How to Explain FAIR to Auditors
By Taylor Maze
When you think of risk (analysis, mitigation, remediation, etc.), what is the first word that comes to mind? If you thought “controls”, you’re probably an auditor.
If I am right, then I have some good news – you’re in good company. Prior to joining the RiskLens team and jumping into the risk quantification movement, I too was an auditor. If you’re anything like I was, then you might be a little hesitant to jump into the deep end of this whole cyber risk quantification thing. As auditors, we have controls, we like controls, and we feel as if our controls do a pretty darn good job of mitigating the cyber risks our organizations face. And luckily for us, most of the time we are right! However, there is more to the risk landscape than controls alone, which is where Factor Analysis of Information Risk (FAIR) comes into play.
I think you might actually really like the FAIR methodology. It combines a few really important things in the auditing world: defensible evidence, well defined risks, and (you’re really going to like this one) controls! If you still aren’t quite convinced – professional skepticism, trust but verify – I get that. Then read on.
In my previous life as an auditor, my sole focus was on controls. Were they in place? Were they appropriately designed? Were they functioning properly? If the answer was yes to all three, then my job was done, consider the risk mitigated. Or sometimes if my life was really exciting (I know, I need to get out more), one of the boxes wouldn’t be checked. In that case, additional procedures would need to be performed to determine if we believed the control could still be relied on. If we determined it couldn’t be relied on, then we would issue an exception, deviation, or deficiency and that was that. At the time, that made perfect sense to me. If the control does not work, then the risk is not mitigated, and risks are bad. When you’re bad, you’re penalized. Easy peasy.
That was my life up until about two months ago when I discovered RiskLens and FAIR and saw the light (cue a choir of angels). What I had never before truly considered was the overall risk we were assessing and its surrounding environment. It turns out that considering all of those factors is significantly more difficult than reading a control description, performing some tests, and checking the appropriate boxes, as I had done previously. That degree of complexity, among other things, is something that the FAIR methodology seeks to simplify.
Controls are important. I do not mean to trivialize them. Without controls the entire world as we know it would probably cease to exist. Controls are extremely important – they are just not the only thing that is important.
When utilizing FAIR, the overarching themes from auditing are still present: we are assessing the degree of cyber risk related to a particular asset (or more specifically loss event – but that comes later), we are asking the right questions to the right people in an attempt to gather the right information to come to an informed decision. The biggest difference is the questions we are asking. As I previously mentioned, the only questions I used to ask were related to specific controls: Do they exist? Are they designed well? Do they work?
I have since learned that the first (and arguably most important step) of assessing risk is to define it. In FAIR, you do exactly that.
The first thing you need to do is scope the scenario you would like to assess. The scoping process involves identifying the asset ( what do you want to protect?), the threat ( who or what are you protecting it from?), and the event or impact ( what are you concerned will happen if you do not properly protect it?). For example, if you are concerned with hackers stealing information then your risk scenario might look something like this:
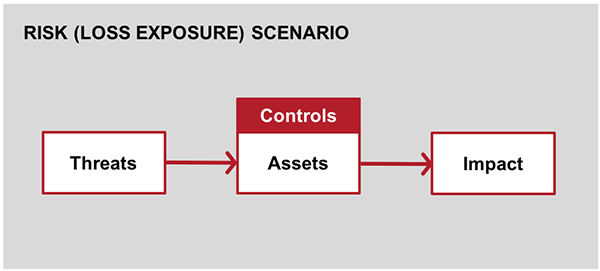
Okay, you have scoped the scenario, awesome! Now is it time to assess controls? Not quite.
After you have scoped your risk scenario, it is time to begin the analysis. This is where it is important to find the right people with the right information. There are two overarching things that are considered at this point: how often does the bad thing happen ( Loss Event Frequency) and how bad is it when it does happen ( Loss Magnitude). I won’t go into too much detail here, but in order to determine these things, often it is necessary to consider additional components such as the Vulnerability of the asset in the scenario.
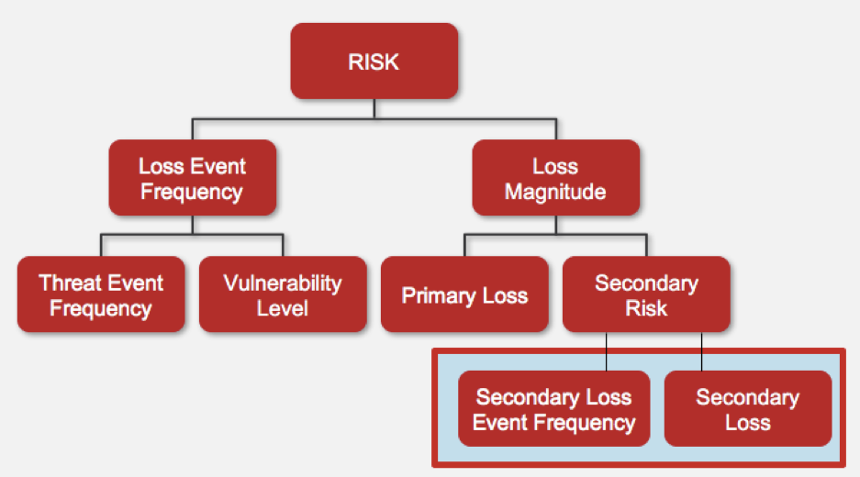
Vulnerability is made up of two things: Threat Capability (how strong are they?) and Resistance Strength (how strong are you?). Are your auditor senses tingling? If you’re thinking that Resistance Strength sounds a lot like controls, then you’re right! This is one of the many areas in the FAIR model where controls come into play. This is where you get to ask those questions you have been dying to ask:
- What controls (if any) are in place?
- Are they designed and implemented appropriately?
- How effective are they?
That last question related to how effective the controls are boils down to the essence of Resistance Strength. There are also many other places you can model controls with FAIR, such as related to Threat Event Frequency (how often does something happen that could cause the loss event?). Can you think of some controls that could reduce this number? If so, they could be modeled here.
To circle back to what I mentioned above – controls are vital to organizations. It is important they are appropriately designed, implemented, and assessed to ensure they are performing their designed purpose, which is why auditors are so important. But what happens if the control fails? Other than the auditing implications (exceptions, deviations, deficiencies, etc.), what happens to the organization itself? Will there be losses sustained? If so, to what extent? What would they be related to? These are questions I had never considered prior to joining RiskLens; but are incredibly relevant and need to be considered.
If you can’t answer those questions (and don’t worry if you can’t – most people couldn’t!), it might be time to consider performing some risk analysis. Utilizing the FAIR framework and tools such as RiskLens Cyber Risk Quantification (CRQ) allows you to see the bigger picture of the risks your organization is facing, rather than strictly having a controls focus.



