Ultimate Guide to Cyber Threat
Understand your threat landscape, plan your defenses and mitigations with the clarity of a quantitative approach to cyber risk.
Let’s take a little test. Which of these are cyber threats?
- Hacktivists
- Denial of service attack (DDoS)
- Social engineering
- Malicious code
- Phishing emails
- Internet of Things (IoT devices)
Now let’s apply FAIR (Factor Analysis of Information Risk), the standard for cyber risk quantification. FAIR teaches us to be precise and disciplined in our definition of cyber threat and other key concepts so that we can construct cyber risk scenarios to produce analyses that give an accurate picture of risk. In FAIR, a risk scenario must lead to a quantifiable loss (or why bother!).
What Is Cyber Threat?
The definition of cyber threat is: An actor that causes an event that produces a loss. So, in our vocabulary quiz, only hacktivists count as a cyber threat. Social engineering, malicious code and phishing emails are forms of attack – they need a threat actor to leverage them in an attack or other loss event. IoT devices are things that could be the location of that loss event caused by a threat actor.
Cyber Risk Analysis Basics: How Does a Cyber Threat Produce a Measurable Loss?
Here’s a quick education on the FAIR model, which you can see represented in this schematic.
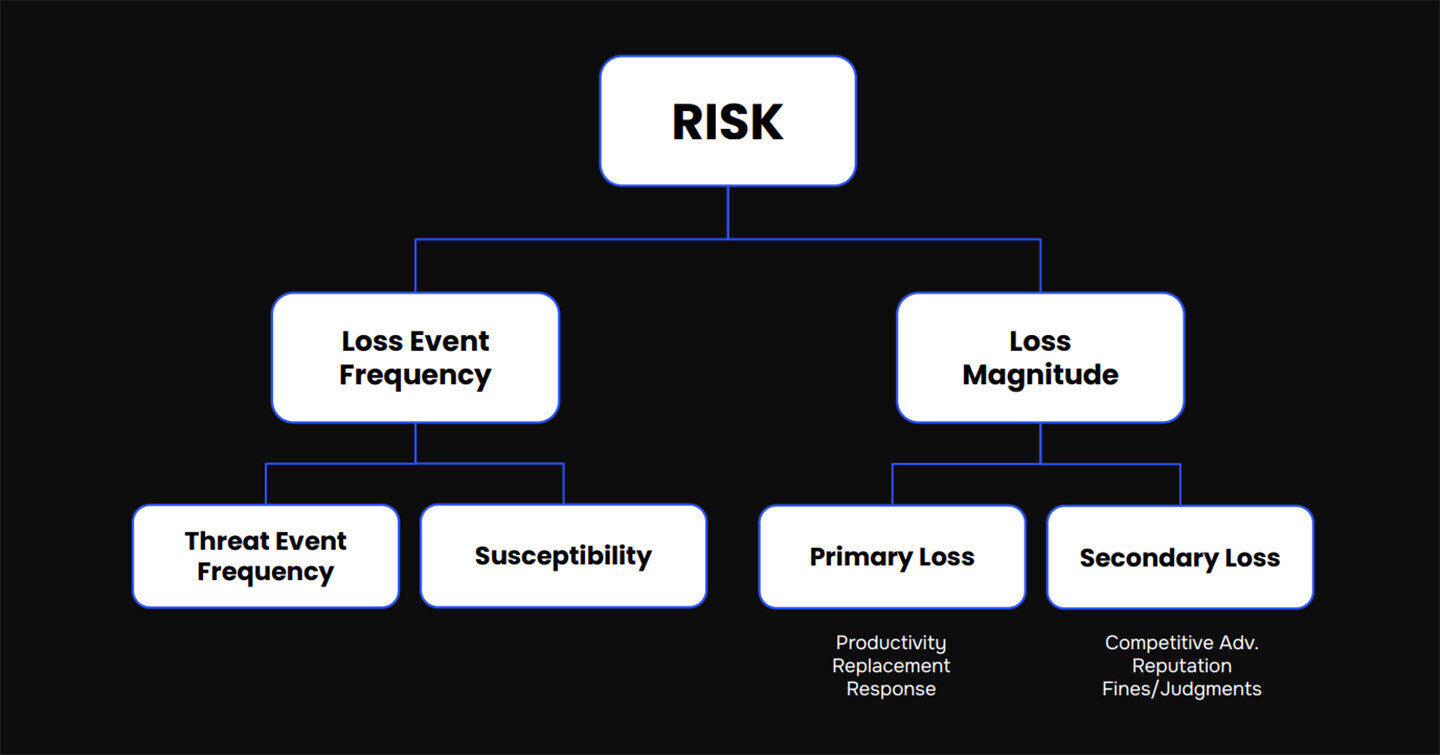
In weighing a risk-based decision, a business leader would want to know what’s the likelihood of a loss event happening (expressed as an annual percentage) and what’s the probable size of the loss (in dollars).
To focus on the left side, we answer the Loss Event Frequency question by quantifying the Threat Event Frequency (how many likely attacks in a time frame) and Susceptibility (how likely is the attacker to break through our defenses, a function of the capabilities of attackers and defenders). We can quantify with confidence based on industry standard data or the organization’s internal data on cyber attacks.
What Is Cyber Threat Intelligence?
Cyber threat intelligence (CTI) is the detection, collection, analysis and application of information about current or potential cyber threats to an organization’s information systems or data. Cyber threat intelligence is a subset of an organization’s broader threat intel effort, also including strategic, tactical, operational, and technical intelligence.
Programs and Tools for Cyber Threat Intelligence
A Threat Intelligence Program gathers, analyzes and disseminates intelligence related to cyber threats within an organization. It relies on a central Threat Intelligence Platform for management of data and cyber threat intelligence.
Cyber Threat Modeling for Threat Intelligence
Cyber Threat Modeling is a systematic approach to identifying and mitigating security risks associated with software applications, systems, or processes. It involves analyzing design, architecture, and functionality to identify potential threats, vulnerabilities, and attack vectors that malicious actors could exploit. By proactively identifying and prioritizing security risks, organizations can implement appropriate countermeasures and security controls.
Uses and Benefits of Cyber Threat Intelligence
With cyber threat intel, organizations can adopt a proactive approach to cyber risk, anticipating likely attacks and prioritizing responses. Examples are:
- Prioritizing deployment of cybersecurity controls along the cyber threat’s probable attack vector, saving money and effort.
- Incident response, planning next steps to stay ahead of attackers as they attempt to move laterally.
- Assessing the organization’s security posture
- Facilitating communication among development teams and security teams so that security is considered early in design and implementation of the system.
Sources of Cyber Threat Intelligence
Cyber defenders can draw on a range of threat intel sources, including
- Open-source intelligence, publicly available information analyzed for intelligence value
- Internal logs and telemetry from security applications and tools
- Shared information from ISACs (Information Sharing and Analysis Centers)
- Cybersecurity alerts and advisories from government agencies such as CISA
Types of Cyber Threat Actors
1. Cyber Criminals
- Motivation: Financial Gain
- Examples: REvil, Conti, and DarkSide groups
- Threat Capability: High
These ruthless perpetrators may use social engineering/phishing emails, stolen login credentials or other means to gain unauthorized access to your systems to steal data or sensitive information or insert malicious code to trigger ransomware, with the goal of making you pay to recover your data. They conduct cybercrime as a business – and a highly successful one, including selling Ransomware as a Service for off-the-shelf attack packages.
2. General Hackers
- Motivation: Developing skills, gaining status in a community
- Example: Lapsus$, Scattered Spider
- Threat Capability: Low
“Script kiddies” possess low skills and may use pre-packaged scripts or programs developed by others to break into computer systems. But watch out. They may graduate to truly destructive attacks. Lapsus$, a gang of teenagers used low-tech approaches such as aggressive social engineering to gain unauthorized access to computing resources at Microsoft and other big tech companies. In another case, a 17-year-old was arrested for an attack that knocked MGM Resorts systems offline for 10 days in 2023.
3. Privileged Insiders
- Motivation: Malicious intent or error
- Threat capability: High
These actors include individuals with access to code in the system, write access in systems or those that can add users. Harmful actions by privileged insiders may occur by accident (human error) or intentionally (maliciously). They have direct access to large amounts of confidential information and can be quite harmful if they choose to attack the systems. Often, they start at a low level of access and escalate privileges to admin status by exploiting vulnerabilities in the system. If a privileged insider causes harm, typically the damage can be remediated quickly but nonetheless could cause high financial impact.
4. Privileged Third Parties
- Motivation: Software update (that goes wrong)
- Example: CrowdStrike
- Threat capability: High
As we’ve seen with the CrowdStrike outage and other recent incidents, trusted third-party vendors may have wide access to sensitive data and even may access computer systems inside the firewall at the deepest, kernel level via automated software updates. They may insert non-malicious but damaging code that can cripple business operations.
5. Non-privileged Insiders
- Motivation: Revenge
- Threat capability: Medium
Think of a disgruntled employee – but without critical access to cyber assets and must break through resistive controls to cause harm.
6. Hacktivists
- Motivation: Political
- Example: Anonymous
- Threat capability: Low to Medium
Activist hackers may attack your systems in the belief they can force their social or political agenda on your organization. Skills vary widely – a favored technique is a distributed denial of service (DDoS) attack staged by their followers.
7. Nation States
- Motivation: Orders from above
- Examples: Russia (Fancy Bear, Cozy Bear), China (APT10, APT41), North Korea (Lazarus Group)
- Threat Capability: High
From supply chain compromise to password spraying to PowerShell subversion to advanced persistent threats (APT), these threat actors tied to intelligence agencies or military units are the ones to fear most. If they truly want to get into your systems, they probably will. But experience has shown they can be thwarted by a serious, risk-based defensive area that scopes out your most sensitive assets, the attack paths that lead to them and a prioritized list of the controls you should put in their way.
Cyber Threats: The 7 Most Common Forms of Attack
1. Ransomware
Malware-based attack designed to pressure a company to pay a ransom by encrypting and withholding access to systems or files, and extorting the victim by threatening to make public sensitive information. An apparent ransomware attack may also be a cover for “wiper” malware intended purely for destruction of data and systems.
2. Insider Error
Misconfigurations, failure to renew expired certificates, improper publishing and other errors by staff members can have damaging consequences to the bottom line. Count as a possible threat actor in this category the trusted third-party supply chain vendor operating inside your network.
3. Insider Privilege Abuse
Whether it is the intentional and malicious disclosure or modification of sensitive data or a logic bomb taking down the network, your most trusted employees can cause significant loss to the company by sabotage.
4. System Intrusion
Through code exploitation or good old fashioned brute force password guessing, a bad actor gets a foothold in your network and can access your most sensitive assets, resulting in a data breach, business interruption or other perils. This category does not include ransomware or social engineering-based attacks.
5. Social Engineering (Phishing)
Tricking insiders into sharing confidential or personal information or making a payment, often through a phishing email that appears to come from a friend, a well-known brand or business partner, possibly resulting in data breach or business interruption if an attacker gains entry to the network. New development: AI-generated voice simulators for phishing phone calls.
6. Web Application Attacks
Compromise of a web application via brute force or code exploitation to create business interruption or data breach, or possibly gain a foothold to target critical assets.
7. Denial of Service (DOS or DDoS)
Attackers flood the victim’s system with traffic, making it unavailable and leading to business interruption.
New Cyber Threats in 2024: Artificial Intelligence (AI)
The widespread adoption of Generative Artificial Intelligence (GenAI) and Large Language Models (LLMs) has introduced some new twists to analyzing cyber threats – namely the emergence of AI itself as a threat. Luckily, we can apply our trusted FAIR quantitative risk techniques to scope out risk scenarios we can analyze.
Some examples of this new cyber threat:
- Threat-actor criminals or nation states use LLMs to generate authentic-looking phishing emails or authentic-sounding voicemail.
- Non-malicious insiders–doing work using an open-source LLM like ChatGPT not controlled by their organization–leak sensitive corporate information
- Non-malicious insiders train an LLM using data without appropriate permissions, leading to a leak.
- Hallucinations – AI itself acts as a threat actor by generating content that’s simply wrong, leading to mistakes within the organization or legal issues from outside the organization.
Other Emerging Cyber Threats to Watch
Threats to Critical Infrastructure
The FBI warned that the Chinese government is engaged in a “broad and unrelenting” cyber targeting of infrastructure inside the US, including water treatment facilities, energy grids, that “form the backbone of our society.”
Disinformation, Misinformation Cyber Threats on Social Media
A recent investigation by the Wall Street Journal found “thousands of videos with political lies and hyperbole” on TikTok, pushed by foreign threat actors seeking to create conflict in the US.
Cyber Threats to Internet of Things Devices (IOT)
With everything from our cars to our refrigerators networked, IOT devices represent a vast attack surface. With their weak security and often outdated firmware, Internet of Things devices can be the target system of choice for distributed denial of service (DOS) attacks such as those staged by the Mirai Botnet. These devices can also be a target for data breaches, given the large amount of personal data they store.
Strategies for Cyber Threat Detection and Protection
The well-known three pillars of threat intelligence are a valuable tool for awareness on the cyber side of the house as well as the traditional units of the business when planning to counter cyber threats.
- Strategic Cyber Threat Intelligence
A high-level view of what may be long-term or even existential threats to the business originating from cyber threats. Useful for cyber risk analysis supporting major decisions such as a merger, opening a foreign operation, or a move of sales away from brick and mortar to ecommerce.
- Tactical Cyber Threat Intelligence
Ongoing analysis of the tactics, techniques and procedures (TTPs) of cyber threat actors–and a concomitant analysis of the strength or vulnerability of the organization’s security controls and processes vs likely cyber threats, particularly targeting key assets of the organization.
- Operational Cyber Threat Intelligence
Real-time reads on the active cyber threats hitting the attack surface and the on/off status of cyber controls, typically conducted through integrations with cybersecurity tools and products for automated cyber risk management. This form of threat intel would also come into play in response to an active incident, including rapid assessment of material impact that might require public reporting.
SAFE Can Help You Protect Your Organization Against Cyber Threat. Understand your organization’s threat landscape, plan your defenses and mitigations with the clarity of a quantitative approach to cyber risk – SAFE is ready to help.



