Automating FAIR: How SAFE Gives CISOs Real-Time Control of Cyber Risk
Taking the standard for quantitative risk analysis from theory to action
By Sachin Jha
Why FAIR Was Established
The digital world is filled with complexities, and with the ever-evolving threat landscape, organizations needed a structured way to understand and quantify their cyber risks. Enter FAIR (Factor Analysis of Information Risk), a game-changing model designed to help businesses move beyond vague and subjective assessments of cyber risk.
FAIR brought a much-needed level of clarity to risk management. Instead of guessing how likely a cyber event might be or how much it would cost an organization, FAIR gave a formula—a standardized way to translate cyber risks into financial terms. This shift allowed organizations to speak a language that boards, executives, and other stakeholders could understand: dollars and cents.
The goal was simple: help decision-makers understand the likelihood of risks and how much those risks could cost the business, enabling better, more informed choices on where to invest in cybersecurity.
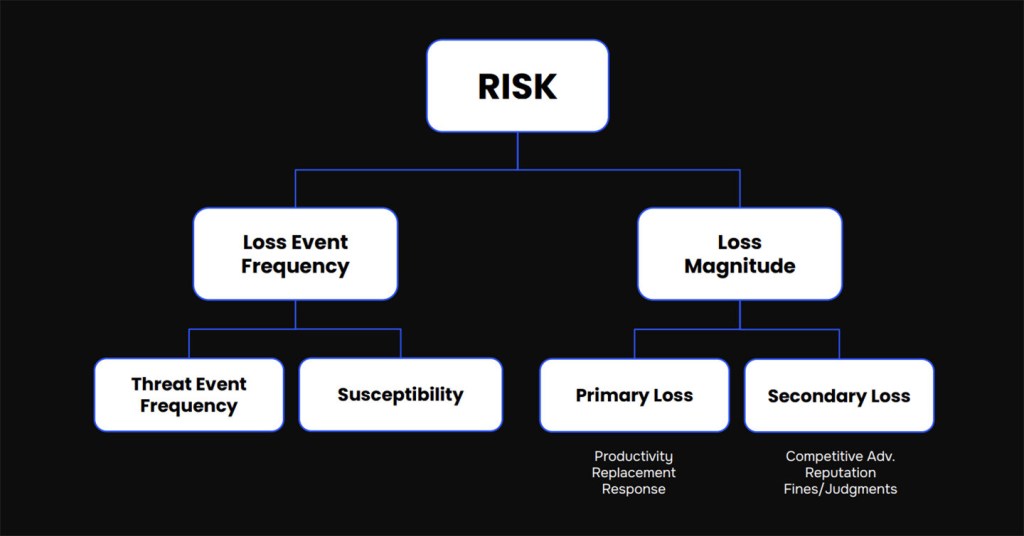
The Problems with Traditional FAIR Implementations
While FAIR was revolutionary in theory, its practical implementation presented several challenges. Organizations quickly realized that the model, while robust, was difficult to operationalize manually.
Here are some key problems with traditional FAIR implementations:
- Manual, Labor-Intensive Process:
To quantify risks using FAIR, cybersecurity teams often relied on spreadsheets and manual data entry. This process was time-consuming and required extensive expertise. - Static Risk Assessments:
Traditional FAIR implementations often resulted in static, point-in-time risk assessments. Once risks were calculated, the process would need to be repeated if new data or threats emerged. - Scalability Issues:
As organizations grow, so do their risks. Scaling FAIR across a large enterprise, with various departments, systems, and third-party vendors, proved to be a major hurdle. Many organizations found it difficult to apply FAIR’s principles consistently across multiple entities.
These challenges highlighted the need for a more efficient, scalable, and dynamic way to implement FAIR—one that could adapt to an organization’s changing risk landscape in real time.
The Need for a Fundamental Reboot – What Is FAIR Automation?
FAIR’s principles were sound, but the framework needed a reboot to keep pace with modern cyber risks and technologies. To fully realize the power of FAIR, it needed to evolve from a model run by a few experts on spreadsheets into a dynamic, automated process.
FAIR automation transforms the traditional FAIR model into a dynamic, real-time system that continuously ingests threat data, control performance, and loss information to provide accurate risk assessments. By automating this process, organizations can instantly quantify both the probable frequency of cyber events and the potential magnitude of losses in financial terms—essential for business decisions.
This is where SAFE, with the SAFE One platform, steps in, transforming FAIR from a static model to a powerful, automated engine for real-time cyber risk quantification.
“The fact that SAFE is embedding the community adopted and trusted FAIR model into the SAFE One platform with an engineering and automation-first approach, coupled with generative AI, makes SAFE the absolute market leader in cyber risk quantification.” – Michael Montoya, CISO at Equinix
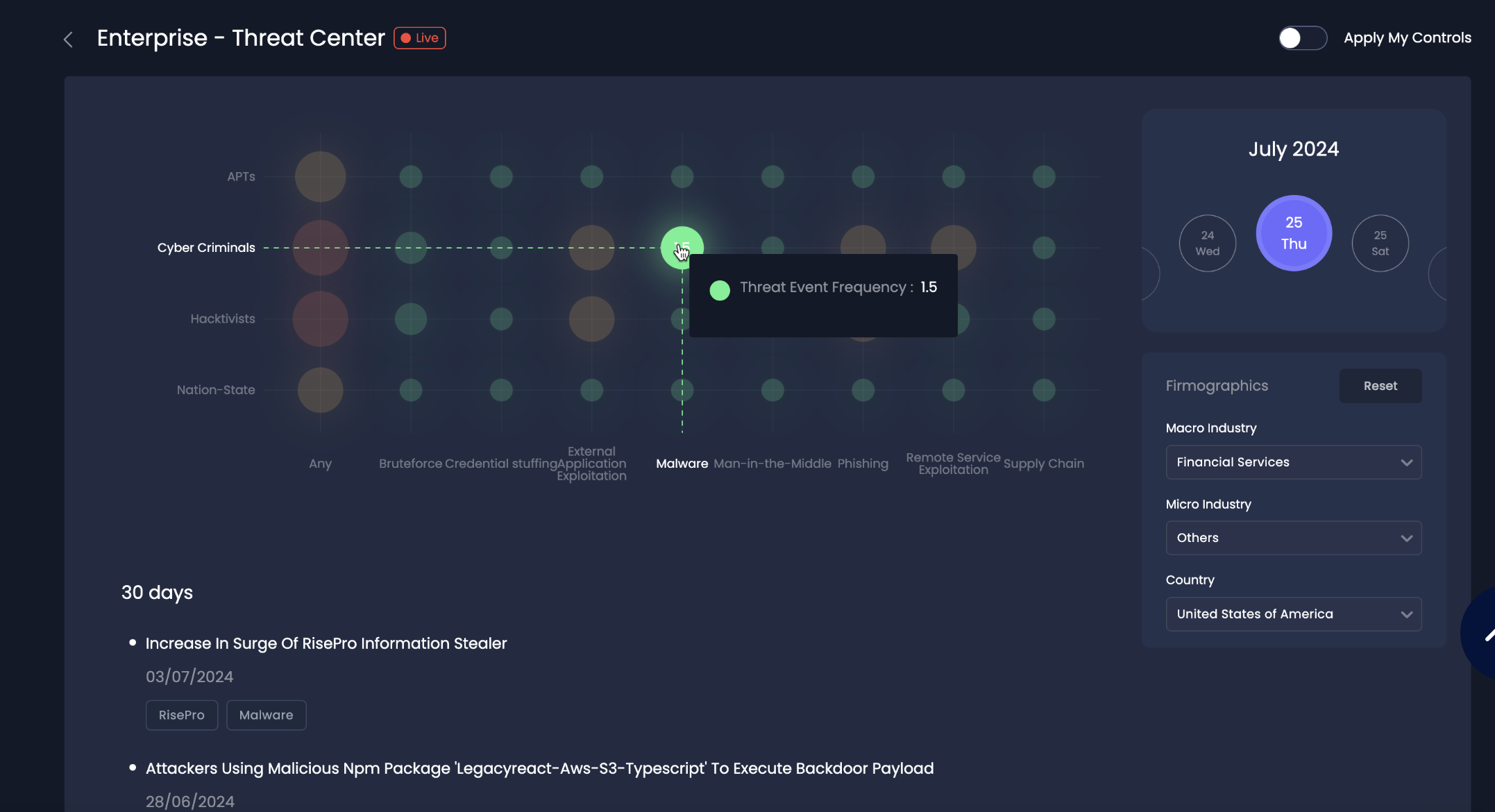
How SAFE One Automates FAIR
Let’s break down how SAFE One automates FAIR by exploring what changed outside (Threat Event Frequency and Automation), what changed inside (Susceptibility), and what drives loss (Loss Magnitude).
1. What Changed Outside: Threat Event Frequency (TEF) and Automation
Traditionally, the FAIR model relied on static, point-in-time assessments that required manual input. SAFE One has fundamentally changed how Threat Event Frequency (TEF) is managed. Instead of relying on historical data and manual estimates, SAFE One leverages AI-driven automation to continuously monitor and update TEF in real time.
The SAFE One platform aggregates multiple cyber signals from across the organization, providing a holistic view of threats. This dynamic approach allows the system to automatically pull in relevant external threat intelligence, including emerging vulnerabilities and threat actor activity. As a result, CISOs receive an up-to-the-minute view of how often specific threat events are likely to occur, based on real-time data.
This shift from static to dynamic TEF enables organizations to make more accurate predictions about the likelihood of cyber events, empowering risk leaders to make data-driven decisions with the most current threat intelligence at hand.
Read a SAFE One factsheet to understand more on how it calculates risk
2. What Changed Inside: Susceptibility
Inside the organization, the traditional FAIR model required cybersecurity teams to take a guess on their systems’ susceptibility to threats. SAFE One transforms this by automating the Susceptibility analysis, which is a critical element in determining how vulnerable an organization is to potential threats.
The SAFE One platform integrates with the FAIR Controls Analytics Model (FAIR-CAM) to monitor the effectiveness of security controls in real time. By automating this process, the platform continuously evaluates how well current controls are mitigating threats and identifies any weaknesses or gaps in protection. This ensures that organizations aren’t relying on outdated information about their security posture.
With real-time data on Susceptibility, SAFE One enables organizations to adjust their defenses on the fly, reinforcing critical controls before vulnerabilities are exploited. This continuous monitoring of controls improves the organization’s overall risk management and reduces Susceptibility to both known and emerging threats.
Read about simplifying FAIR-CAM with SAFE One
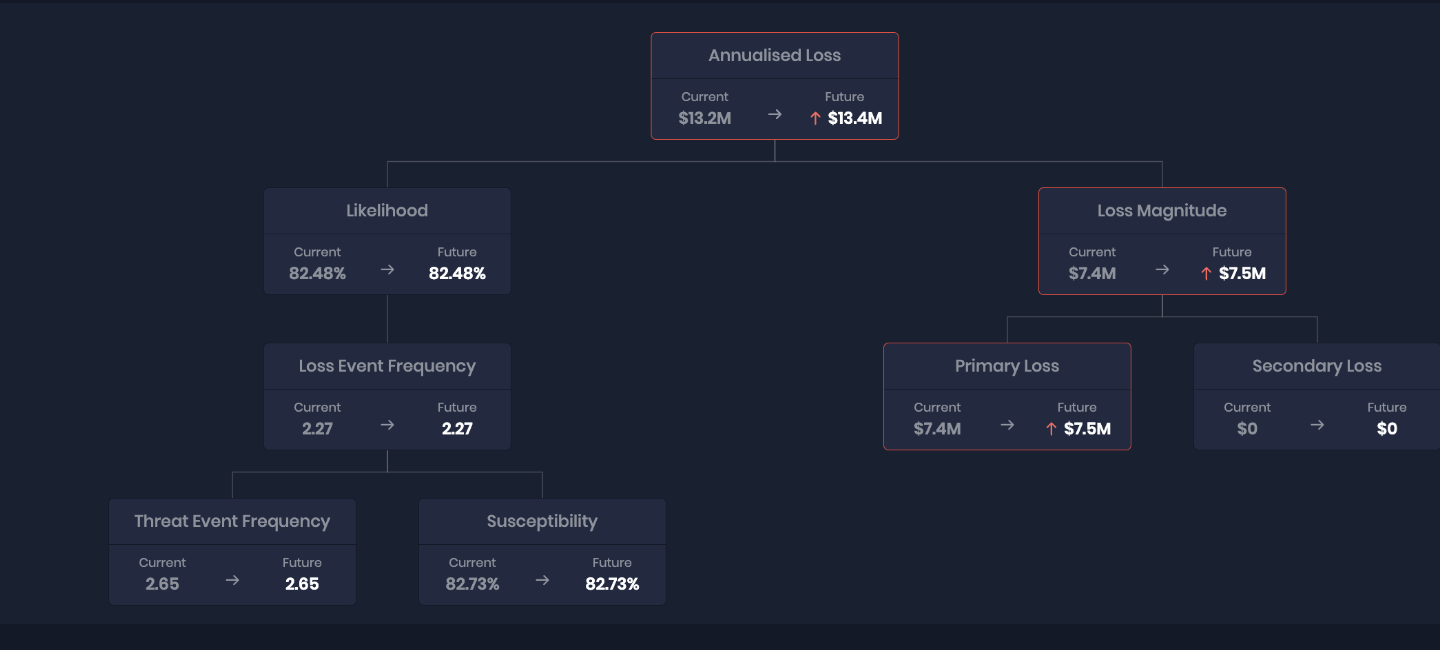
3. What Drives Loss: Loss Magnitude
The third pillar of FAIR automation through SAFE One is focused on Loss Magnitude, which measures the potential financial impact of a cyber event. In traditional implementations, calculating loss magnitude was labor-intensive and based on manually collected data, making it difficult to keep assessments accurate and up to date.
SAFE One automates the Loss Magnitude calculation by integrating real-time data from internal logs and external industry sources. The platform pulls in loss data from trusted vendors and combines it with the organization’s own risk scenarios, which are aligned to industry standards such as MITRE ATT&CK and FAIR-MAM.
By automating loss magnitude calculations, SAFE One provides CISOs with a clear, real-time understanding of the potential financial consequences of a cyber event, along with the likelihood of occurrence. This not only helps them prioritize risk mitigation efforts but also enables them to communicate the business impact of cyber risks in financial terms to stakeholders.
Read more on SAFE MAM assessment
Conclusion: The Power of FAIR Automation with SAFE
SAFE has fundamentally transformed the way organizations implement and benefit from the FAIR model. By automating key aspects like Threat Event Frequency (TEF), Susceptibility analysis, and Loss Magnitude, SAFE turns a once static, manual process into a dynamic, real-time solution. CISOs and cybersecurity leaders can now leverage AI-driven insights to continuously monitor their cyber risk posture, quantify potential financial impacts, and prioritize the most critical threats with confidence.
No longer bound by manual assessments or outdated data, organizations using SAFE One can unlock the full potential of FAIR. This automation empowers teams to make faster, more informed decisions that protect the business, reduce risk, and communicate the financial implications of cyber threats in clear, actionable terms. SAFE doesn’t just automate FAIR—it elevates it, giving CISOs the tools they need to navigate an increasingly complex cyber risk landscape with precision and ease.



