White Paper presents a detailed, data-driven approach to an ePHI risk management program

By Jacqueline Lebo
Executive Summary
This white paper outlines how SAFE provides a robust and comprehensive approach to achieving and maintaining compliance with the Health Insurance Portability and Accountability Act (HIPAA) Security Rule.
By offering continuous, automated risk assessment and quantification, SAFE empowers healthcare organizations and their business associates to proactively identify, prioritize, and mitigate risks to electronic Protected Health Information (ePHI). Leveraging a data-driven methodology, an industry-accepted framework, and advanced features like third-party risk management, SAFE facilitates clear communication with regulatory bodies, optimizes security investments through real-time ROI analysis, and ultimately enables organizations to confidently safeguard ePHI and meet the stringent requirements of HIPAA.
In this white paper:
Chapter 1: The HIPAA Requirements for Cybersecurity Risk Programs
Chapter 2: HIPAA Security Rule Elements of a Risk Analysis
Chapter 3: HIPAA Compliance with SAFE
>>Chart: Detailed Guide to How SAFE Supports Compliance
Chapter 4: Building a Roadmap for HIPAA Compliance with SAFE
>>Guide: 5 Steps to Compliance
Chapter 1: The HIPAA Requirements for Cybersecurity Risk Programs
The HIPAA Security Rule mandates that covered entities, including hospitals and healthcare systems, implement administrative, physical, and technical safeguards to ensure the confidentiality, integrity, and availability of electronic protected health information (ePHI). Compliance necessitates a comprehensive risk assessment, the development and implementation of security policies and procedures, and ongoing monitoring and evaluation. Due to the scalability of the rule, the methods of compliance will vary depending on the size and complexity of the healthcare organization. Here’s a breakdown of how different sized entities may approach compliance:
Small Clinics/Practices: Focus on fundamental security measures: (this may look like informal policies and best practices implemented in the office and reviewed annually)
- Implementing strong access controls (passwords, user roles).
- Regularly backing up ePHI and ensuring data encryption.
- Conducting basic risk assessments and workforce training.
- Using secure messaging and email.
Mid-Sized Hospitals/Healthcare Systems: Establish formal security programs: (including formal risk assessments)
- Designating a security officer and conducting regular risk analyses.
- Implementing robust access controls and audit trails.
- Developing incident response plans and disaster recovery procedures.
- Utilizing intrusion detection and prevention systems.
Large Healthcare Systems: Implement enterprise-wide security frameworks: (an external auditor may review the entire security program while also doing a formal review of all systems)
- Establishing comprehensive security governance and compliance programs.
- Utilizing advanced security technologies (e.g., security information and event management (SIEM) systems).
- Conducting regular security audits and penetration testing.
- Managing third-party risks and business associate agreements.
Chapter 2: HIPAA Security Rule Elements of a Risk Analysis
The HIPAA Security Rule mandates a comprehensive risk analysis as the foundational step for protecting electronic Protected Health Information (ePHI). This isn’t a one-time task but an ongoing process to identify and address potential threats and vulnerabilities to the confidentiality, integrity, and availability of ePHI. While the Rule doesn’t prescribe a specific methodology, it outlines key elements that any effective risk analysis must incorporate. Understanding these elements is crucial for organizations to achieve and maintain HIPAA compliance.
Here’s a breakdown of the essential elements of a HIPAA Security Rule risk analysis:
- Scope of the Analysis: The analysis must encompass all ePHI that the organization creates, receives, maintains, or transmits, regardless of the electronic medium (from workstations to complex networks and portable devices) or its location.
- Data Collection: Organizations must identify where ePHI is stored, received, maintained, or transmitted through methods like interviews, document reviews, and project analysis. This collected data must be documented.
- Identify and Document Potential Threats and Vulnerabilities: Organizations must identify and document reasonably anticipated threats (natural, human, environmental) and vulnerabilities that could be exploited, leading to inappropriate access or disclosure of ePHI.
- Assess Current Security Measures: The analysis must evaluate the security measures already in place to safeguard ePHI, determine if required controls are present, and if they are configured and used correctly. The appropriateness of these measures can vary based on organizational size.
- Determine the Likelihood of Threat Occurrence: Organizations must consider the probability of identified threats actually occurring. This likelihood assessment helps prioritize which threats require the most immediate attention.
- Determine the Potential Impact of Threat Occurrence: The analysis must assess the potential impact (criticality) if a threat exploits a vulnerability, affecting the confidentiality, integrity, or availability of ePHI. This can be qualitative or quantitative.
- Determine the Level of Risk: Based on the likelihood and impact assessments, organizations must assign risk levels to each threat and vulnerability combination. This helps in prioritizing mitigation efforts.
- Finalize Documentation: While HIPAA doesn’t mandate a specific format, the entire risk analysis process and its findings must be documented as it serves as a direct input to the risk management process.
- Periodic Review and Updates: Risk analysis is not static. Organizations must conduct ongoing reviews and updates, especially when new technologies or business operations are introduced, security incidents occur, or there are significant changes in the environment.
In summary, a thorough and ongoing risk analysis, as outlined by HIPAA, is the bedrock of Security Rule compliance. By systematically addressing each of these crucial elements, organizations gain a comprehensive understanding of their risks and can implement appropriate safeguards to protect ePHI.
How Does OCR Define “Risk” and Other Relevant Terms in HIPAA Requirement?
Risk
The potential for harm, this harm stems from the possibility of a “threat” exploiting a “vulnerability.”
A function of likelihood and impact: Specifically, risk is determined by the likelihood that a particular threat will exploit a vulnerability and the potential impact if that exploitation occurs.
Related to ePHI:In the HIPAA context, this harm specifically relates to the confidentiality, integrity, and availability of electronic protected health information (ePHI).
Threat
The potential for something to cause harm. It can be a person, an event, or a circumstance. Examples include hackers, natural disasters, or system failures.
Vulnerability
This is a weakness in a system that could be exploited by a threat. Examples include weak passwords, unpatched software, or lack of physical security.
Examples of OCR Enforcement:
Key areas where organizations commonly fall short, based on OCR enforcement actions:
- Incomplete Scope: Failing to assess all locations, devices, and systems where ePHI is stored, processed, or transmitted. This includes overlooking mobile devices, cloud storage, and business associate systems.
- Lack of Thoroughness: Conducting superficial assessments that don’t adequately identify all potential threats and vulnerabilities. This can include:
- Not considering internal threats, such as employee errors or malicious actions.
- Ignoring environmental threats, like natural disasters.
- Overlooking vulnerabilities in software and hardware.
- Failure to Document: Not properly documenting the risk assessment process and findings. This makes it difficult to demonstrate compliance and track progress.
- Insufficient Risk Management:Identifying risks but failing to implement appropriate safeguards to mitigate them. This includes:
- Not prioritizing risks based on their likelihood and impact.
- Delaying or neglecting to address identified vulnerabilities.
- Failing to regularly review and update risk assessments.
- Lack of Business Associate Agreements (BAAs): Failing to have proper BAA’s in place with third-party vendors that have access to ePHI. This is a very common failure point that OCR finds.
- Not Addressing known vulnerabilities: When OCR investigations find that a healthcare provider was aware of a vulnerability, and failed to take proper action to mitigate the risk. This shows a lack of due diligence.
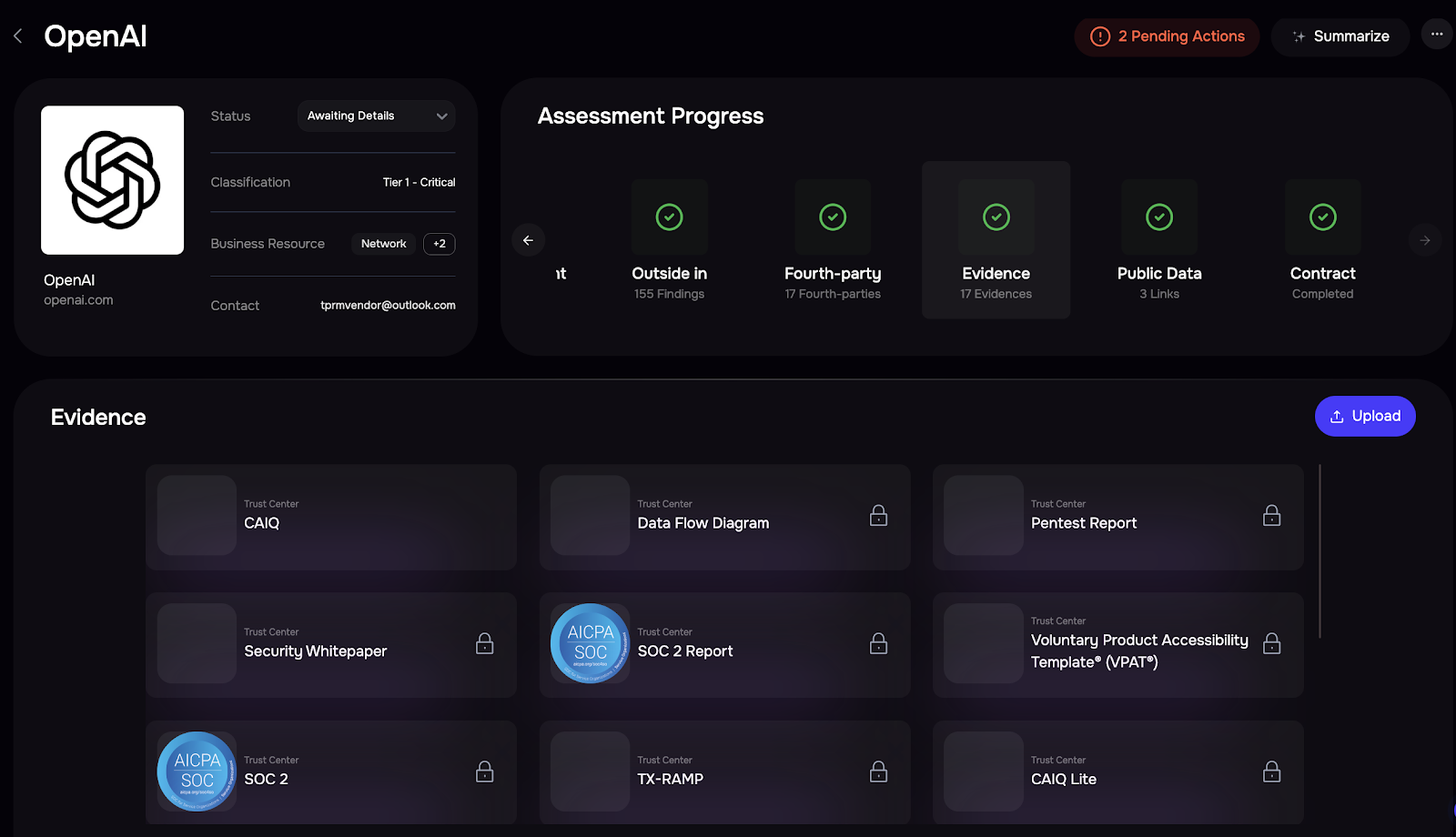
SAFE Platform: Continuous Risk Monitoring
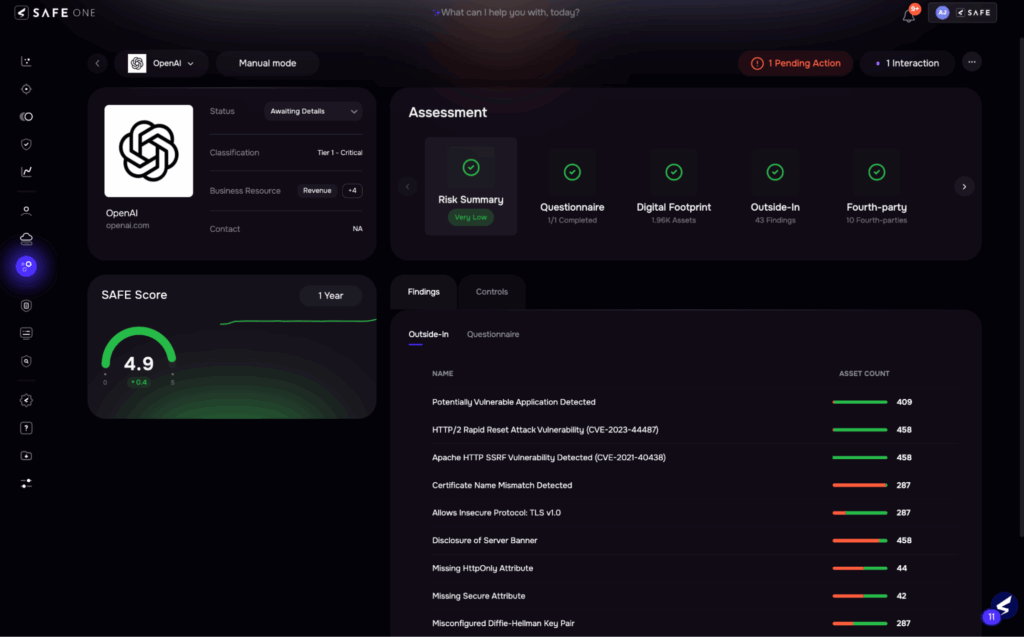
SAFE Platform Threat Center
See SAFE’s solution for HIPAA risk management compliance – Schedule a demo.
Chapter 3: HIPAA Compliance with SAFE
The SAFE platform facilitates HIPAA compliance by providing:
- Automated ePHI Asset Identification & Assessment: SAFE automatically identifies assets handling ePHI and facilitates risk assessments directly within the platform, covering all required scopes.
- Threat-Informed Risk Identification (CIA): SAFE identifies risks to confidentiality, availability, and integrity based on threat actors specifically targeting the healthcare industry.
- Continuous Risk Monitoring & Automated Control Validation: The platform continuously monitors risks and automatically validates security controls using data from existing security tools.
- Real-Time Financial Risk Analysis for Planning & Mitigation: SAFE provides financial quantification of risks, enabling informed decisions for both risk planning and mitigation strategies.
- Low Operational Overhead for Continuous Monitoring: The platform requires minimal manual input for ongoing risk monitoring, streamlining compliance efforts.
- Industry-Accepted Frameworks for Clear Communication: SAFE leverages industry-recognized frameworks including FAIR and MITRE ATT&CK, facilitating clearer communication and understanding with OCR during audits.
Detailed Guide on How SAFE Supports HIPAA Compliance
| Article Description | How SAFE Helps |
| § 164.308(a)(1)(i) Risk analysis (Required) Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information held by the covered entity or business associate. | Implements SAFE automates ePHI asset identification and provides a centralized platform for conducting thorough risk assessments. By leveraging healthcare-specific threat intelligence and continuous monitoring, SAFE ensures an accurate and up-to-date understanding of potential risks and vulnerabilities to the confidentiality, integrity, and availability of ePHI. |
| § 164.308(a)(1)(ii)(A) 2 Standard: Risk analysis Conduct a risk analysis that includes identifying the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information. | Implements SAFE facilitates this requirement by automatically identifying ePHI assets and providing a structured platform to document potential threats and vulnerabilities relevant to confidentiality, integrity, and availability. It leverages healthcare-specific threat intelligence to ensure the risk analysis focuses on pertinent risks to ePHI.Implements |
| § 164.308(a)(1)(ii)(B) Implementation specification: Risk management (Required) Implement security measures sufficient to reduce risks and vulnerabilities to a reasonable and appropriate level to comply with § 164.306(a). | Informs SAFE assists in implementing sufficient security measures by providing a prioritized list of risks based on financial impact, enabling organizations to focus on the most critical vulnerabilities. It also facilitates ROI analysis of different mitigation options, allowing for informed decisions on security investments to reduce risks to a reasonable and appropriate level |
| § 164.308(a)(1)(ii)(C) Implementation specification: Sanction policy (Required) Apply appropriate sanctions against workforce members who fail to comply with the security policies and procedures of the covered entity or business associate. | Informs SAFE informs this requirement by providing clear visibility into security risks and workforce-related vulnerabilities (such as phishing click rates), allowing organizations to identify areas of non-compliance with security policies. This data can inform the development and consistent application of appropriate sanctions against workforce members who fail to adhere to established security procedures. |
| § 164.308(a)(1)(ii)(D) 6 Implementation specification: Information system activity review (Required) Implement procedures to regularly review records of information system activity, such as audit logs, access reports, and security incident tracking reports. | Informs SAFE informs this requirement by providing a centralized platform that can integrate with and analyze data from various security tools. By offering a consolidated view and risk-based analysis of this information, SAFE highlights areas of potential concern and facilitates the regular review of system activity for anomalies and security incidents. |
§ 164.308(a)(5)(i) Implementation specification: Security awareness and training (Required) Implement a security awareness and training program for all members of its workforce (including management). That does the following: Security reminders (Addressable). (A) Periodic security updates.( B) Protection from malicious software (Addressable). Procedures for guarding against, detecting, and reporting malicious software. (C) Log-in monitoring (Addressable). Procedures for monitoring log-in attempts and reporting discrepancies. (D) Password management (Addressable). Procedures for creating, changing, and safeguarding passwords. | Informs SAFE informs the implementation of a security awareness and training program by providing data-driven insights into workforce-related risks and vulnerabilities. By identifying areas where users might be susceptible to threats (e.g., weak password practices, susceptibility to phishing based on simulated attacks – if integrated), SAFE can highlight specific topics that the training program should address. This allows organizations to tailor their security awareness efforts to the most pertinent risks identified within their environment, making the training more effective and targeted, and informing the content for security reminders and periodic updates. |
§ 164.308(a)(6) Implementation specification: Security incident procedures (Required) Implement policies and procedures to address security incidents. | Informs SAFE informs the implementation of security incident policies and procedures by providing a framework for understanding the financial impact of potential security incidents. By quantifying the risk associated with different types of incidents, SAFE helps organizations prioritize the development of response procedures for the most critical threats. Furthermore, the platform’s continuous monitoring and risk analysis can aid in the early detection and identification of potential security incidents, triggering established response protocols more effectively. |
| § 164.308(a)(7)Implementation specification: Contingency plan (Required) Establish (and implement as needed) policies and procedures for responding to an emergency or other occurrence (for example, fire, vandalism, system failure), that damages systems containing electronic protected health information. This includes data backup and disaster recovery plans. | Informs SAFE informs the establishment of emergency response, data backup, and disaster recovery policies and procedures by providing a clear understanding of the financial risks associated with system failures and data loss. By quantifying the potential business impact of such events on ePHI availability, SAFE helps organizations prioritize the development and implementation of robust backup and recovery plans. This financial perspective allows for better resource allocation in creating resilient systems and effective contingency procedures to minimize disruption and data loss during emergencies. |
| § 164.308(a)(8) Implementation specification: Evaluation (Required) Perform a periodic technical and nontechnical evaluation, based initially, and thereafter in response to environmental or operational changes affecting the security of electronic protected health information, that establishes the extent to which a covered entity’s or business associate’s security policies and procedures meet the requirements of this subpart. | Implements SAFE implements the periodic technical and non-technical evaluation requirement by providing a platform for ongoing monitoring and assessment of security controls and risks. It automates the collection of technical data from integrated security tools to continuously evaluate the effectiveness of implemented safeguards. Furthermore, the platform’s ability to track environmental and operational changes, and subsequently reassess risk in response to these changes, facilitates the “thereafter” aspect of the evaluation. This continuous evaluation, coupled with its reporting capabilities, establishes the extent to which an organization’s security policies and procedures meet HIPAA Security Rule requirements over time, not just at a single point. |
| § 164.308(a)(3)(i) Security reminders (Addressable) Periodically remind workforce members of security policies and procedures. | Informs SAFE informs the periodic reminders of security policies and procedures by providing insights into workforce-related risk areas and potential non-compliance. By identifying specific vulnerabilities or areas where user behavior contributes to risk (e.g., weak password usage trends, susceptibility to phishing in simulations), SAFE can highlight which security policies and procedures need reinforcement. This data-driven approach allows organizations to tailor their reminder campaigns to address the most relevant and pressing security concerns observed within their workforce, making the reminders more impactful and targeted. |
| § 164.308(b)Business associate contracts and other arrangements (Required) Document satisfactory assurances from its business associate(s), in accordance with § 164.314(a). | Informs SAFE informs the documentation of BAAs by identifying BA relationships via data mapping and facilitating security risk assessments through its third-party risk management capabilities. This enables organizations to track BAA status and understand the security risks associated with each BA, ensuring they obtain and maintain satisfactory assurances from these external entities. |
| § 164.306(a) General rules A covered entity or business associate must do the following: (1) Ensure the confidentiality, integrity, and availability of all electronic protected health information the covered entity or business associate creates, receives, maintains, or transmits. (2) Protect against any reasonably anticipated threats or hazards to the security or integrity of such information. (3) Protect against any reasonably anticipated uses or disclosures of such information that are not permitted or required under subpart E of this part. (4) Ensure compliance with this subpart by its workforce. | Informs SAFE’s Third-Party Risk Management solution informs this comprehensive HIPAA requirement by enabling organizations to assess and manage risks introduced by external partners who handle ePHI or impact critical infrastructure. By extending risk quantification and providing actionable data for third-party collaboration, SAFE helps ensure that the confidentiality, integrity, and availability of ePHI are protected across the entire ecosystem, contributing to overall HIPAA compliance. |
| § 164.306(b)(1) 13 Standards: General rules Covered entities and business associates may adopt any security measures that permit the covered entity or business associate to comply with the standards in this subpart. In deciding which security measures to use, a covered entity or business associate must take into account the following factors: (i) The size, complexity, and capabilities of the covered entity or business associate. (ii) The covered entity’s or the business associate’s technical infrastructure, hardware, and software security capabilities. (iii) The costs of security measures. (iv) The probability and criticality of potential risks to electronic protected health information. | Informs SAFE’s Third-Party Risk Management solution informs decisions on security measures by providing quantifiable risk data for both the organization and its third parties, factoring in the probability and criticality of potential risks to ePHI. This allows covered entities and business associates to make more informed decisions about security investments for themselves and their partners, considering the overall risk posture and the potential impact of third-party vulnerabilities on their ePHI. |
| § 164.316(b)(1) 15 Documentation (Required) Maintain a written or electronic record of the policies and procedures and actions required by this subpart. | Implements SAFE implements the requirement to maintain records by automatically documenting risk assessments, identified vulnerabilities, implemented controls, and remediation efforts within its platform. This centralized repository provides a comprehensive electronic record of the policies, procedures, and actions taken to comply with the HIPAA Security Rule, facilitating auditability and ongoing management. |
| § 164.316(b)(2)(iii) Standard: Updates to documentation (Required) Update the documentation as needed to reflect changes in the environment or circumstances that affect the security of electronic protected health information. | Implement SAFE implements the updating of documentation by continuously monitoring the security environment and automatically recording changes in risk scores, identified vulnerabilities, and implemented controls. This dynamic tracking ensures that the documented risk assessments and security posture are kept current, reflecting any alterations in the environment or circumstances impacting the security of ePHI. |
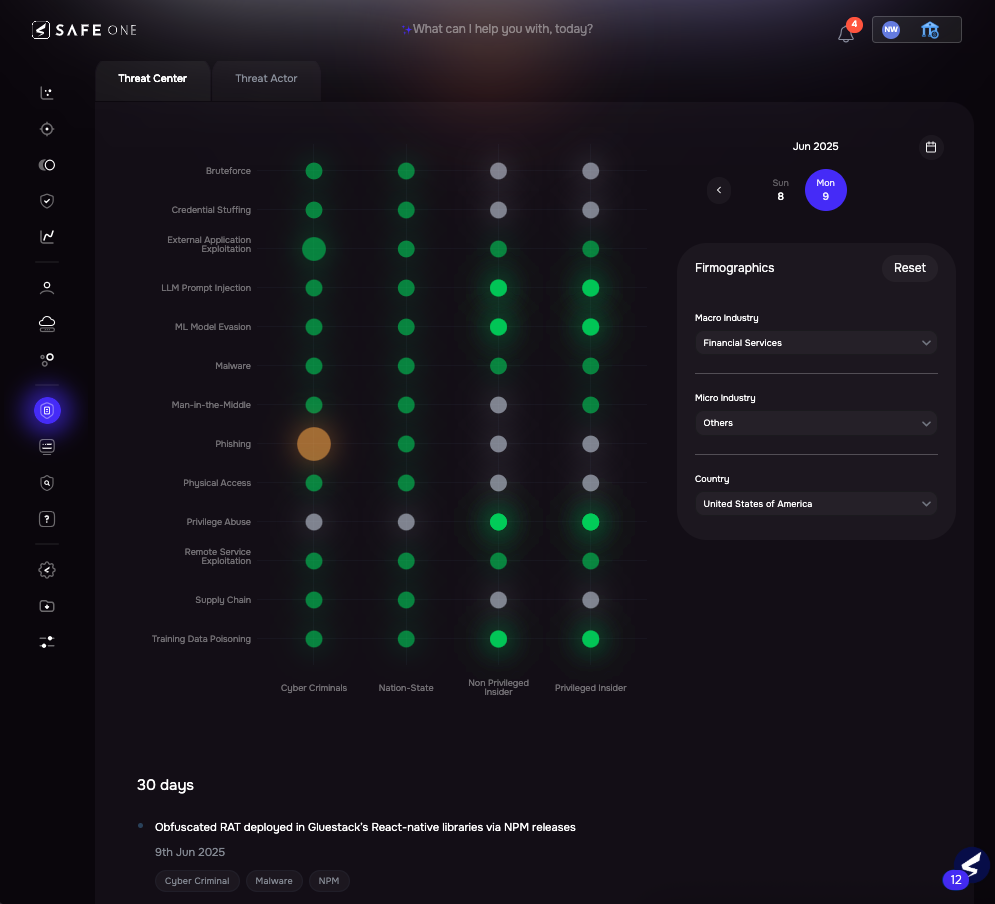
Risk Scenario Analysis, SAFE Platform
Chapter 4: Building a Roadmap for HIPAA Compliance with SAFE
Building a robust Cybersecurity Risk Management Program aligned with HIPAA is an ongoing journey. Organizations operate at varying levels of maturity, and the target state should be tailored to their specific needs and risk profiles. SAFE facilitates this journey, enabling organizations to achieve and maintain HIPAA compliance. Here’s a structured approach for CISOs and GRC leaders:
Step 0: Defining the “Why” and Securing Stakeholder Alignment (Including Scope)
Begin by articulating the rationale for pursuing HIPAA compliance and a robust CRMP. This “Why” should resonate with stakeholders and can encompass:
- Identifying the Scope of Assessment: Clearly define all systems, applications, devices, and locations where electronic Protected Health Information (ePHI) is created, received, maintained, or transmitted. This establishes the boundaries for the HIPAA compliance effort and the subsequent implementation of SAFE.
- Ensuring the confidentiality, integrity, and availability of electronic Protected Health Information (ePHI) as mandated by HIPAA.
- Establishing a data-driven framework for informed decision-making regarding ePHI security.
- Optimizing cybersecurity investments for better ROI in protecting ePHI.
- Meeting the specific governance and reporting obligations of the HIPAA Security Rule.
- Facilitating clearer communication with OCR during potential audits.
Document the “Why” and the defined scope of the ePHI environment, ensuring alignment among key stakeholders. Without this foundational agreement, implementation efforts may falter.
Step 1: Assessing Current Maturity against HIPAA Requirements (Leveraging SAFE for Risk Analysis)
We recommend using the HIPAA Security Rule itself as the framework to assess the current maturity of the organization’s ePHI protection program. Crucially, SAFE can be directly leveraged in this step to conduct the initial HIPAA risk analysis. This involves:
- Utilizing SAFE’s Automated ePHI Asset Identification & Assessment: SAFE automatically discovers and inventories the ePHI-handling assets identified in Step 0, ensuring comprehensive coverage for the risk analysis.
- Leveraging SAFE’s Threat-Informed Risk Identification (CIA): SAFE identifies potential threats and vulnerabilities relevant to the healthcare industry and the confidentiality, integrity, and availability of ePHI. This provides a structured and informed approach to identifying risks beyond generic cybersecurity threats.
- Conducting Assessments within SAFE: The platform facilitates the risk analysis process directly, allowing for the documentation of identified threats, vulnerabilities, and existing security measures associated with the in-scope ePHI assets.
- Initial Risk Scoring: SAFE provides an initial risk scoring based on identified factors, offering a preliminary understanding of the organization’s risk landscape related to ePHI.
Involve relevant stakeholders in reviewing the risk analysis outputs generated by SAFE to ensure a comprehensive understanding of the organization’s current state of ePHI protection within the defined scope.
Step 2: Defining and Aligning on the Target Maturity State for HIPAA Compliance
Establish the desired end state for cybersecurity maturity, considering HIPAA’s specific requirements and the defined scope of ePHI. This involves:
- Setting realistic and achievable goals for each HIPAA Security Rule requirement within the identified scope.
- Prioritizing areas that require immediate attention to address critical compliance gaps related to ePHI protection within the defined scope, informed by the initial risk analysis conducted with SAFE.
- Considering the organization’s risk tolerance, operational complexity, and the evolving threat landscape targeting healthcare data within the defined scope.
- Defining target maturity levels for both the risk management program itself (e.g., frequency of assessments, rigor of analysis) and the specific security controls used to protect the confidentiality, integrity, and availability of ePHI.
Do not allow resource constraints to limit the discussion of the ideal target state for ePHI protection within the defined scope. These constraints should be addressed in the execution plan.
Step 3: Identifying and Empowering Responsible Owners
Assign clear ownership for each workstream related to HIPAA compliance and ePHI protection within the defined scope. Ensure that:
- Owners are incentivized to achieve their assigned objectives related to HIPAA compliance within the defined scope.
- Owners are granted the necessary authority and resources to fulfill their responsibilities in safeguarding ePHI within the defined scope, potentially including access and training on SAFE.
- SAFE can assist owners by providing clear visibility into risks to ePHI within the defined scope, progress toward HIPAA compliance goals identified through the platform, and actionable data for remediation and control improvement.
Step 4: Developing a Sprint-Based Execution Plan for HIPAA Compliance (Maturing Program and Controls)
Create a tactical execution plan that:
- Breaks down HIPAA compliance efforts into manageable sprints focused on specific Security Rule requirements within the defined scope, utilizing the risk analysis output from SAFE to prioritize sprints.
- Identifies dependencies between different workstreams related to ePHI protection within the defined scope (e.g., risk assessment in SAFE preceding the implementation or enhancement of specific controls within the platform or other security tools).
- Establishes clear timelines and milestones for achieving target maturity levels for both the risk management program (e.g., increasing the sophistication of risk assessments within SAFE) and the security controls used to protect the confidentiality, integrity, and availability of ePHI (e.g., implementing stronger encryption, enhancing access controls based on SAFE’s risk insights).
- Incorporates the ongoing utilization of SAFE for continuous monitoring of ePHI risks within the defined scope, automated control validation to track the maturity of implemented safeguards, and third-party risk management for entities interacting with in-scope ePHI.
Consider utilizing a dedicated program manager to oversee the execution plan for HIPAA compliance across the defined scope, leveraging the reporting and tracking features within SAFE to monitor progress in both risk program maturity and control effectiveness. SAFE can assist in tracking progress towards HIPAA compliance within the defined scope, providing data to support the execution plan for both program and control maturation, and offering real-time ROI analysis for security investments related to ePHI protection across the defined scope, all within its integrated platform.
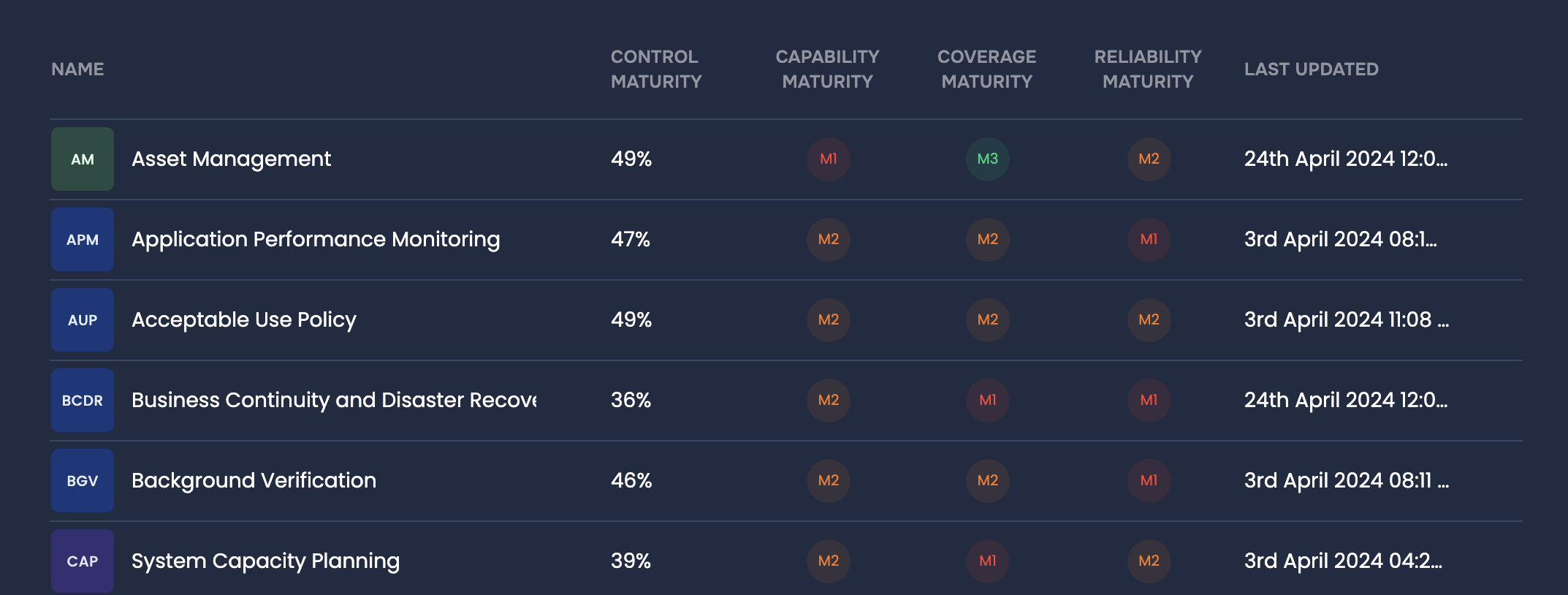
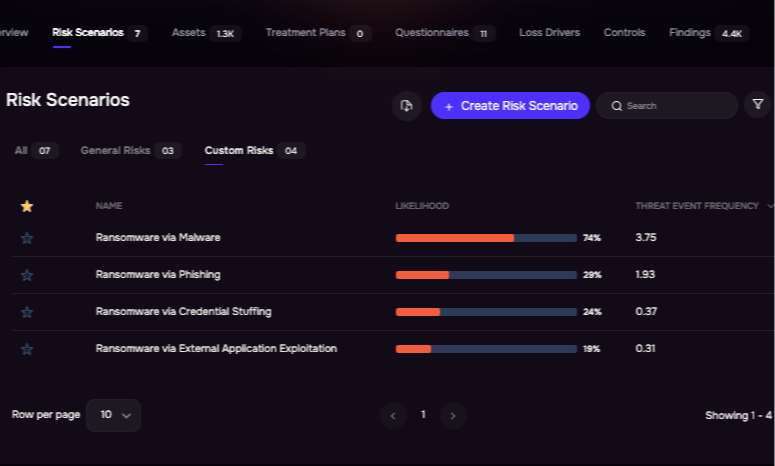
Controls Analysis, SAFE One Platform
Conclusion
Building a continuous Cybersecurity Risk Management Program aligned with HIPAA is essential for regulated organizations in the healthcare industry. The SAFE platform provides the necessary tools and capabilities to achieve and maintain compliance, enabling organizations to effectively manage cybersecurity risks and meet their regulatory obligations. By following a structured roadmap, CISOs and GRC leaders can leverage SAFE to enhance their cybersecurity posture and ensure ongoing compliance with HIPAA.
See how SAFE can advance your HIPAA compliance program — Schedule a demo!
Appendix
Resources
- The Security Series papers available on the Office for Civil Rights (OCR) website, http://www.hhs.gov/ocr/hipaa, contain a more detailed discussion of tools and methods available for risk analysis and risk management, as well as other Security Rule compliance requirements. Visit http://www.hhs.gov/ocr/hipaa for the latest guidance, FAQs and other information on the Security Rule.
Several other federal and non-federal organizations have developed materials that might be helpful to covered entities seeking to develop and implement risk analysis and risk management strategies. The Department of Health and Human Services does not endorse or recommend any particular risk analysis or risk management model. The documents referenced below do not constitute legally binding guidance for covered entities, nor does adherence to any or all of the standards contained in these materials prove substantial compliance with the risk analysis requirements of the Security Rule. Rather, the materials are presented as examples of frameworks and methodologies that some organizations use to guide their risk analysis efforts.
The National Institute of Standards and Technology (NIST), an agency of the United States Department of Commerce, is responsible for developing information security standards for federal agencies. NIST has produced a series of Special Publications, available at http://csrc.nist.gov/publications/PubsSPs.html, which provide information that is relevant to information technology security. These papers include:- Guide to Technical Aspects of Performing Information Security Assessments (SP800-115)
- Information Security Handbook: A Guide for Managers (SP800-100; Chapter 10 provides a Risk Management Framework and details steps in the risk management process)
- An Introductory Resource Guide for Implementing the Health Insurance Portability and Accountability Act (HIPAA) Security Rule (SP800-66; Part 3 links the NIST Risk Management Framework to components of the Security Rule)
- A draft publication, Managing Risk from Information Systems (SP800-39)
- The Office of the National Coordinator for Health Information Technology (ONC) has produced a risk assessment guide for small health care practices, called Reassessing Your Security Practices in a Health IT Environment
See SAFE’s solution for HIPAA risk management compliance – Schedule a demo.