Quick Customer Story: Solve “Data Bottlenecks” for Faster Risk Assessment
SAFE’s controls integrations, centralized data collection knocks assessment time down to hours
By Chad Weinman
As a veteran in CRQ (cyber risk quantification), I wanted to share a recent Customer story. This Customer has been doing CRQ for 3-5 years but only recently onboarded to the SAFE One platform.
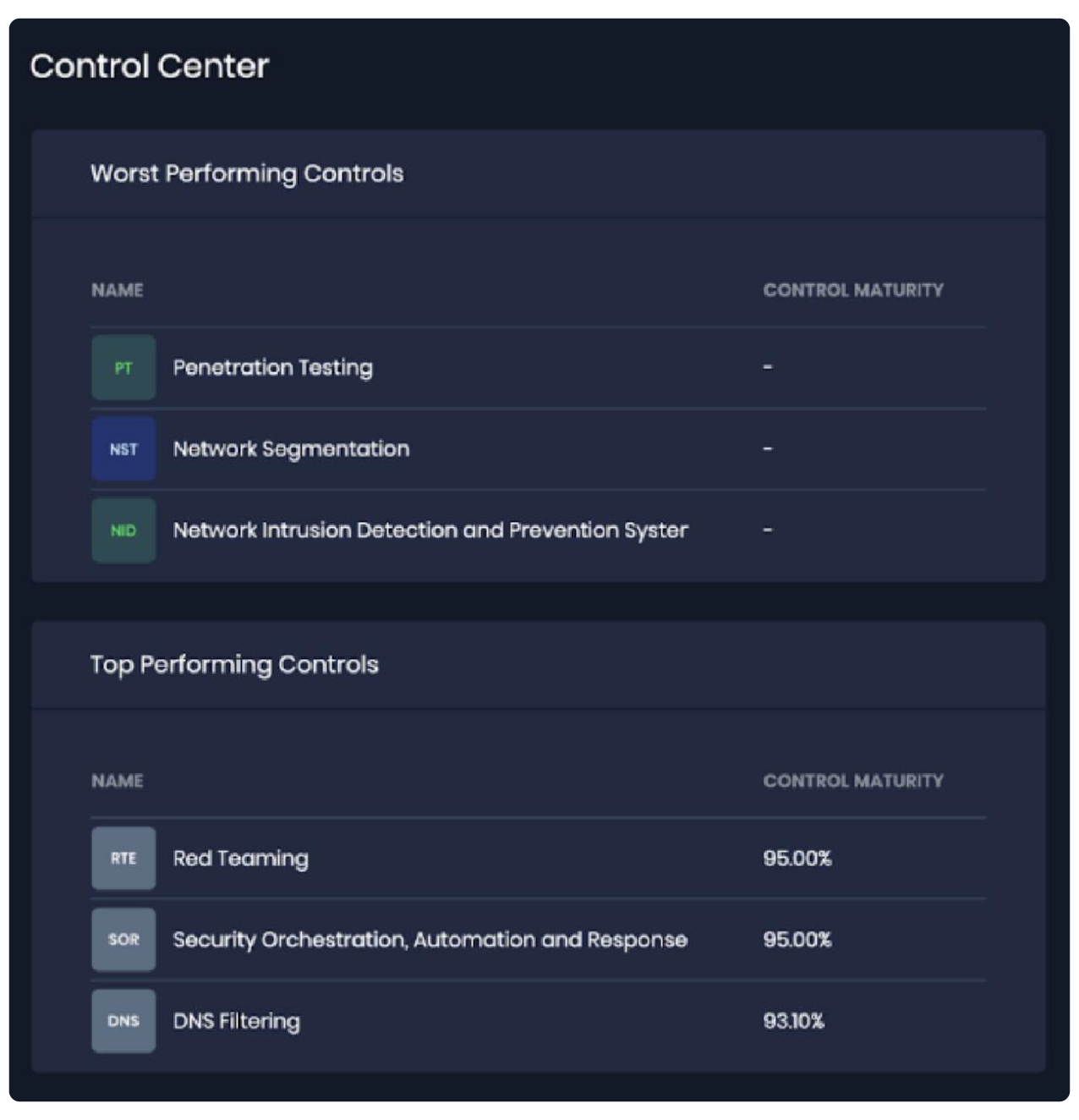
They rapidly populated their FAIR-CAM Control Center by completing their first integration (Tenable) and uploading their most recent NIST CSF assessment.
The SAFE One Platform delivers the industry’s most comprehensive and exhaustive list of technology integrations with cybersecurity controls. The 100+ integrations, available out-of-the-box, provide cybersecurity teams with unified and integrated enterprise-wide visibility, AI-powered analytics, and real-time cyber risk quantification and management capabilities. Learn more about SAFE One integrations.
Learn about uploading NIST CSF or other controls documentation to the SAFE One platform and mapping to the FAIR Controls Analytics Model in this blog post: Measuring the Effectiveness of Cybersecurity Controls with FAIR-CAM.
Now this Customer is not new to CRQ but quickly shared the following positive story. The CISO of this healthcare organization had a request for an assessment to be completed to facilitate a risk decision related to an important system running on an outdated platform.
The entire assessment, from scoping to final report, was completed in 2-4 hours and facilitated a risk decision on the same day. When they shared visible enthusiasm for this SAFE One experience, I asked them to share what their previous experience was on another platform. They said the same type of risk assessment often took an entire week or more. The single most time-consuming part was collecting data from the organization.
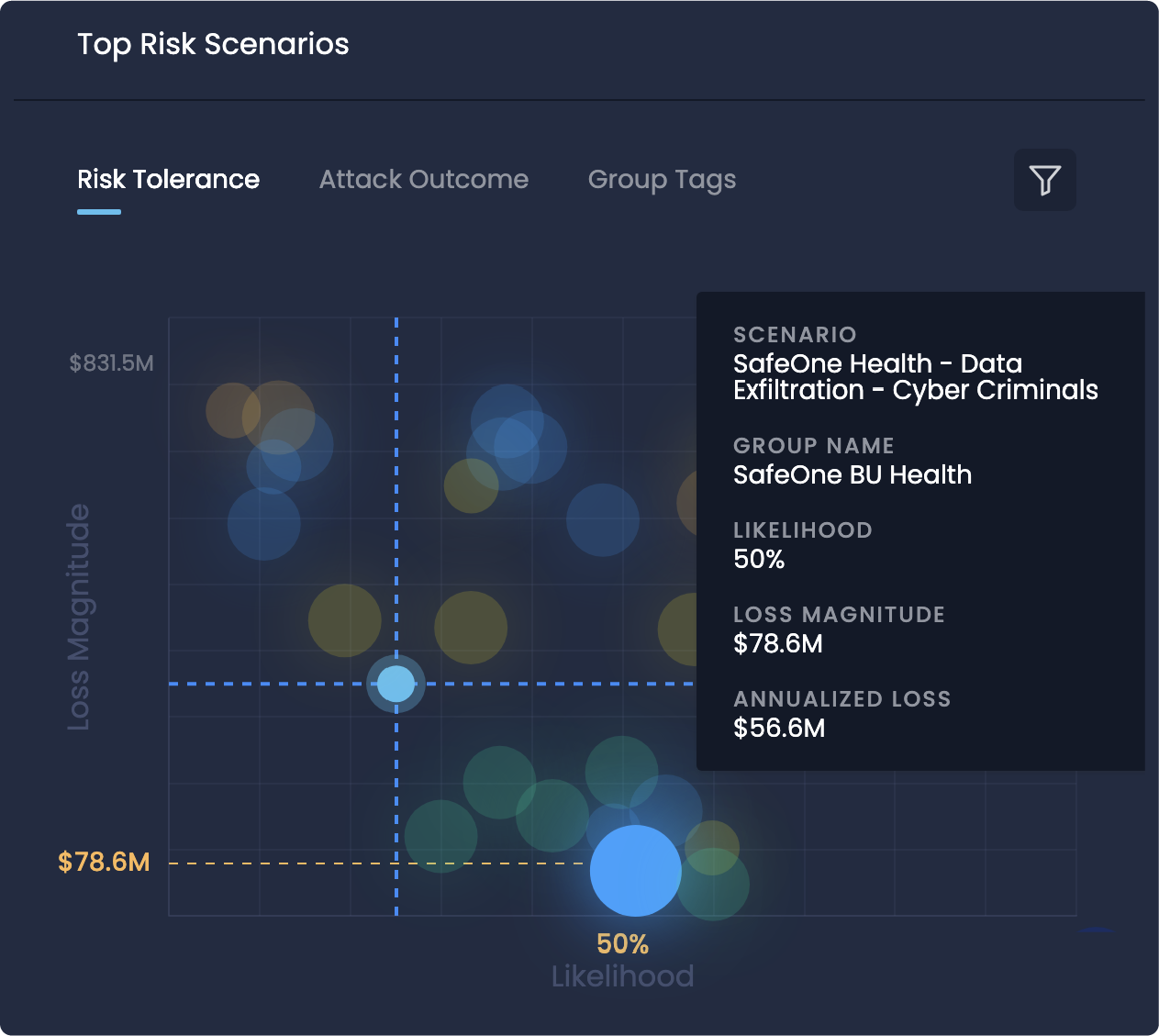
Data collection has long been the “bottleneck” for many approaches to cyber risk quantification. This is just one key benefit of how SAFE One was designed. Centralized data collection allows for “measurement planning”, the ability to upload control data you already have, and integrations that continuously automate your control efficacy.
SAFE leads the industry in development of FAIR-MAM, the standard model for cyber data collection and analysis, based on FAIR (Factor Analysis of Information Risk). This model incorporates industry data and can be tuned to the organization’s particular loss data.
Customer Onboarding at SAFE – Getting to the “First Desired Outcome”
At SAFE, we have developed a highly focused onboarding process to get customers to a “first desired outcome,” a quick win with high value to the organization. It’s a key differentiator for SAFE. We’re not just looking to stand up a SaaS application, we want to guide our clients to a new outlook that’s risk-based and quantitative.
Often clients want to solve a pressing problem, as in our healthcare example. Or they may have a longer-term outlook and need a use case to gain buy-in from the CISO or other key stakeholders. Just from the onboarding process in the platform, they may have learned of controls deficiencies that suggest a risk scenario to analyze.
Our standard jumping-off point to define a first desired outcome is to create a Charter, a document that clarifies the goals of the program, timelines and success metrics. Most importantly, it will define the value the organization hopes to achieve from SAFE One, a North Star the team can be led by. With that in hand, the next question is “What’s the first step?”
We find that SAFE customers most often first choose a top-risks analysis for the organization. But that’s just one of seven decision areas supported by the SAFE One platform that might also serve as a category for a first desired outcome.
The 7 Decision Areas
- Understand and communicate risk – assess and report top risks from the business perspective in financial terms.
- Prioritize and treat risk – mitigate risk to acceptable levels, strengthen resilience.
- Meet regulatory requirements – for internal or external audit or risk assessment.
- Strategically allocate investments – develop business cases that cost-effectively allocate budget to meet ROI goals.
- Manage third-party risk – run cyber TPRM based on loss exposure to vendors
- Benchmark cyber program performance – compare against industry peers.
- Optimize cyber insurance coverage – gain credits for program maturity, and optimize coverage and premiums.
We always enjoy the presentation of the First Desired Outcome as an output from the SAFE One platform – our clients usually see the actionable insights right away. As one CISO told us, “this provides the defensible support I need for allocating my security budget and can even open my eyes to areas I had not considered.”
If you have tried risk quantification before, I invite you to contact me directly. I have been applying FAIR for 15 years, and I would personally love to show you how SAFE One is truly a refreshing and scalable platform for better cyber risk management.



