How we get you up and running with SAFE in under 4 weeks
By Simone Sassoli, Chief Customer Officer

It’s no secret: life as a CISO is demanding. Challenges are increasing in volume and complexity, and more frequent, sophisticated cyber attacks are posing greater, unknown levels of risk to organizations.
This just scratches the surface. So, how do you tackle it? How do you build and execute a plan to address these challenges? The answer doesn’t lie in 30-60-90 day best practice mantras, hiring expensive consultants, or one-off programs with outputs that aren’t easily repeatable. Solutions take time to implement and see value from – if you find a way to measure that value, at all. .
As part of our mission to create a safer digital future we created a platform to help CISOs keep their companies safe – at speed. Attackers don’t hang around, and neither do we.
The SAFE Path to Value: Crawl, Walk, Run, Fly
In just four weeks, our expert teams are able to fully implement your advanced Cyber Risk Quantification and Management function. Within days, you begin experiencing the value of your investment. Let us walk you through the Crawl, Walk, Run, Fly approach, and discover the value you’ll see from week 1 to week 4, anchored by the key elements of our CRQM platform:
- Intelligent automation, powered by API signal-driven inputs
- Dynamic outputs, continuously updated in real-time
- Gathers signals across people, processes, technology, compliance, and third parties
- Incorporates every factor influencing financial impact, including cyber insurance
- Provides analysis across multiple types of initial attack vectors – all within a single dashboard
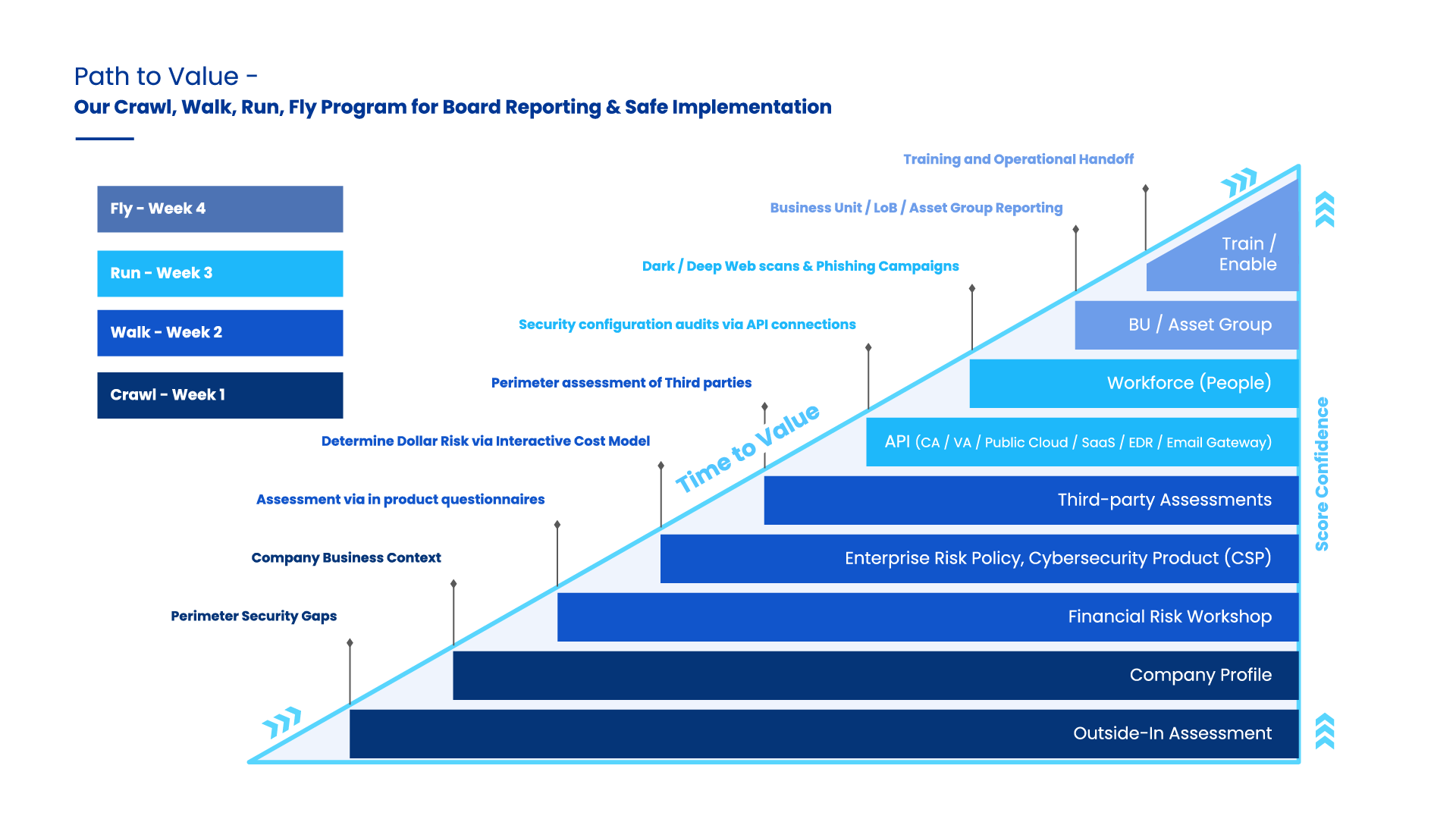
CRAWL: Value after Week 1
Welcome to SAFE. Take two simple steps along our path to value:
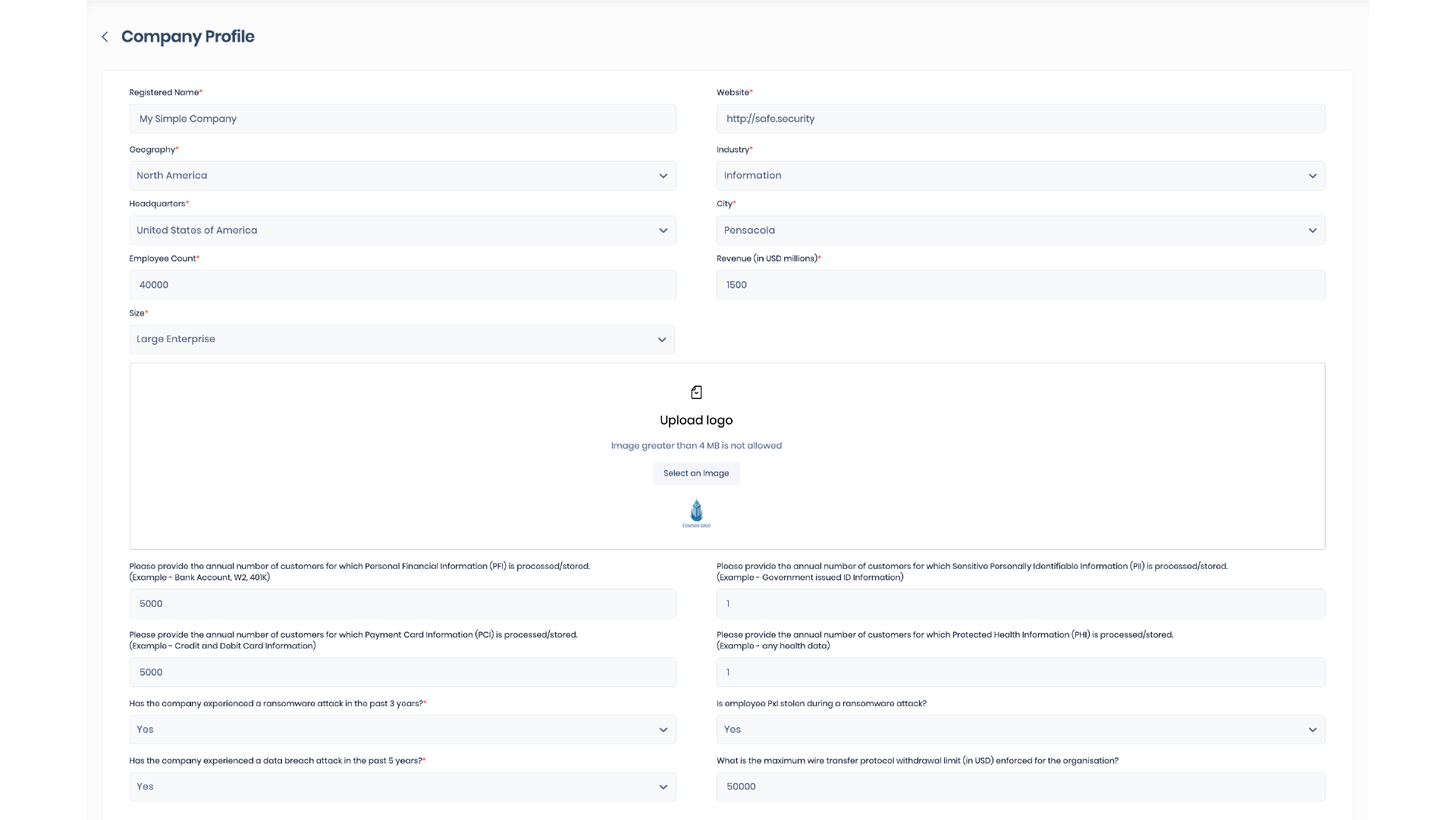
Company Profile and Outside-In Assessments.
During week 1, you answered a set of basic questions about your company. This input is used as the foundation for the initial financial, technical, and industry benchmarks outputs that are specific to your company.
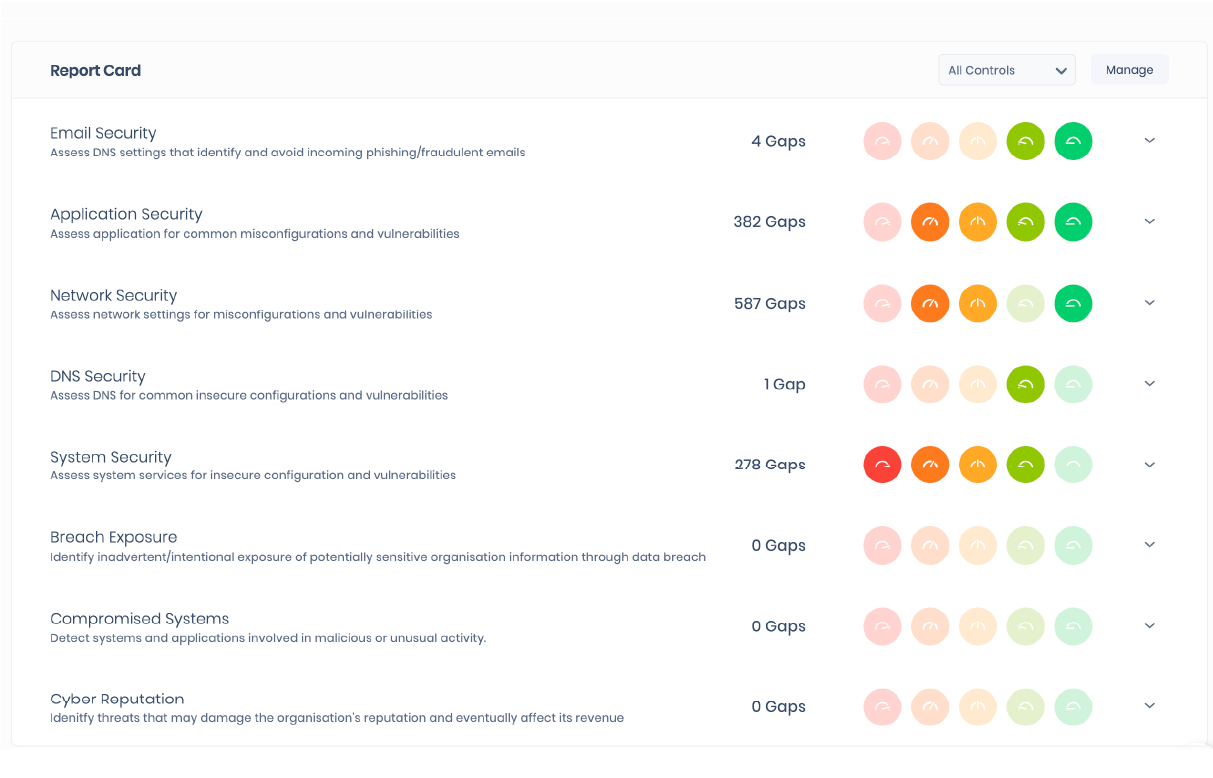
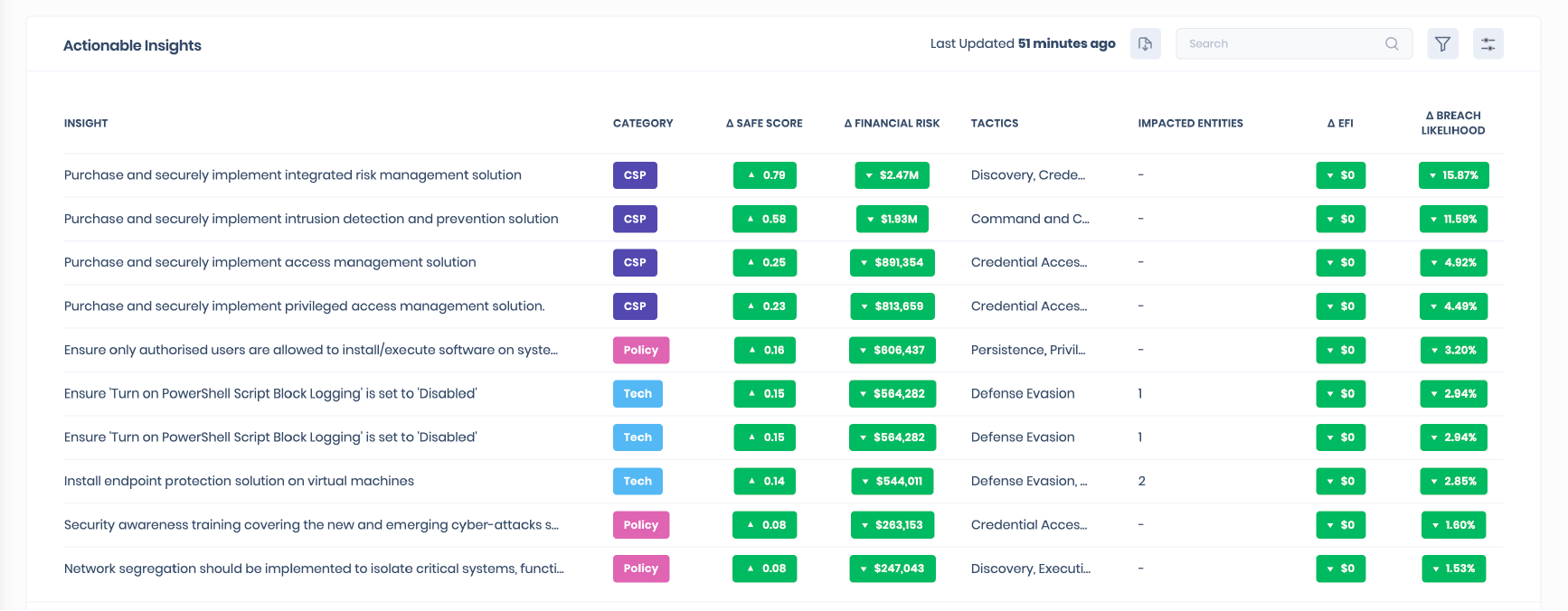
When you check the dashboard a few minutes later, your company’s external attack surface has already been scanned and your security gaps have been identified. You only need to verify that all domains are captured, then start reviewing and following the actionable insights for remediation.
WALK: Value after Week 2
Continue with three additional steps covering:
Financial Risk, Enterprise Risk Policy, and Cybersecurity Products.
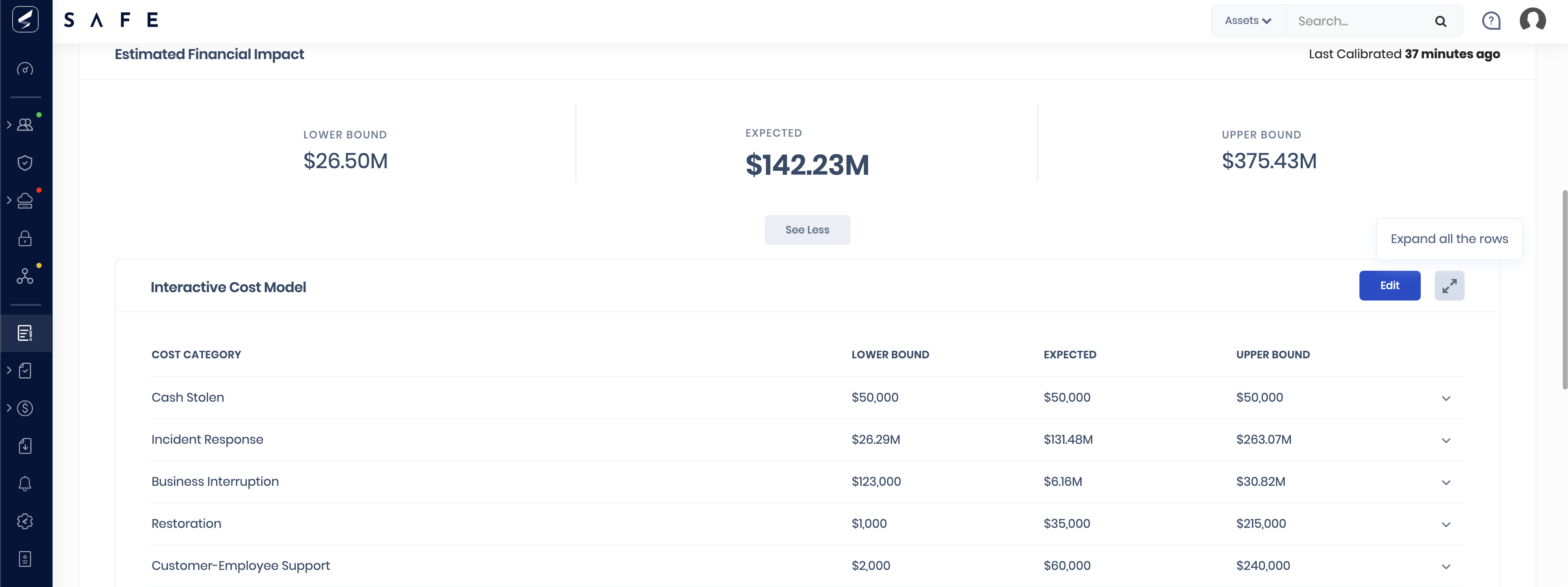
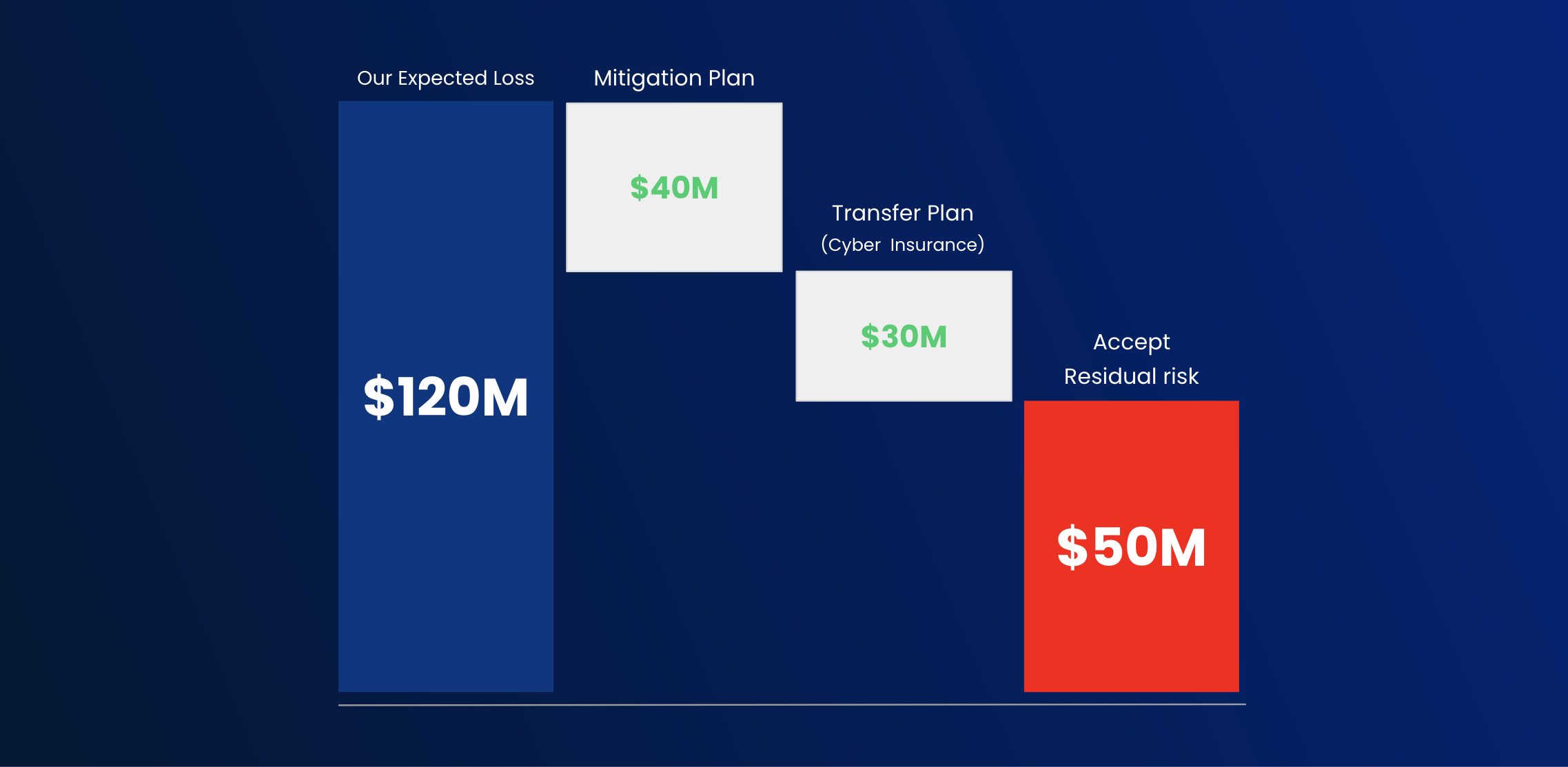
Now we’ll take a deeper dive into mapping cyber risk to financial risk during the Financial Risk Workshop. This can be done independently by the customer, but our Customer Success team is available to guide you. The drivers for the Interactive Cost Model (ICM) are tuned to your company’s own cost models to calculate the Estimated Financial Impact Range (EFIR).
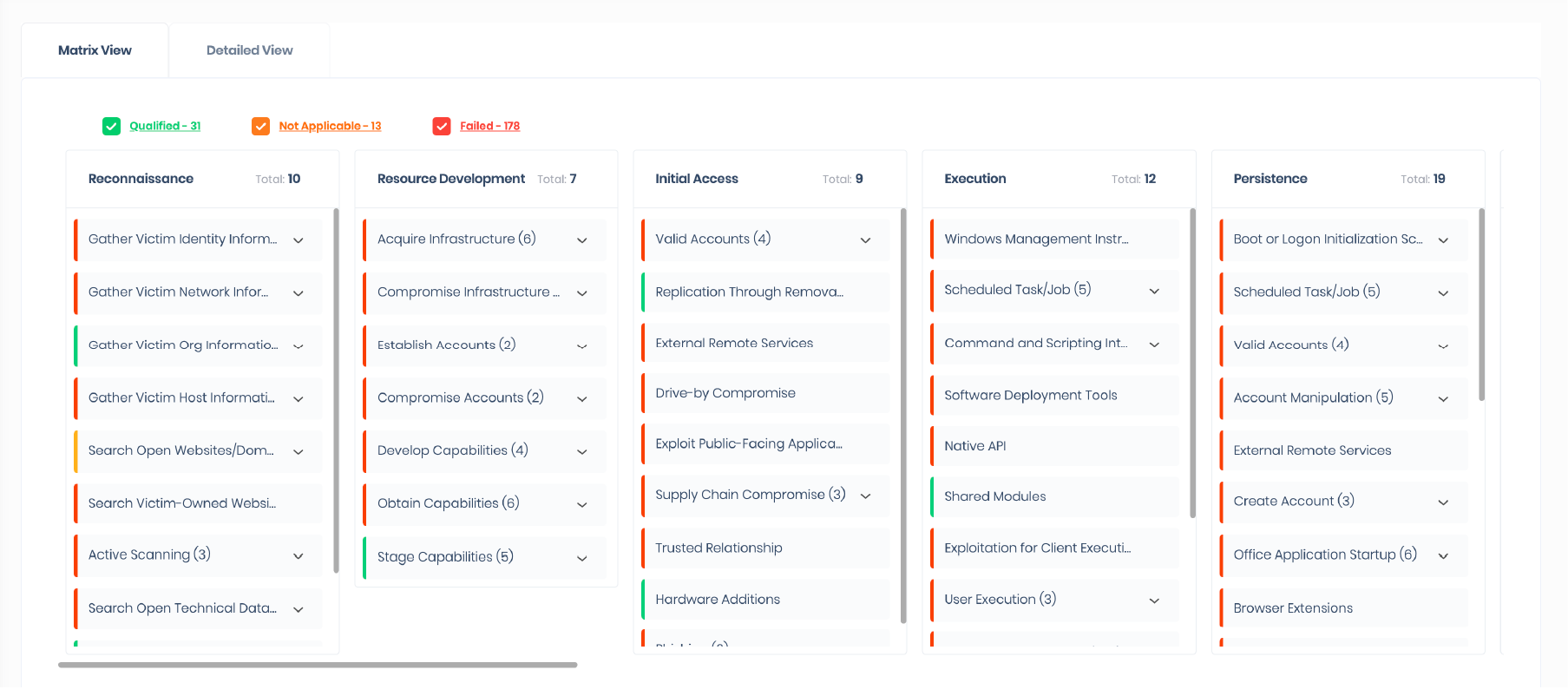
Next, we’ll assess the effectiveness of your company’s Enterprise Security Policy by asking 32 questions. Mapped to the MITRE ATT&CK framework, the answers you provide will map any gaps in policy to the corresponding Tactic, Technique, and Procedure (TTP) and reflect clearly within your SAFE platform dashboard.
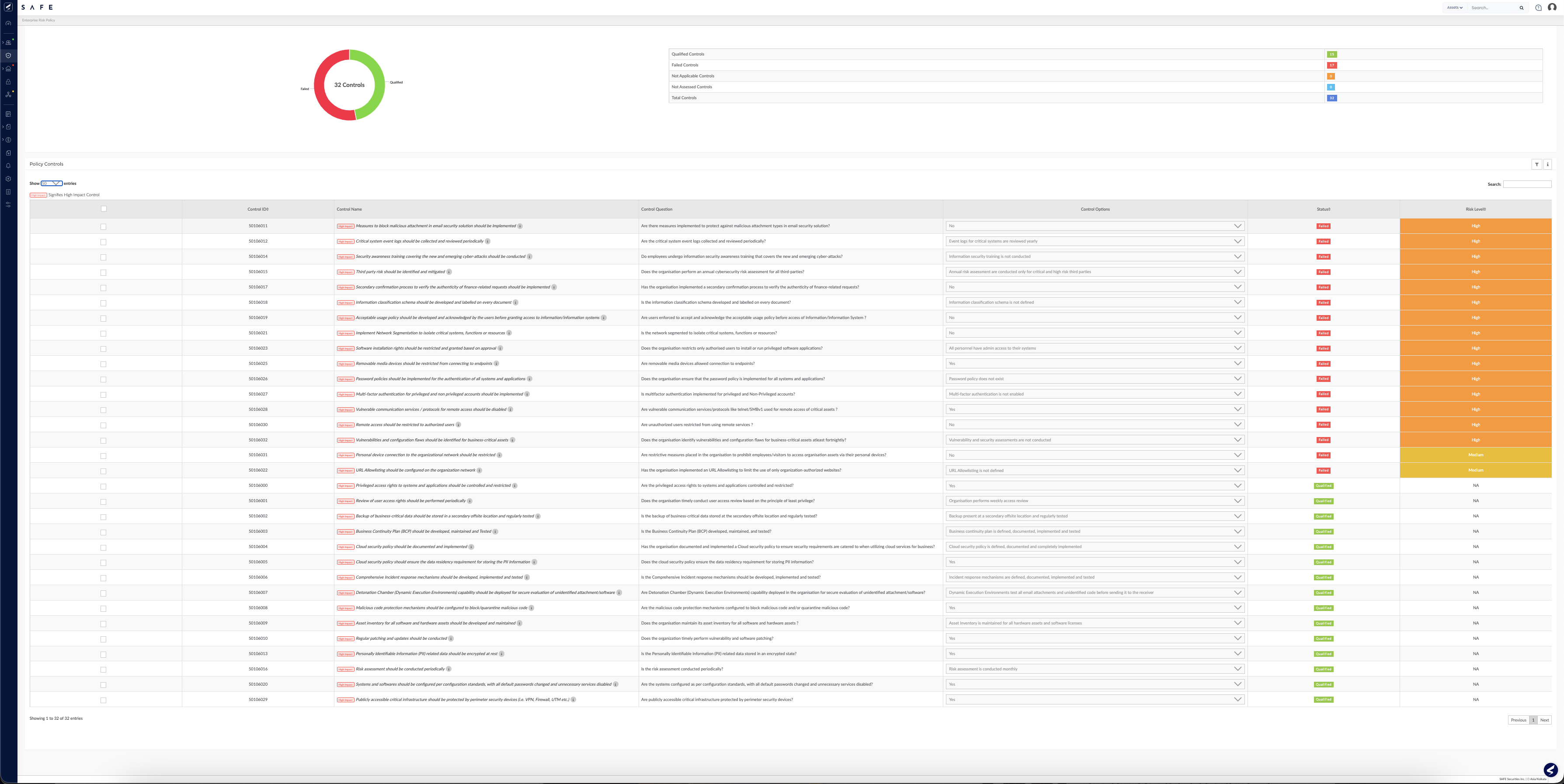
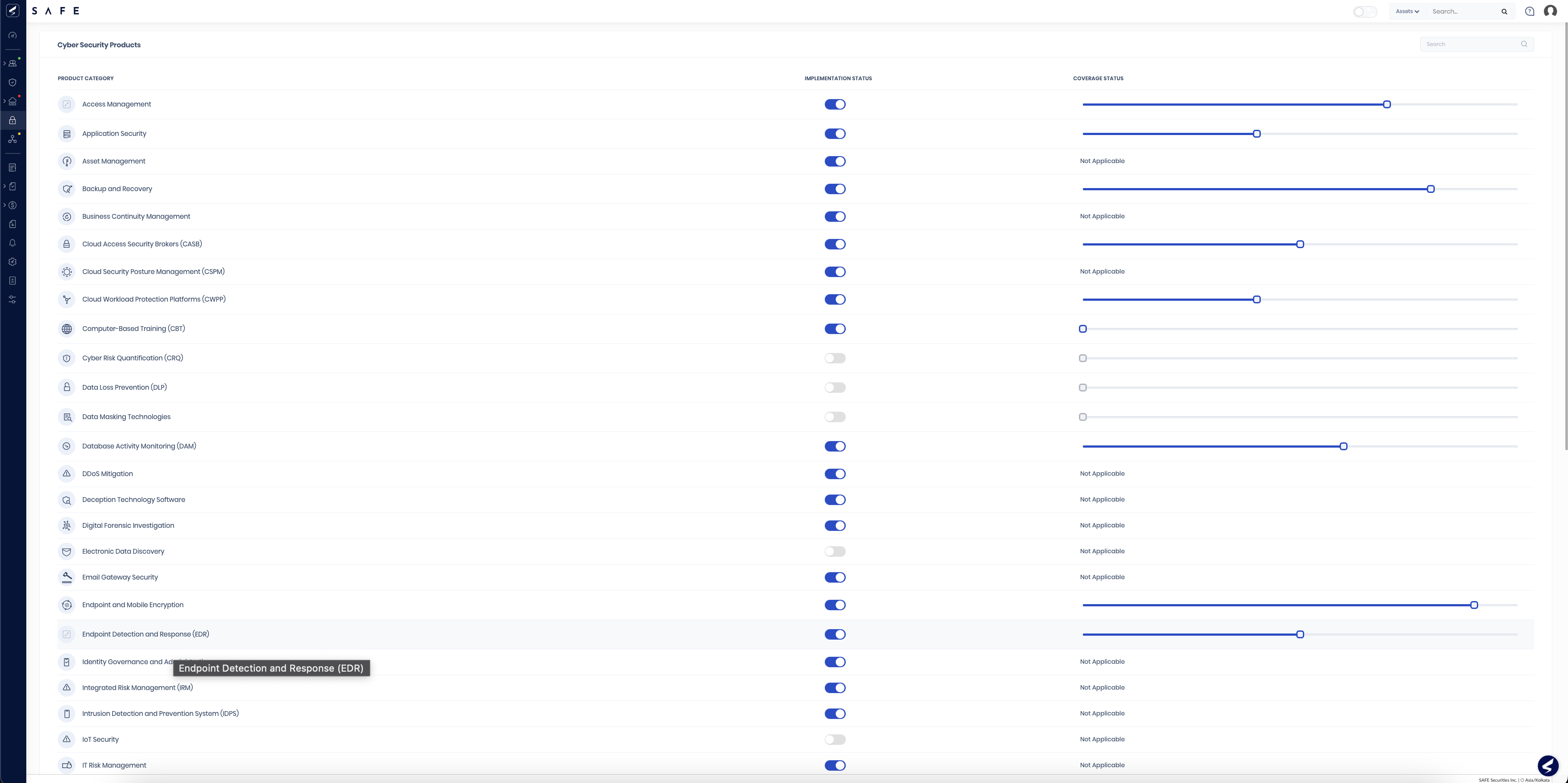
Continue on the value path and identify Cybersecurity Products (CSP) coverage in your enterprise. Simply select ‘product’ and update the percentage coverage on your CSP page. Each CSP has a number of questions – 33 in total – all mapped to MITRE ATT&CK.
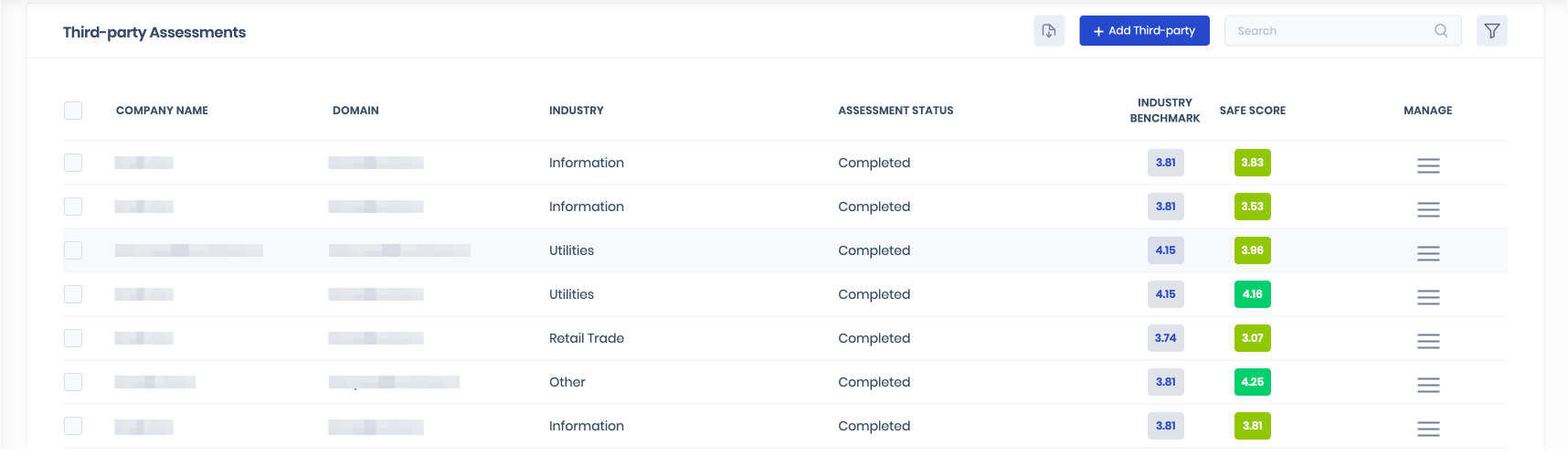
Finally, we’ll perform Third-Party Assessments. Simply add your business partners or supply chain vendors for risk monitoring by providing the company names, domains, and geographies. The results will return your external attack surface and associated security gaps.
RUN: Value after Week 3
During weeks 1 and 2, the focus has been on providing the SAFE platform with the appropriate context about your business. In the Run stage, the focus shifts to configuring technical signals via APIs from your environment and your workforce. The SAFE platform has a robust set of integrations that leverages your existing investment in security tools, like asset configurations (CA), vulnerability assessments (VA), endpoint detection and response (EDR), and many other signals.

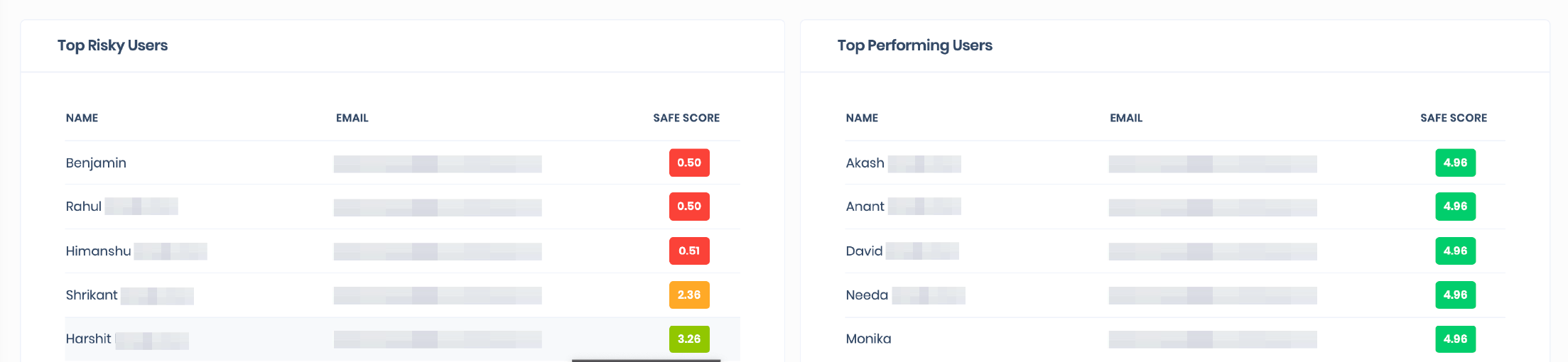
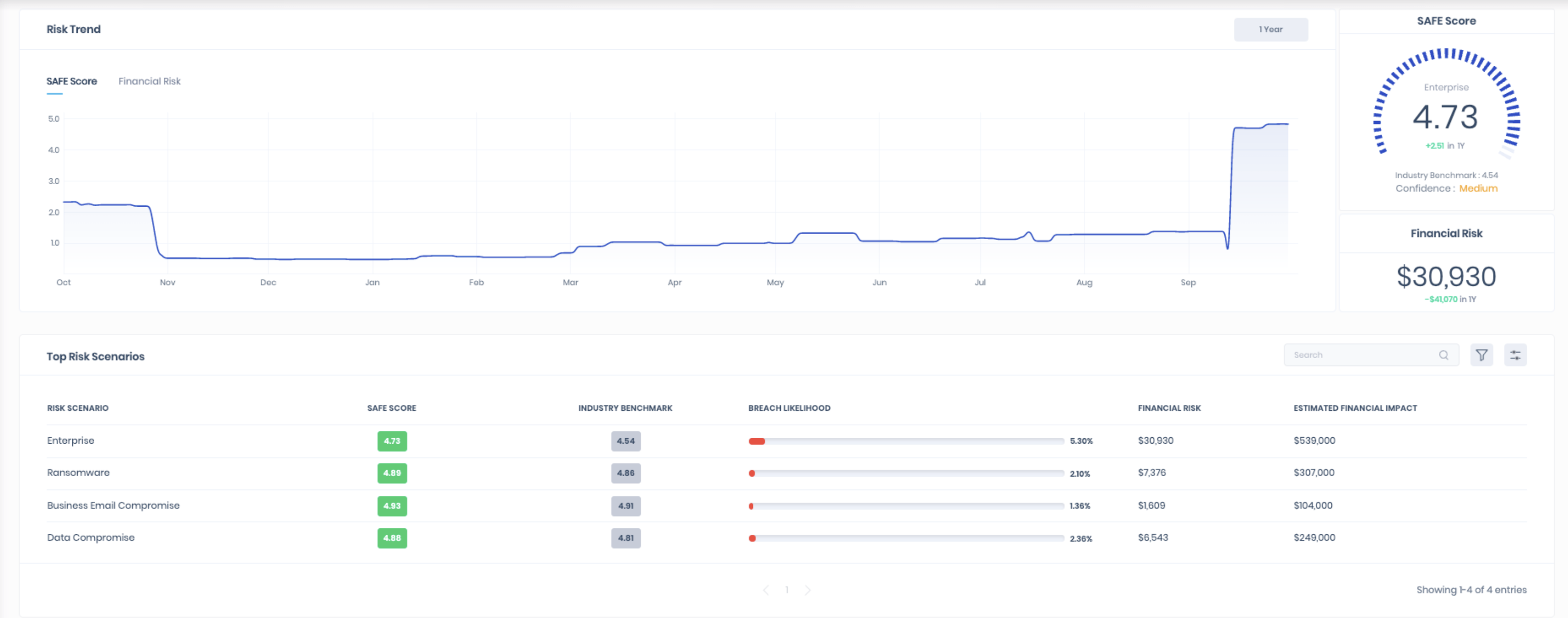
We make it easy to assess the cyber risk posture of your employees in real-time by monitoring the deep and dark web continuously for exposed credentials and personally identifiable information (PII). Either connect your Azure Active Directory environment or upload your user base via CSV file. The data from these integrations is used by the SAFE platform to calculate the likelihood of a breach on your environment presented as your company SAFE SCORE. Your SAFE score is an always-on, real-time calculation of your breach likelihood designed to help you understand your cyber risk posture at any given time.
FLY: Value after Week 4
You’ve reached the Fly stage! Your enterprise deployment is complete and you can continue organize your dashboard views based on how your business is organized: by Business Unit / Asset Group, or by creating custom groups. These are logical groups of assets based on line of business, applications, locations, criticality, technology, region, plus more. Creating custom groups and enhancing your powerful dashboards enable you to consume your data in a way that makes sense to you and your business. During this week, our expert customer success team will help you train the staff that will interact with your SAFE platform so you can maximize the value of your investment.
During this week, our expert customer success team will help you train the staff that will interact with your SAFE platform so you can maximize the value of your investment.
Continue leveraging the benefit of continuous, always visibility and prioritization:
- Discover ROI-driven prioritization of cybersecurity budget, investments, and insurance
- Integrate cybersecurity risk with business risk
- Effectively communicate cybersecurity risk and secure the buy-in of your Board and CXOs
Generate a Board Report Within Minutes Using SAFE’s Sample Board Report Template

Welcome to the summit – enjoy the views!
Armed with full visibility of your Cyber Risk posture and where you need to prioritize your efforts, SAFE unlocks your ability to prevent attacks on your organization through quantified cyber risk management. Equipped wiith powerful dashboards and visualizations, move from siloed, point-in-time assessments of risk to a real-time, always-on understanding. Here are some examples of the new tools in your arsenal:
To find out more about how SAFE can help your business:
- Request a walkthrough of the SAFE platform with one of our CRQM experts.
- Empower your board with a defensible dollar-value estimate of your financial risk due to cyber attack – with our FREE calculator.
- Identify and prioritize what gives your business the maximum Return on Security Investment – with our new ROSI calculator.



