5 First Steps for a New CISO
Position yourself as a key player in your organization’s business strategy.

Congratulations on your new CISO job. More than a job, it’s a calling to defend the organization on the front lines of cybersecurity, in one of the greatest struggles of our time. You’ll have an opportunity to rebuild the security infrastructure organization, be a respected member of the management team consulted by the board of directors, and most likely, get the budget you need. Oh, and at any time you could lose your job for a major security failure – and perfect security is impossible to achieve.
At SAFE, we’ve had the good fortune to work with many successful CISOs, and here’s what we’ve heard are some first steps you can take to lay the groundwork for a great experience as a Chief Information Security Officer:
1. Understand the key sources of business value
It sounds obvious, but security priorities ultimately grow out of the need to keep the cash flowing. What are the applications, platforms, customer databases, intellectual property or other crown jewels that are critical to the continuing profitable operation of the business? To put it another way, your job is to protect the business from material harm from a cyber event – so know where a cyber event would cause the most harm.Whether from high frequency of occurrence, high magnitude of impact, susceptibility to attack of controls, or other factors, there’s a pack of more probable, more expensive risks lurking out there in cyberspace that you need to know because they will help shape your security strategy. SAFE can help. Our SAFE One platform guides you to identify your most important assets and the relevant risk scenarios for each. We leverage the FAIR model to scope, contextualize and quantify risk scenarios to identify the most likely cyber risk loss events, including ransomware, business email compromise and more. You’ll get a bird’s eye view of enterprise risk posture or go granular for insights at an asset- or business-unit level.
2. Understand the threat environment
The organization’s previous experience with cyber events – and what they read about cyber events at their peers – will condition the current expectations of the business leaders. You should be well-informed and ready to discuss:
- Global cyber-related financial and data losses
- New cyber breaches and lessons learned
- Trends in ransomware, zero-day attacks, and new attack patterns
- Cyber threat trends from ISACs (information sharing and analysis centers), MITRE Enguity, CISA or other sources
But know this: The SAFE One platform empowers you to be the authority on your organization’s threat environment, with up to the minute, automated telemetry from your attack surface mapped to the MITRE ATT&CK tactics and techniques. You’ll get play-by-play insight into known and trending data breaches most relevant to your business plus an assessment of how well you stack up against your peers.
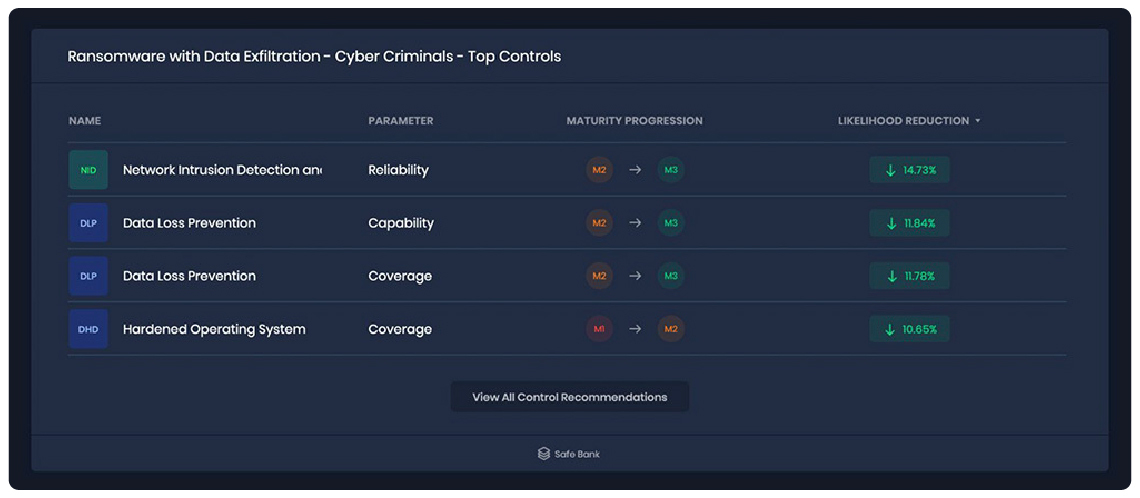
3. Understand the current portfolio of cybersecurity controls
You’ve been left a legacy controls stack; now, dig in and determine which pull their weight in risk reduction and which could be deleted. The SAFE One platform ingests and analyzes your controls stack following the revolutionary FAIR Controls Analytics Model (FAIR-CAM). You’ll gain unprecedented, automated insight into the effectiveness of a single control or controls systems to reduce risk – not just the presence or absence of controls that typical “maturity” ratings provide. Confidently build your cybersecurity investment strategy with a quantified view of your cyber risk appetite and loss exposure. Know that your controls environment is constantly assessed against a changing threat environment to alert you to prioritize controls you may lack.
4. Understand how cybersecurity and risk management fit into the broader organization
Direct and dotted lines of reporting, of course, tell you a lot: How does your job connect to the CEO, CFO, CIO, Chief Risk Officer, Chief Compliance Officer, etc.? How has cyber risk management been incorporated into enterprise risk management (or not)? Who gives direction on risk appetite and other policies and governance? What about Board reporting – Audit Committee, Risk Oversight Committee, IT Oversight Committee? What are the regulatory requirements that will often jump to the head of the line for your project list? With SAFE One, you are always ready to report to business management or the Board in terms they will best understand: cyber risk quantified in financial terms and, displayed through dashboards customized to their requirements.
5. Understand what’s coming around the corner

Every large enterprise is undergoing rapid change and disruption, whether via digital transformation, artificial intelligence, competitive shifts and more – and you need to quickly get on board with the initiatives and investments that disruption has triggered before they accelerate out of reach – they could be new products, new third party vendors or M&A. SAFE One users get total flexibility in risk scenario creation to anticipate a changing risk landscape. With FAIR analysis automation – and AI capabilities – the SAFE One platform empowers cybersecurity to move at the speed of business.
Follow these five steps to start on solid footing – and then stay nimble because the ground is sure to shift. We built our SAFE One platform in close coordination with CISOs; they told us in no uncertain terms that they need a supporting platform that could quickly pivot to meet new and unforeseen risk scenarios but would always be based on defensible data and models such as FAIR and MITRE ATT&CK. We strive to meet their expectations.
Contact us to see how SAFE can partner with you on your CISO journey.



