6 Types of Vendor Risks and Loss
As the supply chain goes digital, your attack surface broadens to include your business partners.
Vendor risk management is essential to maintaining a secure and resilient organization. CISOs and cyber risk managers must effectively identify and mitigate third-party cyber risks (TPRM) to protect business operations, data, and reputation.

As the supply chain across industries goes digital, the effective attack surface of organizations broadens out to include their business partners. Attackers are on top of this trend, carefully mapping, and then targeting the key strategic nodes that could cause the most disruption.
Some 2024 examples:
- The ransomware attack on Change Healthcare, the main processor of medical payments in the US, disrupted every hospital in the country.
- Car dealer software-as-a-service provider CDK Global was hit by a massive cyberattack, causing the company to shut down its systems and leaving 15,000 dealerships unable to operate normally.
Let’s take a closer look at the different types of vendor risk and loss exposure, why they’re critical to monitor, and strategies for managing them effectively.
What Is Vendor Risk?
Vendor risk refers to the potential risks introduced to your organization through its third-party vendors and suppliers. These risks arise from the products, services, or systems that vendors provide, which can expose your business to their vulnerabilities.
The long list of commonly outsourced business functions includes:
- data storage
- ecommerce
- billing and payments
- customer service/help desk
- HR and payroll
- manufacturing of product components
Modern businesses integrate extensively with vendors for operational efficiency, which also creates potential avenues for data breaches, compliance violations, reputational risks, and operational disruptions. Assessing and managing the resulting risks becomes imperative for enterprises of all sizes but particularly large organizations that may have thousands of vendors, many that could be single points of failure in the event of a cybersecurity attack or IT outage.
Why Is Vendor Risk Management Critical for Your Business?
Vendor relationships, while vital, form part of your extended enterprise ecosystem. That means their vulnerabilities can quickly become yours. Failing to monitor and manage vendor risk can expose your organization to significant consequences, such as:
1. Data Breaches: Your vendor could have poor cybersecurity practices or good practices and still be a target for an overwhelming advanced persistent threat (APT) actor. Either way, your sensitive information could be at risk.
2. Regulatory Non-Compliance: Vendors that don’t adhere to relevant compliance frameworks could ultimately result in penalties for your business. Regulators now take the view (as expressed in the 2023 guidance document from the US banking authorities) that “the use of third parties does not diminish or remove banking organizations’ responsibilities” for information security.
3. Reputation Damage: Missteps from a vendor (such as unethical practices or system failures) may lead to brand erosion and ultimately financial loss. An International Monetary Fund study found evidence of customers pulling deposits from banks after cyber attacks.
4. Operational Downtime: Vendor failures can disrupt your supply chain, critical systems, or customer services. The infamous ransomware attack on Colonial Pipeline disrupted fuel shipments to 17 states and the District of Columbia for six days.
Investing in vendor risk management not only aligns with a proactive security strategy but also helps uphold trust with stakeholders, partners, and customers.
Learn More:
Download the TPRM Program Blueprint: Your Guide for Transforming Third-Party Risk Management
6 Key Types of Vendor Risks and Losses
Monitoring vendor risk requires dissecting it into distinct categories. Each type carries its own challenges and demands specific mitigation tactics. Here are the primary types of vendor risk scenarios and resulting impacts you should monitor:
1. Cybersecurity Risks
Cybersecurity risk arises from vulnerabilities introduced by a vendor’s lack of adequate security controls or practices. These could lead to risk scenarios for data breaches, unauthorized access, or malware infections.
For example, a misconfigured vendor system could provide attackers with a pathway to infiltrate your organization’s network. A misconfigured web application firewall, managed by a third-party cloud provider, led to the exposure of personal information of over 100 million customers of banking giant Capital One.
2. Compliance Violations
This refers to a vendor’s failure to comply with relevant regulatory or industry-specific standards, such as GDPR, HIPAA, or ISO certifications. If your vendor breaches compliance, and faces regulatory action, your organization could in turn face hefty fines or legal costs.. For instance, healthcare organizations are liable for the HIPAA violations of their business associates.
3. Operational Risk
Operational risks arise when a vendor fails to deliver products or services reliably, leading to revenue loss or legal liability. Examples include delays in supply chains, outages caused by vendor system failures, or substandard service delivery. The notorious WannaCry ransomware attack of 2017 left cargo ships stuck at sea at the international shipping company Maersk, resulting in $300 million in lost revenue.
4. Reputation Loss
Vendors that engage in unethical business practices, face negative media attention, or have poor public relations management could harm your company’s reputation simply by association, leading to loss of customers or investors. After it was revealed in 2018 that Facebook had shared personal information of its users with Cambridge Analytica that the software vendor used to target political advertising, a “Delete Facebook” movement started, and the company’s shares lost 19% in value in a day.
5. Strategic Risk
This pertains to misalignment between the vendor’s strategies and your organization’s goals. If a vendor fails to adapt to changing technologies or market demands, it may impact your long-term success. The massive shift by organizations to AI has kicked off a widespread reappraisal of AI use at third parties from a security point of view.
6. Financial Loss
Any of the above risks can generate substantial financial loss, both as direct or indirect costs. But consider that loss exposure due to vendors may be mitigated by other factors: cyber insurance and any provisions for indemnification in the enterprise’s contract with the third party vendor.
Effective Strategies for Monitoring and Managing Vendor Risk
Proactive management of vendor risk is not a one-off task—it’s a continuous process requiring a systematic approach geared to the vastly expanded nature of the threat.
Standard operating procedures for TPRM fall far short of that mark. The common practices are
- Cybersecurity rating services that score a vendor based on a partial, outside-in scan of controls and unverifiable, black-box methodologies.
- Questionnaires, that are comprised of 150- 200+ questions that vendors are required to self-attest and update typically only once a year
- Framework compliance reports, mapping a vendor cybersecurity program against a standard framework of controls, often self-reported
Here are best practices to successfully ramp up a TPRM program that isn’t just spray and pray but actually works to your advantage in reducing third-party cyber risk.
Conducting Vendor Risk Assessments
Develop and distribute structured risk assessment questionnaires to your vendors to evaluate their: security postures
- Security postures
- Compliance with controllframeworks
- Top risks and overall risk levels
These assessments should include inquiries about their data protection protocols, incident response plans, and certifications.
Some key distinctions of the best practices vs. common practices in third-party risk assessments:
- Risk-based approach to TPRM: Tier vendors based on 1) the business resources they touch and 2) FAIR quantitative analysis for likelihood and impact of risk they could pose. Allocate attention among vendors accordingly.
- An outside-in and inside-out scan of controls for the most complete view (ideally, requires cooperation from the third party and a shared risk management platform).
- Automated (through AI) ingestion and logging of questionnaires (goal: make it easy on the vendors to encourage cooperation).
- Prioritized focus on only the most relevant controls for third-party risk at the vendor – and zero trust controls on the enterprise side to limit access of third parties to critical functions or data.
Implementing Continuous Risk Monitoring
Continuous monitoring involves leveraging advanced tools and platforms to receive real-time updates on your vendors’ risk profiles. Monitor for security incidents, compliance violations, control outages or operational disruptions that could affect your business. See emerging threats that could impact your vendors and the shifting lineup of top TPRM risks.
Automated platforms, like those offering continuous security ratings or continuous controls monitoring (CCM), are invaluable for providing actionable intelligence and keeping your risk management efforts agile.
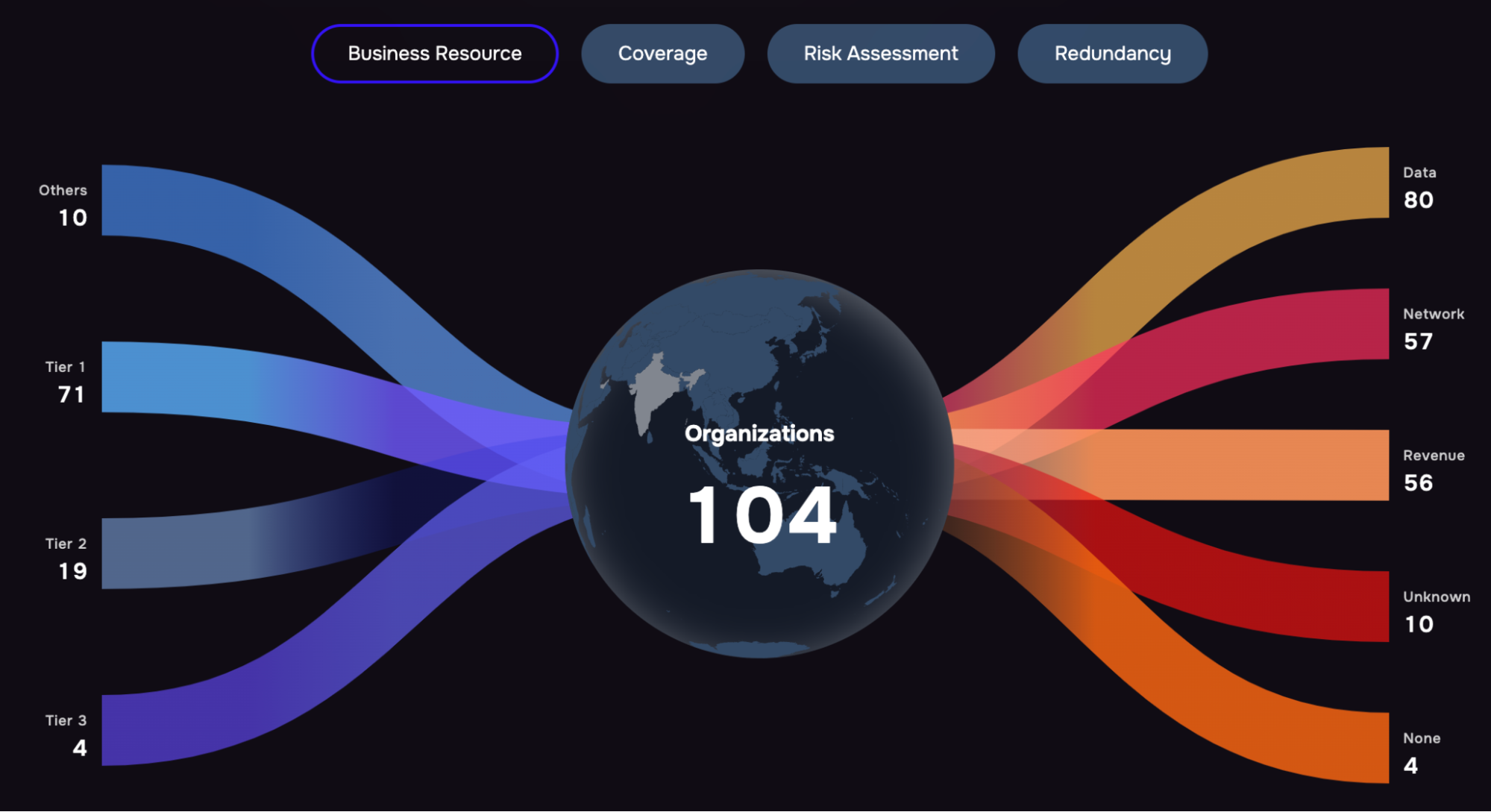
Continuous monitoring of vendors with the SAFE One platform
How SAFE Can Help You Manage Vendor Risks
Effective vendor risk management can feel overwhelming, given the size and complexity of vendor ecosystems. SAFE believes that Third-Party Risk Management must evolve to become an integral part of the organization’s overall cyber risk strategy, managed from a unified approach.
SAFE for TPRM is the industry’s only AI-powered TPRM solution that empowers third-party risk leaders to quantify and manage third-party cyber risk continuously with high automation and scalability. It combines cyber risk quantification with the advantages of outside-in security ratings, questionnaire-based assessments, inside-out scans and zero-trust control recommendations.
Start building a resilient and secure vendor ecosystem today.
Connect with our team to learn more about how SAFE for TPRM can help you protect your enterprise.



