HALVE the Cost of a Data Breach with Cyber Risk Quantification
IBM and the Ponemon Institute suggest CRQ can save $2.10 million

The 2022 Cost of a Data Breach Report has put Cyber Risk Quantification (CRQ) firmly in the spotlight. The yearly report, released by IBM and the Ponemon Institute, sheds light on the leading contributors to the rising costs of data breaches and actions that businesses can take to decrease risk and exposure. In the most recent edition of the report, risk quantification has been deemed one of the key methods that have the largest impact on minimizing losses, alongside cybersecurity AI and automation and incident response (IR), zero trust, and XDR technologies.
This is the first time in the report’s 17-year history that “the use of risk quantification techniques” has been presented as a means of effectively managing security risks and minimizing the cost of a data breach.
Why?
Cybersecurity risk is changing. Therefore, the way organizations manage this risk should adapt, too. This blog post explores why Cyber Risk Quantification is gaining traction and will help YOU understand why it’s essential that CRQ is adopted now.
The ever-evolving cyber risk landscape and how businesses cope

The cybersecurity landscape is ever-evolving, and advanced TTPs continue to outpace the global security response. Globally, organizations and governments are zeroing down on methods to improve and enhance existing security practices by introducing new technologies that reduce human error and bridge the skills gap in cybersecurity, along with regulatory frameworks that warrant accountable cybersecurity reporting. It is, therefore, imperative that businesses manage this complex environment proactively.

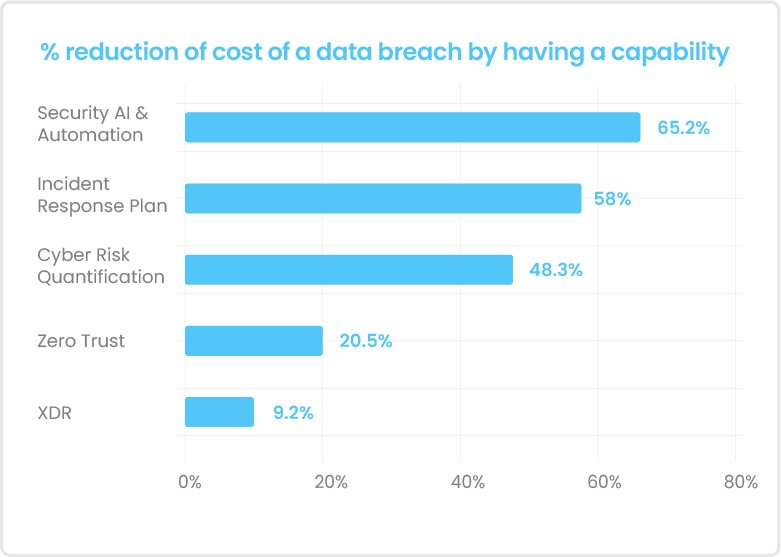
The report found that the top 3 actions to minimize the financial impact (loss) due to a cyber attack are:
- Adding security AI and automation: Fully deployed security AI and automation was associated with average breach costs that were USD 3.05 million lower than with no security AI and automation deployed, a difference of 65.2%, the largest cost savings in the study. [Ponemon Institute/IBM]
- Building robust incident response (IR) capabilities: Breaches at organizations with IR capabilities saw an average cost of a breach of USD 3.26 million in 2022, compared to USD 5.92 million at organizations without IR capabilities. This average cost was a difference of USD 2.66 million or 58%. [Ponemon Institute/IBM]
- Leveraging Cyber Risk Quantification to prioritize actions: Organizations that prioritized risks, threats, and impacts based on risk quantification techniques had an average breach cost of USD 3.30 million. That cost was USD 2.10 million less than those that didn’t use risk quantification, at USD 5.40 million, a savings [sic] of 48.3%. [Ponemon Institute/IBM]
By acknowledging the risk of manually-driven operations across tools and disjointed systems, businesses have begun to pivot away from point-in-time and dispersed cybersecurity practices. In a largely automated and cloud-based infrastructure, business leaders have realized the importance of security AI and automation.
- The share of organizations with fully or partially deployed security AI and automation increased from 65% to 70% between 2021 and 2022.
- In 2018 – which is when security AI and automation were first incorporated in the report– only 15% of companies reported full deployment, and 34% reported partial deployment.
- The % of organizations with no security AI and automation deployed decreased from 35% in 2021 to 30% in 2022
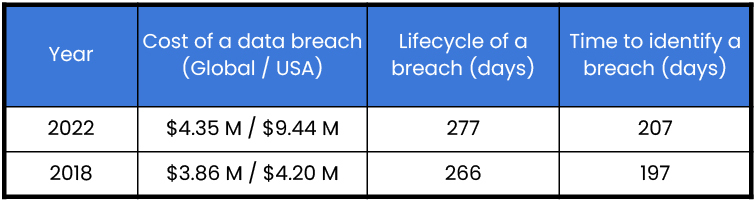
However, despite automation and AI in cybersecurity, the rising financial impact and time to detect a cyber attack are concerning.
Security AI and automation + Cyber Risk Quantification = Efficient Cyber Risk Management
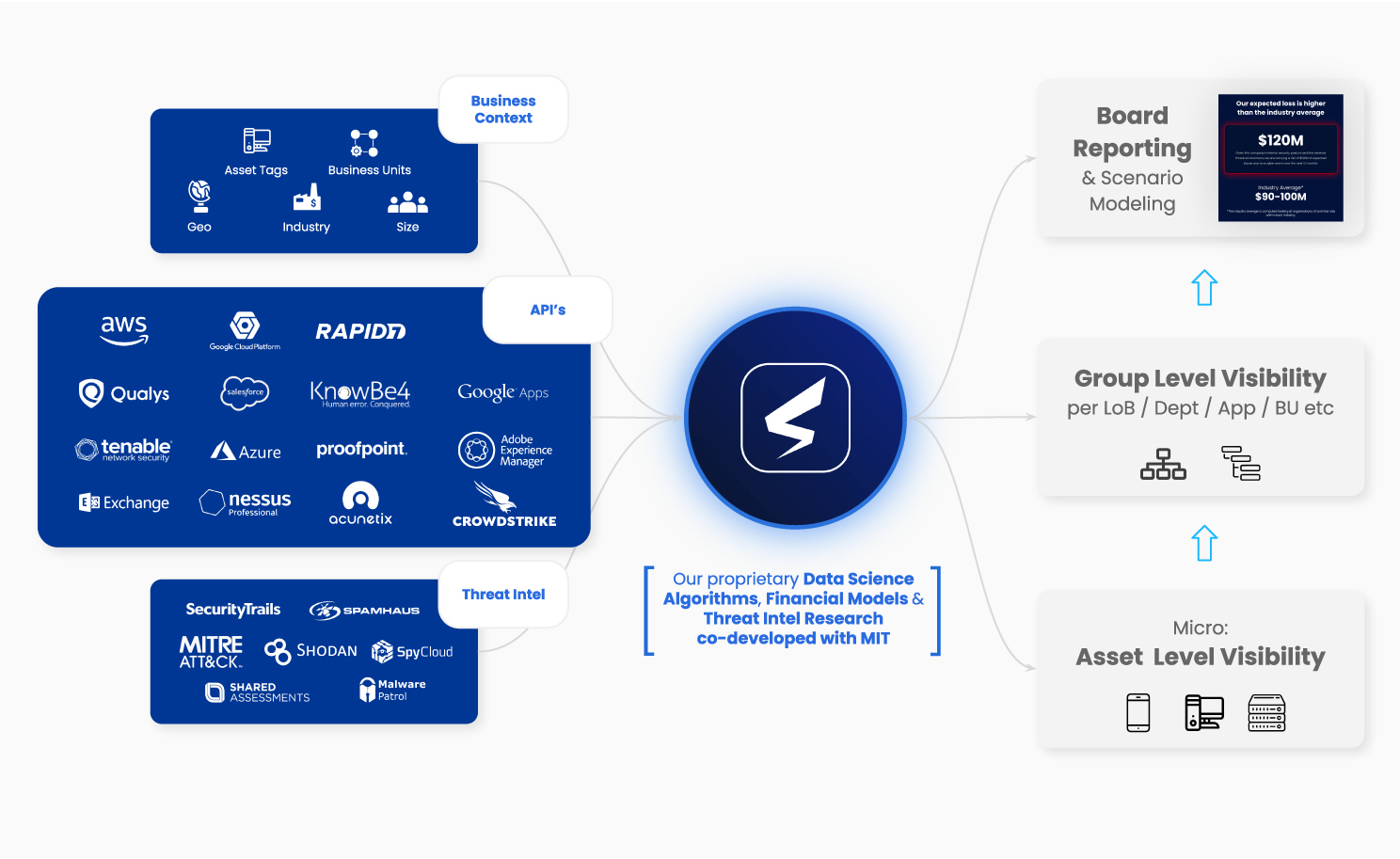
A Cyber Risk Quantification and Management (CRQM) solution worth your time will have advanced beyond subjective, manual, and point-in-time analysis. Instead, it will rely on signals from dispersed and siloed network systems to collate everything within a single dashboard.
What’s encouraging for the industry and readers of the new report is that there are solutions currently on the market that bridge two out of the top three solutions to reduce the cost of a data breach – automation and AI with cyber risk quantification. These more advanced CRQM technologies combine the power of automation with data science and artificial intelligence to provide real-time, always-on visibility of cybersecurity risk.
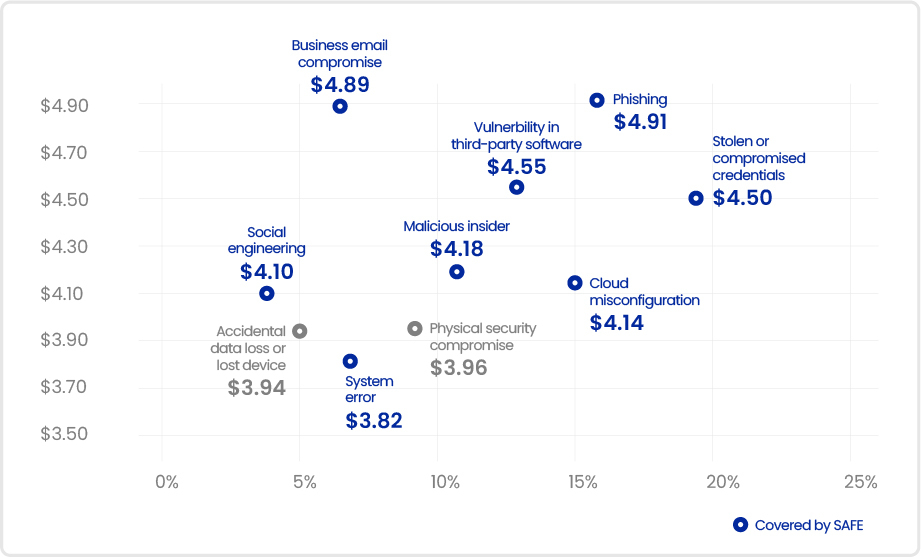
Risk quantification looks at impacts, including financial impacts, availability of data, and data integrity. Using risk quantification can highlight financial loss types by impact, including the following examples: loss of productivity; cost of response or recovery; reputation impact; and fines and judgments. – (Cost of a Data Breach Report 20220).
CRQM was introduced decades back but has recently gained traction – owing to global regulatory proposals to mandate Cyber Risk Management and the inherent benefits of knowing the financial impact of cybersecurity risk.
Broken down into four cost categories — lost business, detection and escalation, notification, and post-breach response — detection and escalation costs surpassed lost business costs as the largest of four cost categories comprising the cost of a data breach for the first time in six years. The costs include activities that enable a company to reasonably detect a breach – forensic and investigative activities; assessment and audit services; crisis management; and communications to executives and boards.
But, these results are not surprising – we have seen that decision-making based on quantified risk measurement can significantly improve a company’s cyber posture.
SAFE: Building CRQM for the Modern Enterprise
Combining security AI and automation with Cyber Risk Quantification will empower you to quantify data that you’re currently unable to visualize and digest. By enabling you to measure your cyber risk in real-time, you’ll also be able to explore:
- What your most crucial cyber threats are
- The likelihood of a particular type of cyber attack
- How your business can manage risk through prioritization and risk sharing (cyber insurance)
How can SAFE help you apply the report’s recommendations?
SAFE, an AI-enabled cyber risk quantification and management platform, gathers API-driven signals from cybersecurity to help your business improve its efficiency in cyber risk management through informed and data-driven decisions to accept, mitigate, or transfer cyber risk.
- The SAFE approach is based on real-time signals coming from your business’ attack surface. Its ability to proactively identify risk extends across the most common (and costliest) initial attack vectors.
- SAFE helps you maximize the ROI from your security actions and incident response (IR) capabilities using automation and prioritization. Layering cyber risk quantification to your IR plan and testing empowers data-driven reports and audits.
- SAFE doesn’t just measure risk but provides succinct prioritized recommendations to reduce the total financial impact of a cyber attack. This enables efficient cybersecurity communication, investment, and risk sharing.
If you’re new to cyber risk quantification and want to learn more about it, visit our dedicated page on CRQ 101.
If you’re already using a framework based on FAIR principles and want to adopt a solution that can help you implement it practically whilst reaping its benefits, visit, How to Implement FAIR .


