A Day in the Life of a SAFE CISO
Practicing proactive cyber risk management, anytime, anywhere
By Patrick Lee
SAFE One, the SAFE cyber risk management platform, aggregates data from over 100 security products to provide a real-time, 360-degree view of an organization’s cyber risk posture that includes a unified view of first- and third-party risk, what-if analysis for remediation, peer insights to benchmark risk management performance and many other features.
But it gets better. The SAFE X mobile assistant makes SAFE One’s functions available at a CISO’s fingertips, with natural language interaction via GenAI to not just monitor risk posture but take action to respond any time, anywhere.

Let’s follow one of our CISO customers for a look at how a day with SAFE One and SAFE X plays out.
5:15 am – Before Leaving for Office
CISO checks phone and sees a push notification from the mobile app about a recent cyber attack headline – it’s an industry peer. SAFE noticed the vulnerability in their environment so CISO opens up the app and navigates to “Known Hacks” feature – SAFE has already quantified the risk scenario in terms of % breach likelihood and $ impact.
8:00 am – Driving to the Office
While driving, CISO thinks of the upcoming meeting with the CIO later this afternoon to discuss top risks. Through the GenAI assistant within SAFE’s mobile app, CISO asks, “What are my top risks?” and the virtual assistant fetches the answers – aiding CISO in mentally preparing a narrative.
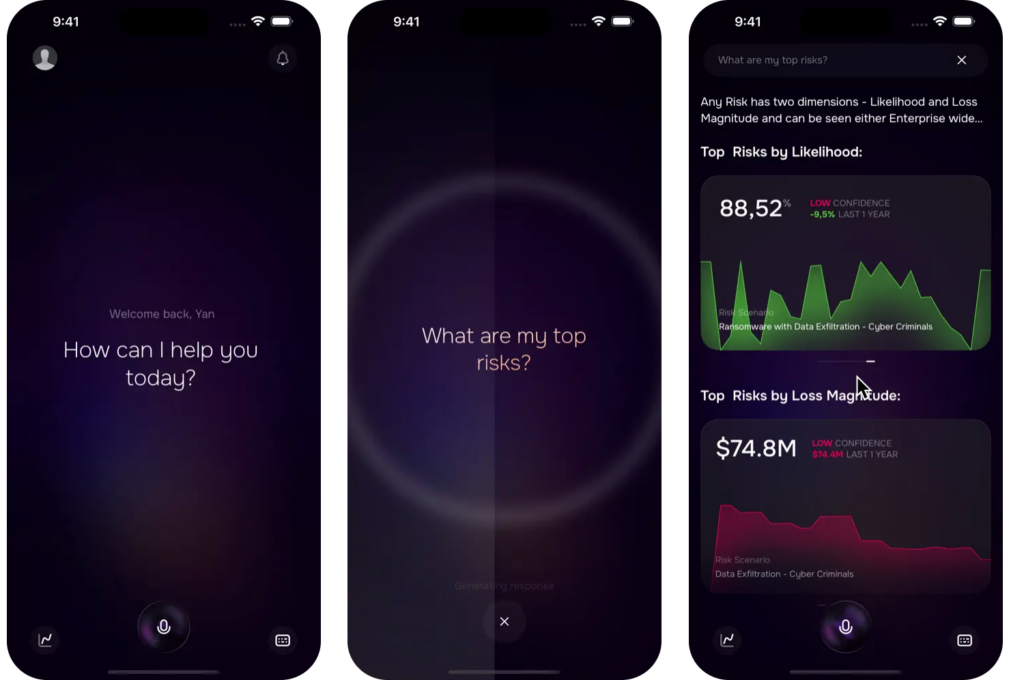
8:30 am – Reached Office
CISO opens up laptop but instead of diving into a dashboard full of overwhelming data points, CISO logs into a personalized SAFE One dashboard to quickly see how risks are changing at the organization – and WHY – in near real-time.
1:00 pm – Lunchtime
While meeting with the broader business stakeholders, CISO uses this time to pull up a dashboard in SAFE that’s configured to showcase risk trends across major digital transformation initiatives. CISO shares a few options for risk treatment that compare risk reduction of % likelihood/$ impact vs. the costs to implement and asks if the current levels are “acceptable.” The business walks away impressed and appreciates that cybersecurity isn’t a barrier to innovation.
1:45 pm – Post Lunch CIO Meeting
CISO walks through the platform’s personalized CIO dashboard to share an update on the company’s top risks. With a recent acquisition, CISO informs CIO about how the acquired company doesn’t meet the required cybersecurity standards and pose a significant risk of over $100M if nothing is done. CISO asks for additional 2025 budget in order to secure the acquired company while highlighting how risk could be burned down to sub-$20M as a result. Approved.
As the meeting concludes, CIO asks CISO about his/her thoughts on a new third-party vendor the IT team is thinking about bringing on to support eCommerce. CISO pulls out the SAFE X mobile app and asks the mobile assistant to “Add [X Company Name] as a new vendor.” SAFE’s app automatically adds the vendor and begins conducting an outside-in scan and populates risk assessments. Within minutes, CISO tells CIO, “Looks like potentially up to $3M in loss exposure. I’d ask for them to increase their limits of liability to match.”
4:00 pm – Exec Meeting
While meeting with the C-Suite, everyone just wants to know whether the org is in danger of suffering the same attack that just happened to their competitor which is all over the news. CISO pulls up the same “Known Hacks” module from earlier this morning to help everyone understand where they are and the major gaps that the team is working on shoring up.
6:00 pm – Quitting Time (at the office, anyway)
Heading home with SAFE X by the CISO’s side, confident in the knowledge that AI constantly monitors the environment and will alert when a risk scenario goes over a threshold, a new hack is reported or other important developments occur – and suggest preventive actions.
How’s your day going? Contact us for a demo and see how SAFE could make it much better.



