Why is Cybersecurity Risk Ratings Just a Feature, Not the Full Picture of Third-Party Cyber Risk
By Sachin Jha
Know the difference between risk ratings and risk quantification. A risk rating is not a quantitative measure of risk — full stop. Instead, it is a score based on security indicators that correlate with risk.
– The Forrester Wave™: Cybersecurity Risk Ratings Platforms, Q2 2024
The recent Forrester Wave report on Cybersecurity Risk Ratings Platforms underscores a significant shift in the cybersecurity industry, advocating for a deeper understanding of risk ratings versus risk quantification. This distinction is not just semantic; it is foundational to how organizations should approach cyber risk management. As noted by Forrester, while risk ratings provide a score based on security indicators, risk quantification delves into the probability and material impact of risk scenarios, offering a more nuanced view of potential vulnerabilities and threats.
Cyber risk quantification (CRQ) directly measures the probability and material impact of a risk scenario. They are related, and ratings data can be used in a CRQ analysis, but they are not the same.
– The Forrester Wave™: Cybersecurity Risk Ratings Platforms, Q2 2024
Read an exclusive factsheet on why your Cybersecurity Risk Ratings are misleading and how you can overcome this challenge with Cyber Risk Quantification
SAFE’s Role in Elevating Third-Party Risk Management
SAFE offers a Gen AI-powered platform integrating first-party and Third-Party Risk Management. By offering a detailed and dollar-quantified view of potential threats, SAFE enables companies to make more informed, strategic decisions about their cybersecurity investments and third-party interactions. Unlike traditional risk management tools that offer static, point-in-time assessments, SAFE provides dynamic, real-time insights into cyber risks, utilizing a comprehensive array of security controls and indicators. Our analysis of incidents, like the recent attack on UnitedHealth Group shows that traditional risk assessments can underestimate potential damages significantly.
Understand and Communicate Cyber Risk from a Business Impact Perspective
SAFE TPRM transforms the way organizations manage and communicate cyber risk by focusing on a risk-based approach rather than mere compliance. Our platform unifies first-party and third party cyber risk management, providing a clear financial quantification of potential risks. Whether these risks stem from internal operations or external vendors, SAFE TPRM assesses them in terms of financial impact and likelihood, allowing for precise prioritization. This is achieved through the integration of our advanced FAIR modules: FAIR-CAM automates the evaluation of control effectiveness, FAIR-MAM quantifies financial risks to prioritize remedial actions, and FAIR-TAM streamlines the assessment process for third-party risks.
Learn more about how SAFE quantifies cyber risk powered by FAIR-MAM: Explore the SAFE Materiality Assessment Module
Prioritize and Execute Risk Treatment Plans Based on a Data-Driven Approach
Using SAFE TPRM, companies can prioritize and manage risk with a data-driven approach that accounts for internal and external risks. SAFE’s method focuses on identifying and enforcing a select set of elite critical controls for third-party vendors, which are derived from thorough research of historical and current cyber attacks. SAFE TPRM constantly gathers and integrates third-party risk data—from external assessments, self-reported questionnaires, and internal evaluations—with external threat intelligence to create a comprehensive view of risks. Additionally, by applying zero trust principles, SAFE TPRM enhances the visibility and effectiveness of an organization’s internal defenses against third-party risks.
Optimize and Justify Cybersecurity Spending and Planning
SAFE TPRM aids in optimizing cybersecurity investments by providing clear insights into the potential financial impact of cyber risks and the effectiveness of existing security measures. The primary advantage of using SAFE TPRM is its cost-effective, fixed pricing model. Regardless of how many vendors an organization works with, the cost remains the same, allowing for unlimited vendor management without additional expenses. This scalable approach supports efficient growth and expansion of third party cyber risk management programs, ensuring that investments in cybersecurity are both strategic and economically sound, catering to the needs of expanding business operations.
Read an exclusive factsheet on why your Cybersecurity Risk Ratings are misleading and how you can overcome this challenge with Cyber Risk Quantification
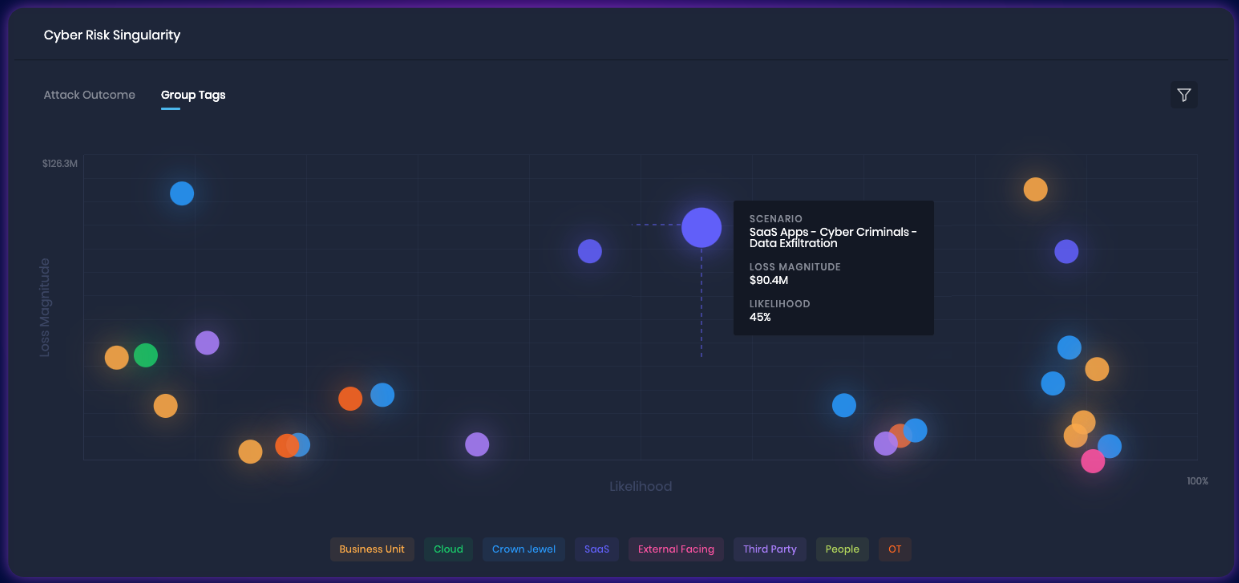
How SAFE Helps You Achieve “Cyber Risk Singularity”
We introduced the concept of “Cyber Risk Singularity” to highlight a pivotal breakthrough in how cyber risk is perceived and managed. For a CISO or a CIO, the concern isn’t just about identifying the origin of a risk—whether from their own infrastructure, a third-party vendor, or a SaaS application. Our mission with SAFE One is bold yet straightforward: to enable every company in the world to achieve cyber risk singularity. This means providing a comprehensive tool where the risk of data exfiltration, whether from an internal data center or a third-party service provider, is clearly visible and quantifiably managed from one unified platform.
A Call to Action for Better Risk Management
The insights from the Forrester Wave report serve as an urgent call for the industry to adopt more sophisticated risk management practices. As companies navigate the complexities of the digital age, understanding the difference between risk ratings and risk quantification becomes paramount. SAFE’s innovative approach to Third-Party Risk Management, focusing on quantification and strategic alignment, offers a path forward for organizations looking to enhance their cybersecurity posture effectively and efficiently.
Schedule a demo with a cyber risk expert to explore how SAFE can elevate your Third-Party Risk Management approach.



