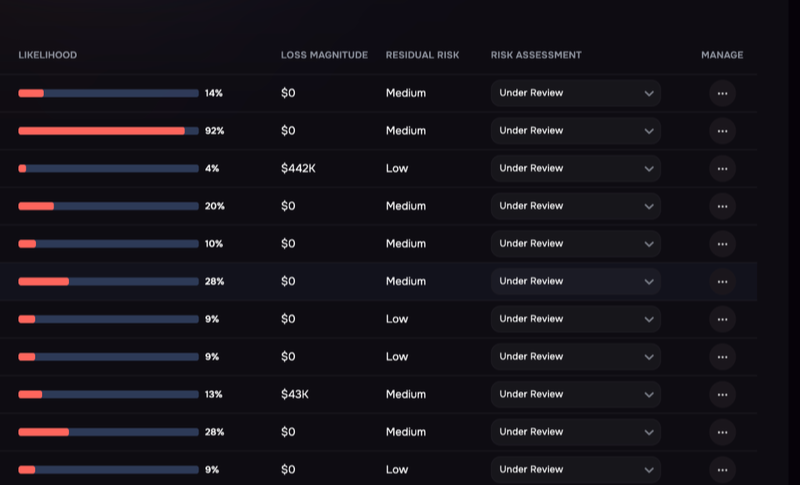
2. Perform risk scoring and tiering
Risk scoring assigns a rating to each vendor based on factors like data sensitivity, criticality to operations, security posture, compliance status, and financial health. This scoring enables “risk tiering” or “vendor segmentation”—categorizing vendors into tiers that determine assessment rigor and monitoring frequency.
Critical (Tier 1) vendors have access to highly sensitive data or business-critical systems and require comprehensive assessments, on-site audits, penetration test results, and continuous monitoring.
High (Tier 2) vendors with moderate data access or operational impact receive detailed questionnaires, compliance validation, security ratings, and quarterly monitoring.
Medium (Tier 3) vendors with limited data access undergo lightweight questionnaires, certifications reviews, and semi-annual or annual assessments.
Low (Tier 4) vendors with no data access or minimal business impact receive basic due diligence, contract review, and annual or event-triggered reviews.
Risk scoring considers both inherent risk (the risk posed by the vendor’s role and data access) and residual risk (the risk remaining after controls are applied).
3. Document findings and assign ownership
Assessment findings require documentation in a centralized system: identified risks, control gaps, compliance issues, and remediation recommendations. This documentation becomes your audit trail for regulatory and internal audit purposes.
Assigning ownership for each risk or finding is essential—typically to the business unit sponsoring the vendor or the vendor relationship manager. Owners track remediation progress, verify closure, and maintain accountability for risk acceptance decisions.
4. Schedule ongoing review and audit
Vendor risk isn’t static—security postures change, new vulnerabilities emerge, and business relationships evolve. Assessments repeat on schedules aligned with vendor risk tiers: critical vendors quarterly, high-risk vendors semi-annually, medium and low-risk vendors annually.
Reassessment triggers also include vendor breaches or security incidents, material changes in services or data access, vendor acquisitions or mergers, and new regulatory requirements.
Risk tiering and continuous vendor monitoring
Continuous monitoring tracks vendor risk signals in real time or near-real time: security ratings, threat intelligence, compliance status, financial health, and operational incidents. This approach replaces static annual assessments with dynamic, always-on oversight that detects emerging risks before they become incidents.
1. Classify vendors by criticality and exposure
Risk tiering forms the foundation for continuous monitoring—critical vendors receive the most intensive monitoring while low-risk vendors may only need periodic checks. Classification considers both criticality (business impact if the vendor fails) and exposure (your attack surface or data exposure through the vendor).
Examples of critical vendors include cloud infrastructure providers, payment processors, ERP systems, and managed security service providers.
2. Use automated third party risk monitoring
Automated monitoring tools continuously collect and analyze risk signals from multiple sources: security rating services like SecurityScorecard, BitSight, and RiskRecon; threat intelligence feeds; dark web monitoring; financial data providers; compliance databases; and vendor self-reporting. The tools generate dynamic risk scores that update in real time as new information becomes available.
Integration with SIEM, SOAR, and GRC platforms enables automated alerting and workflow triggers, connecting monitoring insights directly to response and remediation processes.
3. Track changes and trigger alerts in real time
Continuous monitoring systems generate alerts when risk scores cross thresholds, new vulnerabilities are disclosed, security incidents occur, compliance certifications lapse, or financial health deteriorates. Alert prioritization and routing ensure the right stakeholders receive timely notifications: critical alerts escalate to security or risk teams immediately while lower-priority alerts queue for periodic review.
Integration with incident response and vendor management workflows—with predefined playbooks for containment, communication, and remediation—transforms alerts into action. Without this integration, alerts become noise that teams ignore.
Aligning TPRM with regulatory frameworks
Regulators worldwide now mandate third-party risk oversight as part of broader cybersecurity and operational resilience requirements. Organizations demonstrate compliance by showing they’ve identified critical vendors, assessed their risks, implemented appropriate controls, and continuously monitor vendor performance.
>>DORA (Digital Operational Resilience Act) requires EU financial institutions to manage ICT third-party risk, including contract terms, exit strategies, and concentration risk.
>>NIS2 (Network and Information Security Directive 2) mandates supply chain risk management and vendor security for EU critical infrastructure sectors.
>>SEC Cybersecurity Rules require U.S. public companies to disclose cybersecurity risk management, including third-party oversight.
>>NYDFS Cybersecurity Regulation requires New York financial services firms to conduct third-party service provider risk assessments and due diligence.
NIST Cybersecurity Framework offers a voluntary framework including supply chain risk management.
>>ISO 27001/27002 provides international standards for information security management, including supplier relationship controls.
>>GDPR requires data processors (third parties) to maintain adequate security and notify controllers of breaches.
Compliance requires documented policies, risk assessments, vendor contracts with security and compliance clauses, audit trails, and regular reporting to regulators or boards.
AI automation and the future of TPRM
Traditional TPRM approaches—manual questionnaires, annual assessments, spreadsheet tracking—can’t scale to meet the demands of modern vendor ecosystems. Organizations now manage hundreds or thousands of third parties, and the volume of risk data overwhelms manual processes.
1. Agentic AI and rapid risk insights
Agentic AI refers to AI systems composed of specialized agents that autonomously perform tasks like data ingestion, risk scoring, vendor assessment, anomaly detection, and reporting. The agents process vendor data from multiple sources—questionnaires, security ratings, threat intelligence, financial reports—in real time, generating risk scores, identifying control gaps, and recommending remediation actions without human intervention.
This automation reduces manual effort, increases coverage, and accelerates time-to-insight. SAFE’s Agentic AI system uses over 25 specialized AI agents to autonomously handle vendor onboarding, assessment, continuous monitoring, and natural language reporting—enabling organizations to manage thousands of vendors without adding headcount.
2. Integrating cyber risk quantification
Traditional TPRM relies on qualitative risk ratings (high, medium, low) or abstract risk scores that lack financial context. Traditional TPRM relies on qualitative risk ratings (high, medium, low) or abstract risk scores that lack financial context. Cyber Risk Quantification (CRQ) translates vendor risk into dollar terms, enabling organizations to understand the potential financial loss from a vendor breach or failure.
SAFE TPRM integrates with SAFE CRQ to calculate the expected financial impact of vendor risks using the FAIR (Factor Analysis of Information Risk) model. This financial quantification allows organizations to prioritize vendors based on actual financial exposure rather than subjective ratings.
3. Planning for emerging compliance and AI governance
As vendors increasingly adopt AI and machine learning, organizations face new risks: bias in AI models, lack of transparency (black-box algorithms), data privacy violations, and regulatory compliance with frameworks like the EU AI Act. TPRM programs evolve to include AI governance criteria, evaluating vendors’ AI use cases, data sources, model risk management, and transparency practices.
Elevate your TPRM strategy with autonomous risk management
Third-party risk management has evolved from a compliance checkbox into a business imperative driven by regulatory mandates, cyber threats, and operational dependencies. Organizations moving beyond manual, point-in-time assessments to continuous, automated, and financially quantified TPRM programs gain strategic advantages.
Traditional TPRM has clear limitations: manual processes can’t scale, static assessments miss emerging risks, and qualitative ratings fail to communicate business impact. The future of TPRM is autonomous, AI-powered, and integrated with broader cyber risk management.
About SAFE and Third-Party Risk Management
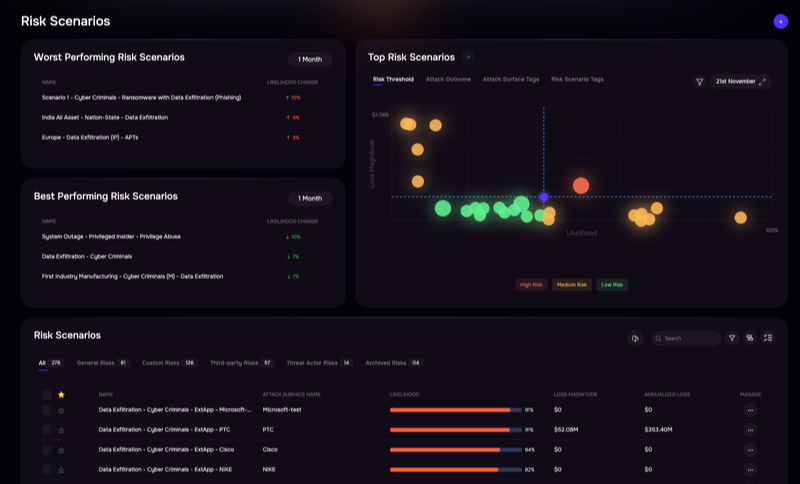
Cyber risk quantitative analysis, SAFE CRQ platform
SAFE TPRM is the industry’s only fully autonomous TPRM solution powered by Agentic AI. It automates vendor onboarding, assessment, and continuous monitoring, reducing manual effort by up to 90%. Vendors are prioritized based on actual cybersecurity risk and potential financial loss, not arbitrary ratings. Integration with SAFE CRQ and SAFE CTEM provides a unified view of enterprise, third-party, and exposure risk.
Request a demo to see how SAFE can transform your TPRM program with autonomous risk management.



