By Jeff B. Copeland
NIST 800-30, ISO 27005, CIS Controls — If you’re looking to get a grip on the confusing web of cybersecurity standards and frameworks—and how FAIR (Factor Analysis of Information Risk) fits into the mix – Frank Kim explained it all in his recent talk at the 2019 RSA Conference.

Watch Frank Kim’s talk How to Make Sense of Cybersecurity Frameworks on the RSAC website (registration required).
Frank is the former CISO of the SANS Institute. He currently leads the management and software security curricula for SANS, the largest security training and certification organization in the world, and runs his own Thinksec CISO advisory firm.
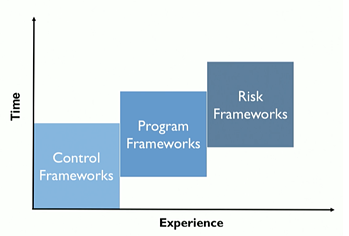
Frank separates the cybersecurity frameworks into three groups that security organizations adapt in turn as they mature.
Control Frameworks
These are the foundation of any security operation. NIST 800-53 is a complete list of controls, so complete no one would ever implement them all. The CIS controls help focus the list on the controls that mitigate 80% of the attacks
Program Frameworks
With the basics in place, security organizations need a way to talk to the rest of the business in non-technical terms. ISO 27001 goes beyond security specific controls to bring in business requirements but, Frank says, it’s costly and time-consuming to implement. The popular NIST CSF maps specific controls to each cybersecurity function, down to a high level of detail, with references to CIS and other frameworks for direction on execution but it’s still basically a checklist of good practices.
Risk Frameworks
The most experienced organizations move up “to analyze what your [stakeholders] actually want”, Frank said, an answer to the question: How much risk do we have? Risk frameworks such as NIST 800-39 outline a process for assessing and managing risk but have a limitation: They “keep it open ended” on how to actually measure risk, qualitatively or quantitatively or a hybrid of the two. “For many years, people said how would we go about measuring it in a quantitative way? This is where FAIR comes into play and it is a complement to those other risk management approaches.” Frank said that FAIR frees cyber risk professionals from limited thinking brought on by the conventional equation for risk.
Risk = Impact x Likelihood
Or, breaking down the right side…
Risk = Impact x (Vulnerability x Threat)
“When we manage risk, historically we in security have focused on which of these three components of risk? Vulnerability…
“It’s easy for us to scan our organization and find vulnerabilities…We’ve also got to think about the Threat and we’ve also got to think about the Impact, how bad is it to our organization.”
The FAIR model puts Vulnerability and the other factors of risk in a relationship that not only enables them to be quantified but requires that they all be considered to complete the picture of risk, adding up to FAIR’s reworking of the traditional equation to this statement:
Risk = Probable Frequency and Probable Magnitude of Loss Events
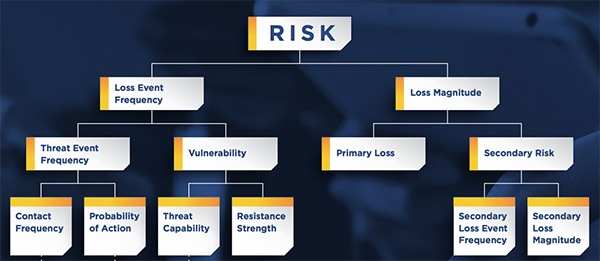
Frank Kim’s view — seeing FAIR at the top of the evolutionary scale for cyber risk management — is spreading. The SANS institute now offers FAIR training and the latest version of its CIS Controls poster, a handy guide used by many in the profession, covers FAIR.
Besides Frank’s presentation, the recent RSA Conference included many other signs of acceptance of cyber risk quantification, including the award given during the conference by SC Media, honoring the FAIR Institute as one of the three most important industry organizations of the last 30 years.