How TPRM Leaders Can Effectively Partner with Business Stakeholders
Stop thinking like a process manager, start thinking like a risk expert
By Vince Dasta
The life of a third-party cyber risk manager can be a frustrating one. You want to protect and add value to the business. But often you’re just waving the vendors through a process of attestations about their processes or one-click scans of a partial list of their controls to generate a simple high/medium/low score. Also often, the vendor has been approved by the organization before you even get to run your assessment.
How can you turn third party cyber risk management (TPRM) into something truly useful to your stakeholders? We asked Vince Dasta, a veteran of many implementations of SAFE’s TPRM solution (more on that below) and here is his advice:
Achieve Effective TPRM in 5 Steps
1. “Stop thinking like a process manager, start thinking like a risk analyst”
Stop accepting the output of scans and checklists as a risk assessment – and stop chasing down every little deficiency that they turn up. Start speaking in risk terms, specifically likelihood and impact of a supply chain disruption. If those little deficiencies don’t significantly affect either of those major variables then move on. (FAIR is the definitive method for quantifying likelihood/impact risk scenarios.)
2. “Understand the business and how the third party in question fits in”
A good place to start is by asking your business stakeholders about any mission-critical processes the vendor would support. To speak in risk terms, is there availability risk, and how serious? If your organization will set itself up for a single point of failure (think of the recent outage of CrowdStrike’s endpoint security software or UnitedHealth’s billing system), those could be serious indeed.

Redundancy check on the SAFE One cyber risk management platform.
3. “Redundancy, indemnity: Not all risk scenarios are created equal”
A corollary to #3. While conventional TPRM software may send you off on a fruitless chase to patch minor vulnerabilities at vendors, take a wider focus first by thinking through the impact of the scenarios that most concern you. Yes, you may be heavily dependent on one vendor, but do you have relationships with others in place as redundancies? Secondly, check the indemnification clauses in your contracts – loss from an outage at one third party might be well covered by contract.
4. “Don’t get boxed in by the standard third-party risk assessment routine. Creatively prove your value to the business”
If the risk assessment process turns up findings, advise business stakeholders to use them as leverage to negotiate a higher indemnity payout or some concession on pricing. Particularly if a vendor has been blocked from onboarding by a slow approval process, show how a risk-based approach can reduce cycle time by reducing or even eliminating the risk assessment effort (see Steps 2 and 3).
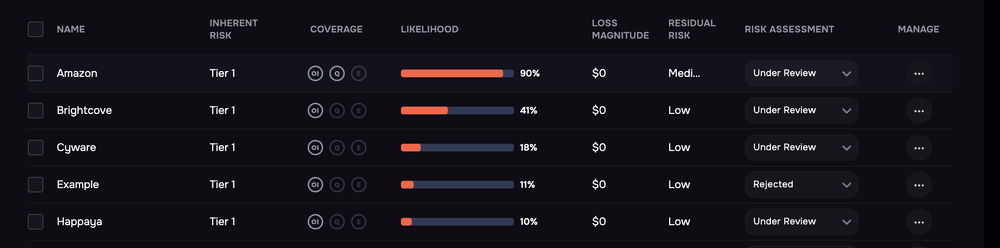
Tracking third parties on the SAFE One platform
5. “Finally, bring order to third party cyber risk management”
Large organizations struggle to get their arms around the risk posed by hundreds, even thousands of vendors and partners. Effectively tier your vendors based on quantitative risk analysis: Run risk assessments for the third parties for probable likelihood and impact of a cyber event and allocate attention and resources accordingly.
SAFE Can Help
Our FAIR-based TPRM solution automates, unifies and runs your third party cyber risk management program at scale. We empower you to:
- Focus on critical third-parties, verified with evidence from secure software and security-conscious personnel
- Prioritize third parties based on breach likelihood and loss impact
- Manage third party risk impact using zero trust controls to enhance native controls in minimizing third party breaches
- Consolidate insights from outside-in and inside-out assessments plus questionnaires.
Learn More:
Download the TPRM Program Blueprint: Your Guide for Transforming Third-Party Risk Management



