How Likely is Your Organization to be Breached?
Our four-step guide to measuring cyber risk in real-time
By Nimmi Sharma, Senior Data Scientist

If your Board was to ask you: How likely is a cyber attack on our business? Would you have an accurate answer? The solutions leaders rely on are unable to keep pace with mounting expectations. They only provide a point-in-time snapshot that becomes quickly outdated. Researchers argue that some techniques, such as risk matrices, can be “worse than useless, leading to worse-than-random decisions.”
CISOs across the globe are on the lookout for the best way to answer this question – quickly and accurately. But, to answer this question, you need to:
- Measure cyber risk posture in real-time
- Translate enterprise-wide security signals into risk
- Understand the threats and TTPs your business is up against
- Leverage external threat intelligence to remain ahead of the attacker
In this blog post, we’ll show you how to answer this crucial question in four steps and communicate cyber risk in a way your team, board, and investors will appreciate.
The four steps to take back control of your cyber risk management
Step One: Measure your cybersecurity risk posture
Your organization’s breach likelihood is the SI unit to measure its real-time cyber risk posture – how likely is the business to get breached? It answers a crucial question: What is the overall financial impact of cybersecurity risk?
Breach Likelihood = Threats x Vulnerabilities x Business Consequence
Breach likelihood is the glue that holds together your security teams, Board of Directors, C-Suite executives, investors, and other crucial stakeholders. Unfortunately, many risk management solutions use scores to summarize cyber risk posture, but the meaning and methodology behind these are obscured and opaque. Vague ratings and a failure to quantify risk lead to misinterpretation, leaving CISOs wide open to a variety of challenges, such as:
- Inaccurate or misleading view of cyber risk.
- Ineffective use of resources on initiatives with low return on security investment.
- Vague, inaccurate, or outdated data reported to boards and investors.
Your security team needs to rethink its approach to cyber risk management and communication. Shifting away from risk matrices and high-medium-low heat maps and moving towards real-time, always-on, and quantified breach-likelihood analyses will empower your team with:
- Visibilty: Discover where your most critical risks are and how much they could potentially cost your business.
- Dollar-driven prioritization: Add, adjust, or reduce investment in security initiatives based on tangible returns on security investment. Redirect precious human and financial resources to where they will create the greatest impact.
- Consistent communication: Integrate cybersecurity with your business risk. Secure Board and C-Level buy-in using relevant insights: What is the business risk reduction from your suggested measures?
SAFE, our Cyber Risk Quantification and Management (CRQM) platform, is designed to empower better visibility, ROI-driven prioritization, and effective communication of cyber risk.
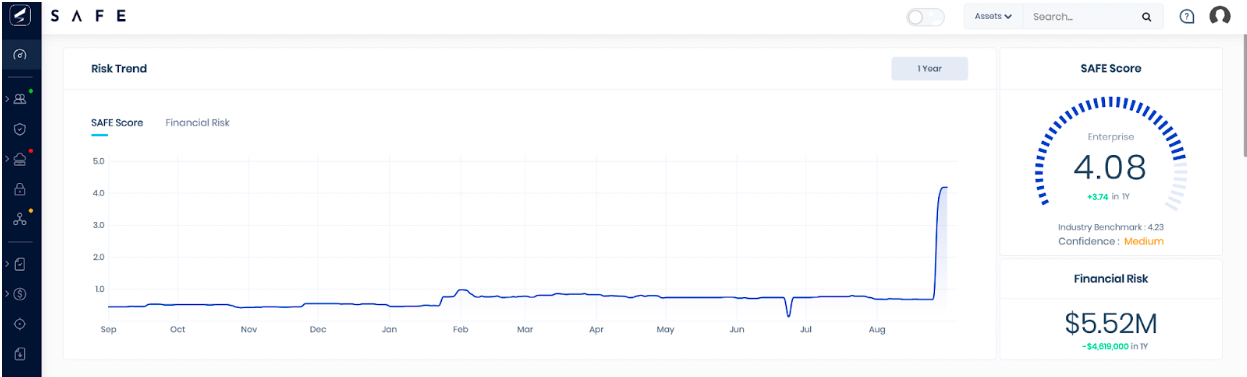
Within the SAFE platform, you have an always-on, real-time measurement of your organization’s cyber risk posture and breach likelihood – represented as your SAFE Score. SAFE leverages research-driven Bayesian Network analysis to compute your real-time cybersecurity risk. The higher the SAFE score, the lower the likelihood of your organization being breached. Going a step further, SAFE provides insights into the inherent risk you are exposed to in your industry. Using the ‘industry benchmark’ feature, you can evaluate your cybersecurity risk posture compared to your peers and adjust your strategy accordingly.
The confidence in the SAFE score is directly proportional to the quantity and quality of data provided as input. The more data available for the model to compute your breach likelihood, the higher the confidence will be, implying a more accurate estimation of breach likelihood.
Step Two: Translate enterprise-wide security signals into risk
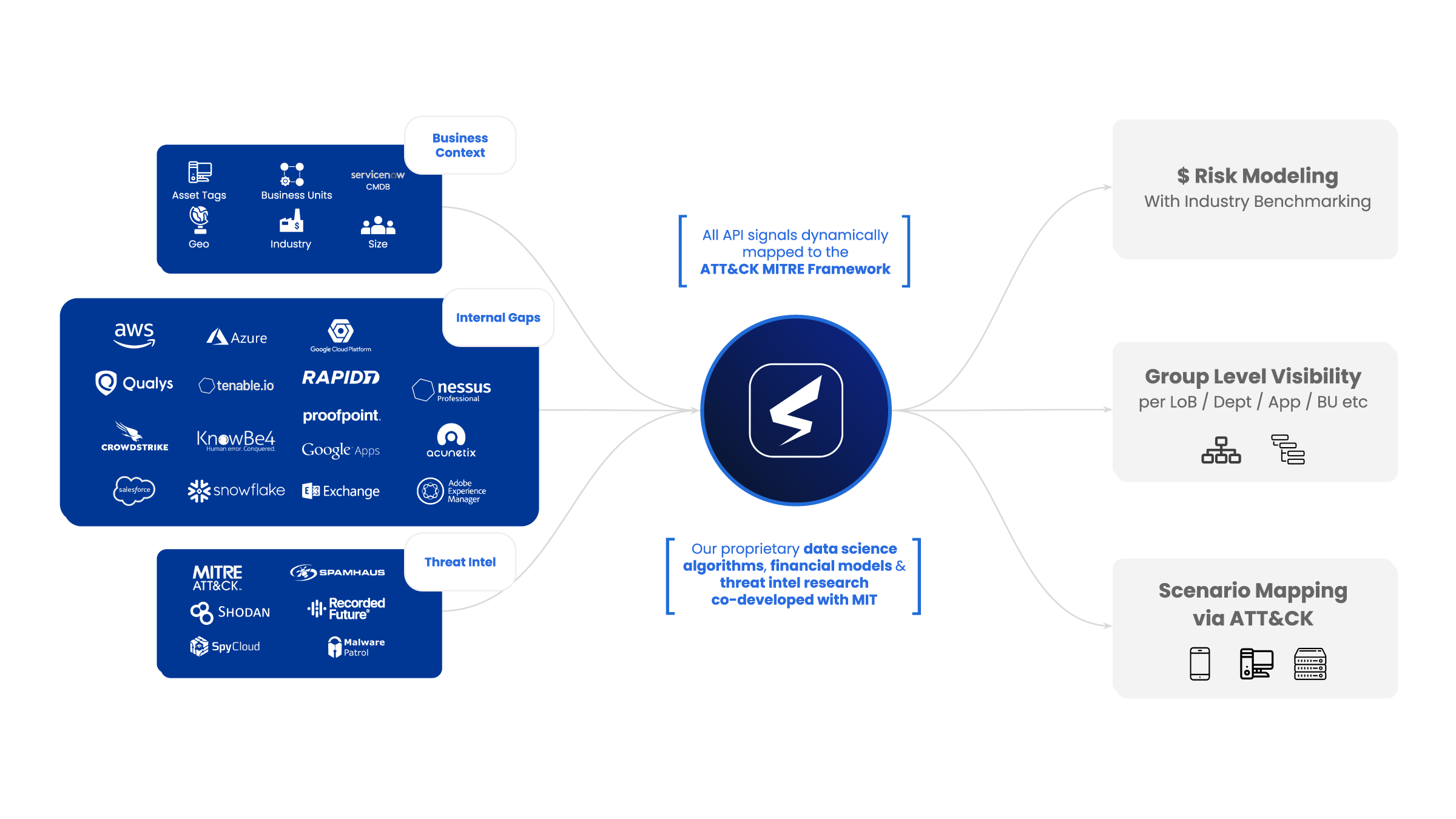
Today’s CISOs have to juggle multiple dashboards, reports, and readouts to determine their greatest cybersecurity risks. Data and risk are complex: there’s a lot of it, and it’s spread across multiple platforms and teams, making it increasingly difficult to manage. Although security information and event management (SIEM) may help centralize data, they don’t tell security and risk teams what to prioritize or how to act. So how can they make this data more actionable? The key is contextualizing signals as risk and categorizing signals based on business context. Doing so will help you measure the cyber risk across your business units.
The SAFE platform automatically aggregates and correlates signals across your cybersecurity programs, including configuration assessments, vulnerabilities, detected malware, outside-in assessments, policies, cybersecurity products, user behavior, user threat profile, user exposure, third-party risk assessments, and more. The output is real-time visibility of your breach likelihood per attack type and initial attack vectors. SAFE provides security and risk management leaders with a centralized dashboard that enables efficient cyber risk reporting.
Step Three: Leverage external threat intelligence to remain ahead of the attacker
Major threat actors are becoming ultra-organized and well-resourced. While security teams can be certain that they will face significant challenges to their external attack surface, they need to balance that with the risk they face within their organization.
An effective way to map vulnerabilities is to evaluate risk against established frameworks of adversary behavior, such as MITRE ATT&CK. Unlike other models, the MITRE ATT&CK framework intentionally adopts the mindset and perspective of an attacker and documents an extensive knowledge base of TTPs based on real-world observations. Not only will it help you understand how attackers could approach and execute an attack on your organization, but you can leverage it to determine where your cybersecurity exposures lie along the kill chain.
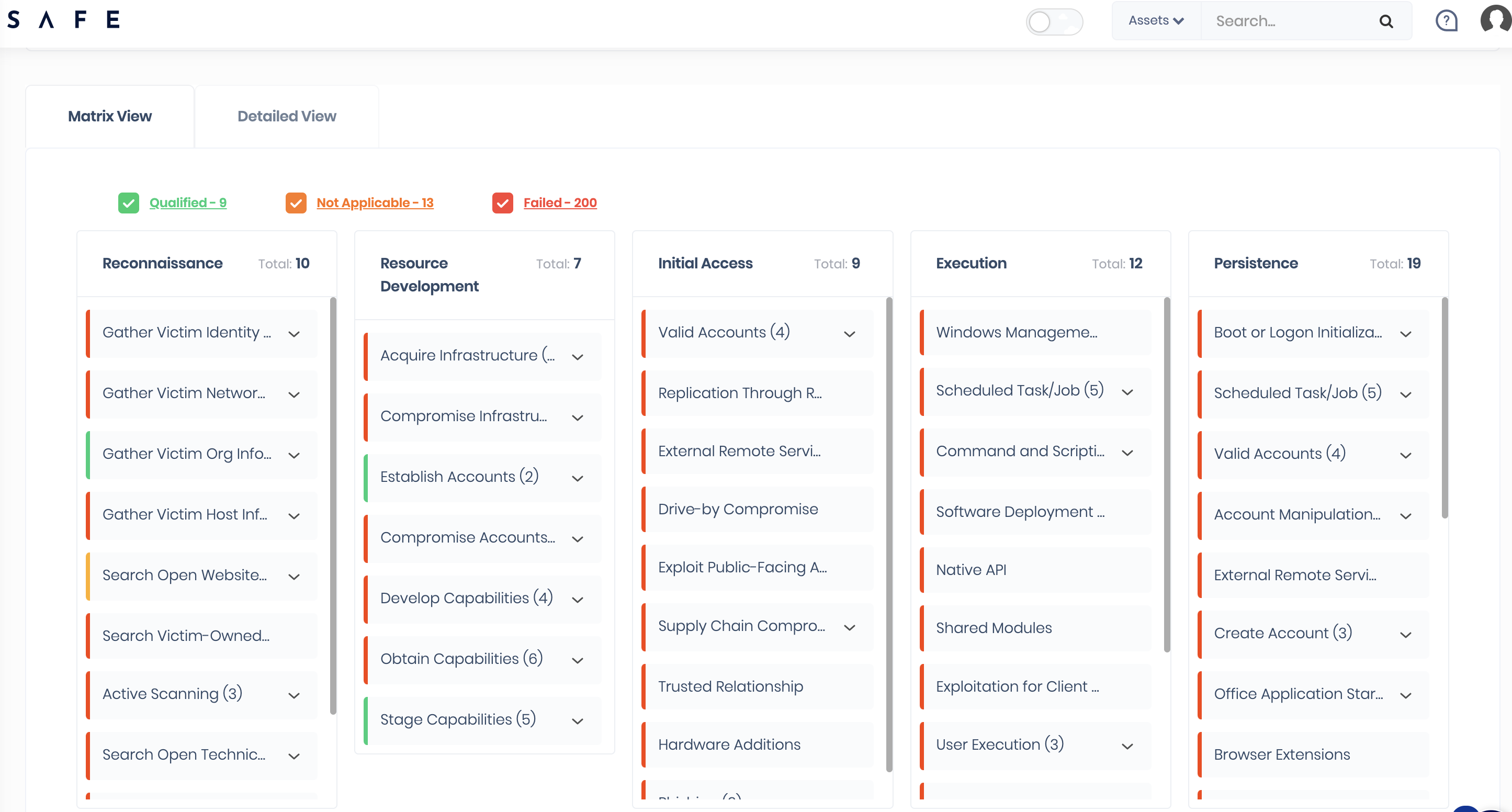
SAFE’s internal threat intelligence research team has mapped the MITRE ATT&CK framework to critical Cyber Risk scenarios to determine the prevalence of techniques across a multitude of attack types. Within the platform, you have complete visibility of your risk per attack type, with the ability to drill down into each one. The Cyber Risk Scenarios feature follows a three-step continuous, always-on, and AI-driven process:
- Identification: All techniques and sub-techniques related to particular attacks are identified, studied, and assessed using previous security incidents.
- Determining prevalence: SAFE calculates the frequency with which specific techniques and sub-techniques are used to exploit misconfigurations, vulnerabilities, or abuse system features.
- Correlation: SAFE correlates its master list of controls with the prevalence of each technique and sub-technique to enable prioritization of cyber risk management: what needs to be reconfigured, patched, or protected.
Step Four: Combine your organization’s inherent risk with external threat intelligence
Security leaders are increasingly pressured to turn their raw data into board-ready business insights. Never before has the C-Suite taken such a high interest in understanding its inherent and residual cyber risk.
Inherent risk is the cyber risk in your estate in the absence of controls. In other words, it is the risk encountered by an organization before it implements any countermeasures. Residual risk is the risk that remains after controls are implemented and successfully deployed.
Estimating the likelihood of a breach begins with understanding your organization’s inherent risk based on its geography, revenue, and industry. Manually analyzing the probability of attack by different vectors takes time, resources, and exhaustive research of public claims reports and loss data from security incidents. But the question remains: how do external security events correlate with your internal cybersecurity risk posture?
SAFE tackles this challenge successfully by:
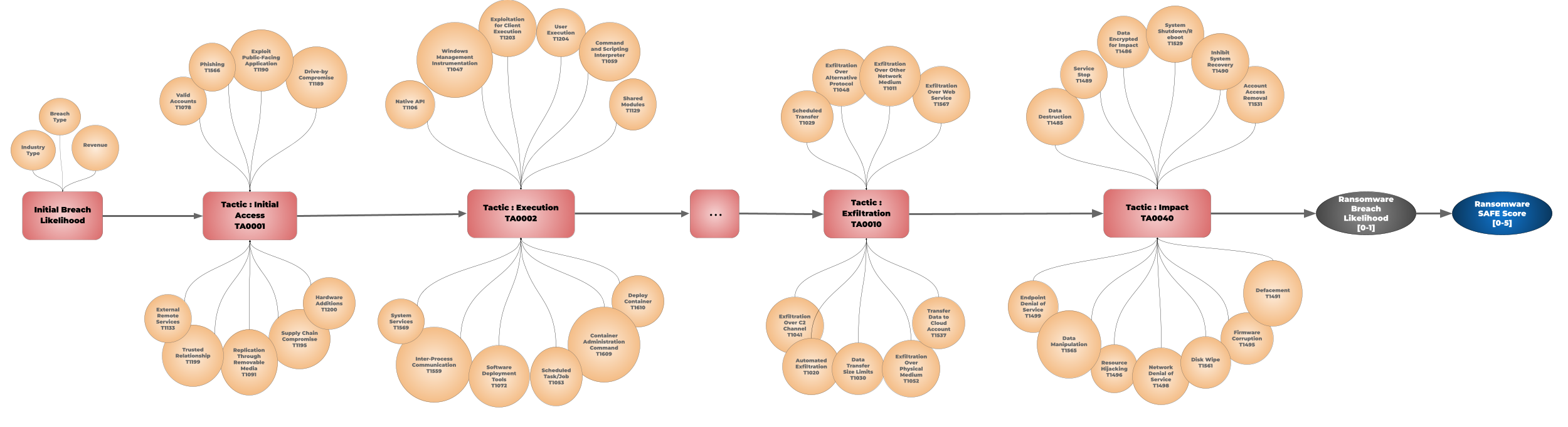
- Converting your security signals to cyber risk (using MITRE ATT&CK mapping)
- Estimating your risk exposure and calculating your breach likelihood (using its Bayesian network)
- Calculating the probability of a successful exploit for each technique
- Providing these insights across each key cyber risk scenario, for example, ransomware, business email compromise, data breaches, and more.
Recap: So, How Likely is Your Organization to be Breached?
Global organizations across industries use SAFE because it gives them the answer – accurately and in real-time. As you’ve discovered during this blog post, the SAFE platform helps you move from point-in-time assessments to continuous measurement, translate signals into risk, and to provide you with the vital intelligence needed to remain ahead of attackers.
We understand timing is critical, so we have designed our platform to be up and running and delivering tangible value in under 4 weeks.
Want to know more?
- See SAFE in Action: Request a Demo with one of our Cyber Risk Quantification Specialists.
- Explore the SAFE Path to Value: Crawl, Walk, Run, Fly
- Discover How to Manage Risk from Attack Surface Expansion
- Learn How to HALVE the Cost of a Data Breach with Cyber Risk Quantification



