Dark Storm Is Coming – Are You Safe Enough to Handle It?
By Safe Threat Research Team
Threat Actor Profile: Dark Storm
Dark Storm is a Hacktivist group surfaced in September 2023, quickly gaining attention for its politically driven campaigns. Often aligning with pro-Palestinian narratives, the group blends ideology with opportunism to drive its operations. While equipped with a diverse cyber toolkit, Dark Storm is best known for executing large-scale Distributed Denial-of-Service (DDoS) attacks against high-profile digital infrastructure.
Their operations often align with geopolitical flashpoints, leveraging DDoS attacks as instruments of protest, coercion, and disruption. Notably, the group has evolved into a DDoS-as-a-Service provider, offering paid services to affiliates and like-minded actors.
The group organizes and amplifies its operations through Telegram channels and dark web forums, sharing attack playbooks, recruiting participants, and spreading propaganda. To maintain anonymity and resilience, Dark Storm leverages VPNs, proxy chains, and botnet networks to execute and scale attacks.
Dark Storm is known to target the following sectors:
- Government Organization
- Defense and Military Organization
- Transportation Sector
- Education Sector
- Financial Services
- Media Sector
- Technology Companies
These attacks usually lead to:
- Widespread service disruptions via sustained DDoS attacks
- Reputational damage on a global scale
- Financial and operational losses due to prolonged outages
- Heightened regulatory and compliance pressure
- Erosion of user trust during high-stakes or critical moments
Recent Claims: Dark Storm Claims Responsibility for Attacks on X (Twitter), Zoom, and Spotify
In recent weeks, Dark Storm has reemerged with high-profile cyberattacks, taking credit for distributed denial-of-service (DDoS) campaigns against some of the world’s most popular digital platforms: X (formerly Twitter), Zoom, and Spotify. These incidents highlight the growing operational reach of threat actors and the urgent need for stronger digital defenses.
Attack on X (Twitter)
On March 10, 2025, X’s (formerly Twitter) users experienced widespread service disruptions globally, attributed to a large-scale DDoS attack. Shortly after the outage, the Dark Storm claimed responsibility via their Telegram channel, sharing real-time outage maps and proof-of-disruption links to substantiate their involvement. By broadcasting public evidence, the group aimed to validate its operational capabilities and boost its credibility within the cybercriminal ecosystem. In response, X quickly deployed Cloudflare protections, a standard mitigation step against high-volume DDoS campaigns.
Attack on Zoom
On April 16, 2025, Zoom suffered a significant nationwide outage. Initial reports attributed the disruption to a “communication error” between Zoom’s domain registrar, MarkMonitor, and GoDaddy Registry, which led to the mistaken shutdown of the zoom.us domain.
However, around the same time, the Dark Storm posted on Telegram claiming responsibility for a DDoS attack on the platform, asserting it was part of their ongoing campaign against U.S. technology services. Although Zoom did not confirm the incident as a hack, the timing and messaging suggest that the group may have already been exploiting a vulnerable situation or amplifying its reputation by opportunistically claiming credit.
Zoom later restored services and advised users to flush their DNS cache if issues persisted.
Attack on Spotify
On April 16, 2025, Spotify experienced technical difficulties, with many users reporting issues accessing the platform. Spotify acknowledged the outage on its X account, was aware of the issues, and was checking them. Dark Storm also claimed involvement in this incident, and Spotify denied any security breach, stating that reports of a hack were “completely inaccurate.” It remains unclear whether external attacks or internal service failures caused the issues. Still, the group’s pattern of claiming responsibility for disruptions adds to the growing anxiety over the availability and resilience of popular cloud platforms.
A Coordinated Campaign?
These attacks demonstrate a coordinated digital offensive by the Dark Storm, targeting some of the most critical pillars of modern communication and productivity. Their ability to disrupt services and gain public attention signals a shift in the threat landscape, where hacktivism, cybercrime-as-a-service, and geopolitical agendas increasingly overlap.
The rise of DDoS-as-a-Service platforms has lowered the barrier for sophisticated cyberattacks, allowing groups like Dark Storm to execute them more easily. This makes it increasingly vital for organizations to implement next-generation threat intelligence and mitigation tools.
Dark Storm Impact on Industries
Government, Technology, and Transportation are at high risk among all sectors due to their critical infrastructure and strategic importance. These industries have become key targets for threat actors like Dark Storm, known for launching large-scale DDoS attacks aimed at disrupting essential services, eroding public trust, and advancing political agendas. Based on historical incidents and recent threat intelligence, the Industry Benchmark Threat Event Frequency (TEF)—which estimates the likelihood of a threat actor targeting organizations via a specific attack vector in a given industry —is highest across these three sectors:
Top Riskiest Industries
| Industry | Industry Benchmark Threat Event Frequency |
| Government | 4.19 |
| Technology | 3.97 |
| Transportation | 2.43 |
These TEF values highlight the urgent need for organizations in these sectors to adopt continuous threat monitoring, contextual risk modeling, and prioritized control implementation to stay ahead of emerging threats.
How can SAFE help combat Threats like Dark Storm?
As cyberattacks increase in frequency and sophistication, organizations need real-time, contextual, and intelligence-driven defense mechanisms. SAFE Security’s platform offers a proactive approach to cyber risk management, helping organizations detect and respond to evolving threats like those posed by the Dark Storm.
Safe’s Threat Research team actively tracks the behavior and activity of over 100 threat actors, consolidating threat intelligence from a wide range of sources, including open-source and commercial feeds, security blogs, industry reports, and social platforms like X and Telegram, where hacktivists and cybercriminals frequently share updates and coordinate attacks.
Factoring Threat Actor Activities for Risk Quantification and Management
To quantify and manage cyber risk effectively, it’s critical to understand how threat actors operate—specifically, the tactics and techniques they use during attacks. SAFE bridges this gap by mapping each threat actor’s known behaviors, as defined by MITRE ATT&CK, to relevant FAIR-CAM Controls that can reduce risk exposure. This mapping enhances the accuracy of risk modeling while enabling organizations to pinpoint control gaps and focus their security investments where they matter most.
ATT&CK techniques associated with Dark Storm and the relevant FAIR CAM controls available in SAFE:
| ATT&CK Techniques | Controls in SAFE | |
| T1595 | Active Scanning | Network Intrusion Detection and Prevention System (NIDS) Web Application Firewall (WAF) Network Firewall (NFW) |
| T1583 | Acquire Infrastructure | Secured Software (SSW) |
| T1584 | Compromise Infrastructure | |
| T1498 | Network Denial of Service | Application Performance Monitoring (APM) |
| Incident Response (IR) | ||
| Security Information and Event Management (SIEM) | ||
| Security Orchestration, Automation and Response (SOAR) | ||
| DDoS Protection (DDoS) | ||
Dark Storm Specific Risk Scenario Modeling in SAFE
SAFE streamlines the integration of threat actor activity into risk quantification through its Threat Center module. Organizations can easily access a curated list of relevant threat actors and begin monitoring them with a simple “Monitor” switch toggle.
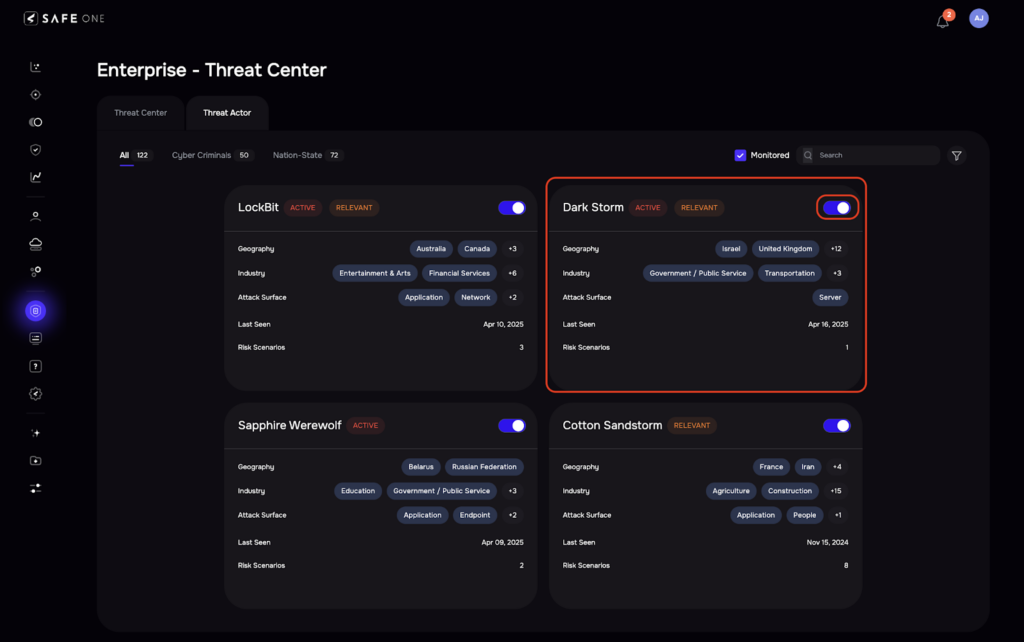
Once enabled, users can access a comprehensive profile for each threat actor.
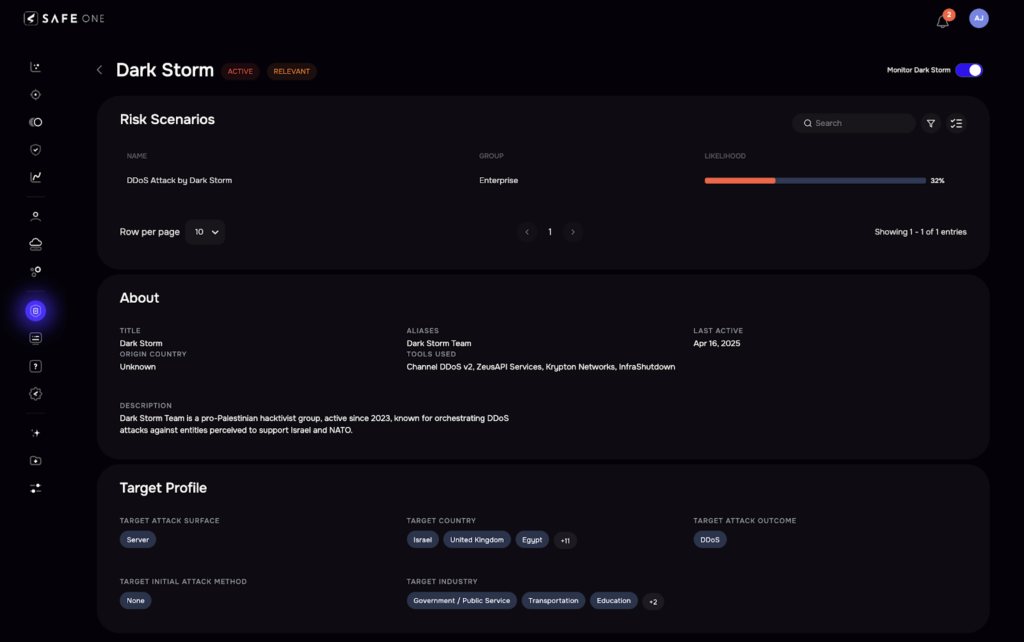
Users can observe the risk by viewing the system-generated risk scenarios for that threat actor under the “Risk Scenarios” section.
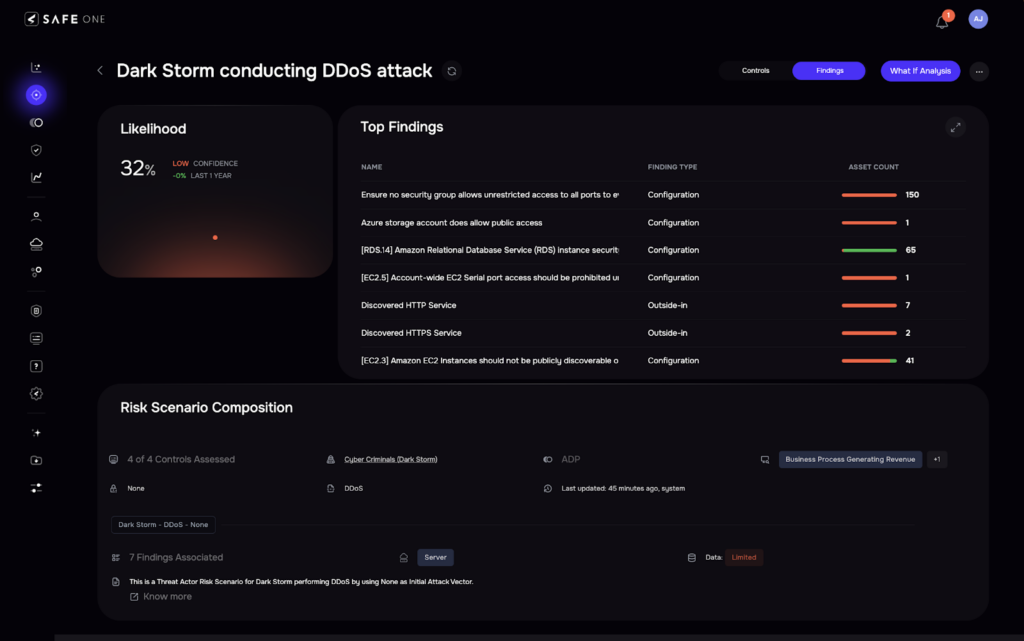
These scenarios are tailored using the threat actor’s known ATT&CK techniques, associated control coverage, asset-specific findings, and the organization’s current implementation maturity.
Risk scenarios offer detailed insights into the specific controls an organization should implement or prioritize and the potential likelihood and loss magnitude if the threat materializes. They also include control recommendations and enable ‘what-if’ analyses, helping organizations take proactive and informed actions to mitigate risks associated with each threat actor.
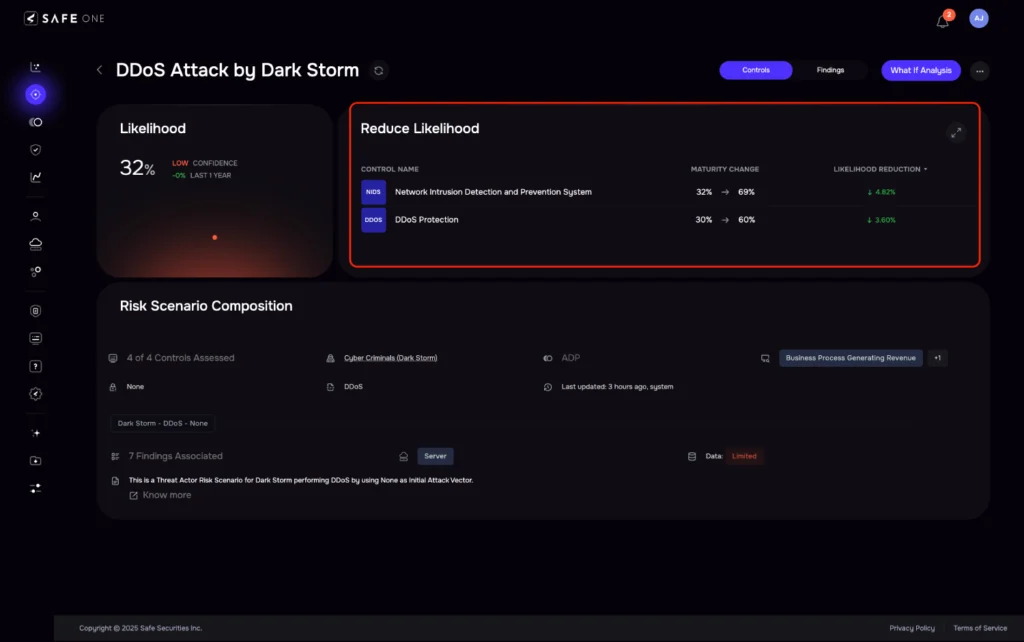
Conclusion
As threat actors like Dark Storm and other hacktivist and cybercriminal groups evolve and launch increasingly sophisticated campaigns, the importance of proactive risk monitoring has never been greater. Recent attacks targeting platforms such as X, Zoom, and Spotify highlight a rapidly shifting threat landscape, where cybercrime, hacktivism, and geopolitics often intersect.
SAFE empowers organizations to stay ahead of these threats through continuous threat actor monitoring, contextual risk modeling, and dynamically generated risk scenarios. By integrating real-time intelligence into measurable cyber risk metrics, SAFE enables security teams to prioritize the most impactful controls and drive informed, risk-based decisions.



